Draft NISTIR 8202
- 1. Draft NISTIR 82021 Blockchain Technology Overview2 3 4 Dylan Yaga5 Peter Mell6 Nik Roby7 Karen Scarfone8 9 10 11 12 13 14 15 16
- 2. Draft NISTIR 820217 Blockchain Technology Overview18 19 20 21 Dylan Yaga22 Peter Mell23 Computer Security Division24 Information Technology Laboratory25 26 Nik Roby27 G2, Inc.28 Annapolis Junction, MD29 30 Karen Scarfone31 Scarfone Cybersecurity32 Clifton, VA33 34 35 36 37 38 January 201839 40 41 42 43 44 U.S. Department of Commerce45 Wilbur L. Ross, Jr., Secretary46 47 National Institute of Standards and Technology48 Walter Copan, NIST Director and Under Secretary of Commerce for Standards and Technology49
- 3. National Institute of Standards and Technology Internal Report 820250 59 pages (January 2018)51 Certain commercial entities, equipment, or materials may be identified in this document in order to describe an52 experimental procedure or concept adequately. Such identification is not intended to imply recommendation or53 endorsement by NIST, nor is it intended to imply that the entities, materials, or equipment are necessarily the best54 available for the purpose.55 There may be references in this publication to other publications currently under development by NIST in accordance56 with its assigned statutory responsibilities. The information in this publication, including concepts and methodologies,57 may be used by federal agencies even before the completion of such companion publications. Thus, until each58 publication is completed, current requirements, guidelines, and procedures, where they exist, remain operative. For59 planning and transition purposes, federal agencies may wish to closely follow the development of these new60 publications by NIST.61 Organizations are encouraged to review all draft publications during public comment periods and provide feedback to62 NIST. Many NIST cybersecurity publications, other than the ones noted above, are available at63 https://csrc.nist.gov/publications.64 65 66 67 68 69 Public comment period: January 24, 2018 through February 23, 2018 National Institute of Standards and Technology Attn: Computer Security Division, Information Technology Laboratory 100 Bureau Drive (Mail Stop 8930) Gaithersburg, MD 20899-8930 Email: nistir8202-comments@nist.gov All comments are subject to release under the Freedom of Information Act (FOIA).70 71
- 4. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW ii Reports on Computer Systems Technology72 The Information Technology Laboratory (ITL) at the National Institute of Standards and73 Technology (NIST) promotes the U.S. economy and public welfare by providing technical74 leadership for the Nation’s measurement and standards infrastructure. ITL develops tests, test75 methods, reference data, proof of concept implementations, and technical analyses to advance76 the development and productive use of information technology. ITL’s responsibilities include the77 development of management, administrative, technical, and physical standards and guidelines for78 the cost-effective security and privacy of other than national security-related information in79 federal information systems.80 81 Abstract82 Blockchains are immutable digital ledger systems implemented in a distributed fashion (i.e.,83 without a central repository) and usually without a central authority. At its most basic level, they84 enable a community of users to record transactions in a ledger public to that community such that85 no transaction can be changed once published. This document provides a high-level technical86 overview of blockchain technology. It discusses its application to electronic currency in depth,87 but also shows its broader applications. The purpose is to help readers understand how88 blockchains work, so that they can be appropriately and usefully applied to technology problems.89 Additionally, this document explores some specific blockchain applications and some examples90 of when a blockchain system should be considered for use.91 92 93 Keywords94 blockchain; consensus model; cryptocurrency; cryptographic hash; distributed ledger; mining95 96
- 5. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW iii Acknowledgments97 The authors wish to thank all contributors to this publication, and their colleagues who reviewed98 drafts of this report and contributed technical and editorial additions. This includes James Dray,99 Sandy Ressler, Rick Kuhn, Lee Badger, Eric Trapnell, and Mark Trapnell.100 101 Audience102 This publication is designed for readers with little or no knowledge of blockchain technology103 who wish to understand at a high level how it works and for what it can be used. It is not104 intended to be a technical guide; the discussion of the technology is abstracted to provide a105 conceptual understanding. Note that some figures and tables are purposefully simplified to fit the106 intended audience.107 108 Trademark Information109 All registered trademarks and trademarks belong to their respective organizations.110 111
