Continuous variable quantum key distribution finite key analysis of composable security against coherent attacks
- 1. Institute for Theoretical Physics Quantum Information Group Continuous Variable Quantum Key Distribution: Finite-Key Analysis of Composable Security against Coherent Attacks Fabian Furrer Leibniz Universität Hannover PRL 109, 100502 Joint work with T. Franz, R. F. Werner (Leibniz Universität Hannover) M. Berta, A. Leverrier, V.B. Scholz, (ETH Zurich) M. Tomamichel (CQT Singapore) Qcrypt 2012, Singapore, 14.09.2012
- 2. Security of a QKD Protocol Security Analysis Constraints: -Key length Information theoretic -Certification Experimental of security ? Experimental Secure implementation Key Minimizing the assumption and maximizing the key length! FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 2
- 3. Security of a QKD Protocol Constraints: Information theoretic Asymptotic key rate vs. finite uses of QM channel (finite-key effects) Notion of security: composable? Limitation on attacks: collective (tensor product) or coherent (general)? ... Experimental / Implementation Model of the measurement devices Model of the quantum source ... FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 3
- 4. Contribution: Security analysis for continuous variable (CV) protocol based on the distribution of two-mode squeezed states (EPR states) measured via homodyne detection. FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 4
- 5. Contribution: Security analysis for continuous variable (CV) protocol based on the distribution of two-mode squeezed states (EPR states) measured via homodyne detection. What’s New: Computation of key length secure against coherent attacks for achievable experimental parameters. Security proof based on Uncertainty relation (c.f. Tomamichel et al., Nat. Comm. 3, 634 ,2012) FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 5
- 6. Discrete Variables vs. Continuous Variables Implementation -Encoding in finite-dimensional -Encoding in infinite-dimensional systems (e.g., polarization of photon) systems (bosonic modes) [1] -Gaussian States -Quadratures of EM-field: Homodyne or Heterodyne detection Advantage: - Compatible with standard telecom technology - high repetition rates for homodyne - efficient state preparation [1] Weedbrook et al., Reviews of Modern Physics 84, 621 (2012) FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 6
- 7. Security Analysis for CV QKD Protocols Challenge: infinite dimensions Finite-Key Analysis: - Leverrier et al, Phys. Rev. A 81, 062343 (2010) - Berta, FF, Scholz, arXiv:1107.5460 (2011) Lifting proofs from collective to coherent (general) attacks: Exponential de Finetti [Renner & Cirac, PRL 102, 110504 (2009)] Problem: Bad bounds, feasible only in the asymptotic limit Post-selection technique, Recent: Leverrier et al., arXiv:1208.4920 (Talk on Monday) FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 7
- 8. Security Analysis for CV QKD Protocols Challenge: infinite dimensions Finite-Key Analysis: - Leverrier et al, Phys. Rev. A 81, 062343 (2010) - Berta, FF, Scholz, arXiv:1107.5460 (2011) Lifting proofs from collective to coherent (general) attacks: Exponential de Finetti [Renner & Cirac, PRL 102, 110504 (2009)] Problem: Bad bounds, feasible only in the asymptotic limit Post-selection technique, Recent: Leverrier et al., arXiv:1208.4920 (Talk on Monday) Uncertainty Relation (direct) : This Talk! Advantage: one-sided device independent no tomography no additional measurements FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 8
- 9. Outline 1. Security Definition and Finite-key length formula 2. Experimental Set Up and Protocol 3. Finite-Key Rates 4. (Security Analysis) FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 9
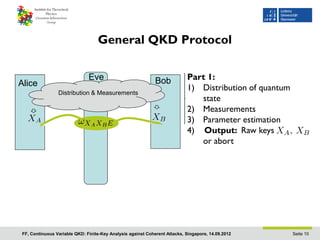
- 10. General QKD Protocol Eve Bob Part 1: Alice 1) Distribution of quantum Distribution & Measurements state 2) Measurements 3) Parameter estimation 4) Output: Raw keys or abort FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 10
- 11. General QKD Protocol Eve Bob Part 1: Alice 1) Distribution of quantum Distribution & Measurements state 2) Measurements 3) Parameter estimation 4) Output: Raw keys classical post processing or abort Part 2: 1) Error correction 2) Privacy amplification Output: Key FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 11
- 12. Security Definitions (trace distance) A protocol which outputs the state is secure if it is: correct : secret: where is the uniform distribution over all keys. Composable Secure* * R. Renner, PhD Thesis (ETH 2005) FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 12
