An optimal algorithm for mutual exclusion in computer networks
- 1. Presented by: Sampson Akwafuo Jacob Hochstetler Authors: Glenn Ricart, National Institute of Health Ashok K. Agrawala, University of Maryland Review of: CSCE 6640
- 2. The paper proposes a novel algorithm for requesting and creating mutual exclusion Unlike similar algorithms, only 2(N-1) messages are sent and received in non-sharing memory location. 3 techniques can b used to achieve minimal number of messages: ◦ Sequential node-by-node processing ◦ Broadcast message ◦ Sending information through timing channels
- 3. Number of messages is minimal Delay/Time needed to achieve Mutual Exclusion is minimal Priority is based on first-come, first-served basis
- 4. Transactions are made on an error-free channel of communication, in which transit time may vary Nodes act symmetrically, without access to timing derived information Nodes operates correctly
- 7. 1. An intending node sends notifications to other nodes 2. All other nodes will reply granting their permission.
- 9. Upon receipt of the REQUEST message, the node: ◦ either sends a REPLY immediately (if the originator of the REQUEST message has priority) ◦ or defers a response until it leaves its own critical section. The priority order decision is made by comparing ◦ a sequence number present in each REQUEST message, ◦ or by using each nodes number to break ties if the sequence numbers are equal. The result is a total ordering among requesting nodes.
- 10. This process simply counts the number of REPLY messages, keeping track of how many messages are outstanding before the node can enter its Critical Section.
- 11. Imagine a network with 3 nodes. All nodes have 0 as their highest sequence number initially. Solid lines indicate REQUEST messages Requests are accompanied by sequence numbers Dashed lines indicates REPLY messages
- 12. 1. In Fig. (a), node 3 is the first to attempt Mutual Exclusion, It choses sequence number 1 and sends REQUEST messages to nodes 1 and 2 2. Before the arrival of Node 3’s messages, node 2 decides to invoke ME and enter critical section. It also chooses sequence number 1 and send out messages to nodes 1 and 3. (Fig (b))
- 13. Fig. (c) shows node 2's messages arriving at node l, which has not yet made a request itself, a REPLY is immediately generated. At node 3, 2's request is found to have an identical sequence number to 3's request; node 2 wins on the node number tie- breaking rule. A REPLY is sent. At node 2, 3's request is found to have an identical sequence number but loses the tie-breaker. A reply is deferred.
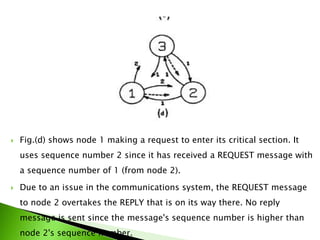
- 14. Fig.(d) shows node 1 making a request to enter its critical section. It uses sequence number 2 since it has received a REQUEST message with a sequence number of 1 (from node 2). Due to an issue in the communications system, the REQUEST message to node 2 overtakes the REPLY that is on its way there. No reply message is sent since the message's sequence number is higher than node 2's sequence number.
- 15. In Fig. (e), node 2 proceeds to its critical section since it has received both of the necessary replies. Node 1's REQUEST has also arrived at node 3 but has been deferred since the request's sequence number is higher than that selected by node 3. When node 2 has finished its critical section processing, it sends REPLY messages back to both nodes 1 and 3 (Fig. (f)).
- 16. In Fig. (g), nodes 1 and 3 have received their REPLY messages from node 2 but not yet from each other. Node 3's request has arrived at node 1. Since it bears a smaller sequence number, a REPLY is immediately generated. Figure l(h) shows node 3 entering its critical section after it received both replies.
- 17. In Fig. (i), node 3 has finished its critical section processing and is returning the deferred REPLY message to node 1. Finally in Figure l(j), node 1 begins critical section processing. At the conclusion of its critical section, node1 does nothing since it knows of no other node wishing to invoke mutual exclusion.
- 18. The sequence numbers are similar to the numbers used by Lamport's "bakery algorithm.“ They prevent high numbered nodes from being "shut-out" by lower numbered nodes. The node with the lowest number is the next one to enter the critical section. Ties are broken by comparing node numbers. A REPLY is generated when its sender agrees to allow the node sending a REQUEST to enter its critical section first. Once node A's REQUEST messages have been processed by all other nodes, no other node may enter its critical section twice before node A has entered its critical section This ensures a unique virtual ordering based on a first-come- first-served discipline.
