Jailbreaking iOS
- 1. Jailbreaking iOS How an iPhone breaks free Kai Aras - CSM Stuttgart Media University
- 2. What is iOS ? • Apples Operating System for iPhone, iPodTouch and iPad • Based on Mac OSX • Latest release 4.2.1
- 3. What is a Jailbreak ?
- 4. What is a Jailbreak ? • removes certain security mechanisms to allow installation and distribution of untrusted 3rd party applications.
- 5. What is a Jailbreak ? • removes certain security mechanisms to allow installation and distribution of untrusted 3rd party applications. • patches code signing to achieve unsigned code execution
- 6. What is a Jailbreak ? • removes certain security mechanisms to allow installation and distribution of untrusted 3rd party applications. • patches code signing to achieve unsigned code execution • makes you play angry birds for free...
- 7. Why does it exist ? • Closed Platform • Software Distribution controlled by Apple (walled garden) • 3rd party developers cannot modify system components • 3rd party developers can only use public APIs • people enjoy hacking things ;)
- 8. What about the name - Jailbreak ? • seems to be originated in first hackers breaking out of the so called chroot jail.
- 9. What can be done with a JB ?
- 10. What can be done with a JB ? • Install software that is unsupported by Apple.
- 11. What can be done with a JB ? • Install software that is unsupported by Apple. • Apps, Addons, Themes
- 12. What can be done with a JB ? • Install software that is unsupported by Apple. • Apps, Addons, Themes • Activate the Device (unofficial carriers)
- 13. What can be done with a JB ? • Install software that is unsupported by Apple. • Apps, Addons, Themes • Activate the Device (unofficial carriers) • Unlock the device.
- 14. What can be done with a JB ? • Install software that is unsupported by Apple. • Apps, Addons, Themes • Activate the Device (unofficial carriers) • Unlock the device. • Do custom development that requires deeper system integration.
- 15. What can be done with a JB ? • Install software that is unsupported by Apple. • Apps, Addons, Themes • Activate the Device (unofficial carriers) • Unlock the device. • Do custom development that requires deeper system integration. • Install pirated software ☹
- 16. A state of the art prison iOS Hardware and Software Design
- 18. iOS Hardware Architecture Application Processor
- 19. iOS Hardware Architecture Application Processor iOS User interaction Applications ...
- 20. iOS Hardware Architecture Application Processor iOS User interaction Applications ... Baseband Processor
- 21. iOS Hardware Architecture Application Processor iOS User interaction Applications ... Baseband Processor NucleusOS Radio communication
- 22. iOS Hardware Architecture audio WIFI display BT camera GSM Application Processor Baseband Processor UART I2S GPIO DMA power managment
- 23. iOS Hardware Architecture audio WIFI display BT camera GSM Application Processor Baseband Processor UART I2S GPIO DMA controls power managment sim/net-lock !
- 25. iOS Security Architecture • Sandboxing
- 26. iOS Security Architecture • Sandboxing • Memory protection
- 27. iOS Security Architecture • Sandboxing • Memory protection • Code signing
- 28. iOS Security Architecture • Sandboxing • Memory protection • Code signing • Encryption
- 29. Sandboxing • NAND Flash • FTL : converts logical partitions to NAND flash architecture • looks like Block Device / (RO) (System Partition) /private/var (RW) (User Partition) • System Partition / (RO) Block Device User Partition /private/var FTL NAND
- 30. Sandboxing / (RO) /private/var (RW) • (System Partition) (User Partition) System Partition read only Block Device • 3rd party lives on user partition FTL • Apps run as mobile user NAND • Kernel signature checks executables in systemcall execve()
- 31. Memory Protection • W^X Policy • a page is either writable or executable but never both! • Non-executable stack & heap • No ASLR! -> ROP
- 32. Code Signing • implemented inside the Kernel • Kernel signature checks executables in systemcall execve() • Kernel stored on System Partition (kernelcache) • Kernel is signature checked before being loaded.
