Authshield integration with mails
- 1. AuthShield Security for Mails Private and Confidential
- 2. “If you were a hacker trying to hack into an organization – what will be your attack methodology? Attack the perimeter (IP Range), scan it for vulnerabilities, try and find a way behind the firewall, IPS, IDS and then find a vulnerability in the router to sniff traffic. (P.S – CISCO spends up to $ 50 Mn every year to scan their routers for vulnerabilities). You will also have to hide your traces during this entire exercise to prevent from getting caught Go on Social media. Identify employees working in the organization. Chat up with them, and carry out a phishing scam to get access to their credentials. Use the same credentials to log into the critical IT assets of the organization” Private and Confidential2
- 3. Vulnerabilities in E-mails Private and Confidential3
- 4. Most vulnerable Point of Attack Private and Confidential4 Credential Access Granted Server
- 5. Mails – Warehouse of Information on the Go! E-mails are an integral part of our communication mechanisms Can be accessed anywhere in the world on almost every device Considered as written proof of communication in many countries Can be used to steal information or to impersonate senior members of an organization Private and Confidential5 As per Internet Crime Complaint Center (IC3) in the past fourteen months there have 1200 US and over 900 non US victims where business mails have been compromised
- 6. Microsoft Exchange Private and Confidential6 • Microsoft Exchange had an installed base of 470 million in 2014 • Microsoft Exchange uses a propriety RPC protocol, MAPI / RPC that was designed to be used by Microsoft Outlook • Emails hosted on exchange can also be accessed using SMTP, POP3 and IMAP4 protocols • Many Android, iOS and Windows Mobile phones now support Exchange ActiveSync Push Email
- 7. Why AuthShield 2FA Private and Confidential7 • Most Cyber attacks are Phishing related scams and effective in majority of cases • A non aware user is the weakest link in the Cyber Security Chain • Every organization needs to protect their mails as they are one of the most critical assets of an organization
- 8. Tackling Identity Theft Only Protection against User Level Attacks • Identify the user based on – – Something he knows (User Name / Password) – Something in the user’s possession – Something the user is Private and Confidential8
- 9. Private and Confidential9 Username, Password + Second Factor of Authentication Access Granted Server Username + Password ACCESS DENIED Hacker may have access to the Password but he cannot have access to the “Second Factor of Authentication”
- 10. How is AuthShield different?? AuthShield Patented Protocol Decoding Engine ensures that Authentication Security is implemented at a Protocol level rather than Application layer Authentication Security has been limited to applications which provide inherent support for 2FA Private and Confidential10
- 12. Solution Components Private and Confidential12
- 13. AuthShield Tokens for OWA Private and Confidential13 Hard Token Android / iOS / Windows /BB Linux / Mac / Windows
- 14. Hard Token Private and Confidential14 • Security device (Hard Token) given to authorized users • The token generates a new password after every 90 seconds • Each token is unique to the user and synchronized with the server based on time • The password is based on a pre defined unbreakable randomized algorithm. Hard Token
- 15. Mobile Token for Smart Phones • Application installed on smart Phones • User identity is mapped to his smartphone • User has to enter PIN to generate the One Time Password • Available for all smart phones Private and Confidential15 Android / iOS / Windows /BB
- 16. Soft Token for Desktops • Application installed on Desktop • User identity is mapped to his desktop • User has to enter PIN to generate the token • Available for all OS Private and Confidential16 Linux / Mac / Windows
- 17. AuthShield Tokens for OWA / ActiveSync / Outlook Anywhere Private and Confidential17 One Touch Authentication for Windows / Linux / Mac Systems OS One Touch Authentication for Android / iOS / Windows Phones
- 18. Mobile One Touch Authentication • Maps users identity to his registered mobile phones • Anytime a user wishes to login, a ‘PUSH’ notification is sent with details on – – IP – Location – TimeStamp • User has to ‘Approve’ the request to login Private and Confidential18
- 19. System One Touch Authentication • Maps users identity to his registered Desktop / Laptop • Anytime a user wishes to login, a ‘PUSH’ notification is sent with details on – – IP – Location – TimeStamp • User has to ‘Approve’ the request to login Private and Confidential19
- 20. User Name and Password are validated from AD On correct validation, request is forwarded to the Authentication Server Users device is mapped against his registered devices In case users device is different from his registered device, an Authentication Notification sent to the registered device(s) of the user User has to approve the Authentication request for the mails to be downloaded on his non-registered device Private and Confidential20 Process Flow
- 21. Private and Confidential21 Process Flow
- 22. About Us Private and Confidential22 About the Company Research Oriented Information Security Organization All technologies are indigenous - Evaluated and approved by multiple Government Agencies Empanelled with DRDO More than six years of experience in Cyber Security Served key clients in Private and Public sector
- 23. Contd. Private and Confidential23 Features Patents on 2FA with Protocol level decoding Direct integration of 2FA with – SAP / ERP Mail servers – Microsoft Exchange, OCMS, IBM Lotus Nodes, Zimbra etc VPN Database Queries Web Applications etc Customized products focused on technology immersion in clients
- 25. In the Press Private and Confidential25 “Rated 9/10 by PC Quest Magazine” “DRDO Implements AuthShield Authentication Security” “AuthShield launches Zero cost Biometrics” “Mindteck has appointed AuthShield for MFA”
- 26. Our Success Stories!!! Empanelled with DRDO for Multi-factor Authentication Only Indian Company to have developed an indigenous Multi-factor Authentication at Protocol Level. Only Indian Company to have developed and deployed an independent Internet Monitoring System across an entire region. Multiple Patent Pending Technologies including Cyber Café Surveillance, Tactical Internet Monitoring System and Multifactor Authentication. Private and Confidential26
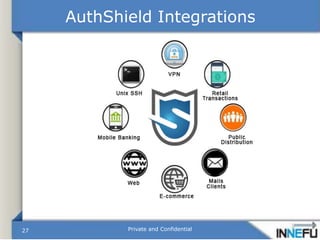
- 27. AuthShield Integrations Private and Confidential27
- 28. Support • 24 * 7 Support center • Dedicated Helpline and Ticketing portal with monthly reports (on support as well as application performance) submitted to client • SLA with inbuilt penalty clauses - Timeframes defined for critical, priority and non-critical support • Optional - Dedicated Team deployed for client (for Priority support) Private and Confidential28
- 29. Some of our Government Clients Private and Confidential29 Delhi Police Ministry of Home Affairs Indian Army Ministry of Defense National Investigation AgencyAP Police UP Police National Technical Research Organization Chandigarh Police JK Police
- 30. Some of our other clients Private and Confidential30
- 31. Contact Us Private and Confidential31 @ authshield2FA +91-11-47065866/ 45272272 info@innefu.com www.auth-shield.com / www.innefu.com 876, 8th Floor, Aggarwal Cyber Plaza II, Netaji Subhash Place, New Delhi, India GET IN TOUCH WITH US. WE’D BE HAPPY TO HELP