lec-05-Message authentication, hashing, basic number theory.ppt
- 1. CMSC 414 Computer and Network Security Lecture 5 Jonathan Katz
- 3. MAC functionality (review) k k Vrfyk(m’,t’) ?? m, t t = Mack(m) •Shared key k •Sender computes a tag t on the message m using k •Receiver verifies the message/tag pair using k Alice Bob
- 4. Defining security Attack model: – A random key k is chosen – Attacker is allowed to obtain t1 = MACk(m1), …, tn = MACk(mn) for any messages m1, …, mn of its choice Attacker is successful if it outputs a forgery; i.e., (m, t) with: – m ≠ mi for all i – VrfyK(m, t) = 1 For any time-bounded adversary, the probability of a successful attack should be small
- 5. A MAC for short messages Let F be a block cipher with n-bit output To authenticate m using key k, compute t = Fk(m) Vrfyk(m, t): output 1 iff t = Fk(m) Why is this secure?
- 6. Authenticating longer messages? Two widely used schemes (among several): – CBC-MAC – HMAC
- 7. CBC-MAC Fix a message length Ln, where the block cipher has n-bit block length To compute MACk(m1, …, mL) do: – Set t0 = 0n – For i=1 to L, set ti := Fk(ti-1 mi) – Output tL To verify, re-compute and check… [Note the similarities to (and differences from) CBC mode encryption]
- 8. Security of CBC-MAC? Secure for fixed-length messages Insecure (as described) for variable-length messages – Must use secure variants of CBC-MAC if variable- length messages will be authenticated
- 9. HMAC Can be viewed as a version of “hash-and-MAC”, using collision-resistant hashing…
- 10. Hash functions A (cryptographic) hash function H maps arbitrary length inputs to a fixed-length output Main goal is collision resistance: – Hard to find distinct x, x’ such that H(x) = H(x’) Other goals – Second pre-image resistance: given x, hard to find x’ ≠ x with H(x) = H(x’) – “Random-looking output”: I.e., “acts like a random oracle” • Controversial; more later
- 11. Hash functions in practice MD5 – 128-bit output – Introduced in 1991…collision attacks found in 2004…several extensions and improvements since then – Still widely deployed(!) SHA-1 – 160-bit output – No collisions known, but theoretical attacks exist SHA-2 – 256-/512-bit outputs Competition to design new hash standard has just begun…
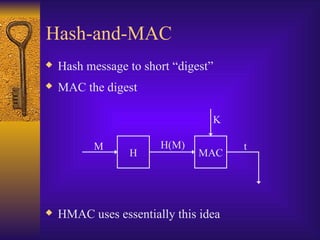
- 12. Hash-and-MAC Hash message to short “digest” MAC the digest HMAC uses essentially this idea H MAC M H(M) K t
- 13. (Informal) sketch of security? Say the adversary sees tags on m1, …, mt,, and outputs a valid forgery on m {m1, …, mt} Two possibilities: – H(m) = H(mi) for some i – collision in H – H(m) {H(m1), …, H(mt)} – forgery in the underlying MAC for short messages
- 14. Encryption + integrity In most settings, confidentiality and integrity are both needed – How to obtain both? Use ‘encrypt-then-authenticate’ Other natural possibilities are problematic!
- 17. Sharing keys? Secure sharing of a key is necessary for private- key crypto – How do parties share a key in the first place? One possibility is a secure physical channel – E.g., in-person meeting – Dedicated (un-tappable) phone line – USB stick via courier service Another possibility: key exchange protocols – Parties can agree on a key over a public channel – This is amazing! (And began a revolution in crypto…)
- 18. Diffie-Hellman key exchange Before describing the protocol, a brief detour through number theory… – Modular arithmetic, Zp, Zp * – Generators – The discrete logarithm assumption






![CBC-MAC
Fix a message length Ln, where the block cipher
has n-bit block length
To compute MACk(m1, …, mL) do:
– Set t0 = 0n
– For i=1 to L, set ti := Fk(ti-1 mi)
– Output tL
To verify, re-compute and check…
[Note the similarities to (and differences from) CBC
mode encryption]](https://image.slidesharecdn.com/lec-05-messageauthenticationhashingbasicnumbertheory-250116090927-18480fbb/85/lec-05-Message-authentication-hashing-basic-number-theory-ppt-7-320.jpg)