Redecentralizing the Web: IPFS and Filecoin
- 1. Intro to Decentralized Systems Nicola Greco Protocol Labs
- 2. disclaimer
- 9. Part 1 Decentralized Web Part 2 Universal Services Part 3 Decentralized Storage Part 4 Cryptonetworks
- 10. Part 1
- 12. decentralization = de-concentration of power Benkler 2016
- 13. distributed system decentralized system no single authority fully trusted minimize risk from misbehaving nodes
- 14. Server <> ClientWeb Server provides the right service Server uses data responsibly Server is secure Server is always online Server is single point of reference
- 15. Server <> ClientWeb Server provides the right service Server uses data responsibly Server is secure Server is always online Server is single point of reference Server <> ServerP2P Altruistic Network Peers are equal
- 16. Server <> ClientWeb Server provides the right service Server uses data responsibly Server is secure Server is always online Server is single point of reference Server <> ServerP2P Altruistic Network Peers are equal Network <> ClientIncentivized Protocols Clients delegate their service to the network The network is “paid” to do so
- 17. 5,000,000,000+ files • Video distribution & streaming • Legal documents • 3D Models (they’re big!) • Games • Scientific data & papers • Blogs & websites • Within blockchains • Totally distributed web apps ex. forums, chat, messaging, cms, blogs, github, ... IPFS
- 19. Content Addressing Where is the data? ? http://nicolagreco.com/slides.pdf
- 20. Content Addressing Where is the data? Who has the data? ? http://nicolagreco.com/slides.pdf QmeomffUNfmQy76CQGy9N… [RFC6920] [BITTORRENT] [IPFS] [BITCOIN]
- 21. Content-addressable Web where: - data links work across application - links are cryptographic hashes - anyone can distribute data
- 23. DHT [CHORD] A D F H J O Q U SHA256( ) = GRxQ123..
- 24. DHT [CHORD] A D F H J O Q U SHA256( ) = GRxQ123..
- 25. DHT [CHORD] A D F H J O Q U SHA256( ) = GRxQ123.. LIBP2P
- 28. SLIDE: SIZE OF THE COMMUNITY Large Open Source Project Over 2000+ Contributors Over 150+ contribute Weekly
- 30. Server <> ClientWeb Server provides the right service Server uses data responsibly Server is secure Server is always online Server is single point of reference Server <> ServerP2P Altruistic Network Peers are equal Network <> ClientIncentivized Protocols Clients delegate their service to the network The network is “paid” to do so
- 33. Part 2
- 34. Universal Services decentralization beyond the web
- 36. Fair Exchange Nicola Samer Fairness Either both parties receive their inputs or none
- 37. Fair Exchange Nicola Samer Fairness Either both parties receive their inputs or none Timeliness Exchange either happens or does terminate
- 39. Fair Exchange Nicola Samer runs with the money Scenario 1
- 40. Fair Exchange Nicola Samer runs with the money Scenario 1 Nicola Samer Scenario 2
- 41. Fair Exchange runs without paying Nicola Samer runs with the money Scenario 1 Nicola Samer Scenario 2
- 43. Fair Exchange Nicola Samer Impossibility of Fair Exchange without a Trusted Third Party [Cleve1986]
- 44. Fair Exchange N S Trusted — Trust Assumptions —
- 45. Fair Exchange N S Trusted N S Building Trust — Trust Assumptions —
- 46. Fair Exchange N S Trusted N S Building Trust N S Third Party * — Trust Assumptions —
- 47. Fair Exchange — Trust Assumptions — Trusted Party
- 48. Fair Exchange — Trust Assumptions — Trusted Hardware Trusted Party
- 49. Fair Exchange — Trust Assumptions — Trusted Hardware Trusted Party Trusted Auditors
- 50. Fair Exchange — Trust Assumptions — Trusted m-of-n Trusted Hardware Trusted Party Trusted Auditors
- 51. Fair Exchange — Trust Assumptions — Trusted Majority Trusted m-of-n Trusted Hardware Trusted Party Trusted Auditors
- 53. Public Ledger Alice-Bob $2 ….. 3 MAY 2017: A-B $2 Patent
