Editor's Notes
- #4: imagine that the dots are Web sites and the user is going from web site to web site to accomplish some task.
- #5: existing browsers offer little help with this task Nearly everything we do only involves multiple Web sites, but there’s no help in connecting them.
- #6: context is: - relevant data to the Web task - links multiple sites - what the user cares about CA generates a browsing experience that links together formerly disconnected experiences and ven modifies individual sites.
- #9: Cookies and sessions are a way of creating context within a single site HTTP is designed to be stateless. Each page stands alone.
- #10: Single sign on is an example of cross-site context - single purpose: authentication context - still not leveraging this as we could. Having a single login that works on multiple sites isn’t the same as having a single authentication context for a given Web episode.
- #11: TrustWatch is a browser extension that provides a security context for users that uses a could-based service for site verification.
- #17: FF and IE have discovered that others will create interesting add-ons to their browsers. They encourage third party developers to build extensions to their platforms. Still some work to do here. Safari not very open. Especially on iPhone.
- #18: FF and IE have discovered that others will create interesting add-ons to their browsers. They encourage third party developers to build extensions to their platforms. Still some work to do here. Safari not very open. Especially on iPhone.
- #19: FF and IE have discovered that others will create interesting add-ons to their browsers. They encourage third party developers to build extensions to their platforms. Still some work to do here. Safari not very open. Especially on iPhone.
- #20: FF and IE have discovered that others will create interesting add-ons to their browsers. They encourage third party developers to build extensions to their platforms. Still some work to do here. Safari not very open. Especially on iPhone.
- #21: - Web 2.0 has made moves toward this individualization, but is stuck in the ad hoc rule. Web 2.0 drives the need for context.
- #22: - Web 2.0 has made moves toward this individualization, but is stuck in the ad hoc rule. Web 2.0 drives the need for context.
- #23: - Web 2.0 has made moves toward this individualization, but is stuck in the ad hoc rule. Web 2.0 drives the need for context.
- #24: - Web 2.0 has made moves toward this individualization, but is stuck in the ad hoc rule. Web 2.0 drives the need for context.
- #25: Fundamentally different than other solutions like OpenID. Cryptographically sound. Deep use cases, not shallow.
- #26: Fundamentally different than other solutions like OpenID. Cryptographically sound. Deep use cases, not shallow.
- #27: Fundamentally different than other solutions like OpenID. Cryptographically sound. Deep use cases, not shallow.
- #28: Fundamentally different than other solutions like OpenID. Cryptographically sound. Deep use cases, not shallow.
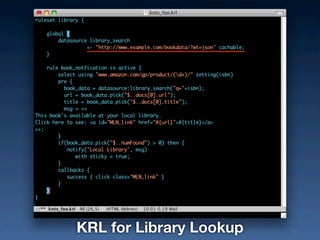
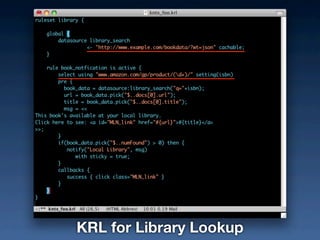
- #35: Greasemonkey - scripts on the browser not the cloud
- #36: Greasemonkey - scripts on the browser not the cloud
- #37: Greasemonkey - scripts on the browser not the cloud
- #42: Structure browsing - connects the dots and threads the experience opt-in, user controlled
- #43: Structure browsing - connects the dots and threads the experience opt-in, user controlled
- #44: Structure browsing - connects the dots and threads the experience opt-in, user controlled
- #45: Structure browsing - connects the dots and threads the experience opt-in, user controlled
- #51: No one’s ever surprised me with a GUI
- #52: No one’s ever surprised me with a GUI
- #53: No one’s ever surprised me with a GUI
- #79: The combination of browser as platform, cloud-based functionality, & strong identity yield an architecture for generating browsing experiences that are ...
- #80: The combination of browser as platform, cloud-based functionality, & strong identity yield an architecture for generating browsing experiences that are ...
- #81: The combination of browser as platform, cloud-based functionality, & strong identity yield an architecture for generating browsing experiences that are ...
- #82: The combination of browser as platform, cloud-based functionality, & strong identity yield an architecture for generating browsing experiences that are ...
- #83: The combination of browser as platform, cloud-based functionality, & strong identity yield an architecture for generating browsing experiences that are ...
- #84: The combination of browser as platform, cloud-based functionality, & strong identity yield an architecture for generating browsing experiences that are ...