- 33. Encryption • Everything is encrypted • Hardware AES Engine • Keys derived from hardware keys GID-key UID-key • Possible to use Jailbreak tools e.g. Syringe to use the hardware engine
- 34. iOS Boot Sequence • Normal Boot • Recovery Mode • DFU Mode
- 35. Normal Boot LLB Bootrom (Low Level iBoot Kernel Application Bootloader) NOR NOR NAND NAND signature signature signature signature check check check check
- 36. DFU Mode LLB Bootrom (Low Level iBoot Kernel Application Bootloader) minimal iBoot Bootrom iBSS iBEC Kernel Ramdisk
- 37. Recovery Mode LLB Bootrom (Low Level iBoot Kernel Bootloader) signature signature Kernel check check Ramdisk
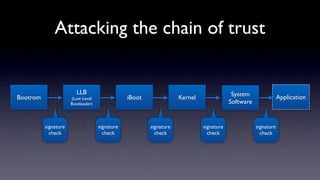
- 38. Attacking the chain of trust LLB System Bootrom (Low Level iBoot Kernel Application Bootloader) Software signature signature signature signature signature check check check check check
- 39. Attacking the chain of trust attack here LLB System Bootrom (Low Level iBoot Kernel Application Bootloader) Software signature signature signature signature signature check check check check check
- 40. Attacking the chain of trust (cannot be fixed) attack here LLB System Bootrom (Low Level iBoot Kernel Application Bootloader) Software signature signature signature signature signature check check check check check
- 41. Attacking the chain of trust (cannot be fixed) attack here attack here LLB System Bootrom (Low Level iBoot Kernel Application Bootloader) Software signature signature signature signature signature check check check check check
- 42. Attacking the chain of trust (cannot be fixed) attack here attack here attack here LLB System Bootrom (Low Level iBoot Kernel Application Bootloader) Software signature signature signature signature signature check check check check check
- 43. Attacking the chain of trust (cannot be fixed) attack here attack here attack here attack here LLB System Bootrom (Low Level iBoot Kernel Application Bootloader) Software signature signature signature signature signature check check check check check
- 44. Breaking free LLB System Bootrom (Low Level iBoot Kernel Application Bootloader) Software signature signature signature signature signature check check check check check
- 45. Breaking free 1. Patch out all the signature checks LLB System Bootrom (Low Level iBoot Kernel Application Bootloader) Software signature signature signature signature signature check check check check check
- 46. Breaking free 1. Patch out all the signature checks 2. Install Cydia to manage unsigned 3rd Cydia party applications LLB System Bootrom (Low Level iBoot Kernel Application Bootloader) Software signature signature signature signature signature check check check check check
- 47. How it’s done
- 48. How it’s done • exploit code-execution vulnerability to deploy and execute jailbreak- payload
- 49. How it’s done • exploit code-execution vulnerability to deploy and execute jailbreak- payload • execute payload, if required gain root by exploiting privilege escalation vulnerability
- 50. How it’s done • exploit code-execution vulnerability to deploy and execute jailbreak- payload • execute payload, if required gain root by exploiting privilege escalation vulnerability • patch LLB, iBoot and Kernel to remove signature checks
- 51. How it’s done • exploit code-execution vulnerability to deploy and execute jailbreak- payload • execute payload, if required gain root by exploiting privilege escalation vulnerability • patch LLB, iBoot and Kernel to remove signature checks • install cydia to allow installation of unsigned 3rd party applications.
