Hardening Three - IDS/IPS Technologies
- 1. HARDENING IDS/IPS Technologies Salvatore Lentini Davide Antonino Vincenzo Micale Hardening Three University of Catania 29 May 2017
- 2. 2 Summary ● Problems ● Arp spoofing ● Video with Netcat Backdoor ● Ping out of network ● Attempt access and Http Bruteforce ● Tools: ● Snort IDS/IPS ● Suricata IDS/IPS ● PulledPork ● Barnyard2 ● Base ● Some theoretical concepts Hardening ThreeUniversity of Catania
- 3. 3 First Scenario Ping out of network We are an Network Administrator and don’t want that someone to ping from out of network our hosts into our network (HOME_NET) So, we want know who execute the ping University of Catania Hardening Three
- 4. 4 Ping Detected University of Catania sudo nano snort -c /etc/snort/snort.conf -A console -i ens38 Detected ICMP Ping Hardening Three
- 5. 5 Ping out of Network Prevention University of Catania Hardening Three
- 6. 6 Ping out of Network Prevention University of Catania sudo snort -c /etc/snort/snort.conf -i ens38:ens39 -Q -A console -q Hardening Three
- 7. 7 Possible problem University of Catania Did you have this error? Don't worry. This is an IPS then it want more memory! You need add more memory your virtual machine Hardening Three
- 8. 8 Video with Netcat Backdoor ● Seems a video, but…… DEMO Hardening ThreeUniversity of Catania Hardening Three
- 9. 9 “It’s dangerous, so dangerous” ● The file is a Self Extracting WinRar(SFX) archive containing: ● Video ● Netcat ● Caller.vbs: on execute, run Netcat on a specific port opening the shell calling the attacker. Open the video Hardening ThreeUniversity of Catania Hardening Three
- 10. 10 Creation of the archive ● “Compression method”: select “Store” ● “Archiving option”: check “Create SFX archive ● On tab “Advanced” → “SFX options” ● On tab “General” → “Path to Extract”: “C:virus” and tick “Absolute path” ● On tab “Setup” → “Setup program/Run after extraction”: “caller.vbs” ● On tab “Modes” → “Silent mode”: tick “Hide all” ● On tab “Update” → “Overwrite mode”: tick “Skip existing files” ● On tab “Text and icon” → “Load SFX icon from the file”: select a .ico file containing the video icon. University of Catania Hardening Three
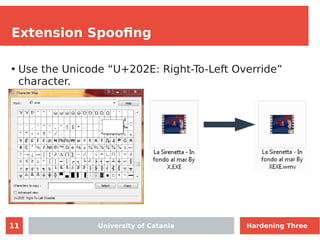
- 11. 11 Extension Spoofing ● Use the Unicode “U+202E: Right-To-Left Override” character. University of Catania Hardening Three
- 12. 12 Attacker side ● Run netcat on listen mode on the specific port ● Wait until the victim play the fake video University of Catania Hardening Three
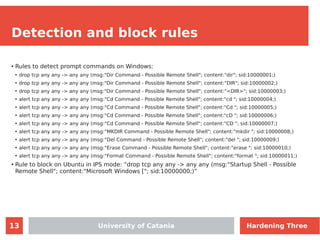
- 13. 13 Detection and block rules ● Rules to detect prompt commands on Windows: ● drop tcp any any -> any any (msg:"Dir Command - Possible Remote Shell"; content:"dir"; sid:10000001;) ● drop tcp any any -> any any (msg:"Dir Command - Possible Remote Shell"; content:"DIR"; sid:10000002;) ● drop tcp any any -> any any (msg:"Dir Command - Possible Remote Shell"; content:"<DIR>"; sid:10000003;) ● alert tcp any any -> any any (msg:"Cd Command - Possible Remote Shell"; content:"cd "; sid:10000004;) ● alert tcp any any -> any any (msg:"Cd Command - Possible Remote Shell"; content:"Cd "; sid:10000005;) ● alert tcp any any -> any any (msg:"Cd Command - Possible Remote Shell"; content:"cD "; sid:10000006;) ● alert tcp any any -> any any (msg:"Cd Command - Possible Remote Shell"; content:"CD "; sid:10000007;) ● alert tcp any any -> any any (msg:"MKDIR Command - Possible Remote Shell"; content:"mkdir "; sid:10000008;) ● alert tcp any any -> any any (msg:"Del Command - Possible Remote Shell"; content:"del "; sid:10000009;) ● alert tcp any any -> any any (msg:"Erase Command - Possible Remote Shell"; content:"erase "; sid:10000010;) ● alert tcp any any -> any any (msg:"Format Command - Possible Remote Shell"; content:"format "; sid:10000011;) ● Rule to block on Ubuntu in IPS mode: “drop tcp any any -> any any (msg:"Startup Shell - Possible Remote Shell"; content:"Microsoft Windows ["; sid:10000000;)” University of Catania Hardening Three
