Presentation, Firewalls
- 1. "And of knowledge, you (mankind) have been given only a little." Surah Al-Isra‘, verse 85.
- 2. By: Khalid El-darymli FIREWALLS
- 3. Introduction The vastness of the internet, along with the differences among its visitors, creates a most unique melting pot. It also contains a great potential for misuse, abuse and criminal activity. A number of organizations have been attacked or probed by intruders, resulting in heavy production losses and embarrassment. On 1996 the US Department of Defense announced that its computer systems were attacked 250,000 times in the preceding year and most of these attacks went undetected. The web site of the United States Information Agency which was broken by internet vandals. But all is not lost: the F IREWALL still stands as the biggest and the best weapon for keeping the evil forces lurking along the miles of the information superhighway at bay.
- 4. Data Transmission in TCP/IP Networks: The internet is like a railroad, sort of. TCP/IP and the OSI reference model.
- 5. What Are F IREWALLs ?? A firewall A F IREWALL is a system ( either software or hardware or both ) that enforces an access control policy between two networks.
- 6. What can F IREWALL protect against, and what they cannot? They Can: F irewalls are excellent at enforcing the corporate security policy . F irewalls are used to restrict access to specific services . F irewalls are singular in purpose. F irewalls are excellent auditors . F irewalls are very good at alerting appropriate people of events. They Cannot: Firewalls cannot protect against what is authorized. Firewalls are only as effective as the rules they are configured to enforce . Firewalls cannot stop social engineers or an authorized user intentionally using their access malicious purposes. Firewalls cannot fix poor administrative practices or poorly designed security policy. Firewalls cannot stop attacks in which traffic does not pass through them .
- 7. Firewall Technology Application Level e.g. Proxy Servers Network Level e.g. packet filtering Both categories together .
- 8. F IREWALL Architectures F IREWALL primarily functions using four fundamental methods: Packet Filters. Application Gateways. Circuit-level Gateways. Stateful Packet Inspection.
- 9. 1- Packet Filters: A packet is like a letter. TCP/IP Packet structure.
- 10. How Packet filtering works: Creating a Rule Set: In order to provide an example of packet filtering we need to create a rule set. The rule set contains the following criteria: 1- Type of protocol. 2- Source address. 3- Destination address. 4- Source port. 5- Destination port. 6- The action the firewall should take when the rule set is not matched. (Example) Network topology for the packet filtering. (Example) Network topology for the packet filtering.
- 11. Sample packet filtering rule set. The flow of the packet filtering example. DENY
- 12. Advantages and disadvantages: Advantages: It creates little overhead, so the performance of the screening device is less impacted. It’s relatively inexpensive or even free. It provides good traffic management. Disadvantages : It allows direct connections to internal host from external clients. It leaves many holes in the network perimeter. That’s because it can only examine the traffic at the transport layer (TCP or UDP) or at the network layer (ICMP or IP protocol type). It’s difficult to manage and scale in complex environments. Because in multilayered security environment, all packet filters in both network traffic directions must be synchronized. It’s vulnerable to attacks that “spoof “ source addresses that match internal IP addressing schemes, unless it’s especially configured to prevent this issue. It offers no user authentication.
- 13. 2- Application Gateways (also, proxy gateway ) Application level gateway ? DENY
- 14. How it works: Overview of application gateway virtual connections. ALLOWED ONLY SSH
- 15. Advantages and Disadvantages of Application Gateways Advantages : Application level gateways tend to be more secure than packet filters. Rather than trying to deal with the numerous possible combinations that are to be allowed and forbidden at the TCP and IP level, the application level gateway need only scrutinize a few allowable applications. In addition it’s easy to log and audit all incoming traffic at the application level. Disadvantages : Prime disadvantage of the application level gateway is the additional processing overhead on each connection. In effect there are two spliced connections between the end users, with the gate way at the splice point, and the gateway must examine and forward all traffic in both directions.