- 6. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW iv Executive Summary112 Blockchains are immutable digital ledger systems implemented in a distributed fashion (i.e.,113 without a central repository) and usually without a central authority. At their most basic level,114 they enable a community of users to record transactions in a ledger that is public to that115 community, such that no transaction can be changed once published. In 2008, the blockchain116 idea was combined in an innovative way with several other technologies and computing concepts117 to enable the creation of modern cryptocurrencies: electronic money protected through118 cryptographic mechanisms instead of a central repository. The first such blockchain based119 approach was Bitcoin. These currency blockchain systems are novel in that they store value, not120 just information. The value is attached to a digital wallet—an electronic device (or software) that121 allows an individual to make electronic transactions. The wallets are used to sign transactions122 sent from one wallet to another, recording the transferred value publicly, allowing all participants123 of the network to independently verify the validity of the transactions. Each participant can keep124 a full record of all transactions, making the network resilient to attempts to alter that record (or125 forge transactions) later.126 Because there are countless news articles and videos describing the “magic” of the blockchain,127 this paper aims to describe the method behind the magic (i.e., how a blockchain system works).128 Arthur C. Clarke once wrote, “Any sufficiently advanced technology is indistinguishable from129 magic” [1]. Clarke’s statement is a perfect representation for the emerging use cases for130 blockchain technology. There is a high level of hype around the use of blockchains, yet the131 technology is not well understood. It is not magical; it will not solve all problems. As with all132 new technology, there is a tendency to want to apply it to every sector in every way imaginable.133 This document attempts bring a high-level understanding of the technology so that it can be134 applied effectively.135 As stated above, blockchain technology is the foundation of modern cryptocurrencies, so named136 because of blockchain’s heavy usage of cryptographic functions. Users utilize public and private137 keys to digitally sign and securely transact within the system. Users of the blockchain may solve138 puzzles using cryptographic hashing in hopes of being rewarded with a fixed amount of the139 cryptocurrency. However, blockchain technology is more broadly applicable than its application140 to cryptocurrencies. In this work, we try to show this broader applicability while still focusing to141 a large extent on the cryptocurrency use case (since that is the primary use case today).142 Organizations considering implementing blockchain technology need to understand important143 aspects of the technology. For example, what happens when an organization implements a144 blockchain system and then decides they need to make modifications to the data stored? When145 using a database, this can be accomplished through a simple query (or major changes can be146 made by updating the database schema or software). However, on a blockchain, it is much more147 difficult to change data or update the ‘database’ software. Organizations need to understand the148 extreme difficulty in changing anything that is already on the blockchain, and that changes to the149 blockchain software may cause forking of the blockchain. Another critical aspect of blockchain150 technology is how the participants agree that a transaction is valid. This is called “reaching151 consensus”, and there are many models for doing so, each with positives and negatives for a152 specific business case.153
- 7. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW v Some existing blockchain technologies focus on storing wealth, while others are a platform for154 smart contracts (software which is deployed on the blockchain itself, and executed by the155 computers running that blockchain). New blockchain technologies are being developed156 constantly to enable new use cases and to improve the efficiency of existing systems. Some157 blockchain implementations are permissionless, meaning anyone can read and write to them.158 Other implementations limit participation to specific people or companies, allow finer-grained159 controls, and may be managed by a central entity. Knowing these specifics allows an160 organization to understand what will be most applicable to its needs.161 Despite the many variations of blockchain systems and the rapid development of new162 technologies, most blockchains use some common core concepts. Each transaction involves one163 or more addresses and a recording of what happened, and it is digitally signed. Blockchains are164 comprised of blocks, each block being a group of transactions. All the transactions in a block are165 grouped together, along with a cryptographic hash of the previous block. Finally, a new hash is166 created for the current block’s header to be recorded within the block data itself as well as within167 the next block. Over time, each block is then chained to the previous block in the chain by168 adding the hash of the previous block to the header of the current block.169 Each technology used in a blockchain system takes existing, proven concepts and merges them170 together in a way that can address problems that were previously difficult. This document171 explores the fundamentals of how blockchain technologies work, how the participants in the172 network come to agree whether a transaction is valid, what happens when changes need to be173 made to an existing blockchain deployment, and how permissions work. Additionally, this174 document explores specific blockchain applications and examples of when to consider using a175 blockchain system.176 The use of blockchain technology is not a silver bullet, and there are issues that must be177 considered such as how to deal with malicious users, how controls are applied, and the178 limitations of any blockchain implementation. That said, blockchain technology is an important179 concept that will be a basis for many new solutions.180
