Crpto ppt
- 1. Submitted by- ASMITA PAL 0201CS141017 Submitted to- Asst. Prof. Deepti Tamrakar Dept. of Computer Science & Engg.
- 2. Overview Security Security Threats Security Goals What is Cryptography Basic Terms Encryption & Decryption Transmission Techniques Categories of Cryptography Comparison Conclusion
- 6. What is Cryptography? • Cryptography is the science of using mathematics to encrypt and decrypt data. • Cryptography enables you to store sensitive information or transmit it across insecure networks so that it cannot be read by anyone except the intended recipient.
- 7. Basic Terms • Plaintext: Data that can be read and understood without any special measures. • Encryption: The method of disguising plaintext in such a way as to hide its substance is called encryption. • Cipher text: Encrypting plaintext results in unreadable gibberish called cipher text. • Decryption: The process of reverting cipher text to its original plaintext is called decryption. • Key: some secret piece of information that customizes how the cipher text is.
- 8. Basic Terms cont. • Cryptanalysis: The art of breaking ciphers, i.e. retrieving the plaintext without knowing the proper key. • Cryptographers: People who do cryptography. • Cryptanalysts: Practitioners of cryptanalysis. • Cryptology: The branch of mathematics that studies the mathematical foundations of cryptographic methods.
- 10. Why Use Cryptography? • For “secret writing” • To establish a shared secret when other people (eavesdroppers) are listening. • TYPES Mainly classified into two types: 1. Symmetric key cryptography 2. 2. Asymmetric key cryptography
- 14. Transposition Cipher • In classical cryptography, a transposition cipher changes one character from the plaintext to another i.e. the order of the characters is changed.
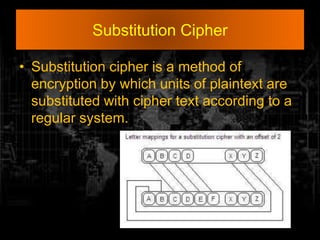
- 15. Substitution Cipher • Substitution cipher is a method of encryption by which units of plaintext are substituted with cipher text according to a regular system.
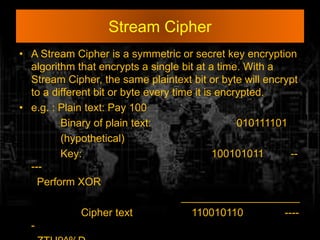
- 16. Stream Cipher • A Stream Cipher is a symmetric or secret key encryption algorithm that encrypts a single bit at a time. With a Stream Cipher, the same plaintext bit or byte will encrypt to a different bit or byte every time it is encrypted. • e.g. : Plain text: Pay 100 Binary of plain text: 010111101 (hypothetical) Key: 100101011 -- --- Perform XOR ____________________ Cipher text 110010110 ---- -
- 17. Block Cipher • Block cipher technique involves encryption of one block of text at a time. Decryption also takes one block of encrypted text at a time. Length of the block is usually 64 or 128 bits. • e.g. : Plain text: four and five Four and five Key Key Key wvfa ast wvfa --- cipher text
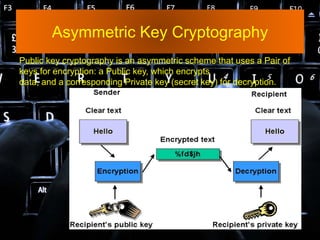
- 18. Asymmetric Key Cryptography Public key cryptography is an asymmetric scheme that uses a Pair of keys for encryption: a Public key, which encrypts data, and a corresponding Private key (secret key) for decryption.
- 20. Conclusion • Cryptography, being an art of encrypting and decrypting confidential information and private messages, should be implemented in the network security to prevent any leakage and threat. • It can be done by using any of these techniques discussed above for fortifying the personal data transmission as well as for secure transaction. • By using of encryption & decryption techniques a fair unit of Confidentiality, Authentication, Integrity, Access control and Availability of data is maintained.