V-Empower Services And Solutions
- 1. Security Services and Solutions Enabling Secure Business
- 2. Mission: To provide state-of-the-art security solutions and services to customers employing in-depth research, comprehensive analysis and knowledge share. Vision: To produce innovative security products and provide superior consulting services for enabling secure computing and business. Introduction
- 3. V-Empower is global solutions and services company established 2000 North America: Bowie, Maryland USA Seattle, Washington USA Los Angeles, California USA Maple, Ontario Canada Europe: London, United Kingdom Asia Pacific Beijing, China South East Asia Hyderabad, India Company Profile
- 4. Company Profile V-Empower saw a 206 % increase in revenue in 2006 Our security team consists of highly talented industry experts Providers of security services and solutions to the worlds largest software company
- 5. Services Infrastructure Security Penetration Testing Network Infrastructure Configuration Review of Infrastructure Devices Design and Deploy Secure Infrastructure Solutions Application Security Black Box Assessments (Penetration Testing) White Box Assessments (Detailed Code Reviews) Threat Analysis and Modeling Security Research and Development Security Program Development Resource Integration Integrating Security into Systems Development Lifecycle (SDLC) Security Policy and Standards Development Security Program Analysis Training Services Secure Application Development Application Source Code Auditing Threat Analysis and Modeling Application Security Awareness
- 6. Comprehensive Penetration Services Typical Penetration Tests consist of arbitrary approaches
- 7. Comprehensive Penetration Services Systematic Approach Comprehensive Services Environment Specific Threat Evaluation Assets Driven Assessment Vulnerability Analysis Comprehensive Reporting Recommendations and Validation
- 8. Comprehensive Penetration Services Assurance on effective controls
- 10. Design And Architecture Review Background Analysis (Business Functionality) Design Documentation (Architecture Diagram) Asset Identification (Data Flow Diagrams) Review Design and Architecture
- 11. Threat Analysis and Modeling Review Threat Models Environment Decomposition Asset Identification (Data, Functionality, etc) Operating Procedures Identification (Use Cases) Threat Identification (Based on Assets and Operations)
- 13. Comprehensive Assessment Identify Technologies Involved
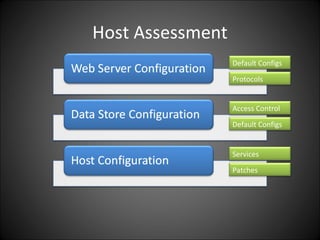
- 14. Host Assessment Default Configs Protocols Access Control Default Configs Services Patches
- 15. Application Layer Assessment AuthN Protocol Elevation of Privileges Logging XSS, XRSF, RI, SQL Injection, BO Resources Cryptography Information D AuthZ Bypass DOS, Deface
- 16. Network Layer Assessment Firewall, IDS, etc Perimeter Cntrls Fuzz Testing Standard Eval Network Security Best Practices.
- 17. Risk Analysis and Reporting Risk Analysis Evaluation of each vulnerability to assess true risk to an environment. Risk is reported based on a matrix which evaluates the following keys factors Vulnerability classification (STRIDE - CIA) Classification of Asset Probability of Exploit Impact of Exploit
- 18. Risk Analysis and Reporting All vulnerabilities are given the following Severity Ratings:
- 19. Severity Ratings Critical : Impact of vulnerability can compromise multiple applications/across organization boundaries. Recommend immediate mitigation. High : Impact of vulnerability can compromise application with limited cross organization impact. Recommend priority in mitigation. Medium : Best Practice & should be fixed with in next version release. Low : Recommended best practice with low priority for mitigation.
- 20. Risk Analysis and Reporting Title Severity Explanation of Issue Explanation of Impact Real life attack scenario Proof of concept exploit Recommendations for Remediation Validation Steps References
- 21. Analysis and Reporting Critical High Medium Low
- 22. Acknowledgements What controls are effective which were tested. Break down of the controls which effectively guard the environment against different threat types.
- 23. Incremental Reviews Due to the in-dept Analysis performed at the first iteration of the assessment, any update and changes can be reviewed incrementally following the same approach.
- 24. Future Follow-up Establish future touch points or additional services required in relation to an assessment.
- 25. Our Team V-Empower Security Team (VST) consist of 27 consultants world wide providing services to Fortune 100 companies VST’s methodology and services have been incorporated by many clients VST’s has been featured in Microsoft’s Information Security Newsletter
- 26. Publications Advances in Forensics Intro to Exploits Coding Forensics with Open Source Software Pen Testing Tools Development Pen Testing Methodologies Exploits Coding Techniques Real Life VulnDev Process of a Win32 Stack Buffer Overflow Vulnerability Development on Linux and Win32 Elevation of Privileges in Thick Clients Presentations Antivirus (In)Security (Black Hat Europe 2007) Vulnerability Development under Unix and Win32 (CIH2K5, International Hackers Congress 2005) Introduction to Exploits Coding (InfoSecurity 2004) Automated Pen testing Tools Development (GCon III) Project Portfolio
- 27. Clients
- 28. Testimonials V-Empower Inc is the preferred Security Vendor for Microsoft. Testimonials … your team is the best in the business. - Todd Kutzke ( Director , Microsoft) Another nice example of how good a job V-Empower is doing….extend my compliments to your team for the quality of their support and making sure our customers see the value of the services we provide… - Shawn Veney ( Manager , ACE Team, Microsoft) Thank you! It’s outstanding that we had someone who actually knows about Email. - Yaron Goland ( PRINCIPAL PROGRAM MANAGER , MSN) “ Quoted in relation to a vulnerability.”
- 29. Future Value Add to Wamu Methodology Knowledge Share Resource Augmentation Off shore development Code Reviews General Security Consulting