Droid echo
- 1. DroidEcho: an in-depth dissection of malicious behaviors in Android applications Presented by Athira K A MCA S5 Regular Guided by Asst.prof Shimi P S MCA Department SNGCE 1
- 2. 28
- 3. 3 Some 343 new Android malware samples every hour in 2018 over 3 million new Android malware samples discovered An average of 8,225 new malware samples for the Android operating system every day 2017: 700,000 malicious apps on Google Play Android still the dominant operating system Security incidents require a rethink
- 4. DROID ECHOA PRESENTATION BY ATHIRA K A
- 5. Presentation overview Introduction • An introduction section for the topic SECTION 2 • Section The inter- component communication graph describes a representation for Android applications. Section 1 • Section semantic model of attack explains abstract models for various attacks in android . 5
- 6. Presentation overview Section 3 • Section System design of DroidEcho Section 5 • Section Conclusion concl udes this work. Section 4 • Section discusses the experiments on approach. 6
- 7. Nowadays, android malware detection is facing two critical challenges: 1) How to design a precise and efficient model to represent malware; 2) how to reduce false alarms and distinguish real malware from benign applications Android malware varies in many aspects such as • Attack targets • Attack methods • And applied techniques For example, android malware may steal users’ sensitive information , elevate their privilege, deplete device resources and remote control users’ devices 7 INTRODUCTION
- 8. o Malware may accomplish attack missions either individually or collaboratively, perform attacks only once or periodically and be triggered by the installation or a broadcast message. o Malware may adopt several mechanisms to bypass the detection of security analysts and antivirus software.. o It is challenging to eliminate greyware from malware o Detection based on an imprecise malicious behavior model would lead to a high false positive rate 8
- 9. A precise representation for attacks can benefit the detection of Malware in both accurantly and efficiently Still far from expectation to describe attacks precisely on the android platform. In addition, malware searching in applications with static approaches is not easy. New features on android, such as communication mechanisms, introduce new challenges and difficulties for attack detection. 9
- 10. To overcome the above challenges, the authors proposed an integrated framework called DROIDECHO to analyze Android applications 10
- 11. DroidEcho Abstract attack models to precisely capture the semantics of various Android attacks Transform Android applications into a comprehensive graph. With the guidance of the attack models, there is a static searching approach to detect attacks hidden in ICCG. To reduce false positive rate,there will be an additional dynamic confirmation step to check whether the detected attacks are false alarms. 11
- 12. The dynamic execution reproduces the occurrence of attacks, and makes the attack detection more precise. To sum up, this paper make the following contributions: Attack model Accurate attack detection approach Attack Confirmation Evaluation 12
- 13. Semantic model of attack 13
- 14. Building blocks Assets •Assets are referred to hardware, software and information on Android devices, which are the targets of attacks. • An attack is composed of: assets, which are the targets of attacks; actions, the execution operations performed on assets, and triggers, of which one entrance to the app that leads to the attack behaviors • An attack has its unique features and characteristics. • It has a variety of attack targets, and includes a sequence of actions Types • Information Assets: Identity code, Contact, SMS messages, File system, Location, System setting, etc. • Software Assets: Phone service, SMS service, Package Manager, Download Manager, Broadcast service, etc. • Hardware Assets: Camera, Media, Sensor, etc. 14
- 15. Actions Triggers • Triggers are events which are taken as inputs to an application and lead to the occurrence of a behavior. An attack action is an operation performing on a certain asset with the purpose of acquisition, tampering and interception, e.g., to fetch the IMEI code of the mobile phone. Types • User Interaction. • Environmental Input 15
- 16. Attack models Based on the aforementioned building blocks for an attack,defined different attacks in this section. 16
- 17. Privacy leakage sensitive transmission flow of data and is generated during the interaction between users and devices. Such sensitive transmission flow transfers sensitive data If there exists a data flow from the return value of the acquire action to the data sent out to the external environment by a communication action, usually called sink, privacy leakage happens. Service abuse Malicious applications may abuse the services provided by Android. According to investigation, the most prevailing services which are abused include phone service, SMS service, package manager, and download manager 17
- 18. Information interception • Mobile devices can interact with the external environment in many ways. However, malicious applications intercept the communication, suspend, or even break off the communication. Content tampering © Malicious applications may tamper content on mobile devices. © It can cause severe damages to the user. © An application can insert, update and delete an item in a content provider with specific permissions. © In addition, it can change system settings such as network connection, wallpaper and sleep time © The trigger of this attack will not give rise to users attention and does not have any data flow relationship with these actions 18
- 19. Attack Percent Supported by DroidEcho Privacy Leakage 31.4 ✓✓ Information Interception 11.6 ✓✓ Content Tampering 13.4 ✓✓ Service Abuse 31.4 ✓✓ Resource Depletion 1.8 ✓✓ Phishing 1.7 ✗ Adware 2.3 ✗ The category of attacks on Android 19
- 20. The inter-component communication graph For an accurate representation of Android applications and the convenience of attack detection, this section presents the inter- component communication graph (ICCG) to capture all possible communications between components and threads inside Android applications. 20