- 14. 14 Second Scenario Attempt of login Now, we want to know who attempted login on our web server University of CataniaUniversity of Catania Hardening Three
- 15. 15 Traffic Analisys University of Catania In our rule we can use this one to detect traffic University of Catania Hardening Three
- 16. 16 Attempt access Detected University of Catania Detected Attempt of Login University of Catania Hardening Three
- 17. 17 Http Bruteforce University of Catania Our credentials University of Catania Hardening Three
- 18. 18 Http Bruteforce Detected University of CataniaUniversity of Catania Hardening Three
- 19. 19 Http Bruteforce Prevention University of CataniaUniversity of Catania Hardening Three
- 20. 20 Http Bruteforce Snort as IPS with nft University of Catania sudo snort -Q -–daq nfq -–daq-mode inline -–daq-var queue=0 -c /etc/snort/snort.conf -A console -q ? It’s a inline modality on Linux using Netfilter 1 2 Orderexecution University of Catania Hardening Three Triggeredrule
- 21. 21 ARP Spoofing “ALL YOUR PACKETS ARE BELONG TO US” DEMO University of Catania Hardening Three
- 22. 22 ARP ● ARP(Address Resolution Protocol): bind the IP address to the MAC address of the devices inside the LAN A B C Switch University of Catania Hardening Three
- 23. 23 Ping ● Goal: A ping B ● ARP, Request who-has 192.168.18.3 tell 192.168.18.1 ● ARP, Reply 192.168.18.3 is-at 00:0C:29:6C:54:28 University of Catania Hardening Three
- 24. 24 ARP Cache ● ARP Cache: table with the associations IP → MAC ● The associations will be deleted periodically ● The device will accept any ARP reply in ANY time! ● No authenticity control of the association IP MAC 192.168.18.3 00:0C:29:6C:54:28 University of Catania Hardening Three
- 25. 25 MITM with ARP Poisoning ● The attacker can sniff the victim packets ● The attacker send on the LAN ARP Reply for each device ● “ARP, Reply X.X.X.X is-at Y:Y:Y:Y” where Y:Y:Y:Y is the attacker MAC address ● Let’s C the attacker and B the victim ● ARP, Reply 192.168.18.3 is-at 00:0C:29:B0:C9:71 ● ARP, Reply 192.168.18.1 is-at 00:0C:29:B0:C9:71 University of Catania Hardening Three
- 26. 26 ARP Cache after the poisoning ● A table ● B table IP MAC 192.168.18.3 00:0C:29:B0:C9:71 IP MAC 192.168.18.1 00:0C:29:B0:C9:71 University of Catania Hardening Three
- 27. 27 ARP Cache after the poisoning - Continue ● The attacker need to ARP spoofing very often ● Every packet of the victim will be seen by the attacker A C B University of Catania Hardening Three
- 28. 28 Ettercap ● “Ettercap is a comprehensive suite for man in the middle attacks.” ● Man in the middle could be accomplished using the -M arp mode ● The attacker must activate the promiscous mode ● “ettercap -T -i IF -M arp /IP_VICTIM//” University of Catania Hardening Three
- 29. 29 Run Ettercap 1) Scan the devices of the LAN 2) ARP Poisoning University of Catania Hardening Three
- 30. 30 Sniffing web navigation ● The attacker can sniff the victim web navigation A Gateway Switch B C Internet ens33 ens39 University of Catania Hardening Three