- 53. Star (jailbreakme.com) • Web based Jailbreak
- 54. Star (jailbreakme.com) • Web based Jailbreak • Injection Vector: Userland Process (via HTTP)
- 55. Star (jailbreakme.com) • Web based Jailbreak • Injection Vector: Userland Process (via HTTP) • first exploits CFF Font Parser (via PDF) in Mobile Safari
- 56. Star (jailbreakme.com) • Web based Jailbreak • Injection Vector: Userland Process (via HTTP) • first exploits CFF Font Parser (via PDF) in Mobile Safari • then exploits IOSurface Kernel extension (via ROP)
- 57. Star 1 Payload 1 2 Payload 2 3 Mobile Safari 6 PDF CFF Font Parser 4 7 System Applicatio iBoot Kernel Cydia Software n 5
- 58. Star 1 Payload 1 2 1. Payload1: Malformed PDF Payload 2 3 Mobile Safari 6 PDF CFF Font Parser 4 7 System Applicatio iBoot Kernel Cydia Software n 5
- 59. Star 1 Payload 1 2 1. Payload1: Malformed PDF Payload 2 3 Mobile 2. Payload2: Post Install Safari 6 PDF CFF Font Parser 4 7 System Applicatio iBoot Kernel Cydia Software n 5
- 60. Star 1 Payload 1 2 1. Payload1: Malformed PDF Payload 2 3 Mobile 2. Payload2: Post Install Safari 6 PDF CFF Font Parser 4 3. Deploy Payload1 via HTTP 7 System Applicatio iBoot Kernel Cydia Software n 5
- 61. Star 1 Payload 1 2 1. Payload1: Malformed PDF Payload 2 3 Mobile 2. Payload2: Post Install Safari 6 PDF CFF Font Parser 4 3. Deploy Payload1 via HTTP 7 System Applicatio iBoot Kernel Cydia Software n 4. Exploit Userland Process 5
- 62. Star 1 Payload 1 2 1. Payload1: Malformed PDF Payload 2 3 Mobile 2. Payload2: Post Install Safari 6 PDF CFF Font Parser 4 3. Deploy Payload1 via HTTP 7 System Applicatio iBoot Kernel Cydia Software n 4. Exploit Userland Process 5. Exploit Kernel to gain root privileges 5
- 63. Star 1 Payload 1 2 1. Payload1: Malformed PDF Payload 2 3 Mobile 2. Payload2: Post Install Safari 6 PDF CFF Font Parser 4 3. Deploy Payload1 via HTTP 7 System Applicatio iBoot Kernel Cydia Software n 4. Exploit Userland Process 5. Exploit Kernel to gain root privileges 5 6. Download Payload2
- 64. Star 1 Payload 1 2 1. Payload1: Malformed PDF Payload 2 3 Mobile 2. Payload2: Post Install Safari 6 PDF CFF Font Parser 4 3. Deploy Payload1 via HTTP 7 System Applicatio iBoot Kernel Cydia Software n 4. Exploit Userland Process 5. Exploit Kernel to gain root privileges 5 6. Download Payload2 7. Install libraries and install Cydia
- 65. greenpois0n
- 66. greenpois0n • PC based Jailbreak
- 67. greenpois0n • PC based Jailbreak • also Jailbreak Toolkit (Syringe, Cyanide, Anthrax...*)
- 68. greenpois0n • PC based Jailbreak • also Jailbreak Toolkit (Syringe, Cyanide, Anthrax...*) • exploits Bootrom vulnerability (limera1n exploit)
- 69. greenpois0n • PC based Jailbreak • also Jailbreak Toolkit (Syringe, Cyanide, Anthrax...*) • exploits Bootrom vulnerability (limera1n exploit) • then exploits Kernel vulnerability (undisclosed exploit)
- 70. greenpois0n • PC based Jailbreak • also Jailbreak Toolkit (Syringe, Cyanide, Anthrax...*) • exploits Bootrom vulnerability (limera1n exploit) • then exploits Kernel vulnerability (undisclosed exploit) • Injection vector: Bootloader communication (DFU Mode)
- 71. greenpois0n Bootrom iBSS iBSS Payload iBoot Kernel Ramdisk Loader.app
- 72. greenpois0n 1. exploit bootrom vulnerability Bootrom iBSS iBSS Payload iBoot Kernel Ramdisk Loader.app
- 73. greenpois0n 1. exploit bootrom vulnerability Bootrom iBSS 2. upload iBSS iBSS Payload iBoot Kernel Ramdisk Loader.app
- 74. greenpois0n 1. exploit bootrom vulnerability Bootrom iBSS 2. upload iBSS 3. upload iBSS payload iBSS Payload iBoot Kernel Ramdisk Loader.app
- 75. greenpois0n 1. exploit bootrom vulnerability Bootrom iBSS 2. upload iBSS 3. upload iBSS payload 4. execute iBSS payload iBSS Payload iBoot Kernel Ramdisk Loader.app
