Digital signatures
- 1. Technology of Digital Signatures in India Presented by: Atul S. Jaybhaye B.A.LL.M.NET Assistant Professor Hidayatullah National Law University, Raipur
- 3. Important Definitions under IT Act Sec 2(p) “Digital signature" means authentication of any electronic record by a subscriber by means of an electronic method or procedure in accordance with the provisions of section 3; Sec 2(f) “Asymmetric crypto system" means a system of a secure key pair consisting of a private key for creating a digital signature and a public key to verify the digital signature; Sec 2(x) "key pair", in an asymmetric crypto system, means a private key and its mathematically related public key., which are so related that the public key can verify a digital signature created by the private key;
- 4. Meaning of Digital Signatures: A digital signature is a mathematical scheme for presenting the authenticity of digital messages or documents. A valid digital signature gives a recipient reason to believe that the message was created by a known sender (authentication), that the sender cannot deny having sent the message (non-repudiation), and that the message was not altered in transit. It is commonly used for software distribution, financial transactions, contract management software, and in other cases where it is important to detect forgery or tampering. move from the pen and paper world to an electronic era.
- 5. Uses of Digital Signature E-filling, E-tender and E-procurement Income Tax Sales Tax Patent and trade marks registration Oil & Natural Gas Corporation (ONGC) MSTC Limited Bharat Petroleum Corporation Limited (BPCL)
- 6. Features of Digital Signature. Authentication- Digital signatures are used to authenticate the source of messages. The ownership of a digital signature key is bound to a specific user and thus a valid signature shows that the message was sent by that user. Integrity - In many scenarios, the sender and receiver of a message need assurance that the message has not been altered during transmission. Digital Signatures provide this feature by using cryptographic message digest functions. Non Repudiation – Digital signatures ensure that the sender who has signed the information cannot at a later time deny having signed it.
- 7. What is PKI System? Digital signatures use a standard, accepted format, called Public Key Infrastructure (PKI), to provide the highest levels of security and universal acceptance. PKI requires the provider to use a mathematical algorithm to generate two long numbers, called keys. One key is public, and one key is private. The purpose of a PKI is to facilitate the secure electronic transfer of information for a range of network activities such as e-commerce, internet banking and confidential email. It is required for activities where simple passwords are an inadequate authentication method and more rigorous proof is required to confirm the identity of the parties involved in the communication and to validate the information being transferred.
- 8. Digital Signature Vs Handwritten Signatures A handwritten signature scanned and digitally attached with a document does not qualify as a Digital Signature. A Digital Signature is a combination of crypto algorithms. An ink signature can be easily replicated from one document to another by copying the image manually or electronically. Digital Signatures cryptographically bind an electronic identity to an electronic document and the digital signature cannot be copied to another document. Digital signatures on the other hand compute the hash or digest of the complete document and a change of even one bit in the previous pages of the document will make the digital signature verification fail.
- 10. Who issues Digital Signatures? A licensed Certifying Authority (CA) issues the digital signature. Certifying Authority (CA) means a person who has been granted a license to issue a digital signature certificate under Section 24 of the IT-Act 2000. Controller, appointed by Central govt. of India is the head of Certifying Authorities. A Digital Signature Certificate is a secure digital key that is issued by the certifying authorities for the purpose of validating and certifying the identity of the person holding this certificate. A digital signature certificate (DSC) contains information about the user’s name, pin code, country, email address, date of issuance of certificate and name of the certifying authority.
- 11. DS- Provisions under IT Act 3. Authentication of electronic records.- (1) Subject to the provisions of this section, any subscriber may authenticate an electronic record by affixing his digital signature. (2) The authentication of the electronic record shall be effected by the use of asymmetric crypto system and hash function which envelop and transform the initial electronic record into another electronic record (3) Any person by the use of a public key of the subscriber can verify the electronic record. (4) The private key and the public key are unique to the subscriber and constitute a functioning key pair.
- 12. UNICITRAL ON D.S. The Model Law on Electronic Signatures (MLES) : 2001 Objective: It aims to enable and facilitate the use of electronic signatures by establishing criteria of technical reliability for the equivalence between electronic and hand-written signatures. The MLES is based on the fundamental principles common to all UNCITRAL texts relating to electronic commerce, namely non- discrimination, technological neutrality and functional equivalence. Electronic signatures, together with certificates, are offered as a substitutive solution of hand-written signatures for a wide scale electronic commerce.