- 31. 31 Password sniffing ● The victim go in a HTTP web page ● The attacker catch Username and Password University of Catania Hardening Three
- 32. 32 IDS and the ARP spoofing ● Suricata can’t do anything to detect an ARP spoofing ● Snort can detect using the ARP Spoof Preprocessor University of Catania Hardening Three
- 33. 33 Snort detection ARP spoofing ● Modify /etc/snort/snort.conf ● Uncomment “preprocessor arpsoof” ● For each devices of the LAN, add “preprocessor arpspoof_detect_host: IP MAC” ● Uncomment “include $PREPROC_RULE_PATH/preprocessor.rules” ● Download the preprocessor rules in the Snort website and save it on the file “/etc/snort/preproc_rules/preprocessor.rules” University of Catania Hardening Three
- 34. 34 Configuration of the Gateway 1)Promiscous mode: every packet will be read by the network interface(whatever it is the destinatary of the packet) 2)Masquerade: every packet transmitted outside through the specific network interface will have the IP Sender set to the gateway IP University of Catania Hardening Three
- 35. 35 Installation and Configuration University of Catania Hardening Three
- 36. 36 Virtual Network ● VMware Workstation ● No DHCP University of Catania (NAT) INTERNET 192.168.232.1 192.168.232.0/24 192.168.232.2 192.168.248.1 192.168.248.2 192.168.248.0/24 University of Catania Hardening Three
- 37. 37 Create Networks Open Virtual Network Editor: ● Add 2 networks vmnet11 ● Host-Only ● 192.168.232.0 ● 255.255.255.0 vmnet12 ● Host-Only ● 192.168.248.0 ● 255.255.255.0 NO DHCP! University of CataniaUniversity of Catania Hardening Three
- 38. 38 Router University of Catania Router (Ubuntu) Add 2 Network Adapter (total) → NAT → Custom: vmnet11 → Custom: vmnet12 sudo nano /etc/network/interfaces auto ens38 iface ens38 inet static address 192.168.232.1 netmask 255.255.255.0 auto ens39 iface ens39 inet static address 192.168.248.1 netmask 255.255.255.0 sudo nano /etc/sysctl.conf (take off #) net.ipv4.ip_forward=1 sudo /etc/init.d/networking restart sudo reboot University of Catania Hardening Three
- 39. 39 Hosts University of Catania Victim (Ubuntu) Add 1 Network Adapter (total) → NAT → Custom: vmnet11 Attacker (Kali Linux) Add 1 Network Adapter (total) → NAT → Custom: vmnet12 sudo nano /etc/network/interfaces auto eth0 iface eth0 inet static address 192.168.232.2 netmask 255.255.255.0 gateway 192.168.232.1 sudo /etc/init.d/networking restart sudo nano /etc/network/interfaces auto ens38 iface ens38 inet static address 192.168.248.2 netmask 255.255.255.0 gateway 192.168.248.1 sudo /etc/init.d/networking restart University of Catania Hardening Three
- 40. 40 Apache Web Server University of Catania In victim machine we must install Apache sudo apt-get install apache2 apache2-utils sudo su cd /var/www/html echo “This is victim webserver” > index.html nano /etc/apache2/site-available/000-default.conf University of Catania Hardening Three
- 41. 41 Apache Web Server University of CataniaUniversity of Catania Hardening Three
- 42. 42 Apache Web Server University of Catania htpasswd -c /etc/apache2/.htpasswd web (insert new password for “web” user ) sudo /etc/init.d/networking restart sudo /etc/init.d/apache2 restart #After this configuration, disable the NAT interface University of Catania Hardening Three
