network security
- 1. 8. Network Security 1 Secure Communication Secure communication refers to a communication whereby only the recipient of the message understands the message even if there are intruders who may intercept, read and perform computations on whatever is being transmitted. The receiver is also sure that the message received was from a particular sender and that it has not been altered in transit. Below are some of the desirable properties of a secure communication. 1. Confidentiality: Only the sender and the receiver should be able to understand the contents of the transmitted message. Because of intruders, i.e. hackers, the message maybe encrypted (its data disguised) so that the interceptor cannot understand the message. This aspect of confidentiality is probably the most commonly perceived meaning of the phrase "secure communication". 2. Authentication: Both sender and receiver should be able to confirm the identity of the other party involved in the communication i.e. to confirm that the other party is indeed who or what they claim to be. 3. Message integrity and nonrepudiation: Even if the sender and receiver are able to authenticate each other, they also want to ensure that the content of their communication is not altered, either maliciously or by accident during transmission. Therefore message integrity can be ensured by extensions to the checksumming techniques that we encounter in reliable transport and data link protocols. 4. Availability and access control: The compelling need for network security has been made unbearable over the past several years by numerous denial-of-access attacks that have rendered a network host or other pieces of network infrastructure unusable by legitimate users. The notion of access control ensures that entities seeking to gain access to resources are allowed to do so only if they have the appropriate access rights and perform their accesses in a well-defined manner. Encryption
- 2. 8. Network Security 2 Encryption Terminology • Algorithm – mathematical formula for encryption – not secret, well-known • Key – the secret part used by formula • Keyspace – available set of keys • Plaintext – not encrypted message • Ciphertext – encrypted message Types of Encryption – Deployment • End-to-end: such encryption is carried out by end systems and the network treats the encrypted data in the same way as normal data. Encryption is not aided or facilitated by the network structure. Most encryption techniques and activities are of this type. • Network-based: this is implemented at the network layer of the protocol stack. I.e. the data is encrypted at the lower layers of protocol stack, esp at the IP header level. Example is IPSec. Type of Encryption – Algorithm/Key Encryption Clear- Text Clear- Text Text This is secret 8vyaleh31&d ktu.dtrw8743 $Fie*nP093h This is secret Decryption
- 3. 8. Network Security 3 • Symmetric encryption: same secret key is used for both encryption and decryption. It is older technique and majority of encryption is based on this class of techniques. – Strength depends upon the size of the key. – But difficult to ensure authenticity and non-repudiation. – Examples are DES, 3DES, AES, RC4 etc. • Asymmetric encryption: separate keys are used for encryption and decryption. More secure than symmetric but more resource-hungry for implementation. – Can be used to ensure authenticity and non-repudiation of the data. – Examples are RSA, Diffie-Hellman etc. Symmetric Encryption
- 4. 8. Network Security 4 DES (Digital Encryption Standard): – DES is the first major symmetric encryption technique. It is a block cipher techniques. – Based on Feistel structure – 64-bit original message blocks – 56-bit keys. – The 56-bit key is used to generate 16 48-bit sub-keys. – Each sub-key is different from the main key and all other sub-keys. – They are derived from the main key using special sub-key generation algorithm. The encryption is done over 16 rounds, each with a separate sub- key. – This technique has been proven to be relatively weak and easy to crack.
- 5. 8. Network Security 5 3DES (Triple DES) – This is based on DES but involves 3-stages of DES (usually done as sequence of encrypt-decrypt-encrypt), each with separate key. But it can be simplified to use only 2 keys by using a sequence of Encrypt-Decrypt-Encrypt with decrypt done by a separate key and two encrypts done by the same key. Designed to make the encryption much more secure compared to DES.
- 6. 8. Network Security 6 AES (Advance Encryption Standard) – Advanced Encryption Standard (AES) is more advanced than 3DES. Like 3DES, it is also block cipher system but uses a block size of 128-bit compared to 64-bit block size of 3DES and DES. The key length in AES can range from 128 to 256 bits. – However, unlike DES, AES is not based on Feistel structure. It does not involve dividing the message block into two halves. Asymmetric Encryption • Use of two separate keys for encryption and decryption. • Can provide confidentiality as well as integrity and authentication mechanism. – Whereas symmetric encryption can provide only confidentiality.
