SDH Principle - Huawei
- 1. www.huawei.com Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. SDH Principle
- 2. Page2Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. Contents 1. SDHOverview 2. Frame Structure & Multiplexing Methods 3. Overheads & Pointers
- 3. Page3Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. Emergence of SDH What is SDH? Synchronous Digital Hierarchy It defines a standard frame structure, a specific multiplexing method, and so on. Why did SDH emerge? Need for a system to process increasing amounts of information. New standard that allows interconnecting equipment of different suppliers.
- 4. Page4Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. Advantages of SDH Interfaces PDH electrical interfaces Only3regionalstandards: European(2.048Mb/s), Japanese, NorthAmerican (1.544Mb/s) PDH optical interfaces Nostandards, manufacturers developattheirwill. SDH electrical interfaces Universalstandards SDH optical interfaces Canbeconnectedto differentvendors’ optical transmissionequipments.
- 5. Page5Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. 140 Mb/s 34 Mb/s 34 Mb/s 8 Mb/s 8 Mb/s 2 Mb/s 140 Mb/s Not suitable for huge-volume transmission Headache for networkplanners More equipment to achieve this functionality More equipment More floor space More power More costs Demultiplexers Multiplexers Multiplexing methods: Level by level Disadvantages of PDH
- 6. Page6Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. Advantages of SDH Lower rate SDH to higher rate SDH (STM-1 STM-4 STM-16 STM-64) 4:1 STM-1 A STM-1 B STM-1 C STM-1 D A B D C B A D C B A … STM-4 One Byte from STM-1 B --- Synchronous multiplexing method and flexible mapping structure --- Multistage pointer to align PDH loads in SDH frame, thus, dynamic drop-and-insert capabilities What about PDH? Multiplexing methods: byte interleaved
- 7. Page7Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. Advantages of SDH OAM function PDH Intheframestructure ofPDHsignals, there arefewoverheadbytes usedforOAM. WeakOAMfunction SDH Abundantoverheads bytesforOAM Remote&Centralized Management Fastcircuitprovisioning fromcentralizedpoint
- 8. Page8Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. Advantages of SDH Processing PDH ATMSDH Ethernet Pack SDHNetwork Processing PDH ATMSDH Ethernet Transmit Receive Container STM-N STM-N Container Service Signal Flow Model Unpack Compatibility
- 9. Page9Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. Comparison between SDH and PDH Low bandwidth utilization ratio In PDH, E4 signal (140Mbits/s) can contain 64 E1 signals. In SDH, STM-1 (155 Mbits/s) can only carry 63 E1 signals. Complex mechanism of pointer justification Influence of excessive use of software on system security
- 10. Page10Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. Contents 1. SDH Overview 2. Frame Structure & Multiplexing Methods 3. Overheads & Pointers
- 11. Page11Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. SDH Frame Structure FromITU-T G.707: 1. One frame lasts for125 microseconds (8000 frames/s) 2. Rectangularblockstructure 9 rows and 270 columns (Basic frame: STM-1) 3. Each unit is one byte (8 bits) 4. Transmission mode: Byte by byte, row by row, fromleft to right, fromtop to bottom Bit rate of STM-1= 9*270*8*8000 123456789 270 Columns 9 rows Frame = 125 us
- 12. Page12Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. SDH Frame Structure Frame = 125 us 9 MSOH AU-PTR Information Payload RSOH 123456789 270 Columns 9 rows Three parts: SOH AU-Pointer Information Payload
- 13. Page13Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. SDH Frame Structure Information Payload √ Also known as Virtual Container level 4 (VC-4) √ Used to transport low speed tributary signals √ Contains low rate signals and Path Overhead (POH) √ Location: rows #1 ~ #9, columns #10 ~ #270 Information Payload √ Also known as Virtual Container level 4 (VC-4) √ Used to transport low speed tributary signals √ Contains low rate signals and Path Overhead (POH) √ Location: rows #1 ~ #9, columns #10 ~ #270 9 MSOH AU-PTR Payload RSOH 270 Columns HPOH 1 package package low rate signal LPOH, TU-PTR LPOH, TU-PTR 9 rows Data package
- 14. Page14Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. SDH Frame Structure Functions: Fulfills the section layer OAM 9 270 Columns 9 rows Types of Section Overhead 1. RSOH monitors the regenerator section 2. MSOH monitors the multiplexing section Location: 1. RSOH: rows #1 ~ #3, columns #1 ~ #9 2. MSOH: rows #5 ~ #9, columns #1 ~ #9 12356789 MSOH AU-PTR Information Payload RSOH Section OverheadSection Overhead
- 15. Page15Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. SDH Frame Structure 9 MSOH AU-PTR Information Payload RSOH 270 Columns 9 rows 4 Function: Indicates the first byte of VC4 Location: row #4, columns #1 ~ #9 J 1 AU-PTRAU-PTR
- 16. Page16Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. SDH Multiplexing Features SDH Multiplexing includes: Low to high rate SDH signals (STM-1 STM-N) PDH to SDH signals (2M, 34M & 140M STM-N) Other hierarchy signals to SDH Signals (IP STM- N) Some terms and definitions: Mapping Aligning Multiplexing Go to glossary
- 17. Page17Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. AU-4 TU-3TUG-3 VC-3 C-3 VC-4 C-4 TU-12 VC-12 C-12 TUG-2 ×3 ×1 ×7 ×3 E4 signal E3 signal E1 signal Multiplexing Mapping Aligning STM-1 AUG-1 ×1 ×1 AUG-4 AUG-16 AUG-64 STM-4 STM-16 STM-64 ×1 ×1 ×1 ×4 ×4 ×4 Go to glossary C-4-4cVC-4-4cAU-4-4c ×1 C-4-16cVC-4-16cAU-4-16c ×1 C-4-64cVC-4-64cAU-4-64c×1 SDH Multiplexing Structure
- 18. Page18Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. From 140Mb/s to STM-N 140M Rate adaptation Add HPOH C4 9 1 260 125 μs 1 Next Mapping VC4 1 9 125μs 1 261 H P O H
- 19. Page19Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. From 140Mb/s to STM-N Add AU-PTR Add SOH Aligning AU-PTR AU-4 10 270 X1 AUG-1 Multiplexing AUG-N 1 270 RSOH MSOH Info PayloadAU-PTR 9 STM-1 Add SOH One STM-1 frame can load only one 140Mbit/s Signal 1 270N RSOH MSOH Info PayloadAU-PTR 9 STM-N
- 20. Page20Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. From 34Mb/s to STM-N 34M Rate Adaptation Add LPOH C3 1 84 9 125μs 1 1 9 VC3 L P O H 125μs 1 85 Next Mapping
- 21. Page21Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. From 34Mb/s to STM-N 1st align Fill gap ×3 86 TU-3 1 H1 H2 H3 1 9 1 86 1 9 H1 H2 H3 R TUG-3 Multiplexing H P O H R R VC-4 9 1 1 2613 Same procedure as 140M Aligning
- 22. Page22Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. From 2Mb/s to STM-N 2M Next page 125μs 1 4 C12 1 9 4LPOH VC12 1 1 9 Rate Adaptation Add LPOH Add TU-PTR Aligning TU12 1 4 1 9 TU-PTRMapping
- 23. Page23Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. From 2Mb/s to STM-N X 3 1 12 TUG-2 1 9 X 7 Multiplexing R R TUG-3 1 86 1 9 Multiplexing Same procedure as 34M
- 24. Page24Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. Questions What are the main parts of SDH Frame structure? What is the transmission rate of STM-4? How to calculate it ?
