Securing Mobile Apps, From the Inside Out
- 1. The global reference in mobile application protection Securing Mobile Apps, From the Inside Out Eric Lafortune, CTO, Guardsquare
- 2. Securing Mobile Apps, from the Inside Out Impossible? Useful?
- 3. Guardsquare Leuven – Boston – San Francisco
- 4. Guardsquare ProGuard – optimization of Java bytecode DexGuard – optimization and protection for Android iXGuard – protection for iOS
- 7. OS Attack scenarios Mobile device Service App store API attack
- 8. OS Attack scenarios Mobile device Service App store MITM attack
- 10. OS Attack scenarios Computer Mobile device Service App store Dynamic analysis Tampering
- 11. OS Attack scenarios Computer Mobile device Service App store Static analysis
- 12. OS Attack scenarios Computer Mobile device Service App store MITM attack Static analysis & tampering
- 13. OS Attack scenarios Computer Mobile device Service App store Cloning Static analysis & tampering
- 15. OS The app as a gateway for many attacks Computer Mobile device Service App store
- 16. What to protect? Mobile threats App Authentication Key loggers Advertisements Malware Keys Intellectual property Protocols Advertisements In-app purchases License checks
- 17. High level threats Mobile applications Piracy API key extraction Cloning & IP theft Financial fraud Malware insertion Credential harvesting
- 18. Consequences Fines and retributions Incident handling cost Revenue loss Reputational damage Mobile applications
- 20. Layers of protection Hardened app Secure implementation Secure architecture V8: Resilience V7: Code quality V1-V6: Architecture, storage, crypto, authentication, networking, platform integrity OWASP Mobile Application Security Verification Standard
- 21. Layers of protection Harden apps against tampering Techniques: • Certificate checking • Re-packaging detection • File integrity Application integrity Platform integrity Application code protection
- 22. Layers of protection Detect apps running in a compromised environment Techniques: • Root detection • Root hiding detection • Hook detection • Debug detection • Emulator detection Application integrity Platform integrity Application code protection • SSL pinning
- 23. Layers of protection Prevent reverse engineering and tampering Techniques: • Name obfuscation • Removal of logging and meta data • Optimization techniques Platform integrity Application protection Application integrity • Call hiding • Control flow obfuscation • Code virtualization • Arithmetic obfuscation • String encryption • Class encryption • Native code obfuscation • Javascript obfuscation • Code packing
- 25. Processing applications DexGuard processing steps 1. Shrinking 2. Optimization 3. Obfuscation
- 26. 1. Shrinking Also called treeshaking, minimizing, shrouding DexGuard processing steps 1. Shrinking 2. Optimization 3. Obfuscation
- 27. 1. Shrinking • Classes, fields, methods • Native libraries • Resources • Resource files • Asset files DexGuard processing steps 1. Shrinking 2. Optimization 3. Obfuscation
- 28. 2. Optimization Resources and bytecode instructions: • Resource inlining • Metadata inlining • Constant propagation • Dead code elimination • Method inlining • Devirtualization • etc. Also: • Remove logging code DexGuard processing steps 1. Shrinking 2. Optimization 3. Obfuscation
- 29. 3. Obfuscation and detection ● Rename identifiers: names of classes, fields, methods, resources, resource files, asset files, native libraries ● Remove debug information: line numbers, local variable names, etc. ● String encryption ● Asset encryption ● Control flow obfuscation ● Code virtualization ● Arithmetic obfuscation ● Root detection ● etc. DexGuard processing steps 1. Shrinking 2. Optimization 3. Obfuscation
- 30. Name obfuscation Obfuscation techniques public class a { private b a; private c b; private int c; public int a(int a) { … return c; } } public class MyComputationClass { private MySettings settings; private MyAlgorithm algorithm; private int answer; public int computeAnswer(int input) { … return answer; } } BEFORE AFTER
- 31. String encryption Obfuscation techniques String KEY = decrypt(“U2VjcmV0IGtleQo”);String KEY = “Secret key”; BEFORE AFTER
- 32. Reflection Obfuscation techniques Class clazz = Class.forName(“java.io.PrintStream”); Method method = clazz.getMethod(“println”, new Class[] { String.class }); method.invoke(null, new Object[]{ “Hello world!” }); System.out.println(“Hello world!”); BEFORE AFTER
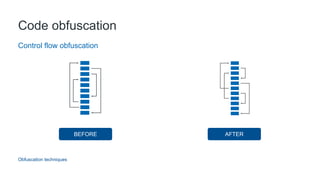
- 33. Code obfuscation Obfuscation techniques Control flow obfuscation BEFORE AFTER
- 34. Code obfuscation Obfuscation techniques Opaque predicates boolean flag = System.currentTimeMillis() > 0; boolean flag = true; BEFORE AFTER
- 35. Code obfuscation Obfuscation techniques Arithmetic obfuscation int c = (a ^ b) + 2 * (a & b);int c = a + b; BEFORE AFTER
- 39. Obfuscation techniques BEFORE AFTER Code encryption
- 40. Alternative bytecode BEFORE AFTER Alternative VM Dalvik bytecode Code virtualization Obfuscation techniques
- 41. Securing Mobile Apps, from the Inside Out Practically possible Very useful Matter of economics
- 42. The global reference in mobile application protection Thank you! Any questions? To learn more, go to guardsquare.com































![Reflection
Obfuscation techniques
Class clazz =
Class.forName(“java.io.PrintStream”);
Method method =
clazz.getMethod(“println”,
new Class[] { String.class });
method.invoke(null, new Object[]{
“Hello world!”
});
System.out.println(“Hello world!”);
BEFORE AFTER](https://image.slidesharecdn.com/finalslides-191210200141/85/Securing-Mobile-Apps-From-the-Inside-Out-32-320.jpg)