110.decision makers.cio.ciso
- 1. Decision Makers Security Solution Sales Larry Smith : Sales Enablement And Training Director
- 2. Questions To Answer Today Who are the decision makers in the security solution purchase process? What are their roles, goals, metrics and challenges? What resonates with them?
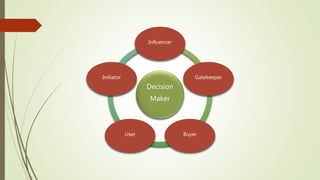
- 4. The IT Security Organization CEO CxO CxO CIO CISO Compliance Identity/AM Privacy Audit IS Architects IS Operations APPSEC Incident Response BUSINESS SYSTEMS APPDEV IT Governance Program Management = Decision Influencer = Decision Maker } Business Advocates } Technology Advocates
- 6. CIO Role: Leads IT strategies to enable the business and drive value Envisions and implements information technology to solve business problems and empower employees and clients Oversees decision input on operational processes to generate revenue streams and cut costs Manages the proliferation of devices and applications, while maintaining a secure environment
- 7. CIO Goals: Serve as a catalyst and enabler across the executive suite Turn insights into competitive advantage with tangible business benefits that fuel innovation and hedge against disruption Build profitability and create cost efficiencies Ensure proper governance oversight Minimize IT silos and capitalize on new business opportunities Manage risks and grow safely
- 8. CIO Key Metrics: • ROI and revenue value • IT expense as a percentage of sales and IT spend per employee • Change success rate and percent of emergency changes • Number of security incidents • Percent of SLAs met and response times • Successful system implementation • Cost management • Uptime • Customer and employee satisfaction
- 9. CIO Challenges: IT failures and crisis management Political and business savvy to navigate the C-suite Compliance, security and governance IT sprawl, shadow IT and BYOD Overburden of operational activities that inhibit the ability to drive innovation Retaining IT Talent
- 10. Critical Issues What Resonates… Business Alignment Digital Leadership Cyber Security Cost/Value Security Talent Transformation Innovation Efficiency CIO
- 12. CISO Role: Drives strategies to limit security risks and protects the brand Balances security strategies with business’ tolerance for risk Defines the security policies for the business Implements security architecture and engineering Ensures compliance within regulatory requirements, industry standards and best business practices Stay in front of threat vectors Incident response and recovery
- 13. CISO Goals: Minimize risk Protect client’s privacy Create an organizational culture of security Collaborate as a trusted business advisor Talking “business risk” vs. “IT security” Quantify the business’ risk appetite Identify risk issues to business assets Detect and correlate multi-level attacks
- 14. CISO Metrics: Monetize the value of protecting intangible assets Quantifiable identity and access management metrics Balanced scorecards that highlight operational inefficiencies, improve security posture, improve employee, partner and client service delivery and satisfaction
- 15. CISO Challenges: Changing threat landscape Balancing strategic and operational tasks Compliance and regulations Quantifying Value of Information Assets Range of devices and technologies to maintain Abundance of security data Attracting and retaining talent
- 16. Critical Issues What Resonates… Compliance IT Complexity Evolving Threats Efficiency Faster Time To Value Reducing Risk Reducing Complexity Innovation CSO/CISO
- 17. It’s Not About Security. It’s About Business Value.
Editor's Notes
- #4: Because these are key players in the buying process, we need to understand their challenges and their perspective on the needs of the business.
- #5: While there are no rules as to how an organization should be structured, there are general guidelines as to how responsibilities roll out through any organization. This presentation is more about responsibilities than titles as often one individual has multiple areas of responsibility. For this presentation we’re going to highlight the decision makers. While your conversations may not begin with the decision makers you do need to understand their challenges and how they see the world. The decision makers are the business advocates, guided by operational impact, cost of ownership, and budgets. They are responsible to the line of business to provide leadership and sound judgement. Generally the decision maker owns the budget for IT spending and will require a solid business case that supports their goals and initiatives. The decision influencers tend to be technology advocates guided by impact on existing processes and systems.
- #6: Let’s meet our first decision maker.. The CIO or Chief Information Officer. CIO’s are pivotal to the entire enterprise IT vision and portfolio. They are strategists, initiators for needs, large budget owners, as well as key influencers over others’ budgets and decisions. Most successful CIO’s are proactive in nature and in practice strive to anticipate issues but managing the unexpected is a trademark of a seasoned CIO.