- 25. Page25Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. Contents 1. SDH Overview 2. Frame Structure & Multiplexing Methods 3. Overheads & Pointers
- 26. Page26Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. Overheads Overheads Section Overhead (SOH) Path Overhead (POH) Regenerator Section Overhead (RSOH) Multiplex Section Overhead (MSOH) High OrderPath Overhead (HPOH) Low OrderPath Overhead (LPOH)
- 27. Page27Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. Overheads A1 A1 A1 A2 A2 A2 J0 X X B1 ● ● E1 ● F1 X X D1 ● ● D2 ● D3 AU-PTR B2 B2 B2 K1 K2 D4 D5 D6 D7 D8 D9 D10 D11 D12 S1 M1 E2 HPOH:VC-3/4 J1 B3 C2 G1 F2 H4 F3 K3 N1 RSOHMSOH 1 2 3 4 5 6 7 8 9 10 1 2 3 4 5 6 7 8 9 ● Media dependent bytes (Radio-link, Satellite) X Reserved for National use Huawei propriety bytes LPOH: VC-11/12 V5 J2 N2 K4
- 28. Page28Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. A1 and A2 Bytes Framing Bytes Indicate the beginning of the STM-N frame Bytes are unscrambled A1 = f6H (11110110), A2 = 28H (00101000) STM-N: (3XN) A1 bytes, (3XN) A2 bytes STM-N STM-N STM-N STM-N STM-N STM-N Finding frame head
- 29. Page29Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. A1 and A2 Bytes Frame Next process Find A1,A2 OOF LOF N Y AIS over 3ms over 625μs (5 frames)
- 30. Page30Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. D1 ~ D12 Bytes Data Communications Channel (DCC) Bytes RS-DCC – D1 ~ D3 – 192 Kbit/s (3x64 Kbit/s) MS-DCC – D4 ~ D12 – 576 Kbit/s (9x64 Kbit/s) TMN DCC channel NE NE NENE OAM Information: Operation, Administration and maintenance
- 31. Page31Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. E1 and E2 Bytes Orderwire Bytes E1 – RS Orderwire Byte Used between regenerators E2 – MS Orderwire Byte Used between multiplexers Digital telephone channel E1-RS, E2-MS E1 and E2 NE NE NENE
- 32. Page32Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. B1 Byte Bit interleaved Parity Code (BIP-8) Byte A parity code (even parity) Used to check the transmission errors over the RS B1 BBE is represented by RS-BBE (performance event) Tx 2#STM-N Rx 1#STM-N Calculate B 1#STM-N 2#STM-N Calculate B’ A1 00110011 A2 11001100 A3 10101010 A4 00001111 B 01011010 BIP-8 B1 = B STM-NB1 B Compare B’ & B RS-BBE
- 33. Page33Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. B2 Byte Bit interleaved Parity Code (MS BIP-24) Byte BIP-24 is used to check the bit errors over the MS B2 BBE is represented by MS-BBE (performance event) The working mechanism of B2 is same as B1
- 34. Page34Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. M1 Byte Multiplexing Section Remote Error Indication Byte A return message from Rx to Tx ,when Rx find B2 bit errors Value is the same as the count of BIP-24xN (B2) bit errors Tx generate corresponding performance event MS-FEBBE Tx Rx Traffic Generat e MS- FEBBE MS-REI Find B2 bit errors Generate MS- BBE Return M1
- 35. Page35Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. K1 and K2 (b1-b5) Bytes Automatic Protection Switching (APS) bytes Transmitting APS protocol Used for network multiplexing protection switch function P WTR WTR P I I I I P S S P
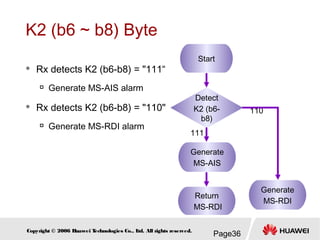
- 36. Page36Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. K2 (b6 ~ b8) Byte Rx detects K2 (b6-b8) = "111“ Generate MS-AIS alarm Rx detects K2 (b6-b8) = "110" Generate MS-RDI alarm Generate MS-AIS Start Detect K2 (b6- b8) Return MS-RDI Generate MS-RDI 111 110
- 37. Page37Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. S1 Byte Synchronization Status Message Byte (SSB): S1 b1 ~ b4 Value indicates the external clock ID (Extended SSM) b5 ~ b8 Value indicates the sync. Level (Standard SSM)bits 5 ~ 8 Description 0000 Quality unknown (existing sync. Network) 0010 G.811 PRC 0100 SSU-A (G.812 transit) 1000 SSU-B (G.812 local) 1011 G.813 (Sync. Equipment Timing Clock) 1111 Do not use for sync (DNU).