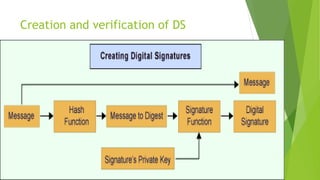
- 13. Creation and verification of DS
- 16. Uses of Public key Cryptography: I. Public key encryption: in which a message is encrypted with a recipient's public key. The message cannot be decrypted by anyone who does not possess the matching private key, who is thus presumed to be the owner of that key and the person associated with the public key. This is used in an attempt to ensure confidentiality. II. Digital Signature: in which a message is signed with the sender's private key and can be verified by anyone who has access to the sender's public key. This verification proves that the sender had access to the private key, and therefore is likely to be the person associated with the public key.
- 17. Example Assume you were going to send the draft of a contract to your lawyer in another town. You want to give your lawyer the assurance that it was unchanged from what you sent and that it is really from you. 1. You copy-and-paste the contract (it's a short one!) into an e-mail note. 2. Using special software, you obtain a message hash (mathematical summary) of the contract. 3. You then use a private key that you have previously obtained to encrypt the hash. 4. The encrypted hash becomes your digital signature of the message. (Note that it will be different each time you send a message.) At the other end, your lawyer receives the message. 1. To make sure it's intact and from you, your lawyer makes a hash of the received message. 2. Your lawyer then uses your public key to decrypt the message hash or summary. 3. If the hashes match, the received message is valid.
- 18. Legal Validity of Digital Signatures One of the primary objectives of the Information Technology Act of 2000 was to promote the use of Digital Signatures for authentication in e-commerce & e-Governance. Section 5 of the Act gives legal recognition to digital signatures based on asymmetric cryptosystems. The digital signatures are now accepted at par with the handwritten signatures. Towards facilitating this, the office of Controller of Certifying Authorities (CCA) was set up in 2000. The CCA licenses Certifying Authorities (CAs) to issue Digital Signature Certificates (DSC) under the IT Act 2000.
- 19. 5 Legal recognition of [electronic signature]. Where any law provides that information or any other matter shall be authenticated by affixing the signature or any document shall be signed or bear the signature of any person, then, notwithstanding anything contained in such law, such requirement shall be deemed to have been satisfied, if such information or matter is authenticated by means of [electronic signature] affixed in such manner as may be prescribed by the Central Government. Explanation.- For the purposes of this section, "signed", with its grammatical variations and cognate expressions, shall, with reference to a person, means affixing of his hand written signature or any mark on any document and the expression "signature" shall be construed accordingly.
- 20. Examples of Electronic Signature: Examples of Electronic Signature: Biometric Information PIN Password
- 21. Legal recognition of electronic records: Sec. 5 Legal recognition of electronic records: Where any law provides that information or any other matter shall be in writing or in the typewritten or printed form, then, notwithstanding anything contained in such law, such requirement shall be deemed to have been satisfied if such information or matter is- (a) rendered or made available in an electronic form; and (b) accessible so as to be usable for a subsequent reference.
- 23. Different uses of Certificates: Class 3 Certificates used for: I. E-tendering II. E-auction III. E-procurement IV. Trademark, copyright, patent e-filing Class 2 Certificates used for: I. Income Tax filing II. EPFO online filing III. Banks-Internet Banking
- 25. Role of Certifying Authorities under IT Act: Relevant Sections: Section 17 Appointment of Controller and other officers: The Central Government may, appoint a Controller of Certifying Authorities. The Deputy Controllers and Assistant Controllers shall perform the functions assigned to them by the Controller.
- 26. Functions of Controller: Sec. 18 Functions of Controller: exercising supervision over the activities of the Certifying Authorities certifying public keys of the Certifying Authorities specifying the contents of written, printed or visual materials and advertisements that may be distributed or used in respect of a Digital Signature Certificate and the public key resolving any conflict of interests between the Certifying Authorities and the subscribers; Specifying the form and contents of Electronic Signature Certificates etc.
- 27. Obtaining a Licence from Controller Sec. 21. License to issue Digital Signature Certificates:- Any person may make an application to the Controller for a license to issue Digital Signature Certificates. (2) No license shall be issued under sub-section (1), unless the applicant fulfills such requirements with respect to qualification, expertise, manpower, financial resources and other infrastructure facilities. (3) A license granted under this section shall- (a) be valid for such period as may be prescribed by the Central Government; (b) not be transferable or heritable; (c) be subject to such terms and conditions as may be specified by the regulations.