- 7. 8. Network Security 7 RSA • Named after its creators (Rivest, Shamir and Adleman of MIT) • Algorithm – C = Me mod n – M = Cd mod n = Med mod n – Where M is plaintext and C is ciphertext block. Both the sender and receiver have to know the value of e and n. Only the receiver needs to know the value of d. Hence the private and public key can be represented as Kpvt = {d, n} and Kpub = {e, n} respectively. Refer to the example given in section 3.5 of Book (Stallings) for the detailed process of generation and use of public/private keys. Digital Certificates • Certificates are used as a measure of assuring authenticity of the public keys used for cryptography. – Each certificate consists of the public key of the user and is signed with the private key of a trusted certification authority. – ITU-T recommendation X.500 specifies the different aspects of certification mechanism.
- 8. 8. Network Security 8 • Such certificate mechanism is used in different security applications such as secure MIME (email encoding technique), IP-Sec, SSL/TLS etc. Component of a Certificate • Version • Serial Number • Signature Algorithm Identifier • Issuer Name • Period of Validity • Subject Name • Subject’s Public Key Identity • Subject Unique Identifier • Extension • Signature Digital Signatures • Digital signatures is a cryptography mechanism to make sure that the message actually came from the source it seems to come from. • It is not a mechanism to secure the data by encrypting it but to authenticate the source of data by embedding a ‘signature’ in the data that is from the sender. • Using asymmetric cryptography, the sender encrypts the whole or part of the message using its private key and the receiver tries to decrypt the encrypted part using the sender’s public key. • Example: DSS (digital signature standard), SHA (Secure Hash Algorithm), MD5 (Message Digest 5). Email Security • Email has been a favored medium of spreading malware, viruses and other types of content that pose threat to the network and services.
- 9. 8. Network Security 9 • Probably also because email service is among the oldest services to be realized over network and Internet. PGP (Preety Good Privacy) The different services provided by PGP and the techniques used for those services is summarize by Table below. Table: PGP Services and Techniques
- 10. 8. Network Security 10 << Radix-64 conversion is a technique to convert the email content into alphanumeric ASCII character string. The actual binary value of the data is converted into sequence of 6-bit groups and each such group is converted into ASCII. The characters are 26 capital alphabets, 26 small alphabets, 10 numerals and two more characters (usually ‘+’ and ‘/’) >> The message encryption technique as indicated in table is illustrated in detail in Figure (Source: Wikipedia). Symmetric key is used to encrypt the message. This symmetric key is itself encrypted using asymmetric encryption (using receiver’s public key) and added to the encrypted message. The receiver first extracts the key from the whole message and uses that key to encrypt the message.
- 11. 8. Network Security 11 Figure: PGP Encryption Process PGP is designed to be able to provide message encryption, authentication and integrity checking mechanism. These different services are achieved as follows: 1. Encryption: the message is encrypted using the symmetric key which is itself is encrypted using asymmetric key and added to the encrypted message as illustrated in Figure 6.2.1.1. The symmetric key used to encrypt the message is separate per message session and is randomly generated. Hence this key is also called the session key. This key for each message is different. 2. Authentication and integrity checking: to verify the sender and to verify message integrity, the sender creates a message digest using a hash function and encrypts that message digest using the sender’s private key. Thus, the sender literally ‘signs’ the message digest. The receiver can thus verify the sender by checking decryption using the sender’s public key as well as the message integrity by comparing the message digest of the received message using the digest sent along with the message. Figure 6.2.1.2 (Source Figure 7.1 Stallings) illustrates the logic for authentication, encryption and both functions using PGP:
- 12. 8. Network Security 12 Figure 6.2.1.2: PGP Process of Authentication and Confidentiality The symbols used in Figure 6.2.1.2 are as follows: Ks = Session key used in symmetric encryption scheme PRa = Private key of user A, used in public-key encryption scheme PUa = Public key of user A, used in public-key encryption scheme EP = Public-key encryption DP = Public-key decryption EC = Symmetric encryption DC = Symmetric decryption M = Original Message SSL SSL (Secure Sockets Layer) is a standard security technology for establishing an encrypted link between a server and a client—typically a web server (website) and a browser; or a mail server and a mail client (e.g., Outlook). SSL allows sensitive information such as credit card numbers, social security numbers, and login credentials to be transmitted securely. Normally, data sent between browsers and web servers is sent in plain text—leaving you vulnerable to eavesdropping. If an attacker is able to intercept all data being sent between a browser and a web server they can see and use that information.