- 19. Mutual exclusion is achieved when no pair of nodes is ever simultaneously in its critical section. For any pair of nodes, one must leave its critical section before the other may enter. Proof: Assuming the contrary is possible. Two nodes are in their critical section at the same time. Lets examine 3 cases.
- 20. Node A sent a REPLY to Node B's REQUEST before choosing its own sequence number. Therefore, A will choose a sequence number higher than B's sequence number. When B received A's REQUEST with a higher number, it must have found its own Requesting_Critical_Section = TRUE and A had received this request before sending its own REQUEST. The algorithm then directs B to defer the REQUEST and not reply until it has left its critical section. Then node A could not yet be in its critical section contrary to assumption.
- 21. CASE 2: Node B sent a REPLY to A's REQUEST before choosing its own sequence number. This is the mirror image of Case 1. CASE 3: Both nodes sent a REPLY to the other’s REQUEST after choosing their own sequence numbers. Both nodes must have found their own Requesting__Critical_Section to be TRUE when receiving the other's REQUEST message. Both nodes will compare the sequence number and node number in the REQUEST message to their own sequence and node numbers. The comparisons will lead to a node deferring the REQUEST until it has left its own critical section contradicting the assumption.
- 24. PROOF: Assume the contrary, that deadlock is possible. All requesting nodes must be unable to proceed their critical sections because one or more REPLYs are outstanding. REPLY could delayed because the REQUEST is deferred by another node which itself is waiting for REPLYs and cannot proceed. Therefore, there must exist a circuit of nodes, each of which has sent a REQUEST to its successor but has not received a REPLY. Since each node in the loop has deferred the REQUEST sent to it, it must be requesting the critical section itself and have found that the sequence number/node number pair in that REQUEST was greater than own. However, this cannot hold for all nodes in the supposed circuit, and thus the assertion must be true.
- 25. Starvation occurs when one node must wait indefinitely to enter its critical section even though other nodes are entering and exiting their own critical sections.
- 26. PROOF. Assume the contrary: (that starvation is possible.) Nodes receiving REQUEST messages will process them within finite time since the process which handles them does not block. After processing the REQUEST sent by the starving node, a receiving node cannot issue any new requests of its own with the same or lower sequence number. After some period of time the sequence number of the starving node will be the lowest of any requesting node. Any REQUESTs received by the starving node will be deferred, preventing any other node from entering its critical section. By the previous assertion, deadlock cannot occur and some process must be able to enter its critical section. Since it cannot be any other process, the starving process must be the one to enter its critical section.
- 27. The system allows only one REQUEST or REPLY messages from each node. If the network consists of N nodes, then 2*(N - l) is the minimum number required when nodes act independently and concurrently. Hence, the algorithm is optimal with regard to the number of messages exchanged.
- 28. For concurrency, at least one message must enter or leave each node. If no message enters/leaves, that node is not necessary to the algorithm Messages entering nodes must not wait for the messages generated at other nodes. This would indicate two separate messaging systems. 2*(N-1) must therefore be minimum for any parallel, symmetric, distributed algorithm. Serial node-by-node processing can also be achieved if the algorithm is modified so that messages are sent from node to node sequentially
- 29. Delay is defined as: ‘’the stretch of time beginning with the requesting node asking for the critical section and ending when that node enters its critical section.’’ The message execution time in the algorithm is assumed to be negligible compared to the message transmission times.
- 30. Assumption 1. No information from an external or central unit. It takes one round-trip time to determine the state of another node. Sending information through timing channels is impossible. Assumption 2. No node possesses the critical section resource when it has not been requested. This prevents a node or series of nodes from acting as a central control Assumption 3. Nodes do not anticipate requests.
Editor's Notes
- #7: A node enters its critical section after all other nodes have been notified of the request and have sent a reply granting their permission.
- #24: The system of nodes is said to be deadlocked when no node is in its critical section and no requesting node can ever proceed to its own critical section.
- #31: to Prevent Central Control of timing or extra information