- 38. Page38Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. Path Overheads J1 B3 C2 G1 F2 H4 F3 K3 N1 VC-n Path Trace Byte Path BIP-8 Path Signal Label Path Status Path User Channel TU Multiframe Indication Path User Channel AP Switching Network Operator Higher Order Path Overhead 1 2 3 4 5 6 7 8 9 10 1 2 3 4 5 6 7 8 9 R S O H M S O H A U – P T R
- 39. Page39Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. J1 Byte Next process Detect J1 Match HP-TIM YN Path trace byte The first byte of VC-4 User-programmable (HUAWEI SBS) The received J1 should match the expected J1
- 40. Page40Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. B3 Byte Next process Verify B3 YN Correct HP-BBE Path bit parity Even parity code Used to detect bit errors Mechanism is same as B1 and B2
- 41. Page41Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. C2 Byte Detect C2 00H HP-UNEQMatch HP-SLMNext process Insert AIS downward N Y NY Signal label byte The received C2 should match with the expected C2 Specifies the mapping type in the VC-n 00H Unequipped 02H TUGstructure 13H ATMmapping
- 42. Page42Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. VC-12VC-12VC-12VC-12 K4N2J2V51 9 1 4 500μs VC-12 multi-frame Low Order Path Overhead V5 Indicated by TU-PTR Error checking, Signal Label and Path Status of VC-12 b1-b2 ErrorPerformance Monitoring(BIP-2) b3 ReturnErrordetectedin VC-12(LP-REI) b8 Returnalarmdetectedin VC-12(LP-RDI) Path Overheads
- 43. Page43Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. Pointers Pointers Administrative Unit Pointer (AU-PTR) Tributary Unit Pointer (TU-PTR) Bytes indicated AU-PTR VC-4 J1 TU-PTR VC-3 J1 VC-12 V5
- 44. Page44Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. AU-PTR RSOH MSOH MSOH RSOH H1YYH2FF H3H3H3 H1YYH2FFH3H3H3 0 --- 1--- --- --- --- --- --- --- --- --- --- 86 696 --- 697 --- --- --- --- --- --- --- --- 782 1 9 270 1 4 9 1 4 9 125μs 250μs 522 --- 523 --- --- --- --- --- --- --- --- 608 435 --- 436 --- --- --- --- --- --- --- --- 521 Negative justification Positive justification 0 --- 1 --- --- --- --- --- --- --- --- --- --- 86 435 --- 436 --- --- --- --- --- --- --- --- 521 87 --- 88 --- --- --- --- --- --- --- --- --- 173 87 --- 88 --- --- --- --- --- --- --- --- --- 173
- 45. Page45Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. TU-PTR VC3 H1 H2 H3 TU POINTERS VC- 12 VC- 12 VC- 12 VC- 12 V 1 V 2 V 3 V 4 1 4 1 9 TU POINTERS TU Multi-frame 500μs
- 46. Page46Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. Questions Which byte is used to report the MS-AIS and MS-RDI? What is the mechanism for R-LOF generation? Which byte implements the RS (MS/HP) error monitoring?
- 47. Page47Copyright © 2006 Huawei Technologies Co., Ltd. All rights reserved. Summary SDH Overview Frame Structure & Multiplexing Methods Overheads & Pointers
Editor's Notes
- #2: Content SDH Overview...........................................................................Page 1 Frame Structure & Multiplexing Methods.................................Page 9 Overheads & Pointers ...............................................................Page 24
- #3: Objectives Upon completion of this course, you will be able to: Understand the basic of SDH multiplexing standard Know the features, applications and advantages of SDH based equipment References SDH Principle Manual ITU-T G.701, G.702, G.707
- #4: SDH is the abbreviation of Synchronous Digital Hierarchy. SDH is a transmission system (protocol) which defines the characteristic of digital signals, including frame structure, multiplexing method, digital rates hierarchy, and interface code pattern, and so on.
- #5: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle PDH (Plesiochronous Digital Hierarchy) electrical interfaces There are only some regional standards: European Series, North American Series and Japanese Series, instead of universal standards for electrical interface. Each of them has different electrical interface rate levels, frame structures and multiplexing methods. This makes it difficult for international interconnection. PDH optical interfaces No universal standards for optical interfaces. All PDH equipment manufacturers use their own line codes to monitor the transmission performance in the optical links. So equipment at the two ends of a transmission link must be provided by the same vendor. This causes many difficulties for network structuring, management and network interconnection. SDH electrical interfaces SDH system provides universal standards for network node interfaces (NNI), including standards on digital signal rate level, frame structure, multiplexing method, line interface, etc. So SDH equipment of different vendors can be easily interconnected. SDH optical interfaces Line interfaces (here refers to optical interface) adopt universal standards. Line coding of SDH signals is only universal scrambling. Therefore the opposite-terminal equipment can be interconnected with SDH equipment of different vendors via standard descrambler alone.
- #6: As PDH system adopts asynchronous multiplexing method, the locations of the low-rate signals are not regular nor fixed when they are multiplexed into higher-rate signals. That is to say, the locations of the lower signals are unable to be identified from the higher speed signals. Therefore, low-rate signals can not be directly added/dropped from PDH high-rate signals. For example, 2Mb/s signals can not be directly added/dropped from 140Mb/s signals. Here arise two problems: Adding/dropping low-rate signals from high-rate signals must be conducted level by level. This not only enlarges the size and increases cost, power consumption and complexity of equipment, but also decreases the reliability of the equipment. Since adding/dropping low-rate signals to high-rate ones must go through many stages of multiplexing and de-multiplexing, impairment to the signals during multiplexing/de-multiplexing processes will increase and transmission performance will deteriorate. This is unbearable in large capacity transmission. That's the reason why the transmission rate of PDH system has not being improved further. No universal network management interface in PDH system Different parts of the network may use different network management systems, which are obstacles in forming an integrated telecommunication management system (TMN).
- #7: As low-rate SDH signals are multiplexed into the frame structure of high-rate SDH signals via byte interleaved multiplexing method, their locations in the frame of high-rate SDH signal are fixed and regular, or say, predictable. Therefore, low-rate SDH signals, e.g. 155Mb/s, (Synchronous Transport Module STM-1 ), can be directly added to or dropped from high-rate signals, e.g., 2.5Gb/s (STM-16 ). This simplifies the multiplexing and de-multiplexing processes of signals and makes SDH hierarchy especially suitable for high rate and large capacity optical fiber transmission systems. As synchronous multiplexing method and flexible mapping structure are employed, PDH low-rate tributary signals (e.g., 2Mb/s ) can also be multiplexed into SDH signal frame (STM-N). Their locations in STM-N frame are also predictable. So low-rate tributary signals can be directly added to or dropped from STM-N signals. Note that this is different from the above process of directly adding/dropping low-rate SDH signals to/from high-rate SDH signals. Here it refers to direct adding/dropping of low-rate tributary signals, such as 2Mb/s, 34Mb/s, and 140Mb/s, to/from SDH signals. This saves lots of multiplexing/de-multiplexing equipment (back-to-back equipment), enhances reliability, and reduces signal impairment, and the cost, power consumption and complexity of the equipment. Adding/dropping of services is further simplified.
- #8: PDH OAM function In the frame structure of PDH signals, there are few overhead bytes used for operation, administration and maintenance (OAM). The fact that few overhead bytes are used for the OAM of PDH signals is also a disadvantage for layered management, performance monitoring, real-time service dispatching, bandwidth control, and alarm analyzing and locating of the transmission network. SDH OAM function Abundant overhead bits for operation, administration and maintenance (OAM) functions are arranged in the frame structures of SDH signals. This greatly enforces the network monitoring function, i.e. automatic maintenance. Some redundancy bits must be added during line coding for line performance monitoring because few overhead bytes are arranged in PDH signals. For example, in the frame structure of PCM30/32 signals, only the bits in TS0 and TS16 time slots are used for OAM function. The abundant overheads in SDH signals account for 1/20 of the total bytes in a frame. It greatly enhances the OAM function and reduces the cost of system maintenance that occupies most of the overall cost of telecommunication equipments. The overall cost of SDH system is less than that of PDH system and estimated to be only 65.8% of that of the later.
