Lesson_3.2- Data-link-Control Lesson_3.2- Data-link-Control.ppt
- 1. 1 Chapter 3 – Data Link Layer 3.2 Data Link Control
- 2. 2 Overview Data Link Control has the following functions: Framing Flow and Error Control Protocol
- 3. 3 FRAMING FRAMING •The data link layer needs to pack bits into The data link layer needs to pack bits into frames. frames. •Each frame is distinguishable from another. Each frame is distinguishable from another. •Framing types: Framing types: •Fixed-Size Framing: Boundary between frames is not necessary e.g. ATM networks. •Variable-Size Framing: need methods to define the end and the beginning of frames. We will discuss Character-oriented and Bit- oriented methods.
- 4. 4 A frame in a character-oriented protocol Byte stuffing and unstuffing
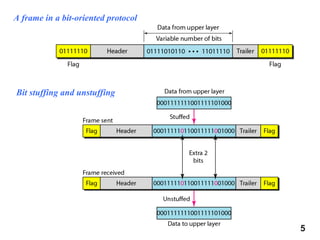
- 5. 5 A frame in a bit-oriented protocol Bit stuffing and unstuffing
- 6. 6 FLOW AND ERROR CONTROL FLOW AND ERROR CONTROL The most important responsibilities of the data link The most important responsibilities of the data link layer are layer are flow control flow control and and error control error control. . These functions are known as These functions are known as data link control data link control. . Error control in the data link layer is based on automatic repeat request, which is the retransmission of data. Flow control refers to a set of procedures used to restrict the amount of data that the sender can send before waiting for acknowledgment.
- 7. 7 PROTOCOLS PROTOCOLS - - How the data link layer can combine framing, flow control, and How the data link layer can combine framing, flow control, and error control to achieve the delivery of data from one node to error control to achieve the delivery of data from one node to another? another? - The protocols are normally implemented in software. - The protocols are normally implemented in software.
- 10. 10 NOISY CHANNELS NOISY CHANNELS Three protocols in this section that use error control. Three protocols in this section that use error control. Stop-and-Wait Automatic Repeat Request Go-Back-N Automatic Repeat Request Selective Repeat Automatic Repeat Request
- 11. 11 Stop-and-Wait ARQ •Keep a copy of the sent frame and retransmit the frame when the timer expires. •Use sequence numbers to number the frames. •The acknowledgment number always announces the sequence number of the next frame expected. •Sequence numbers are based on modulo-2 arithmetic.
- 12. 12 Design of the Stop-and-Wait ARQ Protocol
- 13. 13 Example: Assume that, in a Stop-and-Wait ARQ system, the bandwidth of the line is 1 Mbps, and 1 bit takes 20 ms to make a round trip. If the system data frames are 1000 bits in length, what is the utilization percentage of the link? Solution: The bandwidth-delay product is Link utilization •The system can send 20,000 bits during the time it takes for the data to go from the sender to the receiver and then back again. •However, the system sends only 1000 bits i.e. the link utilization is only 1000/20,000, or 5%. •For a link with a high bandwidth or long delay, the use of Stop-and- Wait ARQ wastes the capacity of the link.
- 14. 14 Go-Back-N Automatic Repeat Request Selective Repeat Automatic Repeat Request •Send several frames before receiving acknowledgments •Keep a copy of sent frames before acknowledgements arrive
- 15. 15 •In the Go-Back-N Protocol, the sequence numbers are modulo 2m , where m is the size of the sequence number field in bits. Go-Back-N Automatic Repeat Request
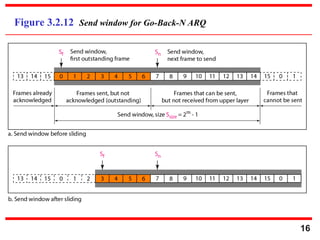
- 16. 16 Figure 3.2.12 Send window for Go-Back-N ARQ
- 17. 17 The send window is an abstract concept defining an imaginary box of size 2m − 1 with three variables: Sf, Sn, and Ssize. Note
- 18. 18 The send window can slide one or more slots when a valid acknowledgment arrives. Note
- 19. 19 Figure 3.2.13 Receive window for Go-Back-N ARQ
- 20. 20 The receive window is an abstract concept defining an imaginary box of size 1 with one single variable Rn. The window slides when a correct frame has arrived; sliding occurs one slot at a time. Note
- 21. 21 Figure 3.2.14 Design of Go-Back-N ARQ
- 22. 22 Figure 3.2.15 Window size for Go-Back-N ARQ
- 23. 23 In Go-Back-N ARQ, the size of the send window must be less than 2m ; the size of the receiver window is always 1. Note
- 24. 24 Algorithm 3.2.7 Go-Back-N sender algorithm (continued)
- 25. 25 Algorithm 3.2.7 Go-Back-N sender algorithm (continued)
- 26. 26 Algorithm 3.2.8 Go-Back-N receiver algorithm
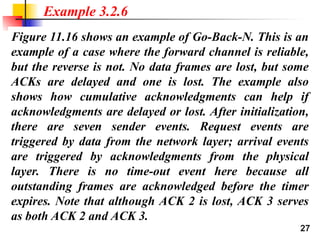
- 27. 27 Example 3.2.6 Figure 11.16 shows an example of Go-Back-N. This is an example of a case where the forward channel is reliable, but the reverse is not. No data frames are lost, but some ACKs are delayed and one is lost. The example also shows how cumulative acknowledgments can help if acknowledgments are delayed or lost. After initialization, there are seven sender events. Request events are triggered by data from the network layer; arrival events are triggered by acknowledgments from the physical layer. There is no time-out event here because all outstanding frames are acknowledged before the timer expires. Note that although ACK 2 is lost, ACK 3 serves as both ACK 2 and ACK 3.