- 8. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW vi Table of Contents181 Executive Summary ..................................................................................................... iv182 1 Introduction ............................................................................................................ 9183 1.1 Background and History.................................................................................. 9184 1.2 Purpose and Scope ...................................................................................... 10185 1.3 Notes on Terms ............................................................................................ 10186 1.4 Document Structure...................................................................................... 10187 2 Blockchain Architecture...................................................................................... 12188 2.1 Hashes.......................................................................................................... 12189 2.2 Transactions ................................................................................................. 13190 2.3 Asymmetric-Key Cryptography ..................................................................... 13191 2.4 Addresses and Address Derivation............................................................... 14192 2.4.1 Private Key Storage............................................................................ 14193 2.5 Ledgers......................................................................................................... 15194 2.6 Blocks ........................................................................................................... 19195 2.7 Chaining Blocks ............................................................................................ 23196 3 Blockchains in Operation.................................................................................... 23197 4 Consensus............................................................................................................ 26198 4.1 Proof of Work Consensus Model .................................................................. 26199 4.2 Proof of Stake Consensus Model ................................................................. 29200 4.3 Round Robin Consensus Model ................................................................... 30201 4.4 Ledger Conflicts and Resolutions ................................................................. 30202 5 Forking.................................................................................................................. 33203 5.1 Soft Forks ..................................................................................................... 33204 5.2 Hard Forks.................................................................................................... 33205 5.3 Cryptographic Changes and Forks ............................................................... 34206 6 Smart Contracts ................................................................................................... 35207 7 Blockchain Categorization .................................................................................. 36208 7.1 Permissioned ................................................................................................ 36209 7.1.1 Application Considerations for Permissioned Blockchains ................. 36210 7.1.2 Use Case Examples........................................................................... 37211 7.2 Permissionless.............................................................................................. 38212 7.2.1 Application Considerations for Permissionless Blockchains............... 38213
- 9. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW vii 7.2.2 Use Case Examples........................................................................... 38214 8 Blockchain Platforms .......................................................................................... 40215 8.1 Cryptocurrencies........................................................................................... 40216 8.1.1 Bitcoin (BTC) ...................................................................................... 40217 8.1.2 Bitcoin Cash (BCC) ............................................................................ 41218 8.1.3 Litecoin (LTC)..................................................................................... 41219 8.1.4 Ethereum (ETH) ................................................................................. 41220 8.1.5 Ethereum Classic (ETC)..................................................................... 41221 8.1.6 Dash (DASH)...................................................................................... 42222 8.1.7 Ripple (XRP) ...................................................................................... 42223 8.2 Hyperledger .................................................................................................. 42224 8.2.1 Hyperledger Fabric............................................................................. 42225 8.2.2 Hyperledger Sawtooth........................................................................ 43226 8.2.3 Hyperledger Iroha............................................................................... 43227 8.2.4 Hyperledger Burrow............................................................................ 43228 8.2.5 Hyperledger Indy ................................................................................ 43229 8.3 MultiChain..................................................................................................... 43230 9 Blockchain Limitations and Misconceptions..................................................... 44231 9.1 Blockchain Control........................................................................................ 44232 9.2 Malicious Users............................................................................................. 44233 9.3 No Trust........................................................................................................ 