CSW2017 jun li_car anomaly detection
- 2. 2 What this talk is about? Automotive intrusion detection Automotive cyber-security architecture
- 3. 3 From the highest viewpointJ
- 4. Outline • Quick recap of the status quo of car security research • Little automobile working principle • CAN bus anomaly detection
- 5. Performance Tuning by modifying firmware Immobilizer Cracking (Hitag, Keeloq) DARPA&UW OBD interface attack,etc. Karl et al. Remote attack via wireless OBD interface Telsa Qihoo360 BMW ConnectedDrive vuln Mbrace Jeep Uconnect Charlie&Chris GM Onstar Vuln,Sammy More to come ? Sure! Car hacking development
- 8. In automotive electronics, Electronic Control Unit (ECU) is a generic term for any secret system that controls one or more of the electrical system or subsystems in a transport vehicle Types of ECU include Electronic/engine Control Module (ECM), Powertrain Control Module (PCM), Transmission Control Module (TCM), Brake Control Module (BCM or EBCM), Central Control Module (CCM), Central Timing Module (CTM), General Electronic Module (GEM), Body Control Module (BCM), Suspension Control Module (SCM), control unit, or control module ECU (Electronic Control Unit)
- 9. Electronic Control Module Example 9
- 11. Non-hackable hackable 11 Throttle position sensor Drive-by-wire system
- 12. 12 Steering-by-wire system Universal joint Steer-by –wire (with mechanical fallback clutch)
- 13. Automotive Control System Architecture
- 14. Vehicle CAN BUS System
- 15. Vehicle Communication System OBDII MOST LIN CAN FlexRay Bluetooth Wifi SubGHz Infotainment System
- 16. ESP TCU ACC ESP(electronic stability program TCU(transmission control unit) ACC(adaptive cruise control) … CAN-C 网 Speedometer CAN-B Infotainment System Music Player INS(Inertial navigation system INS EMU EMU(engine management system) Seat Controller Vehicle Communication System example
- 19. 0 dominant 1 recessive 1 1 1 1 01 1 1 1 0 0 0 1 1 1 0 0 0 0 0 0 CAN Bus Access Arbitration
- 20. Packets injection Parameter spoofing CAN BUS Attack
- 21. Jeep Uconnect Vulnerability WiFifemotocellSprintInternet CAN Remote Attack Example
- 24. Automotive intrusion detection researches
- 25. Automotive intrusion detection researches Not considering Temporal feature
- 29. ① Real time requirements ② Hard to trace back to sender ③ High cost of false positive ④ … Difficulties of CAN bus defence
- 30. CAN Anomaly Detection McAfee&Intel
- 32. CAN security architecture Bluetooth WiFi Cellular V2X IDS
- 33. Experiment Car • Cellular Connection • Cloud Service • Bluetooth Key • Hybrid • Electronic Brake • Electric Power Steering • Electronic Throttle
- 34. Experiment car’s CAN network
- 35. The CAN database
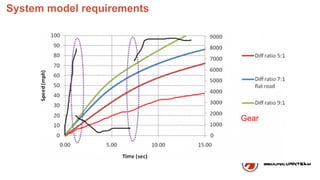
- 36. Why don’t we build a model Take the relation ship of rpm and speed , gear for example,we can create a model of the System‘s behavior
- 37. 汽车工作原理
- 38. Anomaly detection system Realtime data stream Cross Prediction Parameter extraction
- 40. Build the system model Data Collection Data preprocess Data analysis Feature Selection Model Training &Testing
- 41. Data Acquisition Parameter presence on different BUS Parameter Speed Engine RPM Acceleration Pedal Intake Pressure Brake Pedal Steering Wheel Gear BUS Instrument o o x x o o o Comfort o o x x o x x Power o o o o o x x ECM o o o o o x o ESC o o o x o o o
- 43. Data Analysis Can database is kept highly confidential
- 44. Data Preprocess
- 46. Normalization Must make sure the maximum and minimum value,don’t calculate from the training data
- 48. Sub-Sampling
- 49. Sub-SamplingTime_ ms RPM Speed MAP MAF AccPeda l Throttle 13897 3 0.287983 8 0.134259 2 0.059055 1 0.167567 5 0.697107 0 0.137795 2 13897 4 0.287312 5 0.134259 2 0.055118 1 0.167567 5 0.697107 0 0.137795 2 13897 5 0.287312 5 0.134259 2 0.051181 1 0.167567 5 0.697107 0 0.137795 2 13897 6 0.285970 0.134259 2 0.047244 0 0.167567 5 0.697107 0 0.137795 2 13897 7 0.285970 0.134259 0.051181 1 0.167567 5 0.697107 0 0.137795 2
- 50. Sub-Sampling
- 51. Model training
- 52. Model training
- 53. Results
- 54. Result
- 55. Model testing
- 56. Model testing
