Basic Encryption Decryption Chapter 2
- 2. Definitions Encryption: process of encoding a message so its meaning is not obvious. Decryption: reverse process which means try to bring encrypted message back to normal form. Cryptosystem: encryption & decryption system Plaintext: original form of message Ciphertext: encrypted form of message
- 3. Definitions Cryptography: hidden writing Cryptanalysis: breaking of secure messages Cryptanalyst: studies of encryption/decryption message with the goal of finding the hidden message (break the encrypted message). Cryptology: research/study of encryption & decryption (both cryptography + cryptanalyst)
- 4. Encryption Algorithms Plaintext Encryption Ciphertext Decryption Original Plaintext Encoding: the process of translating entire words or phrases to other words or phrases. Enciphering: the process of translating letters or symbols individually. Encryption: is the group of term that covers both encoding and enciphering.
- 5. There are 2 type of encryptions: Symmetric Encryption: uses same key for encryption and decryption process. To encrypt: C = E(P, K) To decrypt: P = D (E(P,K), K) Encryption Algorithms Encryption Decryption Plaintext Ciphertext Original Plaintext Key
- 6. Encryption Algorithms Asymmetric Encryption: uses different key for encryption and decryption process. To encrypt: C = E (P, KE) To decrypt: P = D (E (P, KE), KD) Encryption Decryption Plaintext Ciphertext Original Plaintext Encryption Key (KE) Decryption Key (KD)
- 7. Substitutions Substitution: one letter is exchanged for another. Can be divided into two categories: Monoalphabetic Substitution Polyalphabetic Substitution
- 8. Monoalphabetic Substitutions Monoalphabetic Cipher – always uses the same letter of the alphabet for the ciphertext letter. A – 0 H – 7 O – 14 V – 21 B – 1 I – 8 P – 15 W – 22 C – 2 J – 9 Q – 16 X – 23 D – 3 K – 10 R – 17 Y – 24 E – 4 L – 11 S – 18 Z – 25 F – 5 M – 12 T – 19 G – 6 N – 13 U – 20 Arithmetic is done as if the alphabet table were circular. Encrypt: C = E (a) = (a + k) mod 26 Decrypt: a = D (C) = (C – k) mod 26
- 9. Monoalphabetic Substitutions The Caesar Cipher (Monoalphabetic Substitution) Named after Julius Caesar – said to be the first to use it. Each letter is translated to another letter. Ci = E (pi) = (pi + x) mod 26 Example: (x = 19) A B C D E F G H I J K L M N O P Q R S T U V W X Y Z T U V W X Y Z A B C D E F G H I J K L M N O P Q R S Plaintext = “SECURITY” Ciphertext = “LXVNKBMR” Advantages: easy to remember Disadvantages: easy to predict pattern of encryption
- 10. Monoalphabetic Substitutions Substitution using key phrase: • Example: If the key phrase is BOM, the shifted key are as follows: Plaintext: A B C D E F G H I J K L M N O P... Ciphertext: B O M A C D E F G H I J K L N P.. • Key Phrase must contain unique letters. Any redundancy need to be excluded before encrypting. • Have the same strength as the previous simple substitution ciphers.
- 11. Monoalphabetic Substitutions Let’s analyze the example below: Example: Key: SPECTACULAR (key must not contain redundant letters so drop C and A), therefore key becomes SPECTAULR A B C D E F G H I J K L M N O P Q R S T U V W X Y Z S P E C T A U L R B D F G H I J K M N O Q V W X Y Z
- 12. Monoalphabetic Substitutions To strengthen, apply matrix such as below: C I N A B D E F G H J K L M O P Q R S T U V W X Y Z Key Phrase is CINCIN P : A B C D E F G H I J K L M N O P Q R S T U V W X Y Z C: C E L S Y I F M T Z N G O U A H P V B J Q W D K R X
- 13. Monoalphabetic Substitutions Multiplication f(a) = ak mod n, where k and n are relatively prime so that the letters of the alphabet produced a complete set of residues. If k and n are not relatively prime, several plaintext will encrypt to the same ciphertext letter and not all letter will appear in the ciphertext alphabet e.g. if k = 12 and n =26. Example: If k = 12 Plaintext ABC DEF GHI JKL MNO PQR STU VWX YZ Ciphertext = AMY KWI UJS EQC OAM YKW IUA SEQ CO eg. BOM → MMO
- 14. Cryptanalysis of the Substitution Cipher The Arabs were the first to make significant advances in cryptanalysis. An Arabic author, Qalqashandi, wrote down a technique for solving ciphers which is still used today. The technique is to write down all the ciphertext letters and count the frequency of each symbol. Using the average frequency of each letter of the language, the plaintext can be written out. This technique is powerful enough to cryptanalyze ANY monoalphabetic substitution cipher if enough ciphertext is provided.