45234 9.4 Resource Usage ........................................................................................... 45235 9.5 Transfer of Burden of Credential Storage to Users....................................... 46236 9.6 Private/Public Key Infrastructure and Identity ............................................... 46237 10 Conclusions.......................................................................................................... 47238 239 List of Appendices240 Appendix A— Acronyms ............................................................................................ 48241 Appendix B— Glossary .............................................................................................. 50242 Appendix C— References .......................................................................................... 55243 244 List of Tables and Figures245 Table 1: Examples of Inputs and SHA-256 Digest Values ............................................ 12246
- 10. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW viii Table 2: Example Transaction....................................................................................... 13247 Figure 1 - A simple network maintaining a copy of a ledger across nodes.................... 16248 Figure 2 - Submitting a Transaction to a Node, waiting in the Pending Transaction List249 ............................................................................................................................... 17250 Figure 3 - Transaction 4 information transmitted from node to node............................. 18251 Figure 4 - Transaction 4 has been included into a block, nodes are transmitting the252 information; the final node has not yet received the latest information................... 19253 Figure 5: Example of a Merkle Tree .............................................................................. 21254 Figure 6: Blockchain with Merkle Tree .......................................................................... 22255 Figure 7: Generic Chain of Blocks................................................................................. 23256 Figure 8: Transaction Being Added to Unspent Transaction Pool................................. 24257 Figure 9: Finalized Block (Generalized) ........................................................................ 25258 Figure 10: Distributed Network in Conflict ..................................................................... 31259 Figure 11: Blockchains in Conflict ................................................................................. 31260 Figure 12: Chain B Adds the Next Block ....................................................................... 32261 Table 3: Impact of Quantum Computing on Common Cryptographic Algorithms.......... 34262 263
- 11. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 9 1 Introduction264 Blockchains are immutable digital ledger systems implemented in a distributed fashion (i.e.,265 without a central repository) and usually without a central authority. At their most basic level,266 they enable a community of users to record transactions in a ledger that is public to that267 community, such that no transaction can be changed once published. This technology became268 widely known starting in 2008 when it was applied to enable the emergence of electronic269 currencies where digital transfers of money take place in distributed systems. It has enabled the270 success of e-commerce systems such as Bitcoin, Ethereum, Ripple, and Litecoin. Because of this,271 blockchains are often viewed as bound to Bitcoin or possibly e-currency solutions in general.272 However, the technology is more broadly useful and is available for a variety of applications.273 The numerous components of blockchain technology along with its reliance on cryptographic274 primitives and distributed systems can make it challenging to understand. However, each275 component can be described simply and used as a building block to understand the larger276 complex system. We provide an informal concise description of blockchain technology:277 Blockchains are distributed digital ledgers of cryptographically signed transactions that are278 grouped into blocks. Each block is cryptographically linked to the previous one after279 validation and undergoing a consensus decision. As new blocks are added, older blocks280 become more difficult to modify. New blocks are replicated across all copies of the ledger281 within the network, and any conflicts are resolved automatically using established rules.282 1.1 Background and History283 The core ideas behind blockchain technology emerged in 1991 when a signed chain of284 information was used as an electronic ledger for digitally signing documents in a way that could285 easily show none of the signed documents in the collection had been changed [2]. It was first286 applied to digital cash in 2008 in the initial paper describing the Bitcoin electronic cash solution,287 Bitcoin: A Peer to Peer Electronic Cash System [3], which was published pseudonymously by288 Satoshi Nakamoto. The actual author(s) and owner of the first Bitcoins remain a mystery. Since289 then, blockchain technology has become tightly linked to Bitcoin and is often assumed to be used290 for monetary transactions (although it is not restricted to simple fund transfers). Nakamoto’s291 paper contained the blueprint that most modern digital cash schemes follow, with many292 variations. Bitcoin is in fact the first of many applications or use cases for a blockchain.293 Many electronic cash schemes existed prior to Bitcoin, but none of them achieved widespread294 use. By adopting blockchain technology, Bitcoin achieved compelling capabilities that promoted295 its use. The use of a blockchain enabled Bitcoin to be implemented in a distributed fashion so296 that no single user controlled the currency and no single point of failure existed. Its primary297 benefit was to enable direct electronic financial transactions between users without the need for a298 third party. It also enabled the issuance of new currency in a fair fashion to those users299 (sometimes called miners or minters) maintaining the blockchain that, among other factors,300 enabled lower transaction costs for using the system. The payment of the mining nodes enabled301 distributed administration of the system without the need to organize those maintaining the302 system. By using a distributed blockchain and consensus-based maintenance, a self-policing303 mechanism was created that ensured that only valid transactions were added to the blockchain.304
