Honeypot Basics
- 1. HONEYPOTS HONEYPOTS BY:- Manoj Kumawat R. No. 13075029
- 2. HONEYPOTS • What is honeypot ? A honeypot is a computer security mechanism set to detect, deflect or counteract attempts at unauthorized use of information system. It’s simply a TRAP to attacker.
- 3. HONEYPOTS • How it works ? A honeypot consists of data that appears to be a legitimate part of the site but is actually isolated and monitored, and that seems to contain information or a resource of value to attackers, which are then blocked.
- 4. HONEYPOTS
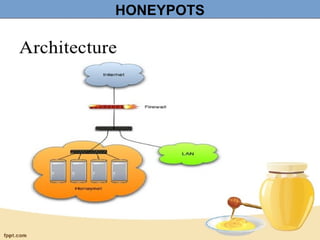
- 5. HONEYPOTS Architecture: •As a bait •Just some regular system •More attractive
- 6. HONEYPOTS
- 7. HONEYPOTS • HONEYPOT CLASSIFICATION: By Implementation • Virtual • Physical By purpose • Production • Research By level of interaction • High • Low • Middle?
- 8. HONEYPOTS • IMPLEMENTATION OF HONEYPOT: Physical • Real machines • Own IP Addresses • Often high-interactive Virtual • Simulated by other machines that: –Respond to the traffic sent to the honeypots –May simulate a lot of virtual honeypots at the same time
- 9. HONEYPOTS • PROPOSE OF HONEYPOT: Research Complex to deploy and maintain. Captures extensive information. Run by a volunteer(non-profit). Used to research the threats organization face. Production Easy to use Capture only limited information Used by companies or corporations Mitigates risks in organization
- 10. HONEYPOTS • INTERACTION LEVEL: • Low Interaction • High Interaction
- 11. HONEYPOTS • LOW INTERACTION VS. HIGH INTERACTION:
- 12. HONEYPOTS • Placement of honeypot In front of the firewall (Internet) DMZ (De-Militarized Zone) Behind the firewall (intranet)
- 13. HONEYPOTS
- 15. HONEYPOTS Prevention: •Keeping the burglar out of your house. •Honeypots, in general are not effective prevention mechanisms.
- 16. HONEYPOTS Detection: •Detecting the burglar when he breaks in.
- 17. HONEYPOTS Response: •Honeypots can be used to help respond to an incident.
- 18. HONEYPOTS