- 54. Public Ledger Alice-Bob $2 ….. 3 MAY 2017: A-B $2 3 MAY 2017: C patent Patent
- 55. State Machine Replication log application OP Log+1 -1 +1 +2 +4 -1 1 0 1 3 7 6 STATE Log 6
- 60. Digital Currency $5 A-B 5 A-B 5 A-B 5 A-B 5 A-B 5 A-B 5 A-B 5 A-B 5
- 61. Digital Currency $2 A-B 5 B-C 2 A-B 5 B-C 2 A-B 5 B-C 2 A-B 5 B-C 2 A-B 5 B-C 2 A-B 5 B-C 2 A-B 5 B-C 2 A-B 5 B-C 2
- 62. Naming Local Naming ./nicola.jpg Global Naming Trusted Party [RFC1035]
- 63. Naming Local Naming ./nicola.jpg Global Naming Trusted Party [RFC1035] Untrusted Party [RFC6962] [CW2009] [CONIKS]
- 64. Naming Local Naming ./nicola.jpg Global Naming Trusted Party [RFC1035] Untrusted Party [RFC6962] [CW2009] [CONIKS] hash( ) Qas13jdsjw Cryptographic Hash [RFC6920] [BITTORRENT] [IPFS]
- 65. Naming Local Naming ./nicola.jpg Global Naming Trusted Party [RFC1035] Blockchain [ENS] [BLOCKSTACK] [NAMECOIN] Untrusted Party [RFC6962] [CW2009] [CONIKS] hash( ) Qas13jdsjw Cryptographic Hash [RFC6920] [BITTORRENT] [IPFS]
- 66. Naming Local Naming ./nicola.jpg Global Naming Trusted Party Untrusted Party [RFC1035] [RFC6962] [CW2009] Blockchain [ENS] [BLOCKSTACK] [NAMECOIN][CONIKS] hash( ) Qas13jdsjw Cryptographic Hash [RFC6920] [BITTORRENT] [IPFS] Trusted Majority Trusted Party Cryptography
- 67. Fair Exchange of Services Nicola Samer Fairness Timeliness Either both parties receive their inputs or none Exchange either happens or does terminate Completeness If seller is honest, both parties receive their inputs Soundness
- 75. Fair Exchange of Services Trusted Majority Any Trust Trusted Hardware Trusted Party Trusted Auditors Reputation PenalizationsRewards Sigma Protocols SNARKs … [NICOLA’s MASTER] [ZKCSP] [ZKCP] …
- 76. Fair Exchange of Services Trusted Majority Any Trust Trusted Hardware Trusted Party Trusted Auditors Reputation PenalizationsRewards Sigma Protocols SNARKs … [NICOLA’s MASTER] [ZKCSP] [ZKCP] …
- 77. Fair Exchange of Services Trusted Majority Any Trust Trusted Hardware Trusted Party Trusted Auditors Reputation PenalizationsRewards Sigma Protocols SNARKs … [NICOLA’s MASTER] [ZKCSP] [ZKCP] …
- 78. Fair Exchange of Services Trusted Majority Any Trust Trusted Hardware Trusted Party Trusted Auditors Reputation PenalizationsRewards Sigma Protocols SNARKs … [NICOLA’s MASTER] [ZKCSP] [ZKCP] …
- 81. Verifiable Markets Order matching Settlement – Don’t need to trust individual service provider – Anyone can participate in the market as participant
- 82. Part 3
- 87. Decentralized Storage Store Get How do we store files without trusting the providers?
- 88. Filecoin Protocol Get - Retrieve a file Put - Store a file Pledge - Add storage
- 90. Proofs of Storage Complete Sound Public Verifiable Transparent Useful everyone with storage will generate valid proofs no adversary can generate fake proofs everyone can verify proofs there is no secret information that can generate proofs info proofs are about useful storage
- 91. Proofs of Storage h1,2 = h(h1,h2) p1 p2 p3 p4 h(1) h(2) h(3) h(4) h3,4 = h(h3,h4) hroot = h(h1,2,h3,4)
- 92. p1 p2 p3 p4 roothash Proofs of Storage
- 93. Proof of Replication Sybil attack Outsourcing attack Generation attack
- 98. Setup Challenge C Proof of Retrievability
- 99. Setup Challenge C Proof of Retrievability
- 100. Setup Challenge C Proof of Retrievability
- 111. Filecoin Markets Order matching Settlement Order matching Settlement Exchange OTC
- 112. Order Matching Storage/ Retrieval orders Store a file for 1 week at 50c GB/h Offer storage for 1 week at 50c GB/h
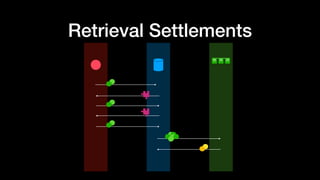
- 114. Storage Settlements
- 117. Open Questions Are there ways to do efficient proofs of replication? Are there ways to overcome front-running attacks? Are there ways to avoid miners posting proofs on chain? Can build a storage-based consensus? What are other incentives beyond economic reward?
