Application of matrix multiplication (cryptography) with solved problem
- 1. Name: Mohammad Waqas Roll Number: 19CH18 Subject: Liner Algebra Analytical Geometry (LAAG) Date: 27/07/2020 1
- 2. Presentation Topic Application of matrix multiplication (Cryptography) 2
- 3. What is Cryptography A cryptogram is a message written according to a secret code (the Greek word kryptos means “hidden”). This section describes a method of using matrix multiplication to encode and decode messages. Cryptography mainly consist of encryption and decryption Encryption Convert the plain data into numerical by giving A to 1,B to 2,C to 3 and so on. Place the numerical in to matrix M of order mn ≥ L. Multiply the matrix M with a non-singular matrix A to get the encoded matrix X. The determinate of (non singular matrix) A must be equal to ±1. Convert the resultant, the encrypted message matrix in to a text message of length L and that will be send to the receiver. 3
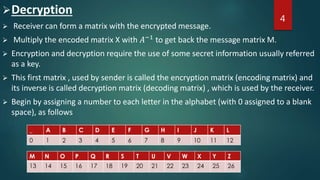
- 4. Decryption Receiver can form a matrix with the encrypted message. Multiply the encoded matrix X with 𝐴−1 to get back the message matrix M. Encryption and decryption require the use of some secret information usually referred as a key. This first matrix , used by sender is called the encryption matrix (encoding matrix) and its inverse is called decryption matrix (decoding matrix) , which is used by the receiver. Begin by assigning a number to each letter in the alphabet (with 0 assigned to a blank space), as follows 4
- 5. 5Application of cryptography Secure communication: To prevent eavesdropping war time communication and business transactions Secret Sharing / data hiding: Hide something that has been written. Access Control: Regulate access to satellite and cable TV. Cell phones: Prevent people from stealing cell phone . Access code or evadropping
- 6. 6
- 7. 7
- 8. 8
- 9. References Book Name: Elementary Linear Algebra Author name: Howard Antion and Chris Rorrers Edition Number: 11th edition Publisher year: 2014 www.synopsys.com. C.J.R.Berges 9
- 10. 10