Core idea driving and defining OO: using dynamic polymorphism to invert key architectural dependencies
- 1. How Can Objects Be Accessed? If objects can be accessed only through their public interface, how, then, is such access permitted? One object accesses another object by sending it a message. Such access, known as a message-send, is the only way one object should access another. What is involved in message sending? Message A message consists of the name of an operation and any required arguments. When one object sends a message to another object, the sender is requesting that the receiver of the message perform the named operation and (possibly) return some information. When the receiver receives the message, it performs the requested operation in any manner it knows. The request does not specify how an operation is to be performed. Such information is always hidden from the sender. The set of messages to which an object can respond is known as the behaviour of the object. Not all messages an object responds to, however, need to be part of its publicly accessible interface. An object can send private messages to itself to implement publicly accessible operations. … https://twitter.com/rebeccawb @rebeccawb
- 2. Polymorphism Limiting object access to a strictly defined interface such as the message-send allows another use of abstraction known as polymorphism. Polymorphism is the ability of two or more classes of object to respond to the same message, each in its own way. This means that an object does not need to know to whom it is sending a message. It just needs to know that many different kinds of objects have been defined to respond to that particular message. Objects of a variety of different, but similar, classes can recognize some of the same messages and respond in similar, appropriate ways. A response appropriate for one class of object might be thoroughly inappropriate for another class. The sender need not be concerned with the method that executes as a result of its message-send. Polymorphism allows us to recognize and exploit similarities between different classes of objects. When we recognize that several different kinds of object could respond to the same message, we recognize the distinction between the message name and a method. An object sends a message: if the receiver implements a method with the same signature, it will respond. Different responses are possible; therefore different methods make sense for instances of different classes, but the sender can simply send the message without being concerned with the class of the receiver. … https://twitter.com/rebeccawb @rebeccawb
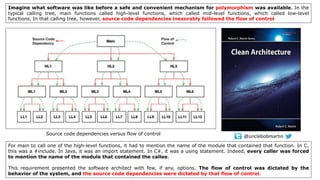
- 3. Imagine what software was like before a safe and convenient mechanism for polymorphism was available. In the typical calling tree, main functions called high-level functions, which called mid-level functions, which called low-level functions. In that calling tree, however, source code dependencies inexorably followed the flow of control Source code dependencies versus flow of control For main to call one of the high-level functions, it had to mention the name of the module that contained that function. In C, this was a #include. In Java, it was an import statement. In C#, it was a using statement. Indeed, every caller was forced to mention the name of the module that contained the callee. This requirement presented the software architect with few, if any, options. The flow of control was dictated by the behavior of the system, and the source code dependencies were dictated by that flow of control. @unclebobmartin
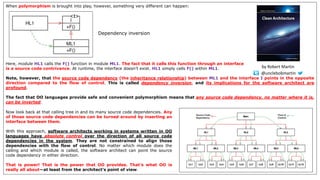
- 4. When polymorphism is brought into play, however, something very different can happen: Here, module HL1 calls the F() function in module ML1. The fact that it calls this function through an interface is a source code contrivance. At runtime, the interface doesn’t exist. HL1 simply calls F() within ML1. Note, however, that the source code dependency (the inheritance relationship) between ML1 and the interface I points in the opposite direction compared to the flow of control. This is called dependency inversion, and its implications for the software architect are profound. The fact that OO languages provide safe and convenient polymorphism means that any source code dependency, no matter where it is, can be inverted. Dependency inversion Now look back at that calling tree in and its many source code dependencies. Any of those source code dependencies can be turned around by inserting an interface between them. With this approach, software architects working in systems written in OO languages have absolute control over the direction of all source code dependencies in the system. They are not constrained to align those dependencies with the flow of control. No matter which module does the calling and which module is called, the software architect can point the source code dependency in either direction. That is power! That is the power that OO provides. That’s what OO is really all about—at least from the architect’s point of view. @unclebobmartin by Robert Martin
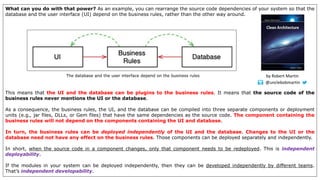
- 5. What can you do with that power? As an example, you can rearrange the source code dependencies of your system so that the database and the user interface (UI) depend on the business rules, rather than the other way around. This means that the UI and the database can be plugins to the business rules. It means that the source code of the business rules never mentions the UI or the database. As a consequence, the business rules, the UI, and the database can be compiled into three separate components or deployment units (e.g., jar files, DLLs, or Gem files) that have the same dependencies as the source code. The component containing the business rules will not depend on the components containing the UI and database. In turn, the business rules can be deployed independently of the UI and the database. Changes to the UI or the database need not have any effect on the business rules. Those components can be deployed separately and independently. In short, when the source code in a component changes, only that component needs to be redeployed. This is independent deployability. If the modules in your system can be deployed independently, then they can be developed independently by different teams. That’s independent developability. The database and the user interface depend on the business rules @unclebobmartin by Robert Martin