- #9: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle SDH has high compatibility, which means that the SDH transmission network and the existing PDH transmission network can work together while establishing SDH transmission network. SDH network can be used for transmitting PDH services, as well as signals of other hierarchies, such as asynchronous transfer mode (ATM) signals and FDDI signals. How does the SDH transmission network achieve such compatibility? The basic transport module (STM-1) of SDH signals in SDH network can accommodate three PDH digital signal hierarchies and other hierarchies such as ATM, FDDI and DQDB. This reflects the forward and backward compatibility of SDH and guarantees smooth transitions from PDH to SDH network and from SDH to ATM. How does SDH accommodate signals of these hierarchies? It simply multiplexes the low-rate signals of different hierarchies into the frame structure of the STM-1 signals at the boundary of the network (e.g. SDH/PDH start point) and then de-multiplexes them at the boundary of the network (end point). In this way, digital signals of different hierarchies can be transmitted in the SDH transmission network.
- #10: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle Low bandwidth utilization ratio One significant advantage of SDH is that system reliability is greatly enhanced (highly automatic OAM) since many overhead bytes for OAM function are employed in SDH signals. To transmit the same amount of valid information, PDH signals occupy less frequency bandwidth (transmission rate) than SDH signals, i.e. PDH signals use lower rate. In other words, STM-1 occupies a frequency bandwidth larger than that needed by PDH E4 signals (they have the same amount of information). Complex mechanism of pointer justification The pointer constantly indicates the location of low-rate signals so that specific low-rate signals can be properly de-multiplexed in time of "unpacking". However, the pointer function increases the complexity of the system. Most of all, it generates a kind of special jitter in SDH system ---- a combined jitter caused by pointer justification. This jitter will deteriorate the performance of low-rate signals being de-multiplexed. Influence of excessive use of software on system security One of the features of SDH is its highly automatic OAM, which means that software constitutes a large proportion in the system. As a result, SDH system is vulnerable to computer viruses, manual mis-operation and software fault on network layer.
- #12: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle ITU-T defines the frames of STM-N as rectangle block frame structure in unit of byte (8bit). The frame structure of STM-N signals is 9 rows 270N columns. The N here is equal to the N in STM-N, ranging from 1, 4, 16, 64, and 256. The N indicates that this signal is multiplexed by N STM-1 signals via byte interleaved multiplexing. This explains that the frame structure of STM-1 signals is a block structure of 9 rows 270 columns. When N STM-1 signals are multiplexed into STM-N signal via byte interleaved multiplexing, only the columns of STM-1 signals are multiplexed via byte interleaved multiplexing. While the number of rows remains constantly to be 9. It is known that signals are transmitted bit-by-bit in lines. Then what is the sequence of transmission? The principle for SDH signal frame transmission is: the bytes (8-bit) within the frame structure is transmitted bit-by-bit from left to right and from top to bottom. After one row is transmitted, the next row will follow. After one frame is completed, the next frame will start. ITU-T defines the frequency to be 8000 frames per second for all levels in STM hierarchy. That means the frame length or frame period is a constant value of 125us. Constant frame period is a major characteristic of SDH signals. The constant frame period makes the rates of STM-N signals regular. For example, the data rate of STM-4 transmission is constantly 4 times as that of STM-1, and STM-16 is 4 times of STM-4 and 16 times of STM-1. Such regularity of SDH signals makes it possible to directly add/drop low-rate SDH signals to/from high-rate SDH signals, especially for high-capacity transmission.
- #13: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle The frame of STM-N consists of three parts Section Overhead (including Regenerator Section Overhead ---- RSOH and Multiplex Section Overhead ---- MSOH) Administrative Unit Pointer---- AU-PTR Information Payload
- #14: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle The Information Payload is a place in the STM-N frame structure to store various information code blocks to be transmitted by STM-N. It functions as the "wagon box" of the truck---STM-N. Within the box are packed low-rate signals ---- cargoes to be shipped. To monitor the possible impairment to the cargoes (the packed low-rate signals) on a real-time basis during transmission, supervisory overhead bytes ---- Path Overhead (POH) bytes are added into the signals when the low-rate signals are packed. As one part of payload, the POH, together with the information code blocks, is loaded onto STM-N and transmitted on the SDH network. The POH is in charge of monitoring, administrating and controlling (somewhat similar to a sensor) the path performances for the packed cargoes (the low-rate signals). What is a path? Let's take the following example. STM-1 signals can be demultiplexed into 63 2Mb/s signals. In other words, STM-1 can be regarded as a transmission path divided into 63 bypaths. Each bypath, which is equal to a low-rate signal path, transmits corresponding low-rate signals. The function of the Path Overhead is to monitor the transmission condition of these bypaths. The 63 2Mb/s paths multiplex and form the path of STM-1 signals that can be regarded as a "section" here. Paths refer to corresponding low-rate tributary signals. The function of POH is to monitor the performance of these low-rate signals transmitted via the STM-N on the SDH network. This is consistent with the analogy in which the STM-N signal is regarded as a truck and the low-rate signals are packed and loaded onto the truck for transmission.
- #15: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle The Section Overhead (SOH) refers to the auxiliary bytes which is necessary for network operation, administration and maintenance (OAM) to guarantee normal and flexible transmission of Information Payload. For example, the Section Overhead can monitor the impairment condition of all "cargoes" in STM-N during transmission. The function of POH is to locate the certain impaired cargo in case impairments occurred. SOH implements the overall monitoring of cargoes while the POH monitors a specific cargo. The Section Overhead is further classified into Regenerator Section Overhead (RSOH) and Multiplex Section Overhead (MSOH). They respectively monitor their corresponding sections and layers. Then, what's the difference between RSOH and MSOH? In fact, they have different monitoring domains. For example, if STM-16 signals are transmitted in the fiber, the RSOH monitors the overall transmission performance of STM-16 while the MSOH monitors the performances of each STM-1 of the STM-16 signals. RSOH, MSOH and POH provide SDH signals with monitoring functions for different layers. For a STM-16 system, the RSOH monitors the overall transmission performance of the STM-16 signal; the MSOH monitors the transmission performances of each STM-1 signal; and the POH monitors the transmission performances of each packaged low-rate tributary signal (e.g. 2Mb/s) in STM-1. Through these complete monitoring and management functions for all levels, you can conveniently conduct macro (overall) and micro (individual) supervision over the transmission status of the signal and easily locate and analyze faults.