- 28. 28 Figure 3.2.16 Flow diagram for Example 11.6
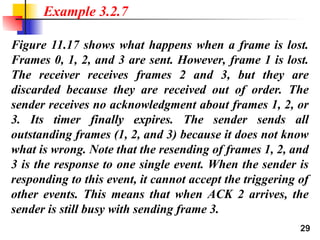
- 29. 29 Figure 11.17 shows what happens when a frame is lost. Frames 0, 1, 2, and 3 are sent. However, frame 1 is lost. The receiver receives frames 2 and 3, but they are discarded because they are received out of order. The sender receives no acknowledgment about frames 1, 2, or 3. Its timer finally expires. The sender sends all outstanding frames (1, 2, and 3) because it does not know what is wrong. Note that the resending of frames 1, 2, and 3 is the response to one single event. When the sender is responding to this event, it cannot accept the triggering of other events. This means that when ACK 2 arrives, the sender is still busy with sending frame 3. Example 3.2.7
- 30. 30 The physical layer must wait until this event is completed and the data link layer goes back to its sleeping state. We have shown a vertical line to indicate the delay. It is the same story with ACK 3; but when ACK 3 arrives, the sender is busy responding to ACK 2. It happens again when ACK 4 arrives. Note that before the second timer expires, all outstanding frames have been sent and the timer is stopped. Example 3.2.7 (continued)
- 31. 31 Figure 3.2.17 Flow diagram for Example 11.7
- 32. 32 Stop-and-Wait ARQ is a special case of Go-Back-N ARQ in which the size of the send window is 1. Note
- 33. 33 Figure 3.2.18 Send window for Selective Repeat ARQ
- 34. 34 Figure 3.2.19 Receive window for Selective Repeat ARQ
- 35. 35 Figure 3.2.20 Design of Selective Repeat ARQ
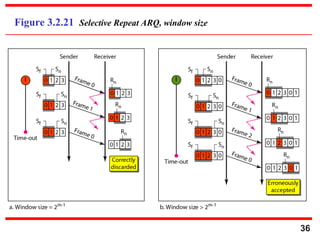
- 36. 36 Figure 3.2.21 Selective Repeat ARQ, window size
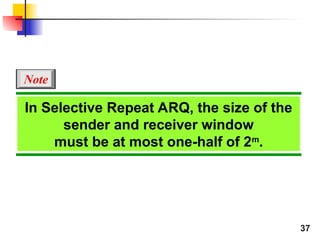
- 37. 37 In Selective Repeat ARQ, the size of the sender and receiver window must be at most one-half of 2m . Note
- 38. 38 Algorithm 3.2.9 Sender-site Selective Repeat algorithm (continued)
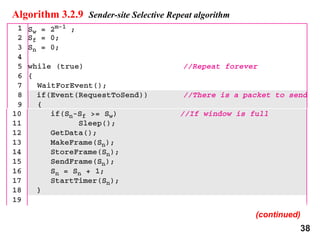
- 39. 39 Algorithm 3.2.9 Sender-site Selective Repeat algorithm (continued) (continued)
- 40. 40 Algorithm 3.2.9 Sender-site Selective Repeat algorithm (continued)
- 41. 41 Algorithm 3.2.10 Receiver-site Selective Repeat algorithm
- 42. 42 Algorithm 3.2.10 Receiver-site Selective Repeat algorithm
- 43. 43 Figure 3.2.22 Delivery of data in Selective Repeat ARQ
- 44. 44 This example is similar to Example 11.3 in which frame 1 is lost. We show how Selective Repeat behaves in this case. Figure 11.23 shows the situation. One main difference is the number of timers. Here, each frame sent or resent needs a timer, which means that the timers need to be numbered (0, 1, 2, and 3). The timer for frame 0 starts at the first request, but stops when the ACK for this frame arrives. The timer for frame 1 starts at the second request, restarts when a NAK arrives, and finally stops when the last ACK arrives. The other two timers start when the corresponding frames are sent and stop at the last arrival event. Example 3.2.8
- 45. 45 At the receiver site we need to distinguish between the acceptance of a frame and its delivery to the network layer. At the second arrival, frame 2 arrives and is stored and marked, but it cannot be delivered because frame 1 is missing. At the next arrival, frame 3 arrives and is marked and stored, but still none of the frames can be delivered. Only at the last arrival, when finally a copy of frame 1 arrives, can frames 1, 2, and 3 be delivered to the network layer. There are two conditions for the delivery of frames to the network layer: First, a set of consecutive frames must have arrived. Second, the set starts from the beginning of the window. Example 3.2.8 (continued)
