Common technique in Bypassing Stuff in Python.
- 1. Bypass AV in Python by y0nd13.
- 2. Quick introduction to Python • By default exist in every major Linux Distribution • Can be install or run as portable tools in Windows :
- 3. How interpreter language work.
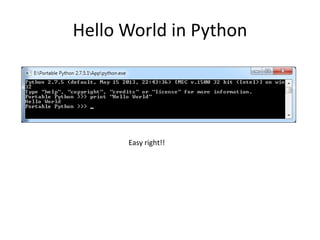
- 4. Hello World in Python Easy right!!
- 5. So what’s the big deal? • Python support Foreign Function Instruction • It supports Ctypes. • http://docs.python.org/2/library/ctypes.html • It provides C compatible data types, and allows calling functions in DLLs or shared libraries. It can be used to wrap these libraries in pure Python • Smell profits!!! • Alternative ways besides using import system • Good for Post Exploitation • Bypass AV
- 6. Quick Introduction to Python FFI
- 7. A Simple MessageBoxA • From MSDN • Required 4 argument,
- 8. How to understand quickly • HWND – A handle to the owner window of the message box to be created. If this parameter is NULL, the message box has no owner window. (SO we set to Null, in Python Null is None) • LPCTSR lpText - It’s a string for a Text • LPCTSR lpCaption – It’s a string for the MessageBox Title • UINT - Unsigned Integer . _in_opt_ is a SAL Annotation saying you can put NULL as a value
- 9. SAL Annotation shortcut Parameters are required Parameters are optional Input to called function _In_ _In_opt_ Input to called function, and output to caller _Inout_ _Inout_opt_ Output to caller _Out_ _Out_opt_ Output of pointer to caller _Outptr_ _Outptr_opt_
- 10. How easy to pop up a MessageBox in python? • Simple from ctypes import * ctypes.windll.user32.MessageBoxA(None,"Hello World","Title",None)
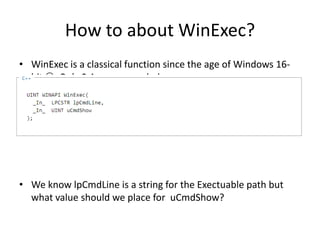
- 11. How to about WinExec? • WinExec is a classical function since the age of Windows 16- bit . Only 2 Args are needed. • From MSDN • We know lpCmdLine is a string for the Exectuable path but what value should we place for uCmdShow?
- 12. uCmdShow from MSDN • http://msdn.microsoft.com/en- us/library/windows/desktop/ms633548(v=vs.85).aspx
- 13. To Spawn a calcfrom ctypes import * ctypes.windll.kernel32.WinExec(“C:Windowssystem32calc.exe”,1)
- 15. How about Executing Shellcode? • Many ways – File Dropping Technique (BAD) – Code Injection Technique(BAD) – InMemory Technique (G000D) • File Dropping Technique are bad , since antivirus/malware will immedietely catch it up and trigeger • Code Injection , affects the integrity of a binary. HIPS might trigger alert. • Why Shellcode? Becoz we can!!
- 16. InMemory Technique • We are going to chain 4 API to execute our shellcode . – >VirtualAlloc() – >WriteProcessMemory() – >CreateThread() – >WaitForSingleObject()
- 17. VirtualAlloc() • lpAddress = Null • dwSize = length of shellcode can be use, • flAllocation = MEM_COMMIT|MEM_RESERVED (0x3000) • flProtect = PAGE_EXECUTE_READWRITE(0x40)
- 18. WriteProcessMemory() • hProcess = -1 * we writing in the same process • lpBaseAddress = A Pointer to address return from VirtualALloc() • lpBuffer = A pointer to our buffer • nSize = we can use shellcode size and times 2 to be safe • lpNUmberofBytesWritten = Null it..
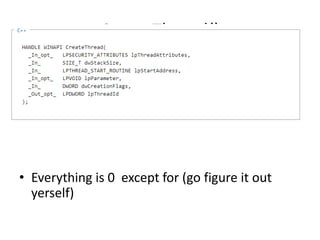
- 19. CreateThread() • Everything is 0 except for (go figure it out yerself)
- 20. WaitForSingleObject() • -1 , -1 !!!
- 21. P.O.C • Inspired by SK Training.. Use xcc !!!
- 22. Using OllyDBG Attached with Olly
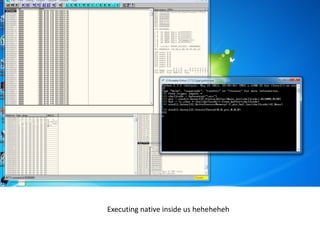
- 23. Executing native inside us heheheheh
- 24. 2nd POC is our calc
- 26. (Optional) Freeze it to exe • Using pyinstaller
- 27. Simple2
- 28. Exercise • Create a Reverse Shell is a piece of cake!
- 29. Reference • Understanding Win32Shellcode Skape: • http://www.hick.org/code/skape/papers/win32-shellcode.pdf • Advance Windows Shellcode, SK: • http://www.phrack.org/issues.html?id=7&issue=62 • http://msdn.microsoft.com/en-US/