- #16: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle The Administrative Unit Pointer within column 9 N of row 4 of the STM-N frame is 9 N bytes in total. What's the function of AU-PTR? We have mentioned before those low-rate tributaries (e.g. 2Mb/s) could be added/dropped directly from high-rate SDH signals. Because the locations of low-rate signals within a high-rate SDH frame structure are predictable, i.e. regular. The predictability can be achieved via the pointer overhead bytes function in the SDH frame structure. The AU-PTR indicates the exact location of the first byte of the information payload within the STM-N frame so that the information payload can be properly extracted at the receiving end according to the value of this location indicator (the value of the pointer). Let's make it easier. Suppose that there are many goods stored in a warehouse in unit of pile. Goods (low-rate signals) of each pile are regularly arranged (via byte interleaved multiplexing). We can locate a piece of goods within the warehouse by only locating the pile this piece of goods belongs to. That is to say, as long as the location of the first piece of goods is known, the precise location of any piece within the pile can be directly located according to the regularity of their arrangement. In this way you can directly carry (directly add/drop) a given piece of goods (low-rate tributary) from the warehouse. The function of AU-PTR is to indicate the location of the first piece of goods within a given pile. In fact, the pointer is further classified into higher order pointer and low order pointer. The higher order pointer is AU-PTR while the lower order pointer is TU-PTR (Tributary Unit Pointer). The function of TU-PTR is similar to that of AU-PTR except that the former indicates smaller "piles of goods".
- #17: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle SDH multiplexing includes three types: multiplexing of lower-order SDH signals into higher-order SDH signals and multiplexing of low-rate tributary signals (e.g. 2Mb/s, 34Mb/s and 140Mb/s) into SDH signals ----STM-N, and other hierarchy signals to SDH Signals. The second type of multiplexing from Low to high rate SDH signals is conducted mainly via byte interleaved by multiplexing four into one, e.g. 4STM-1-->STM-4 and 4STM-4-->STM-16. after the multiplexing, the rate of the higher-level STM-N signals is 4 times that of the next lower-level STM-N signals. During the byte interleaved multiplexing, the information payload, pointer bytes of each frame are multiplexed via interleaved multiplexing based on their original values. The second type of multiplexing is mostly used for multiplexing of PDH signals into the STM-N signals. The last one is other hierarchy signals e.g. IP or ATM signals to SDH Signals.
- #18: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle ITU-T defined a complete multiplexing structure, through which digital signals of three PDH hierarchies can be multiplexed into STM-N signals. This multiplexing structure includes some basic multiplexing units: C - Container, VC - Virtual Container, TU - Tributary Unit, TUG - Tributary Unit Group, AU - Administrative Unit, and AUG - Administrative Unit Group. The suffixes of these multiplexing units denote their corresponding signal levels. The multiplexing route used in a country or an area must be unique. The route on the slide is the most usual and adopted in most of countries. Low-rate tributaries are multiplexed into STM-N signals through three procedures: mapping, aligning and multiplexing. SDH mapping is a procedure by which tributaries are adapted into virtual containers at the boundary of an SDH network, e.g. E1 into VC-12. SDH aligning is a procedure to add TU-PTR or AU-PTR into the VC-12, VC-3 or VC4. The pointer value constantly locates the start point of VC within the TU or AU. So that the receiving end can correctly separate the corresponding VC. SDH multiplexing, a relatively simple concept, is the procedure by which the TUs are organized into the higher order VC or the AUs are organized into STM-N via byte interleaving.
- #19: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle From 140Mb/s to C4 First, the 140Mb/s PDH signals are adapted via bit rate justification (bit stuffing method) into C-4, which is a standard information structure used to accommodate 140Mb/s PDH signals. After being processed via bit rate justification techniques, service signals of various rates involved in SDH multiplexing must be loaded into a standard container corresponding to the rate level of the signal: 2Mb/s---C-12, 34Mb/s---C-3 and 140Mb/s---C-4. The main function of a container is for bit rate justification. The frame structure of C-4 is block frame in unit of bytes, with the frame frequency of 8000-frame per second. From C4 to VC4 A column of path overhead bytes (higher-order path overhead VC-4-POH) shall be added in front of the C-4 block frame during multiplexing in order to monitor the 140Mb/s path signals. Then the signals become a VC-4 information structure. The virtual container, a kind of information structure whose integrity is always maintained during transmission on the SDH network, can be regarded as an independent unit (cargo package). It can be flexibly and conveniently added/dropped at any point of the path for synchronous multiplexing and cross-connection processing. Now you might get the idea that VC-4 is in fact the information payload of the STM-1 frame. The process of packing PDH signals into C and adding the corresponding path overhead to form the information structure of VC is called mapping.
- #20: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle From VC4 to AU4 By adding an Administrative Unit Pointer --- AU-PTR before the VC-4, the signal is changed from VC-4 into another information structure--- Administrative Unit AU-4. The function of AU-PTR is to indicate the location of the higher order VC within the STM frame. Under the pointer function, the higher order VC is allowed to "float" within the STM frame, i.e. the frequency offsets and phase differences to a certain degree between VC-4 and AU-4 are tolerable. Because the AU-PTR is outside of the payload area and co-located with the section overhead instead. This guarantees that the AU-PTR can be accurately found in the corresponding location. Then the VC-4 can be localized by the AU pointer and disassembled from STM-N signals. From AU4 to AUG (N) One or more AUs with fixed locations within the STM frame form an AUG ---- Administrative Unit Group. The location of the first byte of the VC-4 with respect to the AU-4 pointer is given by the pointer value. The AU-4 is placed directly in the AUG. From AUG (N) to STM-N The last step is to add corresponding SOH to AU-4 to form STM-N signals. During being multiplexed, the N AUGs are one-byte interleaved into this structure and have a fixed phase relationship with respect to the STM-N.
- #21: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle From 34Mb/s to C3 Similarly, 34Mb/s signals are first adapted into the corresponding standard container -- C-3 through bit rate justification. From C3 to VC3 After adding corresponding POH, the C-3 is packed into VC-3 with the frame structure of 9 rows 85 columns.
- #22: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle From VC3 to TU3 For the convenience of locating VC-3 at the receiving and separating it from the high-rate signals, a three-byte pointer, TU-PTR (Tributary Unit Pointer), is added to the VC-3 frame. Then what is the function of a tributary pointer? The TU-PTR is used to indicate the specific location of the first byte of the lower order VC within the tributary unit TU. It is similar to an AU-PTR that indicates the location of the first byte of the VC-4 within the STM frame. Actually, the operating principles of these two kinds of pointers are similar. From TU3 to TUG3 The TU-3 frame structure is imcomplete. First fill the gap to form the frame structure of TUG3. From TUG3 to C4, VC4 and STM-N Three TUG-3 can be multiplexed into the C-4 signal structure via byte interleaved multiplexing method. The TUG-3 is a 9‑row by 86-column structure. Two columns of stuffed bits are added to the front of the composite structure of 3 TUG-3 to form a C-4 information structure. The last step is to multiplex C-4 into STM-N. This is similar to the process of multiplexing 140Mb/s signals into STM-N signals: C-4-->VC-4-->AU-4-->AUG-->STM-N.