- 43. 43 Configuration Snort IDS on Router Automatic Installation on Linux Install Snort sudo apt-get install snort * Put the network interface of the network that we want to defend (ens39) * the network address (192.168.248.0/24) Test Installation sudo snort -V Configuration sudo nano /etc/snort/snort.conf (with the automatic installation you have to modified only HOME_NET inserting the network that you want defend) Test Configuration sudo snort -c /etc/snort/snort.conf (If start the sniffing mode, it’s a good thing!) University of CataniaUniversity of Catania Hardening Three
- 44. 44 Create the custom rules file sudo touch /etc/snort/rules/custom.rules sudo nano /etc/snort/snort.conf *include custom.rules in the snort.conf Write the rules sudo nano /etc/snort/rules/custom.rules In rules folder you can put other rules that you can download from Snort site. University of CataniaUniversity of Catania Hardening Three
- 45. 45 Some commands to execute snort IDS Verbose mode snort -v Using configuration file and show alert on the terminal snort -c /etc/snort/snort.conf -A console -i ens38 Log mode sudo snort -c /etc/snort/snort.conf -A console -i ens38 -l /var/log/snort -k ascii University of CataniaUniversity of Catania Hardening Three
- 46. 46 Configuration Snort IPS manual installation Install dependencies sudo su sudo apt-get install libdnet && apt-get install build-essential && apt-get install bison flex && apt-get install libpcap-dev && apt-get install libpcre3-dev && apt-get install libnet1-dev && apt-get install zlib1g-dev && apt-get install libnetfilter-queue-dev # daq: nfq && apt-get install libmnl-dev && apt- get install libnfnetlink-dev && apt-get install libnetfilter-queue-dev && apt-get install checkinstall sudo apt-get update sudo apt-get upgrade Create Tmp directory mkdir -p /tmp/snort-install/ cd /tmp/snort-install/ Download in this folder daq from the Snort Site Download in this folder libdnet.1.11 University of CataniaUniversity of Catania Hardening Three
- 47. 47 Configuration Snort IPS manual installation Install libdnet tar -xvf libdnet-1.11.tar.gz ./configure “CFLAGS=-fPIC” make sudo checkinstall -y sudo dpkg -i libdnet-1.11-1.amd64.deb sudo ln -s /usr/local/lib/libdnet.1.0.1 /usr/lib/libdnet.1 Install daq (Download and Extract daq) in /tmp/snort-install/ ./configure make sudo checkinstall -y sudo dpkg -i daq_2.0.6-1_amd64.deb University of CataniaUniversity of Catania Hardening Three
- 48. 48 Snort as IPS with AFPACKET Enable DAQ in AFPACKET sudo nano /etc/snort/snort.conf University of Catania ? It’s a inline modality on Linux using two bridged interfaces University of Catania Hardening Three
- 49. 49 Installing Suricata on Windows 1) Install WinPcap from https://www.winpcap.org/install/ 2) Install Suricata from https://suricata-ids.org/download/ 3) Place rules into C:Program FilesSuricatarules or C:Program Files (x86)Suricatarules 4) Modify the Suricata configuration file C:Program FilesSuricatasuricata.yaml or C:Program Files (x86)Suricatasuricata.yaml settings ● Home Network ● External Network ● Rule Files ● (In Windows 32 bit) Suricata Folder University of Catania Hardening Three
- 50. 50 Run Suricata on Windows 1)“Run as administrator” Prompt command 2) Run the command “suricata.exe -c suricata.yaml -i IPHOST” 3) In C:Program FilesSuricatalogfast.log C:Program Files (x86)Suricatafast.log contains the logs University of Catania Hardening Three
- 51. 51 Installing Suricata in IPS mode on Ubuntu 1) On terminal: “sudo apt-get install suricata” 2) Place rules into /etc/suricata/rules 3) Modify the Suricata configuration file /etc/suricata/suricata.yaml settings ● Home Network ● External Network ● Rule Files 4) On terminal: “sudo iptables -I FORWARD -j NFQUEUE” University of Catania Hardening Three
