Patterns for Secure Boot and Secure Storage in Computer Systems
- 1. RuhR-University Bochum System Security Lab Patterns for Secure Boot and Secure Storage in Computer Systems Hans Löhr, Ahmad-Reza Sadeghi, Marcel Winandy Horst Görtz Institute for IT Security Ruhr-University Bochum Germany SPattern '10 (co-located with ARES 2010) 4th International Workshop on Secure Systems Methodologies Using Patterns Krakow, Poland, 18 February 2010
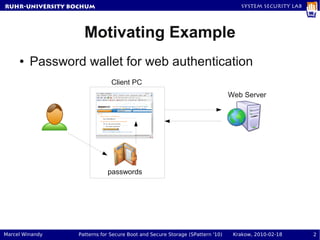
- 2. RuhR-University Bochum System Security Lab Motivating Example ● Password wallet for web authentication Client PC Web Server passwords Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 2
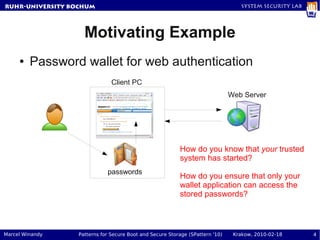
- 3. RuhR-University Bochum System Security Lab Motivating Example ● Password wallet for web authentication Client PC Web Server How do you know that your trusted system has started? passwords Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 3
- 4. RuhR-University Bochum System Security Lab Motivating Example ● Password wallet for web authentication Client PC Web Server How do you know that your trusted system has started? passwords How do you ensure that only your wallet application can access the stored passwords? Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 4
- 5. Secure Boot Pattern Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 5
- 6. RuhR-University Bochum System Security Lab Context ● Users want to be sure about operational integrity of applications and OS ● Unauthorized changes may lead to security violation ● Users trust the hardware – But need to verify integrity status of loaded software ● Users can be local or remote Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 6
- 7. RuhR-University Bochum System Security Lab Problem ● Software can be manipulated or exchanged ● Malware can register itself within any stage of the boot process ● Forces: – You want to ensure integrity of loaded software – You want the computer to always boot in a well- defined secure state – You want to allow modifications of the system (e.g. updates, additional software) Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 7
- 8. RuhR-University Bochum System Security Lab Solution ● Chain of trust – Each boot stage verifies integrity of next stage ● using cryptographically secure methods (hash functions, digital signature) – Only if check ok, control is transferred to next stage otherwise: system is halted ● Root of trust – Whole process depends on integrity of first module – First module therefore protected by hardware ● Including the integrity verification data (hashs, keys) Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 8
- 9. RuhR-University Bochum System Security Lab Solution ● Structure: Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 9
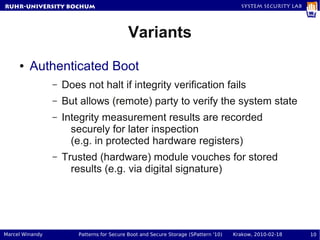
- 10. RuhR-University Bochum System Security Lab Variants ● Authenticated Boot – Does not halt if integrity verification fails – But allows (remote) party to verify the system state – Integrity measurement results are recorded securely for later inspection (e.g. in protected hardware registers) – Trusted (hardware) module vouches for stored results (e.g. via digital signature) Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 10
- 11. RuhR-University Bochum System Security Lab Consequences ● Benefits: – Software integrity state is verified at boot time – System starts only if integrity is OK – Authenticated boot: more flexible, check later ● Liabilities: – Setup/update of integrity verification data securely – Specific mechanisms needed for software updates – Integrity checks are only load-time, not runtime – Adds complexity and overhead Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 11
- 12. RuhR-University Bochum System Security Lab Known Uses ● Cell BE processor Sony PlayStation3 ● Trusted Platform Module (TPM) PCs, Laptops (Authenticated Boot) ● Open Mobile Terminal Platform (OMTP) specs Mobile phones (Abstract definition, different implementations) Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 12
- 13. Secure Storage Pattern Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 13
- 14. RuhR-University Bochum System Security Lab Context ● Provide storage that protects confidentiality and integrity of stored data for software applications ● Grant software to access the clear data only if the software has not been tampered with ● Hardware is trusted Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 14
- 15. RuhR-University Bochum System Security Lab Problem ● Cryptographic methods protect confidentiality and integrity (encryption, digital signatures) ● But software that has access to the keys could be manipulated ● Forces: – You need to protect confidentiality/integrity of data – You need to protect secret keys from unauthorized access and usage – You want to allow modifications/updates of software Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 15
- 16. RuhR-University Bochum System Security Lab Solution Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 16
- 17. RuhR-University Bochum System Security Lab Consequences ● Benefits: – Software can access protected data only if integrity verification of the software has succeeded – Data can be protected such that only authorized software (OS and applications) can access it ● Liabilities: – Backup strategy needed (hardware failures result in data loss because of hardware-protected keys) – Software updates more difficult (mechanism needed for updating integrity verification data) – Adds complexity and overhead Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 17
- 18. RuhR-University Bochum System Security Lab Known Uses ● Cell BE processor Sony PlayStation3 ● Trusted Platform Module (TPM) PCs, Laptops ● Open Mobile Terminal Platform (OMTP) specs Mobile phones (Abstract definition, different implementations) Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 18
- 19. Conclusion Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 19
- 20. RuhR-University Bochum System Security Lab Example Resolved ● Password wallet for web authentication Client PC Web Server How do you know that your trusted system has started? passwords How do you ensure that only your wallet application can access the stored passwords? Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 20
- 21. RuhR-University Bochum System Security Lab Example Resolved ● Password wallet for web authentication Client PC Web Server How do you know that your trusted Secure Boot system has started? passwords How do you ensure that only your wallet application can access the stored passwords? Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 21
- 22. RuhR-University Bochum System Security Lab Example Resolved ● Password wallet for web authentication Client PC Web Server How do you know that your trusted Secure Boot system has started? passwords How do you ensure that only your wallet application can access the Secure Storage stored passwords? Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 22
- 23. RuhR-University Bochum System Security Lab Summary and Conclusion ● Secure Boot describes how to start a system in known secure state (or how to verify it later) ● Secure Storage describes how to bind the access to data to the integrity state of software (and protect data even when system is offline) ● Both are fundamental concepts of trusted computing ● Valuable addition to OS security patterns Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 23
- 24. RuhR-University Bochum System Security Lab Summary and Conclusion ● Secure Boot describes how to start a system in known secure state (or how to verify it later) ● Secure Storage describes how to bind the access to data to the integrity state of software (and protect data even when system is offline) Questions? ● Both are fundamental concepts of trusted computing ● Valuable addition to OS security patterns Marcel Winandy Ruhr-University Bochum marcel.winandy@trust.rub.de Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 24
- 25. BACKUP Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 25
- 26. RuhR-University Bochum System Security Lab Related Patterns ● Secure Boot: – Boot Loader ● Emphasis on error correction; no root of trust – Authenticator ● Creates proof of identity of subjects; no chain of trust Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 26
- 27. RuhR-University Bochum System Security Lab Related Patterns ● Secure Storage: – needs Secure Boot – needs Controlled Virtual Address Space ● Providing process isolation – Information Obscurity ● Encryption, hide encryption keys in protected location – Controlled Execution Environment ● Control access to protected resources; only runtime – Reference Monitor ● Access control enforcement; no offline enforcement Marcel Winandy Patterns for Secure Boot and Secure Storage (SPattern '10) Krakow, 2010-02-18 27