- 15. Character Frequencies Most languages letters are not equally common In English e is by far the most common letter These are different for different languages
- 17. Cryptanalysis of the Caesar Cipher Suppose you were trying to break the following ciphertext message: Wklv phvvdjh lv qrw wrr kdug wr euhdn It is not so difficult to break the ciphertext above by doing some analysis on it. How? (1) Start on the weak points: blank is translated to itself! (2) In English there are relatively few small words like; am, is, be, he, we, and, are, you, she etc… Therefore, one attack can start off by substituting known short words at appropriates places. (3) Look for repetition and patterns.
- 18. Cryptanalysis of the Caesar Cipher Example: If wrr is TOO. wr would be TO (more sense compare to SE) w k l v p h v v d j h l v q r w w r r k d u g w r e u h d n T - - - - - - - - - - - - - OT TOO - - - - TO - - - - -
- 19. Polyalphabetic Substitution Ciphers The weakness of monoalphabetic ciphers - frequency distribution reflects the distribution of the underlying alphabet. Solution : flatten the distribution : use polyalphabetic substitution How to flatten the distribution? – combine both high and low distributions. If E1 (T) = a and E2 (T) = b E1 (X) = a and E2 (X) = b
- 20. T & X – plaintext
- 21. Flat distribution of ciphertext ‘a’ and ‘b’
- 22. Polyalphabetic Substitution Ciphers We can also combine two distributions by using two separate encryption alphabets – the first for all characters in odd positions of the plaintext message and the second for all the characters in even positions.
- 23. Polyalphabetic Substitution Ciphers Consider the two encryption algorithms below: 26mod)*3()(1 λλπ = 26mod)*3()(1 λλπ = 26mod)13)*5(()(2 += λλπ A B C D E F G H I J K L M N O P Q R S T U V W X Y Z a d g j m p s v y b e h k n q t w z c f i l o r u x A B C D E F G H I J K L M N O P Q R S T U V W X Y Z n s x c h m r w b g l q v a f k p u z e j o t y d i Table for Odd Position Table for Even Position
- 24. Polyalphabetic Substitution Ciphers Encrypt TREATY IMPOSSIBLE TREAT YIMPO SSIBL E (plaintext) f umn f dyv t f czysh h (ciphertext) What have you notice?
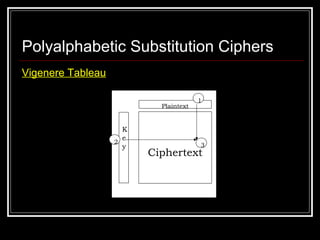
- 25. Polyalphabetic Substitution Ciphers Vigenère Ciphers Proposed by Blaise de Vigenere from the court of Henry III of France in the sixteenth century. Basically it’s a multiple Caesar Ciphers – each row of the Vigenere table corresponds to a Caesar cipher. The first row is a shift of 0, the second is a shift of 1 and the last is a shift of 25. Vigenere cipher uses this table together with a keyword to encipher a message.