- 21. Definition 1 Let M be the communication medium existing on Android. An ICCG is a directed graph defined as G={V,E f ,E c },where V is a set of nodes; E f :V×V is a set of flow edges; and E c:V×M×V is a set of communication edges. The nodes of a graph are the methods contained in the application, which come with two levels of granularity The grained nodes only represent the signature of the functions, and help to express the relationship between functions in the system level. 21
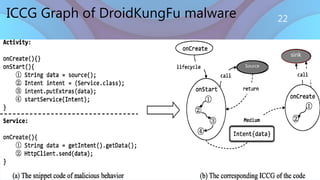
- 22. ICCG Graph of DroidKungFu malware More Expensive Less Convenient More Convenient Source sink 22
- 23. System design of DroidEcho 23
- 24. The Architecture Of The System 24
- 25. Disclaimer learning Some Android applications may perform seemingly suspicious behaviors while they are actually demanded to accomplish the functionality. The demanded functionality and the risks it may bring are usually claimed in their descriptive text We regard this as a benign behavior (henceforth disclaimer), and it will not be considered as an attack candidate. 25
- 26. ICCG Construction DROIDECHO proceeds in three steps successively: pointer analysis, link analysis and graph assembling. The first two steps can provide all auxiliary information to assemble an ICCG. Pointer analysis is a static analysis to infer which variables are pointed by pointer references or heap references. The result of this step is a PointerTable. Link analysis is to establish all links between methods or components in an application, i.e., the edges in ICCG 26
- 27. Graph assembling DROIDECHO employs Soot to generate a rough call graph of the whole application and a control flow graph for each method By far, we have obtained the control flow graph for each method of the application, and all links between these methods We take the control flow graphs as nodes, the links as edges, and assemble them into an ICCG The graph depicts the execution order and communications between different methods at the system level, and illustrates the control flow at the method level. Combined with PointerTable, ICCG is passed to the attack detection phase. Attack detection will search the graph and find out any existing attack. 27
- 28. Attack detection To reduce the search space of attack detection, we will not analyze the program from its entry points. In converse, we first recognize attack-related actions existing in the program in a fast way, and perform a bidirectional flow analysis from behaviors, which can effectively speedup the search process. 28
- 29. If all actions in the attack model are found in ICCG, it will proceed the reachability analysis and program slicing. At last,it get the trigger causing this attack , and check if it is a kind of environmental input, e.g., the initialization of application, system broadcast message and a timer task. Action recognition 29
- 30. Reachability analysis & slicing If the ICCG contains all necessary elements for one attack, we start to do program slicing from these elements The slicing consists of backward and forward control flow analysis. The backward control flow analysis:Find the root cause that lead to such action,Obtain all conditions in a trace from the entry points to the action,Identify the search space for potential taint analysis. The forward control flow analysis :determine the occurrence of the subsequent actions in an attack model,Identify the search space for the taint analysis Taint analysis Taint analysis can track the flow of data to detect flow based vulnerabilities during detection. 30
- 31. Dynamic attack confirmation DROIDECHO’s ICCG construction and attack detection are based on static program analysis, which is less precise than dynamic analysis Authors introduced a confirmation step to reduce false positives, and the attack confirmation is based on the technique of dynamic testing. In order to activate the attack candidate and capture malicious behaviors, we first instrument Android OS by hooking specific Android APIs which are included in our attack model, and then generate the triggers which are used to activate the contained malicious behaviors 31
- 32. Evaluation on real Apps They have collected 7643 applications from Google Play, which are hot and free application in their respective categories By running DROIDECHO,found out 444 applications which have malicious behaviors. In addition,have done a statistics of behaviors which are user-awared already claimed by the description of applications. They compare DROIDECHO with other anti-virus (AV) tools, by uploading apk files into VirusTotal Although AV tools have detected 1541 (20.2%) samples of malware, most of them are Adware, of which the number is up to 1217 (79.0%). 32
- 33. Privacy leakage via 3rd-libraries Library Description Num Behaviors Adobe Measurement of Usage 1 Identity Code, etc. Flurry Measurement of Usage 20 Identity Code, Location, Conversant Measurement of Usage 1 Identity Code, Location, Crashlytics Diagnosis of Crash 8 Identity Code, Sys. Info, etc. Map Service Map Service 5 Location, etc. Crittercism Optimization Tool 1 Identify Code, etc. Umeng Advertisement 4 Identity Code, Location, Google Ads Advertisement 3 Identity Code, Location, Amazon Ads Advertisement 1 Identity Code, Locatoin, Millennialmedia Advertisement 2 Identity Code, Location, 33
- 34. • In this paper, The authors introduced a novel attack model to depict the essential characteristics and features. In addition,they build a transformation from an Android application to a directed graph, called the inter-component communication graph. ICCG captures all structure information of application, including call relationships and communication between different methods, and it contains all control flow information for each method. The approach is proved to be feasible and effective in the experiments. In future, they expect to propose an algorithm to handle more complicated obfuscation or encryption techniques, and will continue enriching the attack model in order to handle more variants or new attacks. Conclusion 34
- 35. 35 References • Guozhu Meng,Ruitao Feng,Guangdong Bai,Kai Chen ,Yang Liu DroidEcho: an in-depth dissection of malicious behaviors in Android applications https://link.springer.com/article/10.1186/s42400-018-0006-7 • Trojan:Android/DroidKungFu.C http://www.f-secure.com/v-descs/trojan_android_droidkungfu_c.shtml https://github.com/secure-software-engineering/DroidBench • Arzt, S, Bodden E (2016) StubDroid: Automatic Inference of Precise Data- flow Summaries for the Android Framework In: Proceedings of the 38th International Conference on Software Engineering, 725–735.