3-D Secure 2.0
- 2. Hello! I am Peter Frick I am here because we have a story to tell. You can find me at peter.frick@netcetera.com 2
- 3. 1. Would you …? Let’s start with a personal question
- 4. Our CV ○ We have walked the ways of 3-D Secure since the early days. ○ One out of 2 cardholders in Germany rely on us. ○ Many more do so in Switzerland. 4
- 5. Authentication Do it right (again) ! 5
- 6. 45 % Is an average failure rate for people using a static password as means of authentication. 6
- 7. 96 % Is a proven, achievable success rate for an SMS OTP authentication mechanism. 7
- 8. 70 % When using an App which is secured by a PIN the number or successful authentications drop again . 8
- 9. Simplicity Don’t overload a user with fall-back means (just because we cover up for a technical insufficiency). As used sporadically and “under stress”, they often turn into a failure. Simplicity, when the time is right Timing Allow your users to switch between authentication methods at their convenience. Ensure your migration strategy is soft. 9
- 10. RBA Risk it! 10
- 11. Silent Run. Apply ! Simple Rules. No need to re- invent the wheel! 11
- 12. Yes, to anything! Our customers have experimented with Risk-Based Authentication already under 3DS 1.0 throughout the entire life cycle, from provisioning a card for an authentication method to securing each and every transaction. 12
- 13. Open-up! An old concept revived 13
- 14. All for 1, but still behind “walls”. 3-D Secure Authorize Prevent Fraud 14
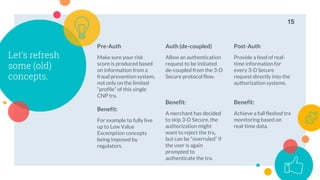
- 15. Pre-Auth Make sure your risk score is produced based on information from a fraud prevention system, not only on the limited “profile” of this single CNP trx. Auth (de-coupled) Allow an authentication request to be initiated de-coupled from the 3-D Secure protocol flow. Post-Auth Provide a feed of real- time information for every 3-D Secure request directly into the authorization systems. Let’s refresh some (old) concepts. Benefit: For example to fully live up to Low Value Excemption concepts being imposed by regulators. Benefit: A merchant has decided to skip 3-D Secure, the authorization might want to reject the trx, but can be “overruled” if the user is again prompted to authenticate the trx. Benefit: Achieve a full fleshed trx monitoring based on real-time data. 15
- 16. “ «If you want to be successful in a country where freedom is scarce, give your employees, customers and partners the freedom to think, experiment and act, and you will succeed in nearly anyhting”. - A friend from a country far South. 16
- 17. Thanks! You can find me at peter.frick@netcetera.com 17
- 18. Credits Special thanks to all the people who made and released these awesome resources for free: ○ Presentation template by SlidesCarnival ○ Photographs by Unsplash 18