Secure the modern Enterprise
- 2. “Security is like oxygen. When you have it, you don't notice it. But when it’s gone, you don’t survive long.” Jessi Hempel Former Senior Writer, WIRED WIRED, “DOD Head Ashton Carter Enlists Silicon Valley to Transform the Military,” November 18, 2015
- 3. “Cybersecurity is like going to the gym. You can’t get better by watching others, you’ve got to get there every day.” Satya Nadella CEO, Microsoft @satyanadella #FIF2017
- 4. “People will only use technology they trust.” Brad Smith President & Chief Legal Officer Microsoft Corporation
- 7. 200 DAYS between infiltration and detection
- 8. HOW DO BREACHES OCCUR? Malware and vulnerabilities are not the only thing to worry about 99.9% of exploited Vulnerabilities were used more than a year after the CVE was published 46% of compromised systems had no malware on them 50% of those who open and click attachments do so within the first hour 23% of recipients opened phishing messages (11% clicked on attachments) Fast and effective phishing attacks leave you little time to react
- 9. 74% of the world’s businesses expect to be hacked in the coming year
- 12. Microsoft is meeting customer security needs with the industry's largest compliance portfolio ISO 27001 PCI DSS Level 1 * SOC 2 Type 2 ISO 27018 Cloud Controls Matrix Content Delivery and Security Association * Shared Assessments SOC 1 Type 2 Worldwide INDUSTRY’S LARGEST COMPLIANCE PORTFOLIO Government FIPS 140-2 DISA Level 2FERPAFedRAMP JAB P-ATO FISMACJIS21 CFR Part 11 IRS 1075Section 508 VPAT United Kingdom G-Cloud NIST 800- 171 National European Union Model Clauses Singapore MTCS Level 3 New Zealand GCIO Australian Signals Directorate Japan Financial Services Spain ENS ENISA IAF HIPAA / HITECH EU-U.S. Privacy Shield China MLPS*, TRUCS*, GB 18030* https://www.microsoft.com/en-us/trustcenter/compliance/complianceofferings
- 13. ASSUME BREACH! !
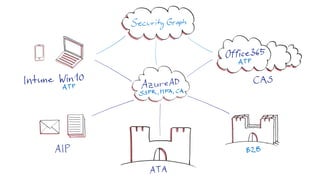
- 16. Apps and Data SaaS Analysis & Action Digital Crimes Unit Hunting Teams Security Response Center Malware Protection Center Device Antivirus Network Infrastructure Cyber Defense Operations Center CERTs and other partners PaaS IaaS Identity
- 17. The Microsoft Cyber Defense Operations Center • Protect Microsoft’s cloud infrastructure, customer- facing cloud services, products and devices, and internal resources 24 x 7 x 365 • Unite personnel, technology, and analytics in a central hub • Provide world-class security protection, detection, and response • More than 50 Security Experts and Data Scientists • Connected to >3500 Security Professionals across Microsoft • Tight partnerships with Microsoft Research and the Security Development Lifecycle (SDL) team
- 19. MICROSOFT CONFIDENTIAL Access to a Transparency Center to work directly with source code for certain high-volume products Remote access to online source code for certain high-volume products Technical data about products and services, including about Microsoft’s cloud services Information sharing about threats and vulnerabilities from Microsoft
- 20. Microsoft Confidential A safer digital experience for every person and organization on the planet The Microsoft Digital Crimes Unit Public and private partnerships to fight technology facilitated crimes . Combining novel legal strategies, cutting- edge forensics, cloud and big data analytics
- 21. SECURE MODERN ENTERPRISE Identity Apps and Data Infrastructure Devices Identity Embraces identity as primary security perimeter and protects identity systems, admins, and credentials as top priorities Apps and Data Aligns security investments with business priorities including identifying and securing communications, data, and applications Infrastructure Operates on modern platform and uses cloud intelligence to detect and remediate both vulnerabilities and attacks Devices Accesses assets from trusted devices with hardware security assurances, great user experience, and advanced threat detectionSecure Platform (secure by design)
- 22. Secure Platform (secure by design) SECURE MODERN ENTERPRISE Identity Apps and Data Infrastructure Devices Phase 2: Secure the Pillars Phase 1: Build the Security Foundation Start the journey by getting in front of current attacks • Critical Mitigations – Critical attack protections • Attack Detection – Hunt for hidden persistent adversaries and implement critical attack detection • Roadmap and planning – Share Microsoft insight on current attacks and strategies, build a tailored roadmap to defend your organization’s business value and mission Phase 1: Build Security Foundation – Critical Attack Defenses Phase 2: Secure the Pillars Continue building a secure modern enterprise by adopting leading edge technology and approaches: • Threat Detection – Integrate leading edge intelligence and Managed detection and response (MDR) capabilities • Privileged Access – continue reducing risk to business critical identities and assets • Cloud Security Risk – Chart a secure path into a cloud- enabled enterprise • SaaS / Shadow IT Risk – Discover, protect, and monitor your critical data in the cloud • Device & Datacenter Security – Hardware protections for Devices, Credentials, Servers, and Applications • App/Dev Security – Secure your development practices and digital transformation components
