RSA-Algorithm-in-Modular-Arithmetic11 (1) (1).pptx
- 1. RSA Algorithm in Modular Arithmetic Discover the RSA algorithm, a revolutionary method for secure communication that relies on modular arithmetic and prime numbers. by Siddhanth Alape
- 2. Introduction to Cryptography and the RSA Algorithm Cryptography's Role Cryptography ensures secure communication by transforming data into an unreadable format, protecting sensitive information from unauthorized access. RSA is a widely used public-key cryptosystem. The RSA Algorithm RSA is a powerful asymmetric encryption algorithm. It relies on a pair of keys - a public key for encryption and a private key for decryption.
- 3. Key Concepts: Prime Numbers, Modular Arithmetic, Euler's Totient Function Prime Numbers A prime number has only two divisors: 1 and itself. Prime numbers are crucial for RSA's security. Modular Arithmetic Modular arithmetic deals with remainders after division. It forms the basis of RSA's mathematical operations. Euler's Totient Function Euler's Totient function counts the number of positive integers less than a given integer that are relatively prime to it. This function is key for generating RSA keys.
- 4. Generating Public and Private Keys 1 Choose two distinct large prime numbers, p and q. 2 Calculate the modulus n: n = p * q 3 Compute Euler's Totient function: φ(n) = (p - 1) * (q - 1) 4 Choose a public key exponent, e, that is relatively prime to φ(n) and 1 < e < φ 5 Calculate the private key exponent, d, such that: (e * d) mod φ(n) = 1 6 Public Key: (e, n) 7 Private Key: (d, n)
- 5. Encryption: Encoding a Message using the Public Key Message Transformation Convert the message into numerical representation, typically using ASCII encoding. Public Key Application Encrypt each numerical block (m) of the message using the public key: C = m^e mod n Ciphertext The encrypted message (C) is called the ciphertext.
- 6. Decryption: Recovering the Original Message using the Private Key Ciphertext Input The ciphertext (C) is received by the intended recipient. Private Key Application Decrypt each block of the ciphertext using the private key: m = C^d mod n Message Recovery The original message (m) is recovered, revealing the plaintext.
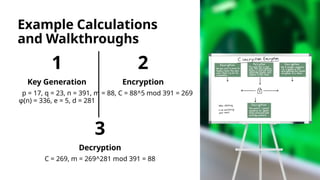
- 7. Example Calculations and Walkthroughs 1 Key Generation p = 17, q = 23, n = 391, φ(n) = 336, e = 5, d = 281 2 Encryption m = 88, C = 88^5 mod 391 = 269 3 Decryption C = 269, m = 269^281 mod 391 = 88
- 8. Summary and Applications of the RSA Algorithm RSA is a cornerstone of modern cryptography, securing online transactions, digital signatures, and data privacy. Its strength lies in the mathematical foundation of modular arithmetic and prime factorization. RSA's widespread use underscores its impact on our digital world.