- #23: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle At present, the most frequently used multiplexing method is multiplexing of 2Mb/s signals into STM-N signals. It is also the most complicated method of multiplexing PDH signals into SDH signals. From 2Mb/s to C12 First, the 2Mb/s signal shall be adapted into the corresponding standard container C-12 via rate adaptation. From C12 to VC12 To monitor on a real-time basis the performance of each 2Mb/s path signal during transmission on SDH network, C-12 must be further packed ---- adding corresponding path overhead (lower order overhead)---- to form a VC-12 information structure. The LP-POH (lower order path overhead) is added to the notch in the top left corner of each basic frame. Since the VC can be regarded as an independent entity, dispatching of 2Mb/s services later is conducted in unit of VC-12. From VC12 to TU12 For correct aligning of VC-12 frames in the receiving end, a four-byte TU-PTR is added to the four notches of the VC-12 multi-frame. Then the information structure of the signal changes into TU-12 with 9 rows 4 columns. The TU-PTR indicates the specific location of the start point of the first VC-12 within the multi-frame.
- #24: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle From TU12 to TUG2 Three TU-12 forms a TUG-2 via byte interleaved multiplexing. The TUG-2 has the frame structure of 9 rows by 12 columns. From TUG2 to TUG3 Seven TUG-2 can be multiplexed into a TUG-3 information structure via byte interleaved multiplexing. Note that this information structure formed by the 7 TUG-2 is 9-row by 84-column. Two rows of fixed stuff bits shall be added in front of the structure. The TUG-3 is a 9‑row by 86-column structure with the first two columns of fixed stuff. From TUG3 to C4, VC4 and STM-N The procedures of multiplexing the TUG-3 information structure into STM-N are the same as mentioned before.
- #25: The frame of STM-N consists of three parts Section Overhead (including Regenerator Section Overhead ---- RSOH and Multiplex Section Overhead ---- MSOH) Administrative Unit Pointer---- AU-PTR Information Payload with POH There are 9 rows and 270N columns in the STM-N frame, which will be transmitted 8000 times per second. Here the value of N equals to 4 for STM-4. 9 (rows) X 270 X 4 (columns) X 8 (bits) X 8000 (frame/second) = 622080000 bits/second. It is so called 622 Mbits/s
- #27: As mentioned before, the functions of overhead are to implement layered monitoring management for SDH signals. The monitoring is classified into section layer monitoring and path layer monitoring. The section layer monitoring is further classified into regenerator section layer monitoring and multiplex section layer monitoring while the path layer monitoring is further classified into higher order path layer and lower order path layer. Thus the layered monitoring for STM-N is implemented. For example, in a STM-16 system, the regenerator section overhead monitors the overall STM-16 signal while the multiplex section overhead further monitors each of the 16 STM-1. Furthermore, the higher order path overhead monitors the VC-4 of each STM-1 and the lower order path overhead can monitor each of the 63 VC-12 in the VC-4. Hence the multistage monitoring functions from 2.5Gb/s to 2Mb/s are implemented.
- #28: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle Then, how are these monitoring functions implemented? They are implemented via different overhead bytes. The overhead of each layer, including RSOH, MSOH, HPOH, and LPOH consists of some different bytes for different OAM function. Especially, several overhead bytes e.g. K1 and K2 bytes are very important for maintenance and troubleshooting. According to ITU-T recommendation, there are some overhead bytes reserved for national use.
- #29: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle Like a pointer, the function of the frame bytes is alignment. The first step is to properly extract each STM-N frame from the received continuous signal stream at the receiver. The function of the bytes A1 and A2 is to locate the start of the STM-N frame. So the receiver can align and extract the STM-N frame from the information stream via these two bytes and further align a specific lower-rate signal within the frame via the pointers. How does the receiver align the frames via the A1 and A2 bytes? The A1 and A2 have fixed value, i.e. fixed bit patterns: A1: 11110110 (f6H) and A2: 00101000(28H). The receiver monitors each byte in the stream. After detecting 3N successive f6H bytes followed by 3N 26H bytes (there are three A1 and three A2 bytes within an STM-1 frame), the receiver determines that an STM-N frame starts to be received. By aligning the start of each STM-N frame, the receiver can identify different STM-N frames and disassemble them. STM-N signals shall be scrambled before being transmitted via the line so that the receiver can extract timing signals from the line. But the A1 and A2 framing bytes shall not be scrambled for the receiver to properly align them. Thus it is convenient to extract the timing from the STM-N signals and disassemble the STM-N signals at the receiver.
- #30: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle If the receiver doesn't receive A1 and A2 bytes within five or more successive frames (625us), i.e. it can't identify the start of five successive frames (identify different frames), it will enter out-of-frame status and generate out-of-frame alarm ---- OOF. If the OOF keeps for 3ms, the receiver will enter loss-of-frame status ---- the equipment will generate loss-of-frame alarm ---- LOF. Meanwhile, an AIS signal will be sent downward and the entire services will be interrupted. Under LOF status, if the receiver stays in normal frame alignment status again for successive 1ms or more, the equipment will restore the normal status.
- #31: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle One of the features of SDH is its highly automatic OAM function which can conduct commands issue and performance auto poll to the networks element via NMT Network Management Terminals. SDH has some functions which are not possessed by PDH systems, such as real-time service allocation, alarm fault location and on-line performance testing. Where are these OAM data arranged to transmit? The data used for OAM functions, such as sent commands and checked alarm performance data, are transmitted via D1-D12 bytes within the STM-N frame. Thus the D1-D12 bytes provide a common data communication channel accessible to all SDH network elements. As the physical layer of the embedded control channel (ECC), the D1-D12 bytes transmit OAM information among the network elements and form a transmission channel of the SDH management network (SMN). The DCC has a total rate of 768kb/s that provides a powerful communication base for SDH network management. D1, D2 and D3 are regenerator section DCC bytes (DCCR) with a rate of 3×64kb/s=192kb/s and are used to transmit OAM information among regenerator section terminals. D4-D12 are multiplex section DCC bytes (DCCM) with a sum rate of 9×64kb/s=576kb/s and are used to transmit OAM information among multiplex section terminals.
- #32: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle E1 is part of the RSOH and may be accessed at regenerators. E2 is part of the MSOH and man be accessed at multiplex section terminations. Each of these two bytes provides a 64kb/s orderwire channel for voice communication, i.e. voice information is transmitted via these two bytes. The orderwire provides a convenient communication function during maintenance and troubleshooting.