- 23. Enterprise identity, security and cybersecurity • Dynamic Identity Framework Assessment (DIF) • Azure Active Directory Implementation Services • Azure Active Directory B2C Architecture Services • Microsoft Identity Management Foundation • Design and Implementation for Active Directory (DIAD) • Enterprise Federated Identity using AD Federation Services (EFI) • Public Key Infrastructure using AD Certificate Services (PKI) • Enterprise Modernization – Active Directory Upgrade • Active Directory Migration Service (ADMS) • Offline Assessment for Active Directory Security (OAADS) • Privileged Access Workstation (PAW) • Persistent Adversary Detection Services (PADS) • ATA Implementation Services (ATA-IS) • Enterprise Threat Detection (ETD) • Enhanced Secure Administrative Environment (ESAE) • Securing Lateral Account Movement (POP-SLAM) • Incident Response and Tactical Recovery (I/R & T/R) • Microsoft Security Risk Assessment • Windows 10 Enterprise Security Integration Briefing • Windows 10 security implementation services • Information Protection using Azure Rights Management Service • Shielded Virtual Machines (VM) Proof of Concept (PoC) • Security Development Lifecycle Maturity Assessment Enterprise services and cybersecurity offersMicrosoft products and capabilities • Azure AD Identity Protection • Advanced Threat Analytics • Enterprise Mobility + Security • Advanced Threat Protection • Azure AD B2C • Microsoft Identity Manager • Azure Information Protection • Windows Information Protection • Enterprise Mobility + Security • Customer Lockbox • Cloud App Security • Azure SQL Security • Windows 10 • Device Guard • Credential Guard • Windows Defender • Windows Defender ATP • Windows Server 2016 • Azure Security Center • OMS Security Suite • Shielded VMs Contact: cyberservices@microsoft.com
- 24. PLAN ENTER TRAVERSE EXECUTE MISSION 4 Threat Actors exfiltrate PII and other sensitive business data Threat Actor targets employee(s) via phishing campaign1 Workstation compromised, threat actor gathers credentials2a Threat Actors use stolen credentials to move laterally 3a Employee B opens infected email (Mobile or PC). Attacker disables antivirus 2b Compromised credentials/ device used to access cloud service / enterprise environment 3bc Credentials harvested when employee logs into fake website 2c A. Enter and Navigate Any employee opens attack email Access to most/all corporate data B. Device Compromise Targeted employee opens attack email Access to same data as employee C. Remote Credential Harvesting Targeted employee(s) enter credentials in website Access to same data as employee(s) Common Attacks Office 365 Technology • Advanced Threat Protection (requires E5) EMS Technology • Cloud App Security (CASB) (requires E5) Office 365 Technology • Advanced Security Management (basic CASB) (requires E5) Azure Technology • Multi-Factor Authentication • Azure Identity Protection Microsoft Incident Response Teams can be engaged to investigate any incident type as well as to assess your organization for existing compromises Windows 10 Technology • SmartScreen URL and App reputation • Application Guard EMS Technology • Azure Information Protection (requires E5) Office 365 Technology • Data Loss Prevention Windows 10 Technology • Windows Information Protection Azure Technology • Disk, Storage, SQL Encryption • Key Vault • … Any Windows 10 Technology • Device Guard • Credential Guard • Defender Advanced Threat Protection (requires E5) Managed Detection and Response (MDR) • Enterprise Threat Detection Published Guidance • Securing Privileged Access Roadmap Professional Services • Security Foundation • Enhanced Security Admin Environment (ESAE) Technology • Advanced Threat Analytics (in EMS E3) • Azure Security Center & Operations Management Suite (OMS) • …and more EMS Technology • Intune conditional access Managed Detection and Response (MDR) • Enterprise Threat Detection (PCs only)
- 37. Why do you want to protect information? Reduce leakage of data shared with others Partitioning of sensitive data from unauthorized users Prevent employees from leaking secrets Meet compliance requirements (GDPR, …) 96% 94% 89% 87%
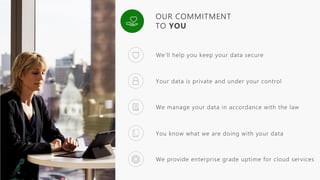
- 39. Protect devices with industry-leading encryption, anti-malware technologies, and identity and access solutions
- 40. Safeguard customer data in the cloud, including personal data, with industry-leading security measures and privacy policies
- 41. Secure your IT environment and achieve compliance with enterprise-grade user and administrative controls
- 42. Protect customer data both in the cloud, and on-premises, with industry-leading security capabilities
- 43. Safeguard customer data in the cloud, including personal data, with industry-leading security measures and privacy policies