Introduction to Common Weakness Enumeration (CWE)
- 1. Common Weakness Enumeration Aung Thu Rha Hein (g5536871)
- 2. Content ■ What is CWE? ■ CWE Process ■ CWE Lists ■ CWE Overviews ■ CWE Requirements ■ Products & Services ■ References
- 3. What is CWE? ■ CWE is an extended project of CVE by MITRE ■ list of software weakness for developers and security practitioners ■ a common language for describing software security weaknesses ■ a standard measurement for software security tools ■ a common baseline standard for weakness identification, mitigation, and prevention efforts
- 4. CWE Process ■ CVE provides real-world vulnerabilities ■ CWE provides specific and concise definition of common software weakness ■ working to map each CWE list with specific CVE-IDs ■ 3 organizational structures for CWE elements: o lowest level for tool vendors & researchers o mid level for security practitioners o highest level for software practitioners & other stakeholders
- 5. CWE Lists ■ latest version - 2.6 o 943 CWEs ● 31 views ● 187 categories ● 717 weakness ● 8 compound elements ■ it also provides filter for different users ■ the lists are community initiative
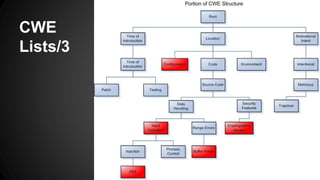
- 6. CWE Lists/2 ■ CWEs are in hierarchical structure
- 7. CWE Lists/3
- 8. CWE Overviews ■ 4 useful overviews (Total,Views,Categories,Weakness, Compound elements) o CWE-699: Development concepts (754, 4, 65, 680, 5) o CWE-1000: Research concepts ( 721, 0, 9, 704, 8) o CWE-2000: Comprehensive CWE Dictionary o PDFs with Graphical Depictions of CWE ■ Views can be slices or graphs ■ Compound Elements are entries that closely associates ■ Chains are entries that has cause/effect on another
- 9. CWE Requirements *4 out of6 requirements CWE Searchable users may search security elements using CWE identifiers CWE Output security elements presented to users includes, or allows users to obtain, associated CWE identifiers Mapping Accuracy security elements accurately link to the appropriate CWE identifiers CWE Documentation capability's documentation describes CWE, CWE compatibility, and how CWE-related functionality in the capability is used CWE Coverage for CWE-Compatibility and CWE-Effectiveness, the capability's documentation explicitly lists the CWE-IDs that the capability claims coverage and effectiveness against locating in software CWE Test Results for CWE-Effectiveness, test results from the capability showing the results of assessing software for the CWEs are posted on the CWE Web site
- 10. Products & Services ■ 10 organizations that hold CWE compatible status o Fascoo (Sparrow) o CXSecurity (WLB) o GrammarTech (CodeSonar) o High-Tech Bridge (HTB SA,ImmuniWeb) o IBM Security Systems (IBM Security AppScan Standard) o Klockwork (Klokwork Insight) o HP o NIST (SARD) o Security Database (Security Database Web Services) o Veracode (Veracode Analysis)
- 11. References ■ http://cwe.mitre.org/ ■ https://en.wikipedia.org/wiki/Common_Weakness_Enu meration ■ https://nvd.nist.gov/cwe.cfm
Editor's Notes
- #4: CWE is a security measurement standard by classifying and categorizing vulnerabilities, attacks, faults, and other concepts to help define common software weaknesses.
- #5: we continue to leverage as many sources and examples as we can from the CWE community other interested parties, to develop the specific and succinct definitions of the CWE List elements and classification tree structures. (1) the lowest level consists of the full CWE List (hundreds of nodes) that is primarily applicable to tool vendors and detailed research efforts; (2) a middle tier consists of descriptive affinity groupings of individual CWEs (25-60 nodes) useful to software security and software development practitioners; and (3) a more easily understood top level consisting of high-level groupings of the middle-tier nodes (5-15 nodes) to define strategic classes of vulnerabilities and which is useful for high-level discourse among software practitioners, business people, tool vendors, researchers
- #6: 2.6 published Feb 2014 full CWEs include View a subset of CWE entries that provides a way of examining CWE content. The two main view structures are Slices (flat lists) and Graphs (containing relationships between entries). Category a CWE entry that contains a set of other entries that share a common characteristic. Class Weakness a weakness that is described in a very abstract fashion, typically independent of any specific language or technology. More general than a Base weakness. Base Weakness a weakness that is described in an abstract fashion, but with sufficient details to infer specific methods for detection and prevention. More general than a Variant weakness, but more specific than a Class weakness. Compound Element an Entry that closely associates two or more CWE entries. The CWE team's research has shown that vulnerabilities often can be described in terms of the interaction or co-occurrence of two or more weaknesses. In CWE 1.0, the only types of compound elements are Chains and Composites, although other types might be defined in later versions.