- 57. Acknowledgement Professor Shuicheng Yan Doctor Ming Lin Doctor Zhanyi Wang Doctor Lin Huang
- 58. Thank You! Q&A
- 59. Reference
- 60. 1. Karl Koscher, Alexei Czeskis, Experimental Security Analysis of a Modern Automobile, 2010 2. Stephen Checkoway,Damon McCoy,Brian Kantor, Comprehensive Experimental Analyses of Automotive Attack Surfaces,2011. 3. Charlie Miller,Chris Valasek,Adventures in Automotive Networks and Control Units,2013. 4. Charlie Miller,Chris Valasek,Remote Exploitation of an Unaltered Passenger Vehicle,2015 5. Dieter Spaar,Sicherheitslücken bei BMWs ConnectedDrive/ Beemer, Open Thyself! – Security vulnerabilities in BMW's ConnectedDrive,2015. 6. Iamthecarvalry.org , Five Star Automotive Cyber Safety Framework,2015. 7. Pierre Kleberger,Security Aspects of the In-Vehicle Network in the Connected Car,IEEE Intelligent Vehicles Symposium,2011 8. Marc Rogers,Kevin Mahaffey,How to Hack a Tesla Model S,DEF CON 23,2015 9. Charlie Miller Chris Valasek,Advanced CAN Injection Techniques for Vehicle Networks,BlackhatUSA,2016 10. Kyong-Tak Cho and Kang G. Shin, Fingerprinting Electronic Control Units for Vehicle Intrusion Detection, 2016
- 61. 11. Nobuyasu Kanekawa,X-by-Wire Systems,Hitachi Research Lab.2011 12. Paul Yih, Steer-by-Wire: Implication For Vehicle Handling and Safety,Stanford PHD Dissertation,2005 13. Luigi Coppolion,Dependability aspects of automotive x-by-wire technologies, 2008. 14. Jonas Zaddach,Andrei Costin,Embedded Devices Security and Firmware Reverse Engineering,Blackhat Workshop,2013. 15. Andrei costin,Jonas Zaddach,A large-Scale Analysis of the Security of Embedded Firmwares,EURECOM,2014. 16. Samy Kamkar,Drive It Like You hacked It,DEF CON23,2015 17. David A Brown, Geoffrey Cooper, Automotive Security Best Practices, White Paper by Intel & McAfee,2014. 18. OpenGarages, Car Hacker’s Handbook,openGarage.org,2014. 19. Henning Olsson, OptimumG,Vehicle Data Acquisition Using CAN,2010 20. Varun Chandola,Arindam Banerjee,Vipin Kumar,Anomaly Detection :A Survey,2009
- 62. 21. Park, Ming Kuang, Neural learning of driving environment prediction for vehicle power management, Joint Conf. on Neural Networks, 2008. 22. Taylor, P., Adamu-Fika, F., Anand, S., Dunoyer, A., Griffiths, N., and Popham, T. Road type classification through data mining,2012. 23. Michael Muter, Naim Asaj,Entropy-based anomaly detection for in-vehicle networks", IEEE Intelligent Vehicles Symposium (IV), 2011. 24. Ulf E. Larson, Dennis K. Nilsson,An Approach to Specification-based Attack Detection for In-Vehicle Networks, IEEE Intelligent Vehicles Symposium,2008. 25. Y. L. Murphey, Zhi Hang Chen, L. Kiliaris, Jungme ,I. Tang and T. P. Breckon, Automatic road environment classication, IEEE Trans. on Intelligent Transportation Systems, 2011. 26. Salima Omar, Asri Ngadi, Hamid H.Jebur, Machine Learning Techniques for Anomaly Detection: An Overview. 27. Perter Harrington,Machine Learning In Action,2013. 28. Jurgen Schmidhuber, Deep learning in neural networks: An overview, 2015. 29. Kaiserslautern,Comparison of Unsupervised Anomaly Detection Techniques, German Research Center for Artificial Intelligence, 2011
- 63. 30. Sepp Hochreiter, Jurgen Schmidhuber, Long short-term memory,Neural computation, 1997. 31. Michael Husken, Peter Stagge,Recurrent neural networks for time series classifcation, Neurocomputing, 2003. 32. Felix A Gers, Jurgen Schmidhuber, Fred Cummins, Learning to forget:Continual prediction with LSTM, Neural computation, 2000. 33. David E Rumelhart, Geo_rey E Hinton, and Ronald J Williams.,Learning internal representations by error propagation,1985. 34. Christopher M Bishop,Pattern recognition and machine learning, springer, 2006. 35. Simon Haykin and Neural Network. A comprehensive foundation. Neural Networks, 2004. 36. Eleazar Eskin,Andrew Arnold,Michael Prerau, A Geometric Framework for Unsupervised Anomaly Detection-Detecting Intrusions in Unlabeled Data tection-Detecting Intrusions in Unlabeled Data,2002. 37. Kingsly Leung, Christopher Leckie, Unsupervised Anomaly Detection in Network Intrusion Detection Using Clusters, 2005