Misconfigurations
0 likes302 views
The document discusses various security issues found on a system including misconfigurations, directory listings exposing sensitive information, and transaction logs containing useful information for attackers. It also notes that while directory listings prohibiting parent directory access were meant to improve security, other issues remained.
1 of 20



















Misconfigurations
- 15. Old School Simple but useful directory listing
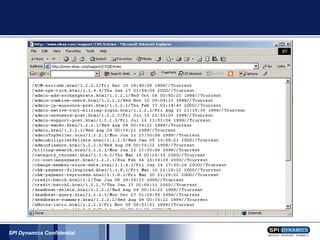
- 16. Thank you directory listing
- 18. Transaction Log Nice info laying around
- 19. Funny Ah, we practice good security no ‘..’ are allowed
- 20. Lot of good that did