- 118. Part 4
- 120. Bell Labs Holmdel site
- 122. Open Source
- 123. Open Source
- 124. Open Source
- 125. Open Source
- 126. Open Source
- 127. Open Source
- 128. Open Source
- 129. Open Source
- 130. Open Source
- 131. Open Source
- 132. Open Source
- 133. Open Source
- 134. Open Source
- 135. Open Source
- 136. Sharing Economy
- 137. IPFS
- 140. Text názvu Text úrovně 1 Text úrovně 2 Text úrovně 3 Text úrovně 4 Text úrovně 5
- 141. Text názvu Text úrovně 1 Text úrovně 2 Text úrovně 3 Text úrovně 4 Text úrovně 5
- 143. Text názvu Text úrovně 1 Text úrovně 2 Text úrovně 3 Text úrovně 4 Text úrovně 5 +
- 144. Text názvu Text úrovně 1 Text úrovně 2 Text úrovně 3 Text úrovně 4 Text úrovně 5
- 146. spend . to store store to earn . exchange for . . .
- 148. Free Market for Data Storage
- 149. Governance?
- 151. Thank you Samer
- 152. Thank you Samer
- 153. Question? What are other trust models? What is any-trust? What are other types of Verifiable Markets? Would this be enough for decentralizing the web? Can DDoS attacks be possible on Filecoin? How do you know Samer?
- 155. Refereed Multi-Prover YES NO NO NO
- 156. YES NO NO NO Refereed Multi-Prover
- 157. YES NO NO NO Refereed Multi-Prover
- 158. Rational Refereed Multi-Prover YES NO NO NO $$$$$$




















![Content Addressing
Where is the data?
Who has the data?
?
http://nicolagreco.com/slides.pdf
QmeomffUNfmQy76CQGy9N…
[RFC6920]
[BITTORRENT]
[IPFS]
[BITCOIN]](https://image.slidesharecdn.com/index-171211101158/85/Redecentralizing-the-Web-IPFS-and-Filecoin-20-320.jpg)

![DHT
[CHORD]
A
D
F
H
J
O
Q
U](https://image.slidesharecdn.com/index-171211101158/85/Redecentralizing-the-Web-IPFS-and-Filecoin-22-320.jpg)
![DHT
[CHORD]
A
D
F
H
J
O
Q
U
SHA256( ) = GRxQ123..](https://image.slidesharecdn.com/index-171211101158/85/Redecentralizing-the-Web-IPFS-and-Filecoin-23-320.jpg)
![DHT
[CHORD]
A
D
F
H
J
O
Q
U
SHA256( ) = GRxQ123..](https://image.slidesharecdn.com/index-171211101158/85/Redecentralizing-the-Web-IPFS-and-Filecoin-24-320.jpg)
![DHT
[CHORD]
A
D
F
H
J
O
Q
U
SHA256( ) = GRxQ123..