- 16. 3- Circuit Level Gateways: (e.g. Proxy and Socks servers) Circuit-Level gateway. www.companyName.com www.companyName.com
- 17. Disadvantages: Most circuit level gateways are configurable on a TCP port basis. This does have disadvantage in that the circuit level gateway may not examine each packet at the application layer. This allows applications to utilize TCP ports that were opened for other, legitimate applications, several peer to peer applications can be configured to run on arbitrary ports, such as TCP 80 and TCP 443 (commonly opened for web browsing). This opens the possibility for misuse and exposes potential vulnerabilities inherent in these applications. There are several other disadvantages to using circuit level gateway as a sole meaning of protecting a network. Inbound connection, are in general, not allowed, unless the functionality is built into the gateway as a separate application. Some client applications cannot be modified to support SOCKS or proxying. This would prevent them from accessing external resources through a gateway.
- 18. Bastion Host: It is a computer that is the central component in a network security architecture, often the main entrance to the network, intended to protect. It’s running a proxy software. It’s usually the most critical, and therefore the best secured, system in the network. An other kind of bastion host called a victim machine ( also called a sacrificial lamb). Bastion hosts are used in all arrangements that use a proxy server.
- 19. 3- Stateful Packet Inspection: How it works: T he logic flow of stateful packet inspection.
- 20. Advantages and Disadvantages of SPI: Advantages: The connection table greatly reduces the chance that a packet will be spoofed to appear as it were part of an existing connection. The ability to look into the data of certain packet types. Disadvantages: It does not protect the internal hosts to the same degree as an application layer firewall. it does not act as proxy or setup a separate connection on behalf of the source.
- 21. Firewall Configurations 1- Screened Network (Packet Filtering Only): A simple firewall that uses a screening router
- 22. 2- Dual-Homed Gateway: A dual homed host has two IP addresses.
- 23. 3- Screened Host: The screened-host configuration.
- 24. Benefits & Disadvantages: Benefits : More flexible than a dual-homed gateway firewall. The rules for packet filter can be less a complex than for a screened network configuration because most or all the traffic will be directed to the application gateway. If either component fails in an “open” condition, so that it no longer blocks anything, the other component still affords some measure of protection. Disadvantages: The two components of the firewall need to be configured carefully to work together correctly. The flexibility of the system can lead to the temptation to take shortcuts that can subvert security.
- 25. 4- Screened Subnet: The screened-host configuration. Demilitarized Zone
- 26. Benefits & Disadvantages: Benefits : The chief benefit is an other layer of protection. To gain access to the protected network, an attacker would have to go through two routers and the application gateway-not impossible, but more difficult than with a screened-host firewall. Disadvantages: It’s the most expensive configuration (of those described here). With three machines. Including two routers with their rule tables, configuration of the overall system can become quite complicated.
- 27. Other firewall Configuration: You can come up with variations of the configurations described here to suit your security policy. You might want to use more bastion hosts to separate traffic for different services. You could add more layers of screened subnets to deal with traffic to and from networks with varying degrees of trustworthiness.
- 28. The point: There are no hard and fast rules for how a F irewall should be set up. Just remember a couple of guidelines: Avoid the temptation to take shortcuts around more burdensome aspects of the security policy. Effective security sometimes means inconvenience. Keep it as simple as possible. More is not necessarily better, especially if adding more elements to your firewall makes it impossibly complex to set up and administer, or so difficult to use that users resort to unauthorized shortcuts.
- 29. Practical F IREWALL Implementation Acme’s organizational chart shows a simple management structure with function consolidated in three main departments: production, sales/marketing, and finance. New Orleans
- 30. S ecurity I ssue: Defining the internet connection : S olutions: The system could be created so that no information flows out of Acme via the channel. Other data that the Web provider might need for the home page, such as announcements of new products, updates on product availability, special promotions, and so on, could likewise be transferred via some secure method - e.g., a one way email service on the company’s intranet-such that no files need to be transferred via the internet for this service. Information about ACME’s products. Web users will have the ability to send Email messages to any of Acme’s regional sales offices, generating a call back from the appropriate salesperson.
- 31. S ecurity I ssue: Determining Who Need Access: S olutions: This table shows where various information inside Acme is created and how it’s shared.