- 46. 46 Another important point is that a NAK is sent after the second arrival, but not after the third, although both situations look the same. The reason is that the protocol does not want to crowd the network with unnecessary NAKs and unnecessary resent frames. The second NAK would still be NAK1 to inform the sender to resend frame 1 again; this has already been done. The first NAK sent is remembered (using the nakSent variable) and is not sent again until the frame slides. A NAK is sent once for each window position and defines the first slot in the window. Example 3.2.8 (continued)
- 47. 47 The next point is about the ACKs. Notice that only two ACKs are sent here. The first one acknowledges only the first frame; the second one acknowledges three frames. In Selective Repeat, ACKs are sent when data are delivered to the network layer. If the data belonging to n frames are delivered in one shot, only one ACK is sent for all of them. Example 3.2.8 (continued)
- 48. 48 Figure 3.2.23 Flow diagram for Example 11.8
- 49. 49 Figure 3.2.24 Design of piggybacking in Go-Back-N ARQ
- 50. 50 3.2-6 HDLC 3.2-6 HDLC High-level Data Link Control (HDLC) High-level Data Link Control (HDLC) is a is a bit-oriented bit-oriented protocol for communication over point-to-point and protocol for communication over point-to-point and multipoint links. It implements the ARQ mechanisms multipoint links. It implements the ARQ mechanisms we discussed in this chapter. we discussed in this chapter. Configurations and Transfer Modes Frames Control Field Topics discussed in this section: Topics discussed in this section:
- 51. 51 Figure 3.2.25 Normal response mode
- 52. 52 Figure 3.2.26 Asynchronous balanced mode
- 53. 53 Figure 3.2.27 HDLC frames
- 54. 54 Figure 3.2.28 Control field format for the different frame types
- 55. 55 Table 3.2.1 U-frame control command and response
- 56. 56 Figure 11.29 shows how U-frames can be used for connection establishment and connection release. Node A asks for a connection with a set asynchronous balanced mode (SABM) frame; node B gives a positive response with an unnumbered acknowledgment (UA) frame. After these two exchanges, data can be transferred between the two nodes (not shown in the figure). After data transfer, node A sends a DISC (disconnect) frame to release the connection; it is confirmed by node B responding with a UA (unnumbered acknowledgment). Example 3.2.9
- 57. 57 Figure 3.2.29 Example of connection and disconnection
- 58. 58 Figure 11.30 shows an exchange using piggybacking. Node A begins the exchange of information with an I-frame numbered 0 followed by another I-frame numbered 1. Node B piggybacks its acknowledgment of both frames onto an I-frame of its own. Node B’s first I-frame is also numbered 0 [N(S) field] and contains a 2 in its N(R) field, acknowledging the receipt of A’s frames 1 and 0 and indicating that it expects frame 2 to arrive next. Node B transmits its second and third I-frames (numbered 1 and 2) before accepting further frames from node A. Example 3.2.10
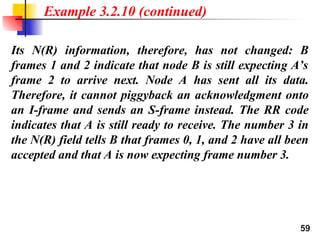
- 59. 59 Its N(R) information, therefore, has not changed: B frames 1 and 2 indicate that node B is still expecting A’s frame 2 to arrive next. Node A has sent all its data. Therefore, it cannot piggyback an acknowledgment onto an I-frame and sends an S-frame instead. The RR code indicates that A is still ready to receive. The number 3 in the N(R) field tells B that frames 0, 1, and 2 have all been accepted and that A is now expecting frame number 3. Example 3.2.10 (continued)
- 60. 60 Figure 3.2.30 Example of piggybacking without error
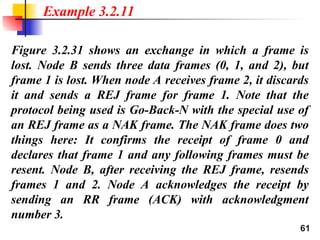
