Secure Your WordPress Site - And Your Business
- 1. Secure Your WordPress Site – AND Your Business Stacy M. Clements WordCamp Minneapolis 2019 https://www.linkedin.com/in/stacyclements @StacyClements
- 5. Secure Your WordPress Site – And Your Business Why you should care Ways you’re vulnerable Cybersecurity Framework Three cybersecurity fundamentals
- 6. • Small business owner • Air Force veteran • Technology & security enthusiast Stacy M. Clements Fixer • Problem Solver • Pitbull
- 7. Why should you care?
- 8. • Computing power • Server resources • Personal information • Connections / access What Do You Have?
- 9. • Phishing • Ransomware • Cryptojacking • Denial of service • Insider attack What Can Happen To It?
- 10. • Technical problems and changes • Security misconfiguration • Uneducated or inattentive users How Can They Get It?
- 13. Risk
- 14. Why isn’t a plugin enough?
- 16. Application • WordPress core • Themes/plugins • cPanel Network • Server • Computer/mobile device • Router • “Tubes” Human • Site administrators • Contributors/users ATTACK SURFACE
- 19. NIST Cybersecurity Framework • Collaborative effort • Built using “best practice” guidelines for organizations to better manage and reduce cybersecurity risk • Designed to be flexible
- 20. Framework Core Elements Functions organize basic cybersecurity activities at the highest level
- 21. Framework Core Elements Categories break down Functions into groups of cybersecurity outcomes
- 22. Framework Core Elements Subcategories get more specific – describing specific outcomes of technical and/or management activities
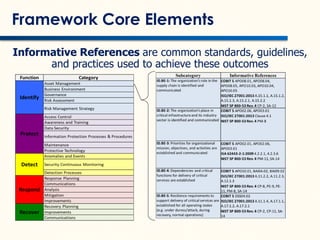
- 23. Framework Core Elements Informative References are common standards, guidelines, and practices used to achieve these outcomes
- 24. Once Upon A Time…
- 25. BOB
- 26. Source: Sucuri Website Hack Trend Report 2018
- 28. IDENTIFY Asset Management Identify WordPress site Cloud storage Plugins Database Users Files Payments Server • What are your assets? • Who can access – and how? SALLY
- 29. Identify IDENTIFY Asset Management Risk Assessment • What are the threats and vulnerabilities? • How do you get your “cyber threat intelligence”?
- 30. PROTECT Access Control Protect • Enforce strong passwords and use 2FA • Change default credentials!
- 31. Protect PROTECT Access Control Information Protection Procedures Protect • Secure – Update – Backup – TEST! • Develop and exercise response and recovery plans
- 32. PROTECT Access Control Information Protection Procedures Protective Technology Protect • Plugin is protective technology – if configured • Logs / removable media / no “kitchen sink” servers
- 33. Detect DETECT Security Continuous Monitoring • Awareness – have a baseline and know when something looks suspicious
- 34. Detect • Who is getting and assessing alerts? • Who is taking action? DETECT Security Continuous Monitoring Detection Processes
- 35. Respond RESPOND Execute Response Plan • What immediate actions do you need to take? • Make required notifications
- 36. Respond RESPOND Execute Response Plan Analysis & Mitigation
- 37. • Restore from the backup you created and tested (You did do that, right?) • Communicate with your customers Recover RECOVER Execute Recovery Plan
- 38. Recover • Recovery is not just returning to the pre-incident state • Hotwash / Lessons Learned? RECOVER Execute Recovery Plan Improvements
- 40. Secure Access • Password management • Multi-factor authentication Update • Inventory • Regular update schedule • Periodic review Backup • Backup • Backup • Backup • TEST!
- 41. Takeaways Security is managing risk Protect your entire “attack surface” Cybersecurity Framework 3 fundamentals to do now S-U-B set – Secure Access, Update, Backup (and test)
- 42. Secure Your WordPress Site – AND Your Business Stacy M. Clements WordCamp Minneapolis 2019 https://www.linkedin.com/in/stacyclements @StacyClements