CipherGraph Cloud VPN
- 1. Cloud Access Gateway Software Defined Security Infrastructure for Cloud
- 2. 23% 25% 27% 38% 45% 69% 44% 51% 53% 31% 35% 23% 32% 24% 20% 31% 19% 8% LACK OF EXPERTISE COST COMPLEXITY LOSS OF CONTROL COMPLIANCE SECURITY Levels of Concern About Cloud Hosting Organizations Remain Concerned about the security and compliance of their cloud deployments High Medium Low CipherGraph helps you gain marketshare Eliminate the impedance in your sales & integration • Security: Enterprise Class Security • AES 256 Encryption • In built Two-Factor Authentication • Role-Based Access Control • Compliance • Simplified PCI-DSS and HIPAA Compliance • Loss of Control • Simple VM based deployment • Full control of all network and security aspects • Completely independent of Cloud/Virtualization platform • Complexity • Complete setup in under 30 minutes • In-built support for Hybrid Cloud • Easy Load Balancing and High Availability • Cost • Low TCO and little ongoing maintenance • Opex Pricing, no hardware • Lack of Expertise • Simple to configure using existing basic IT skills Source: 451 Research
- 3. CipherGraph: True Enterprise Grade Cloud Security Solution Putting the Cloud at the center of your Network Hardware-free, instant enterprise class security Protect Public, Private, Hybrid clouds Protect Multisite and Distributed deployments PCI-DSS Compliance Two-Factor Authentication Role Based Access Control & Auditing Exceptional Performance - no data backhauling latency Easy Load-balancing and High Availability Full Support for Mobile Devices
- 4. Unify security, audit and access control across your hybrid setup: Direct-to-cloud Security for the distributed enterprise
- 5. Existing security solutions for Cloud Access: Do they really fit your needs? Hardware VPNs / Backhauling • Expensive – Spend up to $500K upfront as well as high operating costs • Rigid – Risk of technological obsolescence • Inelastic – Fixed capacity to be provisioned • Slow – extra hops to cloud / backhauling degrades performance, often unusable • Unsuitable – designed for datacenter topology, not cloud/BYOD Open Source Solutions • No Enterprise Focus – Not designed for enterprise apps and use cases • Poor Compliance – Not built for business class security regulatory compliance • High Maintenance and Ownership Cost – Difficult to setup, configure, and operate, leading to higher TCO • Scale & Reliability – Not built for Scale and high availability
- 6. Working with CipherGraph Getting started with CipherGraph CAG • Instant Deployment with Amazon AWS • Less than 20 Minutes for any other cloud or virtualization platform • Quick managed setup with other Cloud platforms and private datacenters • Simple Automated Deployment • No disruption of your deployment • Risk Free POC • No software install necessary for any server or application • Flexible pricing models
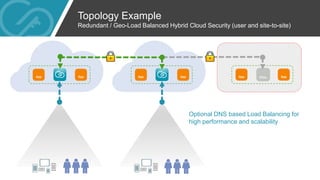
- 7. Topology Example Redundant / Geo-Load Balanced Hybrid Cloud Security (user and site-to-site) Optional DNS based Load Balancing for high performance and scalability
- 8. Key Features • Security Compliance on the cloud • Ready to use Two-factor authentication • Role Based Access Control • Multisite setup in minutes • High Availability and intelligent load balancing • Rich Audit reports and visibility into access and utilization • Zero-hardware deployment for enterprise class user access security • Rapid Deployment and POC speed up sales and integration
- 9. Selected typical use cases
- 10. Industry Use Case Strong Security / Compliance Needs • Organization needs advanced security • Optionally comply with PCI, HIPAA or others • Two factor authentication • Role Based Access Control • Rich Audit Reports • Examples • Healthcare, Finance, Government, E-Commerce etc. • Organizations needing access control for: • Employees / functions • Partners • Customers
- 11. Industry Use Case Hybrid Cloud or Phased Migration to cloud • Organization with on-prem footprint (temporary / permanent) • Unified and simple IT experience across all zones/deployments • Users would like access to datacenter as well as cloud apps • Hardware-free elastic model to effortlessly scale-up from small initial deployment • Enterprise class security is critical • Examples • Organization experimenting with cloud • Mid/large organizations setting up hybrid cloud
- 12. Industry Use Case Virtual Desktop Farm (VDI) • Organization requires secure VDI • Farm or virtual desktops to be secured behind firewall • (Optional) Restrict users to their assigned virtual desktop(s) • Users need access from non-windows platform (Remote Desktop within Browser) without data ever touching native client device • Examples • Finance, large retail / commerce organizations, scientific computing
- 13. Industry Use Case Multiple apps/protocols on cloud (web, client/server etc.) • Organization has some non-web apps on the cloud • Need support to secure even non http/https protocols • Access control to cover ports and protocols • High performance and low latency needed • Native/3rd party applications using client server protocols • Examples • Any domain • Presence of VoIP, client-server apps, RDP/VNC, Database protocols etc. a strong indicator • Need to prevent against espionage, DLP and APTs
- 14. Industry Use Case Cloud-first organizations • Organizations have no on-prem footprint • Have limited IT expertise • May have an evolving and increasing number/types of apps on cloud • Need very easy to deploy solution with web console only • Examples • Startups • Organizations moving completely to data centers (typically have little IT expertise)
- 15. Industry Use Case Geo-distributed enterprise • Organization has people/locations across the world • Need access from everywhere • Need native cloud security without multiple network hops/latency • Data backhauling has been ruled out due to bottlenecks it imposes • Examples • Organizations with many partners needing data access • Organizations with large number of roadwarriors (eg. Salespersons) • Organizations with offices across the world
- 16. Simple Audits and Analysis (examples) 25% 17% 0% 8% 8% 0% 8% 0% 0% 0% 8% 25% WINDOWS MAC OS X IOS Safari Netscape Firefox Chrome 32 700 411 317 51 303 88 EMILY JOHN DOE MICHAEL ALICE Mobile Non Mobile 12 5 20 90 134 32 18 13 40 71 175 12/19/2013 10:26 12/19/2013 10:27 12/19/2013 10:27 12/19/2013 19:43 12/19/2013 19:47 12/19/2013 19:53 12/19/2013 19:59 12/19/2013 20:01 12/19/2013 20:02 12/19/2013 20:04 12/19/2013 20:05 TESTUSER Detailed User Behavior
- 17. Full Network Access Audit logs (Analytics-ready)
- 18. Thank You Jitender Sharan (CEO) jsharan@ciphergraph.com Sales sales@ciphergraph.com | +1 415 287 0246 www.ciphergraph.com