oauth-for-credentials-security-in-rest-api-access
- 2. Open Authorization : OAuth for credentials security in REST API access
- 3. Panggi Libersa Jasri Akadol Web : http://www.opensecuritylab.org Twitter : @panggi
- 4. Agenda • Web 2.0 and Data • OAuth usage • Useful resources
- 5. Web 2.0 and Data
- 6. Web 2.0
- 7. = Your Data
- 8. Different service = Different data
- 9. What if you need to use your data that stored in another service provider’s server ?
- 10. Yup , just take it
- 12. OK .. Enough with the Cute creatures :-p Let’s dive into technical things
- 13. Once again.. How ?
- 14. Using API (Application Programming Interface)
- 15. An application programming interface (API) is an interface implemented by a software program that enables it to interact with other software. It facilitates interaction between different software programs similar to the way the user interface facilitates interaction between humans and computers. ( via http://en.wikipedia.org/wiki/API)
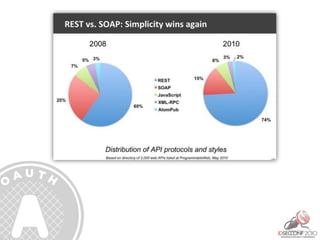
- 17. REST Representational State Transfer •Provide every resource with a unique ID, for example, a URI •Link resources with each other, establishing relationships among resources •Use standard methods (HTTP, media types, XML) •Resources can have multiple representations that reflect different application states •The communication should be stateless using the HTTP
- 18. Accessing API
- 21. What’s on your mind ?
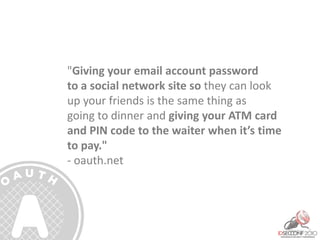
- 22. "Giving your email account password to a social network site so they can look up your friends is the same thing as going to dinner and giving your ATM card and PIN code to the waiter when it’s time to pay." - oauth.net
- 23. we need an easy, user-friendly standard for third party api security
- 24. OAuth usage
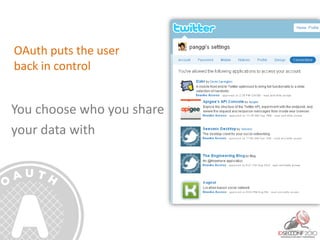
- 26. OAuth puts the user back in control You choose who you share your data with
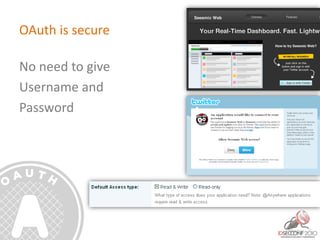
- 27. OAuth is secure No need to give Username and Password
- 28. Big Name Adoption Google Yahoo! OpenSocial Netflix MySpace twitter SmugMug GetSatisfaction and more...
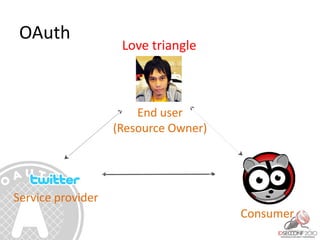
- 29. Love triangle End user (Resource Owner) Service provider Consumer OAuth
- 30. OAuth Protected resources are exposed by service providers and used by consumer applications on behalf of users
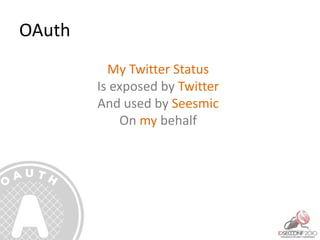
- 31. OAuth My Twitter Status Is exposed by Twitter And used by Seesmic On my behalf
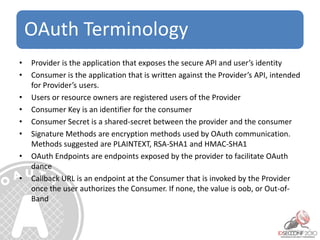
- 32. OAuth Terminology • Provider is the application that exposes the secure API and user’s identity • Consumer is the application that is written against the Provider’s API, intended for Provider’s users. • Users or resource owners are registered users of the Provider • Consumer Key is an identifier for the consumer • Consumer Secret is a shared-secret between the provider and the consumer • Signature Methods are encryption methods used by OAuth communication. Methods suggested are PLAINTEXT, RSA-SHA1 and HMAC-SHA1 • OAuth Endpoints are endpoints exposed by the provider to facilitate OAuth dance • Callback URL is an endpoint at the Consumer that is invoked by the Provider once the user authorizes the Consumer. If none, the value is oob, or Out-of- Band
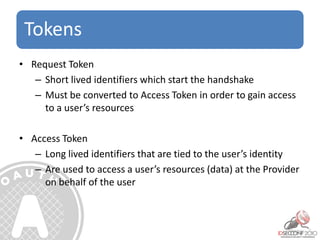
- 33. Tokens • Request Token – Short lived identifiers which start the handshake – Must be converted to Access Token in order to gain access to a user’s resources • Access Token – Long lived identifiers that are tied to the user’s identity – Are used to access a user’s resources (data) at the Provider on behalf of the user
- 34. Endpoints • Get request token • Authorize token • Get access token
- 35. Get Request Token • The endpoint provides consumers to get an unauthorized request token by providing their consumer key and other parameters as a signed request • The credentials can be passed via HTTP Header, POST body or GET QueryString • The request includes an oauth_signature which is calculated by following the steps defined in the spec. Use libraries instead of writing your own signing implementations. • The response has an unauthorized request token as well as a token secret, and a flag indicating if the callback was accepted.
- 36. Authorize Token • The step authorizes an unauthorized request token retrieved via previous request. • The endpoint takes the unauthorized request token – or the user can enter one manually if supported. • The Authorize Token endpoint then redirects the user to the Provider’s login page • The user logs in, and is asked to authorize the consumer (and hence the request token) • Once the user authenticates, and authorizes access to the consumer, the provider calls the callback URL provided earlier with a verifier code. This verifier code, along with other credentials is used to get an Access Token.
- 37. Get Access Token • At this step, the now authorized request token is exchanged for an access token • The access token acts as a user’s credential for any further transactions • The endpoint takes the request token and the verifier code returned via the callback, or manually if callback is not supported. The request is signed with consumer secret and the request token’s secret. • The Provider returns an access token and a token secret. • The token secret is used to sign the requests along with the consumer secret.
- 38. Access User’s Resources • Now that the consumer has the access token, the user’s resources can be requested via signed requests to the provider. • The user should be able to unauthorize the consumer by revoking the access token. • The access token has a time to live which is typically longer than the request token
- 39. Useful Resources
- 40. • http://tools.ietf.org/html/rfc5849 • http://oauth.net/code/ • http://hueniverse.com/oauth/ • http://code.google.com/p/oauth/ • http://opensecuritylab.org/tag/oauth