- 26. Polyalphabetic Substitution Ciphers Vigenere Tableau Plaintext K e y Ciphertext 2 1 3
- 27. Polyalphabetic Substitution Ciphers Cryptanalysis of Polyalphabetic Substitutions There are two ways: Kasiski Method Index of Coincidence Kasiski Method for repeated pattens Named for its developer, a Prussian military officer. Is a way of finding the number of alphabets that were used for encryption. -th, -ion, -ed, -tion, and, to, are, appear with high frequency (regularity of English).
- 28. Polyalphabetic Substitution Ciphers Kasiski Method For Kasiski Method, the steps are: 1. Identify repeated patterns of three or more characters. 2. For each patterns write down the position at which each instances of the pattern begins. 3. Compute the difference between the starting points of successive instances. 4. Determine all factors of each difference. 5. If a polyalphabetic substitution cipher was used, the key length will be one of the factors that appears often in step 4.
- 29. Polyalphabetic Substitution Ciphers - Form set of letters according to the position of key assumed. - Use previous monoalphabetic cryptanalysis. Index of Coincidence Index of coincidence is a measure of the variation between frequencies in a distribution.
- 30. The “Perfect” Substitution Cipher What makes a perfect substitution cipher? An ideal substitution would use many alphabets for an unrecognizable distribution and no apparent pattern for the choice of an alphabet at a particular point. Let’s look at Vernam Cipher or One-Time Pad algorithms.
- 31. The “Perfect” Substitution Cipher Vernam Cipher (One Time Pad) Introduced by Gilbert Vernam (AT&T Engineer) in 1918. Immune to cryptanalytic attack because the available ciphertext does not display the pattern of the key. Involves an arbitrarily long non-repeating sequence of numbers that are combined with the plaintext.
- 32. The “Perfect” Substitution Cipher Vernam Cipher (One Time Pad) Compared with most cryptosystems it is very simple. To use a one time pad, you need two copies of the “pad” (also known as the key) which is a block of truly random data at least as long as the message you wish to encode. If the data on the pad is not truly random the security of the pad is compromised.
- 33. The “Perfect” Substitution Cipher Example: Assume that the alphabetic letters are combined by sum mod 26 with a stream of random two-digit numbers. Plaintext : V E R N A M C I P H E R Numerical Value : 21 4 17 13 0 12 2 8 15 7 4 17 +random number : 76 48 16 82 44 3 58 11 60 5 48 88 = sum : 97 52 33 95 44 15 60 19 75 12 52 105 mod 26 : 19 0 7 17 18 15 8 19 23 12 0 1 ciphertext : T A H R S P I T X M A B
- 34. The “Perfect” Substitution Cipher Note: random number 48 happen to fall at the places of repeated letters, accounting for repeated ciphertext A but however highly unlikely. repeated letter t comes from different plaintext letter
- 35. The “Perfect” Substitution Cipher Binary Vernam Cipher Works just as well as “alphabets”. Example : This operation is perform on each letter in sequence. Plaintext: 1 0 1 1 0 1 1 0 0 1 0 1 0 1 1 1 0 0 1 0 1 1 0 1 Input Bits Output BitsMessage Pad 0 0 0 0 0 0 1 1 1 1 1 1
- 36. The “Perfect” Substitution Cipher Vernam Cipher (One Time Pad) Systems using perfect random, non-repeating keys which is endless and senseless Random key used once, and only once. It is the only unbreakable cryptography system Unbreakable in theory: the key neither repeats, nor recurs, nor makes sense, nor erects internal frameworks perfect randomness nullifies any horizontal, or lengthwise cohesion
- 37. The “Perfect” Substitution Cipher Vernam Cipher (One Time Pad) Why wouldn't it be used today? Sender and receiver need to be perfectly synchronized It would not work for a T1 communication line: If receiver is off by a bit (bit dropped during transmission) the plaintext will not make any sense If bits are altered during transmission (noise hit) those bits will decrypt incorrectly It does not provides authenticity, only confidentiality