- 13. 8. Network Security 13 More specifically, SSL is a security protocol. Protocols describe how algorithms should be used; in this case, the SSL protocol determines variables of the encryption for both the link and the data being transmitted. Secure HTTP (HTTPS) HTTPS or secure HTTP deploys the standard HTTP over SSL. This results in secure and encrypted communication between the web server and the client (i.e. the browser). For compatibility and differentiation, HTTPS uses separate well-known TCP port of 443 rather than the TCP port 80 used for standard HTTP. As a result, same web content can be served over HTTP and HTTPS at the same time from the same server. When HTTPS is used, the following data transfer between the server and the client are encrypted. The encryption is normally asymmetric. URL of the requested document Contents of the document Contents of browser forms (filled in by browser user) Cookies sent from browser to server and from server to browser Contents of HTTP header For HTTPS implementation, the key or certificate management of the encryption can be done by the specific web site alone or can be taken from a third part certificate repository. The process of establishment of data transfer session for secure HTTP is as follows: 1. The client (browser) sends its SSL version number and cryptographic preference to the server. This is needed for the browser and the server to negotiate the symmetric key algorithm they are to use for the data transfers. 2. The server sends its SSL version number, cryptographic preferences and its certificate. The certificate includes the servers public key (RSA) and is normally certified by a Certificate Authority (CA) with its private key (digital signature). 3. The browser has a list of public keys for known CAs. It validates the authenticity of the key sent by server. If it cannot validate, it throws an alert. 4. The browser creates a symmetric session key, encrypts it with the server’s public key and sends the encrypted key to the server. 5. The browser also tells the server that all future messages from the client shall be encrypted with the symmetric session key. 6. The server also informs the client that all subsequent messages from server shall also be encrypted with the same session key. 7. The SSL handshake is now complete and subsequent transfers on both sides shall be encrypted. Virtual Private Networks Virtual Private Network or VPN is a mechanism to realize private communication over a public, shared network infrastructure. The major characteristic of a VPN connection are:
- 14. 8. Network Security 14 They use the public network infrastructure for private communication. Use different techniques to hide actual data. Creates a kind of ‘tunnel’ across the public network to give the feeling of direct, point-to-point connections between the two points. Can be end-system based or network-based. Extensively used for branch connectivity, private connectivity to corporate network by mobile employee, secure connectivity between two networks, access into private, secure networks over the public networks such as Internet. Based on their purpose, there are different types of VPN: End-to-end: Realized by VPN client software connecting to the VPN servers over public network. After connectivity is complete, the private network inside the VPN server boundary can be accessed by the client over the private tunnel. Network-based: Mainly over IPSec or MPLS. At the network layer of the protocol stack. Whole IP packets including the IP addresses are encapsulated into the new header. Encryption is used in IPSec but not in MPLS. MPLS can be considered to be between layers 2 and 3. Hence, at the receiving end, the MPLS header is processed before IP header. Hence, MPLS header can create tunnel across different IP networks provided MPLS service is available in the intermediate nodes. Similarly, based on the deployment modality, there are different types of VPN such as: Site-to-Site: Point-to-point VPN between two fixed nodes or sites. For example between one office to other office, branch office to head office or one organization to other organization. Remote Access: VPN designed to provide access to the central or secure network for the user on the move. Used to access corporate system from home or from other networks. Wireless Network Security While all the threats and security dimensions of the wired networks are applicable to the wireless network as well, the very nature of the wireless technology creates some additional security scenarios. This can be summarized as: a. While wired network limits the network coverage to places where wires have reached, the wireless network has no such restriction. The signals of the network can cross physical boundaries and hence less control on the devices that can connect to it.
- 15. 8. Network Security 15 b. In wired network, the data flowing in the network can only be received by the nodes physically connected by the wires whereas, anybody in the coverage area in wireless network can sense the data. Because of these, the task of securing wireless network needs more robust security mechanisms. Wired Equivalent Privacy (WEP) WEP was the security mechanism in the initial 802.11 standard. IT mainly provided encryption of the data being transferred through the Wi-Fi network but did not provide good authentication mechanism. Even the encryption it provided was quickly found to insufficient and easily breakable. However it is still in wide use, normally in end-user networks. However, for secure corporate networks, it is not preferred due to its weaknesses. The simple encryption mechanism used in WEP is illustrated in Figure 6.5.1.1 (here IV = Initialization Vector). Figure 6.5.1.1: The WEP Encryption Mechanism Confidentiality: for data confidentiality, WEP uses RC4 (ref. Chapter 2.4 Stallings for details on RC4) stream cipher mechanism with key length ranging from 40-bit to 128-bit. Some vendors also provide 232-bit keys (in each case, a 24-bit initialization vector is used for the RC4 algorithm). Authentication: two modes are available – no authentication (open network) or shared key authentication. Open networks can be joined by any client. Then the encrypted data transaction happens. As a result, this mode provides only data encryption but not access control. In shared key authentication mode, same key is used by the client and the access node. During the client joining the network, the following happens: i. The client sends an authentication request to the Access Point. ii. The Access Point replies with a clear-text challenge. iii. The client encrypts the challenge-text using the configured WEP key, and sends it back in another authentication request. iv. The Access Point decrypts the response. If this matches the challenge-text the Access Point sends back a positive reply.