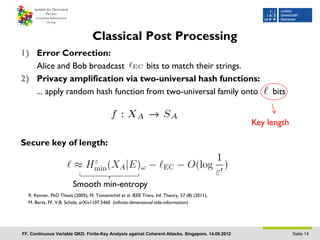
- 13. Classical Post Processing 1) Error Correction: Alice and Bob broadcast bits to match their strings. 2) Privacy amplification via two-universal hash functions: ... apply random hash function from two-universal family onto bits Key length FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 13
- 14. Classical Post Processing 1) Error Correction: Alice and Bob broadcast bits to match their strings. 2) Privacy amplification via two-universal hash functions: ... apply random hash function from two-universal family onto bits Key length Secure key of length: Smooth min-entropy R. Renner, PhD Thesis (2005), M. Tomamichel et al. IEEE Trans. Inf. Theory, 57 (8) (2011), M. Berta, FF, V.B. Scholz, arXiv1107.5460 (infinite-dimensional side-information) FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 14
- 15. Classical Post Processing 1) Error Correction: Alice and Bob broadcast bits to match their strings. 2) Privacy amplification via two-universal hash functions: ... apply random hash function from two-universal family onto bits Key length Secure key of length: Smooth min-entropy R. Renner, PhD Thesis (2005), M. Tomamichel et al. IEEE Trans. Inf. Th, 57 (8) (2011), M. Berta, FF, V.B. Scholz, arXiv1107.5460 (infinite-dimensional side-information) Use parameter estimation to bound min-entropy! FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 15
- 16. Experimental Set Up Source: two-mode squeezed state (EPR state) Measurements: homodyne detection, randomly either amplitude or phase (synchronized via LO) Entanglement based! Cerf, N. J., M. Levy, and G. van Assche, 2001, Phys. Rev. A 63, 052311 FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 16
- 17. Measurements Source: Correlated outcomes if both measure two-mode squeezed amplitude or phase: state Measurements: homodyne detection, randomly either amplitude or phase (synchronized via LO) Entanglement based! FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 17
- 18. Measurements Binning of the Outcome Range: Spacing parameter: Cutoff parameter: Outcome Range: FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 18
- 19. Protocol 1. Performing 2N measurements 2. Sifting: approx. N data points left 3. Parameter estimation: pick random sample of k data points and check correlation: Hamming distance: 4. Classical post-processing on remaining strings : FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 19
- 20. Protocol 1. Performing 2N measurements 2. Sifting: approx. N data points left 3. Parameter estimation: pick random sample of k data points and check correlation: Hamming distance: 4. Classical post-processing on remaining strings : A secret key of length can be extracted FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 20
- 21. Protocol 1. Performing 2N measurements 2. Sifting: approx. N data points left 3. Parameter estimation: pick random sample of k data points and check correlation: Hamming distance: 4. Classical post-processing on remaining strings : A secret key of length Statistical correction can be extracted Monotonic function Complementarity of amplitude and phase measurement: depending on spacing parameter FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 21
- 22. Finite-Key Length The key is ... composable secure provides security against coherent attacks Experimental constraints: Alice’s measurements are modeled by projections onto spectrum of quadrature operator for amplitude and phase (parameter: ) subsequent measurements commute trusted source in Alice’s lab of Gaussian states (can be relaxed) No assumptions about Bob’s measurements: one-sided device independent FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 22
- 23. Finite-Key Rates Key Rate depending on symmetric losses for two-mode squeezed state input squeezing/antisqueezing 11dB/16dB * error correction efficiency of 95% * T. Eberle et al., arXiv:1110.3977 excess noise of 1% * additional symmetric losses of ... 0% 4% 6% Plot: FF et al., PRL 109, 100502 (2012) FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 23
- 24. Key Rate versus Losses Key rate versus losses for N=10^9 sifted signal: Asymptotic optimal rate with perfect error correction Coherent attacks Gaussian collective attacks symmetric losses Plot: FF et al., PRL 109, 100502 (2012) FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 24
- 25. Security Analysis Based on Uncertainty Relation Extractable key length: Goal: bound for Key ingredient: Uncertainty relation with side-information* * Tomamichel & Renner, Phys. Rev. Lett. 106, 110506 (2011) FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 25
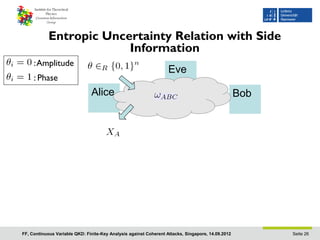