- 52. 52 Run Suricata on Linux IPS mode 1) Run the command “sudo suricata -c suricata.yaml -q 0” 2) /var/log/suricata/fast.log contains the logs University of Catania Hardening Three
- 53. 53 Barnyard2 ● Parsing and processing of snort log(unified2 format file) and output it in other output: ● Storing on database(PostgreSQL or MySql/MariaDB) ● Talk to Sguil daemon ● Talk to SnortSam University of Catania Hardening Three
- 54. 54 Installing Barnyard2 with MySql/MariaDB on Ubuntu 17.04 ● sudo apt-get install mysql-server libmysqlclient-dev mysql-client autoconf libtool ● Set the MySql root password ● Be sure to have libdumbnet-dev libpcap-dev bison flex packages and to install the DAQ ● Be sure to have the sid-msg.map file on /etc/snort ● Be sure the custom rules have the “rev” field ● Modify the Snort configuration file adding: “output unified2: filename snort.u2, limit 128” University of Catania Hardening Three
- 55. 55 Installing Barnyard2 - Continue ● Install Barnyard2: ● wget https://github.com/firnsy/barnyard2/archive/master.tar.gz -O barnyard2-Master.tar.gz ● tar zxvf barnyard2-Master.tar.gz ● cd barnyard2-master ● autoreconf -fvi -I ./m4 ● sudo ln -s /usr/include/dumbnet.h /usr/include/dnet.h ● sudo ldconfig ● ./configure --with-mysql --with-mysql-libraries=/usr/lib/x86_64-linux-gnu ● make ● sudo make install ● Put barnyard2 configuration file in Snort folder: sudo cp etc/barnyard2.conf /etc/snort/ ● Create barnyard2 log folder and file. Make them belong to Snort user and Snort Group: ● sudo mkdir /var/log/barnyard2 ● sudo chown snort.snort /var/log/barnyard2 ● sudo touch /var/log/snort/barnyard2.waldo ● sudo chown snort.snort /var/log/snort/barnyard2.waldo University of Catania Hardening Three
- 56. 56 Installing Barnyard2 - Continue ● Create the Barnyard2 database using the commands preinstalled and create the Snort user of the database. Be sure to change “PASSWORD” with a secure password: ● mysql -u root -p ● mysql> create database snort; ● mysql> use snort; ● mysql> source schemas/create_mysql ● mysql> CREATE USER 'snort'@'localhost' IDENTIFIED BY 'PASSWORD'; ● mysql> grant create, insert, select, delete, update on snort.* to 'snort'@'localhost'; ● mysql> exit ● Modify barnyard2 configuration file /etc/snort/barnyard2.conf adding(Be sure to change “PASSWORD” with the previous password): “output database: log, mysql, user=snort password=PASSWORD dbname=snort host=localhost sensor name=sensor01” ● Remove others read permission of the barnyard2 file: “sudo chmod o-r /etc/snort/barnyard2.conf” University of Catania Hardening Three
- 57. 57 Run Snort and Barnyard2 ● Run Snort: “sudo snort -u snort -g snort -c /etc/snort/snort.conf -i INTERFACE” ● Run Barnyard2: “sudo barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.u2 -w /var/log/snort/barnyard2.waldo -g snort -u snort” University of Catania Hardening Three
- 58. 58 Installing BASE on Ubuntu 17.04 ● BASE is a PHP frontend for Barnyard2 log database ● Permit to analyse the logs with a graphical interface ● Install the no more supported PHP 5.6: ● sudo add-apt-repository ppa:ondrej/php ● sudo apt-get update ● sudo apt-get install -y apache2 libapache2-mod-php5.6 php5.6-mysql php5.6-cli php5.6 php5.6-common php5.6-gd php5.6-cli php-pear php5.6-xml ● Install Pear image Graph: “sudo pear install -f --alldeps Image_Graph” ● Install ADODB: ● wget https://sourceforge.net/projects/adodb/files/adodb-php5-only/adodb-520-for-php5/adodb-5.20.8.tar.gz ● tar -xvzf adodb-5.20.8.tar.gz ● sudo mv adodb5 /var/adodb ● sudo chmod -R 755 /var/adodb ● Download BASE and copy on the Apache web folder: ● wget http://sourceforge.net/projects/secureideas/files/BASE/base-1.4.5/base-1.4.5.tar.gz ● tar xzvf base-1.4.5.tar.gz ● sudo mv base-1.4.5 /var/www/html/base/ University of Catania Hardening Three
