Ch10
- 1. Chapter 10: File-System Interface
- 2. Files
- 3. File Concept & Structure Contiguous persistent logical address space, can be storing data or programs File Structure: None - sequence of words, bytes Simple record structure Lines Fixed length Variable length Complex Structures Formatted document Relocatable load file Can simulate last two with first method by inserting appropriate control characters Who decides: Operating system Program
- 4. File Attributes Name – only information kept in human-readable form Identifier – unique tag (number) identifies file within file system Type – needed for systems that support different types Location – pointer to file location on device Size – current file size Protection – controls who can do reading, writing, executing Time, date, and user identification – data for protection, security, and usage monitoring Information about files are kept in the directory structure, which is maintained on the disk
- 5. Example of File Attributes UNIX: ls -li 26047823 -rw-r--r-- 1 Salim staff 596480 Mar 16 20:17 Lecture10.ppt
- 6. File Operations File is an abstract data type File operations: Create Write Read Reposition within file Delete Truncate Open(F i ) – search the directory structure on disk for entry F i , and move the content of entry to memory Close (F i ) – move the content of entry F i in memory to directory structure on disk
- 7. Open Files Several pieces of data are needed to manage open files: File pointer: pointer to last read/write location, per process that has the file open File-open count: counter of number of times a file is open – to allow removal of data from open-file table when last processes closes it Disk location of the file: cache of data access information Access rights: per-process access mode information
- 8. Open File Locking Provided by some operating systems and file systems Mediates access to a file Mandatory or advisory: Mandatory – access is denied depending on locks held and requested Advisory – processes can find status of locks and decide what to do
- 9. File Types – Name, Extension
- 10. Access Methods Sequential Access read next write next reset no read after last write (rewrite) Direct Access read n write n position to n read next write next rewrite n n = relative block number
- 12. Simulation of Sequential Access on a Direct-access File
- 13. Example of Index and Relative Files
- 14. Directories
- 15. Directory Structure A collection of nodes containing information about all files F 1 F 2 F 3 F 4 F n Directory Files Both the directory structure and the files reside on disk Backups of these two structures are kept on tapes
- 16. A Typical File-system Organization
- 17. Operations Performed on Directory Search for a file Create a file Delete a file List a directory Rename a file Traverse the file system
- 18. Organize the Directory (Logically) to Obtain Efficiency – locating a file quickly Naming – convenient to users Two users can have same name for different files The same file can have several different names Grouping – logical grouping of files by properties, (e.g., all Java programs, all games, …)
- 19. Single-Level Directory A single directory for all users Naming problem Grouping problem
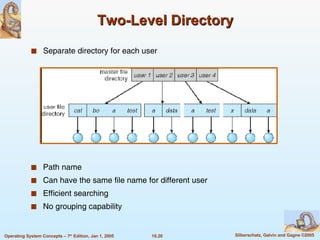
- 20. Two-Level Directory Separate directory for each user Path name Can have the same file name for different user Efficient searching No grouping capability
- 22. Tree-Structured Directories (Cont) Efficient searching Grouping Capability Current directory (working directory) cd /spell/mail/prog type list
- 23. Tree-Structured Directories (Cont) Absolute or relative path name Creating a new file is done in current directory Delete a file rm <file-name> Creating a new subdirectory is done in current directory mkdir <dir-name> Example: if in current directory /mail mkdir count mail prog copy prt exp count Deleting “mail” deleting the entire subtree rooted by “mail”
- 24. Acyclic-Graph Directories Have shared subdirectories and files
- 25. Acyclic-Graph Directories (Cont.) Two different names (aliasing) If dict deletes list dangling pointer Solutions: Backpointers, so we can delete all pointers Variable size records a problem Backpointers using a daisy chain organization Entry-hold-count solution New directory entry type Link – another name (pointer) to an existing file Resolve the link – follow pointer to locate the file
- 27. General Graph Directory (Cont.) How do we guarantee no cycles? Allow only links to file not subdirectories Garbage collection Every time a new link is added use a cycle detection algorithm to determine whether it is OK
- 28. File System Mounting A file system must be mounted before it can be accessed A unmounted file system (i.e. Fig. 11-11(b)) is mounted at a mount point
- 29. (a) Existing. (b) Unmounted Partition
- 30. Mount Point