Secure erasure code based distributed storage system with secure data forwarding
- 1. Secure Erasure Code-Based Distributed Storage System with Secure Data Forwarding
- 2. Introduction Constructing a secure storage system that supports multiple functions is challenging when it is distributed and has no central authority The proposed system consist of threshold proxy re- encryption scheme, integrated with a decentralized erasure code The main focus is on designing a storage system for robustness, confidentiality, and functionality
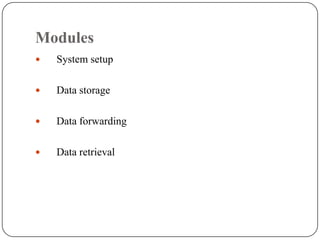
- 4. Modules System setup Data storage Data forwarding Data retrieval
- 5. 1. System setup create set of users, n storage servers SS1, SS2, . . ., SSn, and m key servers KS1, KS2, . . . , KSm. Each user A is assigned a public-secret key pair (PKA, SKA).
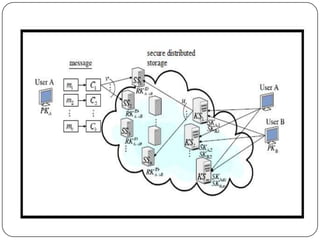
- 6. 2.Data Storage: In the data storage phase, user A encrypts his message M and dispatches it to storage servers. A message M is decomposed into k blocks m1, m2.. User A encrypts each block mi into a ciphertext Ci and sends it to v randomly chosen storage servers Each storage server linearly combines them with randomly chosen coefficients into a codeword symbol and stores it.
- 7. 3.Data Forwarding: User A forwards his encrypted message with an identifier ID stored in storage servers to user B such that B can decrypt the forwarded message by his secret key. compute a re-encryption key RK AB Each storage server uses the re-encryption key to re-encrypt its codeword symbol for later requests by B . The re-encrypted codeword symbol is the combination of cipher texts under B’s public key.
- 8. 4.Data Retrieval: user A requests to retrieve a message from storage servers User A sends a retrieval request to key servers user A combines the partially decrypted codeword symbols to obtain the original message M.
- 9. Work Done Setting servers and users Each user has assigned with a key pair Selecting a file Splitting file into blocks Encrypting each block Sending cipher text to storage server
- 10. Work To Be Done Encoding each block and storing. Data Forwarding Generating re-encryption key Re-encrypting codeword Data Retrieval Decrypting each block Combing all blocks
- 11. THANK YOU