- #33: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle This B1 byte is allocated for regenerator section error monitoring (Byte B1 is located in the regenerator section overhead). What is the mechanism for monitoring? First, we'll discuss the BIP-8 parity. Suppose that a signal frame is composed of 4 bytes: A1=00110011, A2=11001100, A3=10101010 and A4=00001111. The method of providing BIP-8 parity to this frame is to divide it into 4 block with 8 bits (one byte) in a parity unit (each byte as a block because one byte has 8 bits, the same as a parity unit) and to arrange these blocks. Compute the number of "1" over each column. Then fill a 1 in the corresponding bit of the result (B) if the number is odd, otherwise fill a 0. That is, the value of the corresponding bit of B makes the number of "1" in the corresponding column of A1A2A3A4 blocks even. This parity method is called BIP-8 parity. In fact this is an even parity since it guarantees that the number of "1" is even. B is the result of BIP-8 parity for the A1A2A3A4 block. The mechanism for B1 byte is: the transmitting equipment processes BIP-8 even parity over all bytes of the previous frame (1#STM-N) after scrambling and places the result in byte B1 of the current frame (2#STM-N) before scrambling. The receiver processes BIP-8 parity over all bits of the current frame (1#STM-N) before de-scrambling and compares the parity result and the value of B1 in the next frame (2#STM-N) after de-scrambling. The different bit means the error block. According to the number of different bits, we can monitor the number of error blocks occurred in 1#STM-N frame during transmission. If the B1 of the receive end has detected error blocks, the number of error blocks detected by the B1 will be displayed in receive end performance event RS-BBE (Regenerator Section Background Block Error). When the error bits detected by the receive end exceed a given threshold, the equipment will report corresponding alarms. When the error bit ratio (EBR) is greater than 10E-6, the given alarm is B1-SD. When the error bit ratio (EBR) is greater than 10E-3, B1-EXC (another name B1-OVER) will be given.
- #34: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle B2 is similar to B1 in operation mechanism except that it monitors the error status of the multiplex section layer. The B1 byte monitors the transmission error of the complete STM-N frame signal. There is only one B1 byte in an STM-N frame. There are N*3 B2 bytes in an STM-N frame with every three B2 bytes corresponding to an STM-1 frame. The B2 monitoring adopts BIP-24 (three bytes) method, which can at most monitor 24 error blocks one time. Since error performance of higher rate signals is reflected via error blocks, the error status of STM-N signals is actually the status of error blocks. As can be seen from the BIP-24 parity method, each bit of the parity result is corresponding to a bit block. So three B3 bytes can at most monitor 24 error blocks from an STM-N frame that occur during transmission (The result of BIP-24 is 24 bits with each bit corresponding to a column of bits ---- a block). If the B2 of the receive end has detected error blocks, the number of error blocks detected by the B2 will be displayed in this end performance event MS-BBE (Multiplex Section Background Block Error). At the same time, M1 will be used to report to the transmit end that error blocks have been detected, and the transmit end will report MS-FEBBE (Multiplex Section Far End Background Block Error) performance event and MS-REI (Multiplex Section Remote Error Indication) alarm. When the error bits detected by the receive end exceed a given threshold, the equipment will report corresponding alarms. When the error bit ratio (EBR) is greater than 10E-6, the given alarm is B2-SD. When the error bit ratio (EBR) is greater than 10E-3, B2-EXC will be given.
- #35: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle If the B2 of the receive end has detected error blocks, the number of error blocks detected by the B2 will be displayed in this end performance event MS-BBE (Multiplex Section Background Block Error). At the same time, M1 will be used to report to the transmit end that error blocks have been detected, and the transmit end will report MS-FEBBE (Multiplex Section Far End Background Block Error) performance event and MS-REI (Multiplex Section Remote Error Indication) alarm. This is a message returned to its transmit end by the receive end so that the transmit end can get the receiving error status of the receive end. For STM-N levels this byte conveys the count (in the range of [0, 255]) of interleaved bit blocks that have been detected in error by the BIP-24N (B2). For rates of STM‑16 and above, this value shall be truncated to 255.
- #36: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle Two bytes are allocated for APS signaling for the protection of the multiplex section. For the bit assignments for these bytes and the bit-oriented protocol, please refer to G.783, G.841 (10/98).
- #37: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle This is an alarm message, returned to the transmit end (source) by the receive end (sink), which means that the receive end has detected an incoming section defect or is receiving the Multiplex Section Alarm Indication Signal (MS-AIS). That is, when the receive end detects receiving deterioration, it returns an Multiplex Section Remote defect Indication (MS-RDI) alarm signal to the transmit end so that the later obtains the status of the former. If the received b6-b8 bits of the K2 is 110, it means that this signal is an MS-RDI alarm signal returned by the opposite end. If the received b6-b8 bits of the K2 is 111, it means that this signal is an MS-AIS alarm signal received by current end. Meanwhile, the current end is required to send out MS-RDI signal to the opposite end, i.e. insert 110 bit pattern into the b6-b8 of the K2 within the STM-N signal frame to be sent to the opposite end. Not all deterioration results in returning MS-RDI. Current end equipment returns MS-RDI only upon receiving R-LOS, R-LOF, and MS-AIS alarm signals.
- #38: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle We can use the extended SSM for clock protection. In this case, the different value of bits 1 ~ 4 of byte S1 indicates the different clock source. Bits 5 to 8 of byte S1 are allocated for Synchronization Status Messages. Table 3-1 gives the assignment of bit patterns to the four synchronization levels agreed to within ITU-T. Two additional bit patterns are assigned: one to indicate that quality of the synchronization is unknown and the other to signal that the section should not be used for synchronization. The remaining codes are reserved for quality levels defined by individual Administrations. Different bit patterns, indicating different quality levels of clocks defined by ITU-T, enable the equipment to determine the quality of the received clock timing signal. This helps to determine whether or not to switch the clock source, i.e. switch to higher quality clock source. The smaller the value of S1 (b5-b8), the higher the level of clock quality.
- #39: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle The Section Overhead is responsible for section layer OAM functions while the Path Overhead for path layer OAM functions. Like transporting the cargoes loaded in the container: not only the overall impairment status of the cargoes (SOH) but also the impairment status of each cargo (POH) shall be monitored. According to the "width" of the monitored path (the size of the monitored cargo) , the Path Overhead is further classified into Higher Order Path Overhead and Lower Order Path Overhead. In this curriculum the Higher Order Path Overhead refers to the monitoring of VC-4 level paths within the STM-N frame. The Lower Order Path Overhead implements the OAM functions for VC-12 path level, i.e. monitoring the transmission performance of 2Mb/s signals within the STM-N frame. The Higher Order Path Overhead, consisting of 9 bytes, is located in the first column of the VC-4 frame.