LIBP2P](https://image.slidesharecdn.com/index-171211101158/85/Redecentralizing-the-Web-IPFS-and-Filecoin-25-320.jpg)
















![Fair Exchange
Nicola Samer
[Cleve1986]](https://image.slidesharecdn.com/index-171211101158/85/Redecentralizing-the-Web-IPFS-and-Filecoin-42-320.jpg)
![Fair Exchange
Nicola Samer
Impossibility of Fair Exchange without a Trusted Third Party
[Cleve1986]](https://image.slidesharecdn.com/index-171211101158/85/Redecentralizing-the-Web-IPFS-and-Filecoin-43-320.jpg)


















![Naming
Local Naming
./nicola.jpg
Global Naming
Trusted Party
[RFC1035]](https://image.slidesharecdn.com/index-171211101158/85/Redecentralizing-the-Web-IPFS-and-Filecoin-62-320.jpg)
![Naming
Local Naming
./nicola.jpg
Global Naming
Trusted Party
[RFC1035]
Untrusted Party
[RFC6962]
[CW2009]
[CONIKS]](https://image.slidesharecdn.com/index-171211101158/85/Redecentralizing-the-Web-IPFS-and-Filecoin-63-320.jpg)
![Naming
Local Naming
./nicola.jpg
Global Naming
Trusted Party
[RFC1035]
Untrusted Party
[RFC6962]
[CW2009]
[CONIKS]
hash( )
Qas13jdsjw
Cryptographic
Hash
[RFC6920]
[BITTORRENT]
[IPFS]](https://image.slidesharecdn.com/index-171211101158/85/Redecentralizing-the-Web-IPFS-and-Filecoin-64-320.jpg)
![Naming
Local Naming
./nicola.jpg
Global Naming
Trusted Party
[RFC1035]
Blockchain
[ENS]
[BLOCKSTACK]
[NAMECOIN]
Untrusted Party
[RFC6962]
[CW2009]
[CONIKS]
hash( )
Qas13jdsjw
Cryptographic
Hash
[RFC6920]
[BITTORRENT]
[IPFS]](https://image.slidesharecdn.com/index-171211101158/85/Redecentralizing-the-Web-IPFS-and-Filecoin-65-320.jpg)
![Naming
Local Naming
./nicola.jpg
Global Naming
Trusted Party Untrusted Party
[RFC1035] [RFC6962]
[CW2009]
Blockchain
[ENS]
[BLOCKSTACK]
[NAMECOIN][CONIKS]
hash( )
Qas13jdsjw
Cryptographic
Hash
[RFC6920]
[BITTORRENT]
[IPFS]
Trusted
Majority
Trusted
Party
Cryptography](https://image.slidesharecdn.com/index-171211101158/85/Redecentralizing-the-Web-IPFS-and-Filecoin-66-320.jpg)








![Fair Exchange of
Services
Trusted
Majority
Any
Trust
Trusted
Hardware
Trusted
Party
Trusted
Auditors
Reputation
PenalizationsRewards
Sigma
Protocols
SNARKs …
[NICOLA’s MASTER]
[ZKCSP]
[ZKCP]
…](https://image.slidesharecdn.com/index-171211101158/85/Redecentralizing-the-Web-IPFS-and-Filecoin-75-320.jpg)
![Fair Exchange of
Services
Trusted
Majority
Any
Trust
Trusted
Hardware
Trusted
Party
Trusted
Auditors
Reputation
PenalizationsRewards
Sigma
Protocols
SNARKs …
[NICOLA’s MASTER]
[ZKCSP]
[ZKCP]
…](https://image.slidesharecdn.com/index-171211101158/85/Redecentralizing-the-Web-IPFS-and-Filecoin-76-320.jpg)
![Fair Exchange of
Services
Trusted
Majority
Any
Trust
Trusted
Hardware
Trusted
Party
Trusted
Auditors
Reputation
PenalizationsRewards
Sigma
Protocols
SNARKs …
[NICOLA’s MASTER]
[ZKCSP]
[ZKCP]
…](https://image.slidesharecdn.com/index-171211101158/85/Redecentralizing-the-Web-IPFS-and-Filecoin-77-320.jpg)
![Fair Exchange of
Services
Trusted
Majority
Any
Trust
Trusted
Hardware
Trusted
Party
Trusted
Auditors
Reputation
PenalizationsRewards
Sigma
Protocols
SNARKs …
[NICOLA’s MASTER]
[ZKCSP]
[ZKCP]
…](https://image.slidesharecdn.com/index-171211101158/85/Redecentralizing-the-Web-IPFS-and-Filecoin-78-320.jpg)