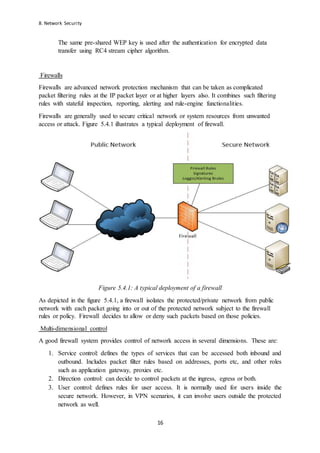
- 16. 8. Network Security 16 The same pre-shared WEP key is used after the authentication for encrypted data transfer using RC4 stream cipher algorithm. Firewalls Firewalls are advanced network protection mechanism that can be taken as complicated packet filtering rules at the IP packet layer or at higher layers also. It combines such filtering rules with stateful inspection, reporting, alerting and rule-engine functionalities. Firewalls are generally used to secure critical network or system resources from unwanted access or attack. Figure 5.4.1 illustrates a typical deployment of firewall. Figure 5.4.1: A typical deployment of a firewall As depicted in the figure 5.4.1, a firewall isolates the protected/private network from public network with each packet going into or out of the protected network subject to the firewall rules or policy. Firewall decides to allow or deny such packets based on those policies. Multi-dimensional control A good firewall system provides control of network access in several dimensions. These are: 1. Service control: defines the types of services that can be accessed both inbound and outbound. Includes packet filter rules based on addresses, ports etc, and other roles such as application gateway, proxies etc. 2. Direction control: can decide to control packets at the ingress, egress or both. 3. User control: defines rules for user access. It is normally used for users inside the secure network. However, in VPN scenarios, it can involve users outside the protected network as well.
- 17. 8. Network Security 17 4. Behavior control: defines more complicated activities such as redirection of services, allowing some services while blocking others, allowing access to only part of a service or network etc. Types of Firewall The major types of firewall are: 1. Packet filtering firewall: define allow/disallow rules for packets based on the specific content of each packet such as addresses, ports (protocols), interfaces etc. The rules and functional architecture are similar to that of the packet filter lists or access lists. Figure 5.4.2.1 shows the schematic of the packet filtering firewall. Figure 5.4.2.1: Packet filtering firewall 2. Stateful inspection firewall: simple packet filtering firewall decides to allow/block a packet entirely based on the content of that same packet. It does not look at the context of that packet. However, a stateful mechanism can keep track of connections, data sessions and other parameters and uses them to decide on each packet. It can keep track of individual TCP sessions and even their sequence numbers to be able to make packet decisions based more on the previous record, overall behavior and context rather than the content of individual packet only. Figure 5.4.2.2 shows schematic of stateful inspection firewall.
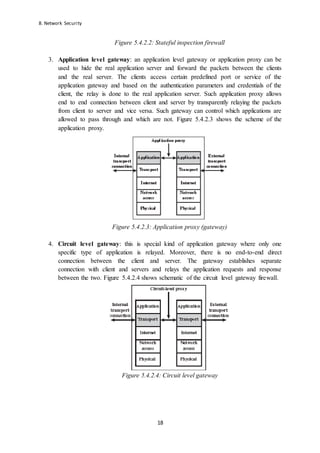
- 18. 8. Network Security 18 Figure 5.4.2.2: Stateful inspection firewall 3. Application level gateway: an application level gateway or application proxy can be used to hide the real application server and forward the packets between the clients and the real server. The clients access certain predefined port or service of the application gateway and based on the authentication parameters and credentials of the client, the relay is done to the real application server. Such application proxy allows end to end connection between client and server by transparently relaying the packets from client to server and vice versa. Such gateway can control which applications are allowed to pass through and which are not. Figure 5.4.2.3 shows the scheme of the application proxy. Figure 5.4.2.3: Application proxy (gateway) 4. Circuit level gateway: this is special kind of application gateway where only one specific type of application is relayed. Moreover, there is no end-to-end direct connection between the client and server. The gateway establishes separate connection with client and servers and relays the application requests and response between the two. Figure 5.4.2.4 shows schematic of the circuit level gateway firewall. Figure 5.4.2.4: Circuit level gateway