- 59. 59 Configure BASE ● Copy the default configuration file: ● cd /var/www/html/base ● sudo cp base_conf.php.dist base_conf.php ● Modify it and set(Be sure to change “PASSWORD” with the mysql snort password): ● $BASE_urlpath = '/base'; ● $DBlib_path = '/var/adodb/'; ● $alert_dbname = 'snort'; ● $alert_host = 'localhost'; ● $alert_port = ''; ● $alert_user = 'snort'; ● $alert_password = 'PASSWORD'; ● Remove others read permission of the BASE configuration file and make the BASE folder, subfolders and files belong to “www-data” user and group : ● sudo chown -R www-data:www-data /var/www/html/base ● sudo chmod o-r /var/www/html/base/base_conf.php ● Restart Apache: “sudo service apache2 restart” ● Open via Browser the URL: “http://localhost/base/index.php“ ● Click to “Setup page” ● “Create BASE AG” University of Catania Hardening Three
- 60. 60 Installing PulledPork ● PulledPork is a tool that download automatically the Snort/Suricata rules to keep they up to date and unify every rule files in a single one ● Install the dependencies: “sudo apt-get install libcrypt-ssleay-perl liblwp-useragent-determined-perl” ● Download and install PulledPork: ● wget https://github.com/shirkdog/pulledpork/archive/master.tar.gz -O pulledpork-master.tar.gz ● tar xzvf pulledpork-master.tar.gz ● cd pulledpork-master/ ● sudo cp pulledpork.pl /usr/local/bin ● sudo chmod +x /usr/local/bin/pulledpork.pl ● sudo cp etc/*.conf /etc/snort ● Modify the PulledPork configuration file /etc/snort/pulledpork.conf: ● Comment or insert the Oinkcode in order to download the Oinkcode ● Uncomment the rules you want download and comment the rules you don’t want ● Set the version of rules “snort_version” ● Set where to store the Snort rules (for example “snort.rules”) ● Set where are stored the custom Snort rules ● Set where is stored the sid-msg.map ● Set where is stored the Snort configuration file ● Set the distro version(in this case, Ubuntu 12.04) ● Modify the Snort configuration file. Comment every rules and add the rule “snort.rules” ● Run PulledPork: “sudo /usr/local/bin/pulledpork.pl -c /etc/snort/pulledpork.conf -l “ University of Catania Hardening Three
- 61. 61 Snort rules ● From https://www.snort.org/downloads/#rule-downloads you can download the Snort rules(rules are organized in category in rules ● Snort Community(free) ● Snort Registered(free previous registration) ● Snort Subscription(starting at 29,99 €/year) ● From EmergingThreat https://rules.emergingthreats.net/open/ (free) University of Catania Hardening Three
- 62. 62 Some Theoretical concepts on IDS and IPS University of Catania Concept of IDS was developed by James P. Anderson on 15 April in 1980 in his technical rapport An IDS or an IPS is a system that it was developed to detect typical signs of an intrusion. An IDS is similar to an anti-theft, it see the bad traffic but does not block it. An IPS is an IDS but with the behavior of a firewall. Both see until the Application layer of the packets ● NIDS/NIPS ● HIDS/HIPS ● Anomaly detection (“behavior based”) ● Misuse detection (“Signatures based”) University of Catania Hardening Three
- 63. 63 Thanks IDS/IPS Technologies Hardening three University of Catania 29 May 2017 University of CataniaUniversity of Catania Hardening Three