- #40: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle The AU-PTR pointer indicates the specific location of the start of the VC-4 within the AU-4, i.e. the location of the first byte of the VC-4, so that the receive end can properly extract VC-4 from the AU-4 according to the value of this AU-PTR. The J1 is the start of the VC-4, so the AU-PTR indicates the location of the J1 byte. The J1 byte is used to transmit repetitively a Higher Order Path Access Point Identifier so that a path receiving terminal can verify its continued connection to the intended transmitter (this path is under continued connection). This requires that the J1 bytes of the received and transmit ends match. The default transmit/receive J1 byte values of the equipments provided by Huawei Company are “HuaWei SBS”. Of course the J1 byte can be configured and modified according to the requirement. The received J1 should match or be same with the expected J1. If not, HP-TIM alarm will be generated, which perhaps interrupts the service within the VC4 sometimes.
- #41: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle The B3 byte is allocated for monitoring the transmission error performance of VC-4. Its monitoring mechanism is similar to that of the B1 and B2 except that it is used to process BIP-8 parity for the VC-4 frame. Once the receive end detects error blocks, the number of error blocks will be displayed in the performance monitoring event ---- HP-BBE (Higher Order Path Background Block Error) of the received end. At the same time, G1 (b1-b4) will be used to report to the transmit end that error blocks have been detected, and the transmit end will report HP-FEBBE (Higher-order Path Far End Background Block Error) performance event and HP-REI (Higher-order Path Remote Error Indication) alarm. When the error bits detected by the receive end exceed a given threshold, the equipment will report corresponding alarms. When the error bit ratio (EBR) is greater than 10E-6, the given alarm is B3-SD. When the error bit ratio (EBR) is greater than 10E-3, B3-EXC will be given.
- #42: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle The C2 is allocated to indicate the composition of multiplexing structure and information payload of the VC frame, such as equipped or unequipped status of the path, the type of loaded services and their mapping method. For example, C2=00H indicates that this VC-4 path is unequipped. Then the payload TUG-3 of the VC-4 is required to be inserted all "1" ---- TU-AIS and the higher order path unequipped alarm ---- HP-UNEQ appears in the equipment. C2=02H indicates that the payload of the VC-4 is multiplexed via a TUG structure multiplexing route. In China, the multiplexing of 2Mb/s signals into VC-4 adopts the TUG structure. To configure the multiplexing of 2Mb/s signals for Huawei equipments, the C2 is required to be configured as TUG structure. The received C2 should match or be same with the expected C2. If not, HP-SLM alarm will be generated, which interrupts the service within the VC4 sometimes.
- #43: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle The LPOH here refers to the path overhead of the VC-12 that monitors the transmission performance of the VC-12 path level, i.e. monitors the transmission status of 2Mb/s PDH signals within the STM-N frame. Where is the LPOH located within the VC-12? The lower order POH is located in the first byte of each VC-12 basic frame. An LP-POH consists of four bytes denoted V5, J2, N2 and K4. Usually, V5 byte is the most important in LPOH. The V5 provides the functions of error checking, signal label and path status of the VC-12 paths. So this byte has the functions of the G1, B3 and C2 bytes within the higher order path overhead. If the V5 (b1b2) of the receive end have detected error blocks, the number of error blocks detected by the V5 (b1b2) will be displayed in this end performance event LP-BBE (Lower-order Path Background Block Error). At the same time, V5 (b3) will be used to report to the transmit end that error blocks have been detected, and the transmit end will report LP-FEBBE (Lower-order Path Far End Background Block Error) performance event and LP-REI (Lower-order Path Remote Error Indication) alarm. When the error bits detected by the receive end exceed a given threshold, the equipment will report corresponding alarms. When the error bit ratio (EBR) is greater than 10E-6, the given alarm is BIP-SD. When the error bit ratio (EBR) is greater than 10E-3, BIP-EXC will be given. Bit 8 of the V5 is allocated for the VC-12 Path Remote Defect Indication. An LP-RDI (Lower Order Path Remote Defect Indication) is sent back to the source if either a TU-12 AIS signal or signal failure condition is being detected by the sink. Notes: In this curriculum, RDI is called remote deterioration indication or remote defect indication.
- #44: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle The function of the pointers is aligning via which the receiver can properly extract the corresponding VC from the STM-N and then disassemble the VC and C packages and extracts the lower rate PDH signals, i.e. directly drop lower rate tributary signals from the STM-N signal. What is aligning? Aligning is a procedure by which the frame offset information is incorporated into the Tributary Unit or the Administrative Unit, i.e. via the Tributary Unit Pointer (or Administrative Unit Pointer) attached to the VC to indicate and determine the start of the lower order VC frame within the TU payload ( or the start of the higher order VC frame within the AU payload). When relative differences occur in the phases of the frames and make the VC frames "float", the pointer value will be justified to ensure that it constantly and properly designates the start of the VC frame. For a VC-4, its AU-PTR indicates the location of the J1 byte while for a VC-12; its TU-PTR indicates the location of the V5 byte. The TU pointer or AU pointer provides a method of allowing flexible and dynamic alignment of the VC within the TU or AU frame because these two pointers are able to accommodate differences, not only in the phases of the VC and the SDH, but also in the frame rates.
- #45: Page-<number> Confidential Information of Huawei. No Spreading Without Permission SDH Principle The AU-PTR, located in row 4 of columns 1 to 9 within the STM-1 frame, is used to indicate the specific location of the fist byte J1 of the VC-4 within the AU-4 payload so that the receiver can properly extract the VC-4. The AU-4 pointer provides a method of allowing flexible and dynamic alignment of the VC‑4 within the AU-4 frame. Dynamic alignment means that the VC-4 is allowed to "float" within the AU-4 frame. Thus, the pointer is able to accommodate differences, not only in the phases of the VC-4 and the SOH, but also in the frame rates. The pointer contained in H1 and H2 designates the location of the byte where the VC‑4 begins. The last ten bits (bits 7‑16) of the pointer word carry the pointer value.
- #46: The TU pointer is used to indicate the specific location of the first byte V5 of the VC-12 within the TU-12 payload so that the receiver can properly extract the VC-12. The TU pointer provides a method of allowing flexible and dynamic alignment of the VC-12 within the TU-12 multi-frame. The TU-PTR is located in the bytes denoted V1, V2, V3 and V4 within the TU-12 multi-frame. The TU pointer of TU3 consists of H1, H2 and H3. Their function is similar to that of AU-PTR.
- #47: K2 byte is used to monitor the status of MS, which might generate MS-AIS or MS-RDI alarm. If the receiver doesn't receive A1 and A2 bytes within five or more successive frames (625us), i.e. it can't identify the start of five successive frames (identify different frames), it will enter out-of-frame status and generate out-of-frame alarm ---- OOF. If the OOF keeps for 3ms, the receiver will enter loss-of-frame status ---- the equipment will generate loss-of-frame alarm ---- LOF. Meanwhile, an AIS signal will be sent downward and the entire services will be interrupted. Under LOF status, if the receiver stays in normal frame alignment status again for successive 1ms or more, the equipment will restore the normal status. The BIP-8 parity.
- #48: The focus is the mechanism for the bytes to monitor alarms and performances.