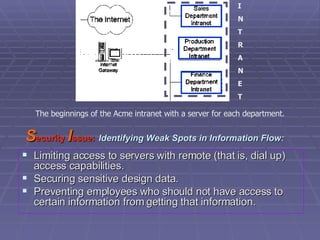
- 32. S ecurity I ssue: Identifying Weak Spots in Information Flow: Limiting access to servers with remote (that is, dial up) access capabilities. Securing sensitive design data. Preventing employees who should not have access to certain information from getting that information. The beginnings of the Acme intranet with a server for each department. I N T R A N E T
- 33. First, sales reps take the orders from the customers and input the information into computer order forms on their notebook computers. They compile the orders into single data files for transfer to the regional sales office. Next, sales representatives begin the process of uploading the sales onto the company’s FTP order sites, located at each of the regional sales offices. This is accomplished by using communications software on the notebook computer to dial into the regional office’s “modem center” via a cellular phone built into the notebook computer. Anywhere an organization uses a standard telephone line for remote access; a danger exists that the number, and thus the line, may be attacked by a hacker. S ecurity I ssue: Managing Remote Access:
- 34. S olutions: Acme decides to use a two-stage firewall at this point in its system. Acme decides to use the Modem Security Enforcer , that requires users to call in, and pass a two-step password test, then hangs up the system and calls the user back at a pre-established telephone number . After the salesperson successfully passes through the modem security, the salesperson encounters the second firewall located on the Sales/Marketing Web server. the second firewall located on the Sales/Marketing Web server. Acme uses a proxy server such Borderware Firewall Server which accepts the data from the salesperson's notebook-generated order file and passes it through to the FTP site on the intranet. Any data that comes back to the notebook during this process is protected by means of a Network Address Translation (also provided by Borderware's Firewall Server), which changes the actual internal addressing on information sent out to the remote computer. Here is the Sales/Marketing part of the Acme intranet with the firewalls added.
- 35. A process similar to that described here is used for transferring the data from the three sales offices to the main office. That is, the sales orders are combined into a single, larger format order and transferred to the various offices and the appropriate shipping points. Here, however, no public telephone lines are used . Rather, dedicated " T l" telephone lines are used to move the data from the sales offices to the shipping point and main office internal FTP sites, respectively. This diagram shows a typical sales order as it travels from the point of sale to the production and shipping facilities.
- 36. the regional (and central) sales offices must make available to the sales force the latest information concerning changes to product lines, pricing information, shipping delays, and so on. As with previous tasks, Acme is not only concerned that this information be made available but also that the process of making it available be as secure as possible. Also, as noted previously in the Table, all offices (sales, marketing, and finance) must be able to access production figures and shipping times from the main production facility. S ecurity I ssue: Managing Remote Access: These tasks can be accomplished using a secure e-mail system. Thus, the Acme intranet design team decides that, due to the need to pass queries and other short messages among various employees, the primary intranet system will be supplemented with a dedicated mail server system to handle only internal e-mail. S olutions:
- 37. S ecurity I ssue: Managing Internal Access to Sensitive Information Acme's Finance Department presents some unique challenges in that all of the other departments must have access to some of the data (for example, budgeting information) but should not be allowed access to other data (for example, the president's expense account) in that department.
- 38. S olutions: Acme's Secure Server Net approach to controlling data in the Finance Department. (One such product is Borderware’s Secure Server Net system) Tri Homed Gateway
- 39. Additional Security Needs: A similar approach could be used in any department that has both information that should be available company-wide and data that should be used within that department only. In addition to the firewall placement matters mentioned here, Acme will also employ other, more traditional, computer security measures. For example, all users will have unique user names and passwords, providing an additional level of security inside the firewalls. These passwords will have relatively short expiration dates and will be changed approximately every 60 days.
- 40. S ecurity I ssue: Security Issue: Virus Detection & Removal Virus detection and removal software will be used on all Acme computers (desktop and notebooks) Acme's Future: Acme will begin to automate the flow of essential data around the company. At the same time, the company will ensure with each new phase of automation that sensitive and proprietary information is protected and, as important, that the company's intranet is guarded from outside attacks by unscrupulous hackers.
- 41. The completed Acme intranet, included the firewalls described in the chapter.