- 26. Entropic Uncertainty Relation with Side Information : Amplitude Eve : Phase Alice Bob FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 26
- 27. Entropic Uncertainty Relation with Side Information : Amplitude Eve : Phase Alice Bob uncertainty Eve has about uncertainty of Bob about outcome of Alice outcome of Alice complementary of the M. Tomamichel , PhD Thesis, measurements M. Berta, FF, V.B. Scholz, arXiv1107.5460 (2011) FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 27
- 28. Entropic Uncertainty Relation with Side Information : Amplitude Eve : Phase Alice Bob Data processing inequality M. Tomamichel et al., Phys. Rev. Lett. 106,110506 (2011), M. Tomamichel , PhD Thesis (2012); M. Berta, FF, V.B. Scholz, arXiv1107.5460 (2011) FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 28
- 29. Entropic Uncertainty Relation with Side Information : Amplitude Eve : Phase Alice Bob Data processing inequality Correlation betw. Alice & Bob M. Tomamichel et al., Phys. Rev. Lett. 106,110506 (2011), M. Tomamichel , PhD Thesis (2012); M. Berta, FF, V.B. Scholz, arXiv1107.5460 (2011) FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 29
- 30. Correlation between Alice & Bob Correlation between Alice and Bob can be bounded in terms of the Hamming distance of a random sample via Combining with Uncertainty Relation: FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 30
- 31. Conclusion Advantage: one-sided device independent (e.g. local oscillator included) direct approach (no additional measurements compared to post- selection approach) no state tomography robust under small deviations of experimental parameters Problems: very sensitive to noise asymptotically not optimal: Uncertainty relation not tight for the Gaussian states used in the protocol Implementation in Leibniz University in Hannover: Crypto on Campus: T. Eberle, V. Händchen, J. Duhme, T. Franz, R. F. Werner, and R. Schnabel FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 31
- 32. Thank you for your attention! FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 32




![Discrete Variables vs. Continuous Variables
Implementation
-Encoding in finite-dimensional -Encoding in infinite-dimensional
systems (e.g., polarization of photon) systems (bosonic modes) [1]
-Gaussian States
-Quadratures of EM-field:
Homodyne or Heterodyne
detection
Advantage:
- Compatible with standard
telecom technology
- high repetition rates for homodyne
- efficient state preparation
[1] Weedbrook et al., Reviews of Modern Physics 84, 621 (2012)
FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 6](https://image.slidesharecdn.com/continuousvariablequantumkeydistributionfinite-keyanalysisofcomposablesecurityagainstcoherentattacks-121214215358-phpapp01/85/Continuous-variable-quantum-key-distribution-finite-key-analysis-of-composable-security-against-coherent-attacks-6-320.jpg)
![Security Analysis for CV QKD Protocols
Challenge: infinite dimensions
Finite-Key Analysis:
- Leverrier et al, Phys. Rev. A 81, 062343 (2010)
- Berta, FF, Scholz, arXiv:1107.5460 (2011)
Lifting proofs from collective to coherent (general) attacks:
Exponential de Finetti [Renner & Cirac, PRL 102, 110504 (2009)]
Problem: Bad bounds, feasible only in the asymptotic limit
Post-selection technique,
Recent: Leverrier et al., arXiv:1208.4920 (Talk on Monday)
FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 7](https://image.slidesharecdn.com/continuousvariablequantumkeydistributionfinite-keyanalysisofcomposablesecurityagainstcoherentattacks-121214215358-phpapp01/85/Continuous-variable-quantum-key-distribution-finite-key-analysis-of-composable-security-against-coherent-attacks-7-320.jpg)
![Security Analysis for CV QKD Protocols
Challenge: infinite dimensions
Finite-Key Analysis:
- Leverrier et al, Phys. Rev. A 81, 062343 (2010)
- Berta, FF, Scholz, arXiv:1107.5460 (2011)
Lifting proofs from collective to coherent (general) attacks:
Exponential de Finetti [Renner & Cirac, PRL 102, 110504 (2009)]
Problem: Bad bounds, feasible only in the asymptotic limit
Post-selection technique,
Recent: Leverrier et al., arXiv:1208.4920 (Talk on Monday)
Uncertainty Relation (direct) : This Talk!
Advantage:
one-sided device independent
no tomography
no additional measurements
FF, Continuous Variable QKD: Finite-Key Analysis against Coherent Attacks, Singapore, 14.09.2012 Seite 8](https://image.slidesharecdn.com/continuousvariablequantumkeydistributionfinite-keyanalysisofcomposablesecurityagainstcoherentattacks-121214215358-phpapp01/85/Continuous-variable-quantum-key-distribution-finite-key-analysis-of-composable-security-against-coherent-attacks-8-320.jpg)