- #7: In today’s economy the CIO isn’t merely a technical advisor to the board. Today the CIO is the enabler of the business. As organizations rely more heavily on technology to engage clients, improve business efficiency and drive revenue, the CIO and the IT organization have become the business. This is one dimension of digital transformation.
- #8: The goals of the successful CIO are so closely aligned to the business they are often indistinguishable from the line of business. Generally the goals are to drive efficiency, reduce cost and reduce risk to the organization; You need to understand this because solutions that are not clearly aligned with their goals will likely not find their way through finance. Make sure your value proposition resonates with the CIO.
- #9: These are some of the key metrics that a CIO is measured against. Obviously those most closely tied to managed security services would include: Number of security incidents Cost Management client and Employee Satisfaction… That last one is less tangible than the others but let me explain why this is perhaps the most critical to the CIO. Just consider what is happening in the news these days; Security breeches can be business ending events; Even minor events can damage a brand reputation; So client satisfaction becomes both an operational and a security challenge for the CIO as the business transforms to a digital workplace and clients become more demanding of impeccable brand experiences.
- #10: Among the most challenging issues and decisions they face are around coping with outages, compliance, security, cost controls, complexity of their infrastructure and retention of skilled employees. Solutions that provide leverage to improve efficiency, mitigate risk and reduce costs while supporting the growth and expansion of the business are going to resonate with the CIO.
- #11: In summary, Business Alignment, Digital Leadership and Cyber Security are often at or near the top of their list of issues to work through… Conversations about how to reduce cost, improve security, retain talent, help transform the business, enable innovation or improve efficiency are going to be of interest to the CIO.
- #12: Now let’s meet our next decision maker, The CISO or Chief Information Security Officer. Sometimes referred to as simply the CSO or Chief Security Officer. Chief Security Officers are lead influencers on IT overall and can be a deal-maker or deal-breaker. In some organizations their identity can be a mystery, which they prefer because being well known in this role is generally the consequence of a security breach or an appearance on CNN. But the CISO of an organization is a strategic leadership role from a business standpoint. Monitoring and responding to cyber threats while meeting compliance requirements are a just the beginning of their challenges. They have board level visibility and must often articulate and explain complex threat management to the board. Many CISO’s come from non-business backgrounds having worked in engineering and IT for many years, this can be challenging. The typical CISO may have 15 or more years experience in IT and IT Security, To their credit they are often very technically savvy with deep industry knowledge and experience. Selecting or even changing managed security services providers is significant strategic change for an organization. Most often managed security services are part of a larger IT strategy which must be properly aligned. The benefits not only need to outweigh the risk, the business case has to meet with business approval including that of the board. Finally, the CISO is regarded as the company expert and educator. Someone the board relies upon and appreciates for their leadership and guidance in matters of cyber security, risk mitigation and cyber resilience.
- #13: The CISO is there to ensure the security of information assets; In some cases the role or responsibility of the CISO may be delegated to an IT Director or other senior IT manager; In any case they will share certain similarities in terms of goals and challenges; Less important than the title is to understand who serves in this role and has these responsibilities;
- #14: The goals of the CISO are aligned to those of the CIO, or they should be. As a trusted business advisor to boards they need to understand and convey information in the context of business risk as opposed to IT Security; Beyond compliance and policy enforcement, they must manage information risks more strategically and work toward a culture of shared cyber risk ownership across the enterprise.
- #15: Metrics for the CISO can vary from one organization to another and can be difficult to quantify from a business perspective. How do you measure and monetize the prevention of or minimization of risk? As environments become more complex and threat models evolve, better detection, prevention and mitigation metrics can help CISO’s demonstrate value to their organizations. Key performance indicators for the CISO often include such measures as; Business process productivity and efficiency; R&D Spending client Satisfaction (Revenue) Employee Satisfaction (Retention)
- #16: We all recognize that cyber threats are an evolving menace. But the person charged with protecting an organizations information assets has the enormous task and responsibility to oversee all aspects of that organizations security posture. They include everything from attracting and keeping skilled talent to policies, practices and technologies that reduce risk and maintain the integrity of data while aligning to the needs of the business.
- #17: In summary, Compliance, IT Complexity and the evolving threat landscape are often at or near the top of their list of issues the CISO needs to work through… Conversations about how to improve efficiency, achieve faster time to value, reduce risk and support innovation will resonate with the CISO of an organization…