- 28. Sec. 22. Application for license. – Sec. 22. Application for license. – (1) Every application for issue of a license shall be in such form as may be prescribed by the Central Government. (2) Every application for issue of a license shall be accompanied by- a certification practice statement; payment of such fees, not exceeding twenty-five thousand rupees as may be prescribed by the Central Government; such other documents, as may be prescribed by the Central Government .
- 29. Renewal, Rejection & Grant of license 23. Renewal of license – An application for renewal of a license shall be- (a) in such form; (b) accompanied by such fees, not exceeding five thousand rupees, as may be prescribed by the Central Government and shall be made not less than forty- five days before the date of expiry of the period of validity of the license. 24. Procedure for grant or rejection of license.- The Controller may, on receipt of an application under sub-section (1) of section 21, after considering the documents accompanying the application and such other factor, as he deems fit, grant the license or reject the application: Provided that no application shall be rejected under this section unless the applicant has been given a reasonable opportunity of presenting his case.
- 30. Sec. 25. Suspension of license. – 25. Suspension of license. – For providing incorrect or false in material particulars; Failure to comply with the terms and conditions subject to which the license was granted; Contravened any provisions of this Act, rule, regulations or order made thereunder; Note: reasonable opportunity necessary to be given. Provided that no license shall be suspended for a period exceeding ten days unless the Certifying Authority has been given a reasonable opportunity of showing cause against the proposed suspension:
- 31. Notice of suspension revocation of license.- 26. Notice of suspension or revocation of license.- (1) Where the license of the Certifying Authority is suspended or revoked, the Controller shall publish notice of such suspension or revocation, as the case may be, in the database maintained by him. (2) Where one or more repositories are specified, the Controller shall publish notices of such repositories: Provided that the database containing the notice of such suspension or revocation, as the case may be, shall be made available through a web site which shall be accessible round the clock:
- 32. Display & Surrender of license: 32. Display of license.- Every Certifying Authority shall display its license at a conspicuous place of the premises in which it carries on its business. 33. Surrender of license. – (1) Every Certifying Authority whose license is suspended or revoked shall immediately after such suspension or revocation, surrender the license to the Controller. (2) Where any certifying authority fails to surrender a license under sub- section (1), the person in whose favor a license is issued, shall be guilty of an offences and shall be punished with imprisonment which may extend upto six months or a fine which may extend upto ten thousand rupees or with both.
- 33. Certifying authority to issue Electronic Signature Certificate. – 35. Certifying authority to issue Digital Signature Certificate. – (1) Any person may make an application fee not exceeding twenty-five thousand rupees Every such application shall be accompanied by a certification practice statement. It may grant the Digital Signature Certificate or for reasons to be recorded in writing, reject the application. Conditions: The applicant holds the private key corresponding to the public key to be listed in the Digital Signature Certificate. The applicant holds a private key, which is capable of creating a digital signature; The public key to be listed in the certificate can be used to verify a digital signature affixed by the private key held by the applicant: reasonable opportunity of showing cause against the proposed rejection- Mandatory.
- 34. Suspension of Digital Signature Certificate. 37. Suspension of Digital Signature Certificate. – on receipt of a request to that effect from: the subscriber listed in the Digital signature Certificate; or any person duly authorized to act on behalf of that subscriber; if it is of opinion that the Digital Signature Certificate should be suspended in public interest. A Digital Signature Certificate shall not be suspended for a period exceeding fifteen days unless the subscriber has been given an opportunity of being heard in the matter.
- 35. Revocation of Digital Signature Certificate:- 38. Revocation of Digital Signature Certificate. – (1) A Certifying Authority may revoke a Digital Signature Certificate issued by it- I. where the subscriber or any other person authorized by him makes a request to that effect; or II. upon the death of the subscriber; or III. upon the dissolution of the firm or winding up of the company where the subscriber is a firm or a company.

















![5 Legal recognition of [electronic
signature].
Where any law provides that information or any other matter shall be
authenticated by affixing the signature or any document shall be
signed or bear the signature of any person, then, notwithstanding
anything contained in such law, such requirement shall be deemed to
have been satisfied, if such information or matter is authenticated by
means of [electronic signature] affixed in such manner as may be
prescribed by the Central Government.
Explanation.- For the purposes of this section, "signed", with its
grammatical variations and cognate expressions, shall, with reference
to a person, means affixing of his hand written signature or any mark
on any document and the expression "signature" shall be construed
accordingly.](https://image.slidesharecdn.com/digitalsignatures-180806165214/85/Digital-signatures-19-320.jpg)