- 61. 61 Figure 3.2.31 shows an exchange in which a frame is lost. Node B sends three data frames (0, 1, and 2), but frame 1 is lost. When node A receives frame 2, it discards it and sends a REJ frame for frame 1. Note that the protocol being used is Go-Back-N with the special use of an REJ frame as a NAK frame. The NAK frame does two things here: It confirms the receipt of frame 0 and declares that frame 1 and any following frames must be resent. Node B, after receiving the REJ frame, resends frames 1 and 2. Node A acknowledges the receipt by sending an RR frame (ACK) with acknowledgment number 3. Example 3.2.11
- 62. 62 Figure 3.2.31 Example of piggybacking with error
- 63. 63 3.2-7 POINT-TO-POINT PROTOCOL 3.2-7 POINT-TO-POINT PROTOCOL Although HDLC is a general protocol that can be used Although HDLC is a general protocol that can be used for both point-to-point and multipoint configurations, for both point-to-point and multipoint configurations, one of the most common protocols for point-to-point one of the most common protocols for point-to-point access is the access is the Point-to-Point Protocol (PPP). Point-to-Point Protocol (PPP). PPP is a PPP is a byte-oriented byte-oriented protocol. protocol. Framing Transition Phases Multiplexing Multilink PPP Topics discussed in this section: Topics discussed in this section:
- 64. 64 Figure 11.32 PPP frame format
- 65. 65 PPP is a byte-oriented protocol using byte stuffing with the escape byte 01111101. Note
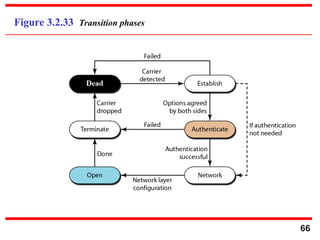
- 66. 66 Figure 3.2.33 Transition phases
- 67. 67 Figure 3.2.34 Multiplexing in PPP
- 68. 68 Figure 3.2.35 LCP packet encapsulated in a frame
- 69. 69 Table 3.2.2 LCP packets
- 70. 70 Table 3.2.3 Common options
- 71. 71 Figure 3.2.36 PAP packets encapsulated in a PPP frame
- 72. 72 Figure 3.2.37 CHAP packets encapsulated in a PPP frame
- 73. 73 Figure 3.2.38 IPCP packet encapsulated in PPP frame
- 74. 74 Table 3.2.4 Code value for IPCP packets
- 75. 75 Figure 3.2.39 IP datagram encapsulated in a PPP frame
- 76. 76 Figure 3.2.40 Multilink PPP
- 77. 77 Let us go through the phases followed by a network layer packet as it is transmitted through a PPP connection. Figure 3.2.41 shows the steps. For simplicity, we assume unidirectional movement of data from the user site to the system site (such as sending an e-mail through an ISP). The first two frames show link establishment. We have chosen two options (not shown in the figure): using PAP for authentication and suppressing the address control fields. Frames 3 and 4 are for authentication. Frames 5 and 6 establish the network layer connection using IPCP. Example 3.2.12
- 78. 78 The next several frames show that some IP packets are encapsulated in the PPP frame. The system (receiver) may have been running several network layer protocols, but it knows that the incoming data must be delivered to the IP protocol because the NCP protocol used before the data transfer was IPCP. After data transfer, the user then terminates the data link connection, which is acknowledged by the system. Of course the user or the system could have chosen to terminate the network layer IPCP and keep the data link layer running if it wanted to run another NCP protocol. Example 3.2.12 (continued)
- 79. 79 Figure 3.2.41 An example
- 80. 80 Figure 3.2.41 An example (continued)


















































![58
Figure 11.30 shows an exchange using piggybacking.
Node A begins the exchange of information with an
I-frame numbered 0 followed by another I-frame
numbered 1. Node B piggybacks its acknowledgment of
both frames onto an I-frame of its own. Node B’s first
I-frame is also numbered 0 [N(S) field] and contains a 2
in its N(R) field, acknowledging the receipt of A’s frames
1 and 0 and indicating that it expects frame 2 to arrive
next. Node B transmits its second and third I-frames
(numbered 1 and 2) before accepting further frames from
node A.
Example 3.2.10](https://image.slidesharecdn.com/lesson3-250427145229-f3097bb1/85/Lesson_3-2-Data-link-Control-Lesson_3-2-Data-link-Control-ppt-58-320.jpg)