- 38. Transpositions (Permutations) The plaintext remains the same, but the order of characters is shuffled around – example: shuffle secret to etcrse Arrangement was classically done with the aid of some type of geometric figure, usually 2-dimensional array (matrix). Transposition is not a permutation of alphabet characters but a permutation of places: letters retain their identity but lose their position there is a permutation of the plaintext letters
- 40. Transpositions (Permutations) Transposition Cipher: Columnar Encryption: Plaintext is written horizontally onto the matrix of of fixed width and the ciphertext is read off vertically. Decryption: Ciphertext is written vertically onto the same matrix of identical width and then reading the plaintext off horizontally. Example : Plaintext is RENAISSANCE is written into a 3 x 4 matrix as follows R E N A I S S A N C E the resulting cipher text is RINESCNSEAA
- 41. Transpositions (Permutations) Double Transposition Algorithm Involves 2 columnar transposition, with different numbers of columns, applied one after the other. Example: Single Columnar T H (I S) I S A (M E) S S A (G E) T O S (H O) W H O (W A) C O L (U M) N A R (T R) A N S (P O) S I T (I O) N W O (R K) S Produces : TSSOH OANIW HAASO LRSTO (I(M(G(H(W (U(T(P(I(R S)E)E)O)A) M)R)O)O)K) ISTWC NASNS
- 42. Transpositions (Permutations) Second transposition written in an 8 by 7 matrix: Can you write down the result? T S S O H O A N I W H A A S O L R S T O (I (M (G (H (W (U (T (P (I (R S) E) E) O) A) M) R) O) O) K) I S T W C N A S N S X X X X X X
- 43. Transpositions (Permutations) Extra position must be filled with a padding character, eg. X However the X’s filling the last row stands out. Better way is to use letters that are frequently used so that it would not be possible to identify the padding character.
- 44. Stream vsBlock Ciphers Stream cipher – encrypt one symbol of plaintext immediately into a symbol of ciphertext Block cipher – encrypt a group of plaintext symbols as one block.
- 45. Stream vs Block Ciphers Advantages of stream ciphers: Speed of transmission – each symbol is encrypted alone, each symbol is encrypted as soon as it is read. Low error propagation – an error in the encryption process affects only that character (each symbol is separately encoded). Disadvantages of stream ciphers: Low diffusion where all information of the symbol contained in one symbol of the ciphertext – cryptanalyst consider each ciphertext as a separate entity. Susceptibility to malicious insertion & modification – interceptor who has broken the code can splice together pieces of previous message and transmit a spurious new message that may look authentic.
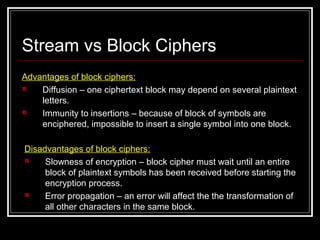
- 46. Stream vs Block Ciphers Advantages of block ciphers: Diffusion – one ciphertext block may depend on several plaintext letters. Immunity to insertions – because of block of symbols are enciphered, impossible to insert a single symbol into one block. Disadvantages of block ciphers: Slowness of encryption – block cipher must wait until an entire block of plaintext symbols has been received before starting the encryption process. Error propagation – an error will affect the the transformation of all other characters in the same block.
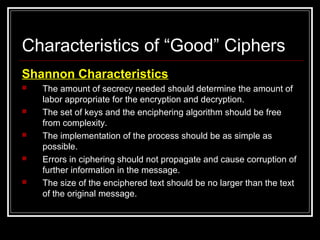
- 47. Characteristics of “Good” Ciphers Shannon Characteristics The amount of secrecy needed should determine the amount of labor appropriate for the encryption and decryption. The set of keys and the enciphering algorithm should be free from complexity. The implementation of the process should be as simple as possible. Errors in ciphering should not propagate and cause corruption of further information in the message. The size of the enciphered text should be no larger than the text of the original message.
- 48. Characteristics of “Good” Ciphers Confusion – Interceptor should not be able to predict what changing one character in the plaintext will do to the ciphertext. Diffusion – Changes in the plaintext should affect many parts of the ciphertext. Good diffusion means that the interceptor needs access to much ciphertext to infer the algorithm.
- 49. THE END