- 76. greenpois0n 1. exploit bootrom vulnerability Bootrom iBSS 2. upload iBSS 3. upload iBSS payload 4. execute iBSS payload 4.1. upload, patch and jump to iBoot iBSS Payload iBoot Kernel Ramdisk Loader.app
- 77. greenpois0n 1. exploit bootrom vulnerability Bootrom iBSS 2. upload iBSS 3. upload iBSS payload 4. execute iBSS payload 4.1. upload, patch and jump to iBoot iBSS 4.2. upload iBoot payload Payload iBoot Kernel Ramdisk Loader.app
- 78. greenpois0n 1. exploit bootrom vulnerability Bootrom iBSS 2. upload iBSS 3. upload iBSS payload 4. execute iBSS payload 4.1. upload, patch and jump to iBoot iBSS 4.2. upload iBoot payload Payload 4.3. upload ramdisk iBoot Kernel Ramdisk Loader.app
- 79. greenpois0n 1. exploit bootrom vulnerability Bootrom iBSS 2. upload iBSS 3. upload iBSS payload 4. execute iBSS payload 4.1. upload, patch and jump to iBoot iBSS 4.2. upload iBoot payload Payload 4.3. upload ramdisk 4.4. execute ramdisk iBoot Kernel Ramdisk Loader.app
- 80. greenpois0n 1. exploit bootrom vulnerability Bootrom iBSS 2. upload iBSS 3. upload iBSS payload 4. execute iBSS payload 4.1. upload, patch and jump to iBoot iBSS 4.2. upload iBoot payload Payload 4.3. upload ramdisk 4.4. execute ramdisk 4.5. set kernel boot args iBoot Kernel Ramdisk Loader.app
- 81. greenpois0n 1. exploit bootrom vulnerability Bootrom iBSS 2. upload iBSS 3. upload iBSS payload 4. execute iBSS payload 4.1. upload, patch and jump to iBoot iBSS 4.2. upload iBoot payload Payload 4.3. upload ramdisk 4.4. execute ramdisk 4.5. set kernel boot args iBoot Kernel 4.6. upload kernel cache Ramdisk Loader.app
- 82. greenpois0n 1. exploit bootrom vulnerability Bootrom iBSS 2. upload iBSS 3. upload iBSS payload 4. execute iBSS payload 4.1. upload, patch and jump to iBoot iBSS 4.2. upload iBoot payload Payload 4.3. upload ramdisk 4.4. execute ramdisk 4.5. set kernel boot args iBoot Kernel 4.6. upload kernel cache 4.7. boot Ramdisk Loader.app
- 83. greenpois0n 1. exploit bootrom vulnerability Bootrom iBSS 2. upload iBSS 3. upload iBSS payload 4. execute iBSS payload 4.1. upload, patch and jump to iBoot iBSS 4.2. upload iBoot payload Payload 4.3. upload ramdisk 4.4. execute ramdisk 4.5. set kernel boot args iBoot Kernel 4.6. upload kernel cache 4.7. boot Ramdisk 5. install loader.app Loader.app
- 84. Conclusion • Fun from a technical perspective • Actually useful for only a few (Unlockers, Developers) • Mostly used for the wrong purposes • Crapware like themes and custom sms sounds • Software pirating
- 85. more in the final paper... slides available at http://blog.010dev.com
- 86. Unlocking signature signature check check Bootrom Bootloader Firmware (Nucleus OS) ROM NOR seczone protected area contains: encrypted lock-state
- 87. Unlocking signature signature check check Bootrom Bootloader Firmware (Nucleus OS) ROM NOR seczone 1. truly unlock protected area by altering lock-state in seczone contains: encrypted lock-state
- 88. Unlocking signature signature check check 2. unlock on-the-fly by constantly overriding netlock checks in firmware Bootrom Bootloader Firmware (Nucleus OS) ROM NOR X seczone 1. truly unlock protected area by altering lock-state in seczone contains: encrypted lock-state
- 89. Unlocking 2. unlock on-the-fly by constantly overriding netlock checks in firmware
- 90. Unlocking 2. unlock on-the-fly by constantly overriding netlock checks in firmware Nucleus OS seczone NOR Baseband Processor
- 91. Unlocking 2. unlock on-the-fly by constantly overriding netlock checks in firmware iOS Nucleus OS seczone NOR UART Application Processor Baseband Processor
- 92. Unlocking 2. unlock on-the-fly run deamon process on by constantly overriding netlock application processor checks in firmware exploit code execution * (requires jailbreak) vulnerabilities to override netlock „on-the-fly“ unlockd iOS Nucleus OS X seczone NOR UART Application Processor Baseband Processor