Subdomain Takeover
- 2. What is Subdomain? • A subdomain is a variation or forwarder address derived from your root domain name, such as help.yourdomainname.com. • Your IT department, web master or you usually set subdomains for use with 3rd party services such as helpdesk applications, calendar or mail apps, and sometimes used to host a micro website.
- 3. What is DNS? • The Domain Name System (DNS) translates Internet domain and host names to IP addresses and vice versa. • On the Internet, DNS automatically converts between the names we type in our Web browser address bar to the IP addresses of Web servers hosting those sites. Larger corporations also use DNS to manage their own company intranet. Home networks use DNS when accessing the Internet but do not use it for managing the names of home computers.
- 4. What is DNS Records? • The data that tells the web server how to respond to your input is known as the DNS records, or zone files. • These records play a vital role in the functionality of the internet, and any aspiring internet technology expert should learn the facts about DNS records and how they are used. • DNS records are basically mapping files that tell the DNS server which IP address each domain is associated with, and how to handle requests sent to each domain.
- 5. What is DNS Records? • When someone visits a web site, a request is sent to the DNS server and then forwarded to the web server provided by a web hosting company, which contain the data contained on the site. • Various strings of letters are used as commands that dictate the actions of the DNS server, and these strings of commands are called DNS syntax. • Some DNS records syntax that are commonly used in nearly all DNS record configurations are A, AAAA, CNAME.
- 6. What Is ‘A’ Configuration? • A record (Address Record) points a domain or subdomain to an IP address. • For example, you can use it for store.website.com or blog.website.com and point it to where you have your store. • This is a common practice for people who use Amazon, eBay, Tumblr, etc.
- 7. What is ‘AAAA’ Configuration? • The AAAA record is similar to the A record, but it allows you to point the domain to an IPv6 address • Zone File: This is where all the DNS records are stored for a domain. • Host Record: This is the domain or subdomain you wish to use. The @ symbol is used to indicate the root domain itself. In our example the Host Record 'ftp' would be for the subdomain ftp.google.com and '@' would be google.com itself
- 8. What is CNAME? • The “CNAME” record stands for “canonical name” and serves to make one domain an alias of another domain. CNAME is often used to associate new subdomains with an existing domain's DNS records.
- 9. That’s enough of basics! Let’s look into the Vulnerability!!
- 10. Ever seen one of these?
- 11. The Attack Scenario • Many websites do not just work with company.com technique or just www.company.com. For emails, blog, internal domains these companies tend to use subdomains. • Subdomains map itself to a specific IP, 3rd party services, etc. to serve the contents. • There are some very popular cloud e-commerce providers (e.g. Shopify, BigCommerce, Magento, Yokart, Big Kartel), so company setups a new store in one of these available offerings. • After the setup and configuration, the cloud e-commerce provider assigns exampleshop.someecommerceplatform.com as a domain for the company. • But, this doesn't look very compelling to share and communicate to the customers, so company want it to be present on their brand, under shop.company.com
- 12. The Attack Scenario • In order to achieve this, company have two configuration options: 1. A 301/302 redirect HTTP will take care of redirecting visitors of shop.company.com to the domain of the e-commerce provider. This approach is less appealing because it will completely replace the domain in the URL bar of the user's browser. 2. Configuration of a CNAME DNS record that will delegate the DNS resolution directly to e-commerce provider. Using this approach, the domain in the URL bar keeps unchanged. (Note: not all cloud providers support DNS delegation using CNAME) • Since the CNAME approach is more robust, company proceeds with option 2.
- 13. The Attack Scenario • Now, due to whatever reason the company decided to stop utilizing this service. To save money, company cancels the subscription of the 3rd party e-commerce platform supplier. • But, company can easily forget to update or simply remove the CNAME record in the DNS zone file. • Hackers find out that your subdomain is offline but still offers active redirects to the 3rd party e-commerce platform - signs up for the same service and claims the subdomain as their own! • As this subdomain is already setup and verified previously, no additional verification will be required for the new account created by the hacker.
- 14. The Attack Scenario • Now, hacker can clone company’s website, create login pages, redirect users to login to the subdomain. • Even to the worst, hacker can email company’s user-base in some cases - and in turn steal their credentials. • This will lead to large scale hacking and in turn create a bad business credibility for company data handling and security practices.
- 15. NO BODY WAS EXCEPTION FOR THIS!!!
- 17. iFIXIT SUBDOMAIN TAKOVER Subdomain Takeover in 3 easy steps!!! 1. Found a subdomain point to an expired Shopify shop.
- 18. iFIXIT SUBDOMAIN TAKOVER 2. Signed in into Shopify and linked the vulnerable subdomain with account
- 19. iFIXIT SUBDOMAIN TAKOVER 3. Subdomain successfully taken over!!!
- 21. • First You need to check the DNS info for CNAME Entry that should b something like (something.github.io) • After that visit the CNAME, also it should show the same Error as The subdomain is showing. • Now You need to create a New repository in Your Github account matching with the CNAME of the website then simply go to the settings of the repository and do the configurations. Hijacking Expired/Unlinked Github Pages
- 23. • Now Scroll down to the GitHub Pages section. Press Choose a theme and Select a New Theme for your Github page. Hijacking Expired/Unlinked Github Pages
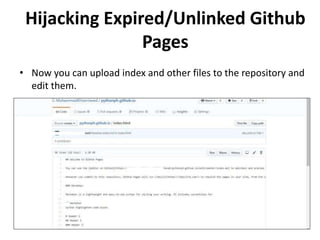
- 24. • Now you can upload index and other files to the repository and edit them. Hijacking Expired/Unlinked Github Pages
- 25. • Last step is just to add the vulnerable subdomain as Custom Domain. Hijacking Expired/Unlinked Github Pages
- 27. • To verify check the DNS entry for CNAME record it should be something like (site.desk.com) • After confirmation create an account on desk.com with the same CNAME. • Go to settings and add the subdomain in the Web address. Hijacking Expired/Unlinked Desk Pages
- 28. • After that just switch the status to Enable and the Subdomain will be yours Hijacking Expired/Unlinked Desk Pages
- 29. Is it really “hacking”? • It isn’t a hack even though it looks that way. • Its just that the subdomains point another domain using a CNAME-record. • However, imagine the case where someone aiming to steal credentials.
- 30. PREVENTION! • Preventing subdomain takeover starts with proper monitoring and analysis of the DNS records of your digital footprint. • Building and maintaining visibility on your dynamic digital footprint including the changes to your DNS configuration is key to address this problem before it's too late.
- 31. Tools to Enumerate Subdomains • HostileSubBruteforcer This tool was written by Ben Sadeghipour aka (@Nahamsec). It is written in Ruby and is one of the best tools for takeovers. This tool not only lists out subdomains by bruteforcing them, it also maps out where it points to. Along with that, if the domain throws out errors like ”This Github pages does not exist”, ”NoSuchBucket”, etc., it will print it out in red alert and asks you to check them for possible takeovers. • Sublist3r This tool is a package of multiple website’s results. It contains subdomains from VirusTotal, ThreatCrowd, DNSDumpster, PassiveDNS and many others. One bad side of this tool is that it might give out false positives. Some websites like DNSDumpster update their website after 1 month. Due to this, if a service was updated within that time period, DNSDumpster will take time to show it. Nonetheless, this is a great tool to have on your side
- 32. FEW MORE TOOLS… 1. Aquatone 2. Subjack 3. Sub6 4. Knockpy 5. Crt.sh
- 33. HAPPY HACKING!