Migrating your certification authority hashing algorithm from sha 1 to sha-2
0 likes137 views
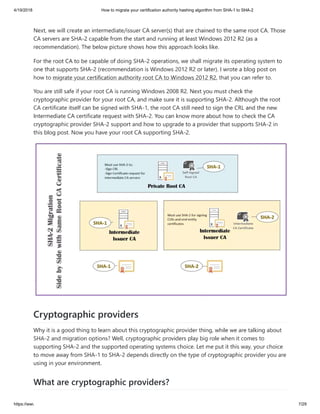
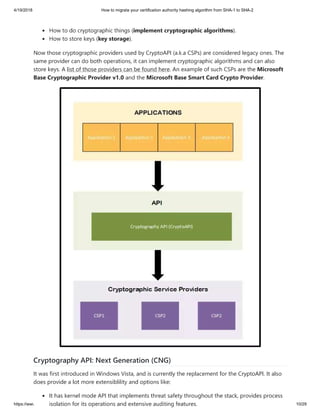
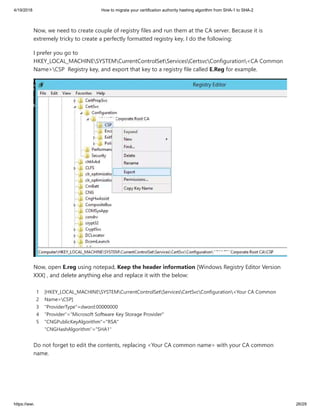
A practical guide on how to migrate your certification authority hashing algorithm from SHA-1 to SHA-2, and guidance on cryptographic providers, what makes your CA SHA-2 capable, and step by step guide with screenshots.
Related topics:1 of 29
Download to read offline


























More Related Content
More from Ammar Hasayen (20)
Ad
Recently uploaded (20)
Ad