- 12. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 10 Also, the blockchain enabled users to be pseudonymous, meaning that users are anonymous but305 their accounts are not – all their transactions are publicly observable. This has effectively306 enabled Bitcoin to offer pseudo-anonymity because accounts can be created without any307 identification or authorization process. Finally, the distributed maintenance of the blockchain308 created a system with complete transparency, which promoted trust in its use. Since all309 transactions are transparent within the system, and must be verified before being included, it310 greatly reduces the ability for users to double spend (sending the same digital asset to more than311 one user) their digital assets. One of the most valuable aspects of applications built on312 blockchains is that they can enable business to be conducted with untrusted and unknown users.313 1.2 Purpose and Scope314 This document provides a high-level technical overview of blockchain technology. It discusses315 its application for electronic currency in depth, but also shows its broader uses. It looks at316 different categories of approaches since many blockchain platforms exist, each subtly different.317 This document is intended to help readers to understand the technologies which comprise318 blockchain systems and to understand how blockchains can be appropriately and usefully applied319 to technology problems.320 1.3 Notes on Terms321 The terminology for blockchain technology varies from one implementation to the next – in322 order to talk about the technology as a whole, generic terms will be used. Throughout this323 document the terms user and node are used to describe aspects of blockchain components. For324 the purposes of this document, a user is a generic term to describe any person, organization,325 entity, business, government, etc. which is utilizing the blockchain system. A node is an326 individual system within a blockchain system, and can further be refined to full node (stores the327 entire blockchain), mining node (full node that also maintains the blockchain by publishing new328 blocks), and lightweight node (node that does not maintain a history of the entire blockchain).329 1.4 Document Structure330 The rest of this document consists of the following sections and appendices:331 • Section 2 defines the high-level components of a blockchain system architecture,332 including hashes, transactions, ledgers, blocks, and blockchains.333 • Section 3 discusses how a blockchain is expanded through the addition of new blocks334 representing sets of transactions.335 • Section 4 examines the need for consensus models to resolve conflicts among blockchain336 mining nodes.337 • Section 5 introduces the concept of forking.338 • Section 6 defines and discusses smart contracts.339 • Section 7 looks at blockchain permission models, discusses their application340 considerations, and provides use case examples for each model.341 • Section 8 provides several examples of blockchain platforms in use today to indicate the342 variations from one platform to another.343 • Section 9 highlights some of the limitations of blockchain technology.344
- 13. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 11 • Section 10 gives a short conclusion for the document.345 • Appendix A contains a glossary for selected terms defined in the document.346 • Appendix B provides a list of acronyms and abbreviations used in the document.347 • Appendix C defines the references used throughout the document.348 349
- 14. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 12 2 Blockchain Architecture350 Blockchain systems can seem complex; however, they can be easily understood by examining351 each component technology individually. At a high level, blockchains utilize well-known352 computer science mechanisms (linked lists, distributed networking) as well as cryptographic353 primitives (hashing, digital signatures, public/private keys) mixed with financial concepts (such354 as ledgers).355 2.1 Hashes356 An important component of the blockchain technology is the use of cryptographic hash functions357 for many operations, such as hashing the content of a block. Hashing is a method of calculating a358 relatively unique fixed-size output (called a message digest, or just digest) for an input of nearly359 any size (e.g., a file, some text, or an image). Even the smallest change of input (e.g., a single bit)360 will result in a completely different output digest. Table 1 shows simple examples of this. Hash361 algorithms are designed to be one-way (known as being preimage resistant): it is computationally362 infeasible to find any input that maps to any pre-specified output. If a particular output is desired,363 many inputs must be tried by passing them through the hash function until an input is found that364 produces the desired result. Hash algorithms are also designed to be collision resistant (known as365 second preimage resistant): it is computationally infeasible to find two or more inputs that366 produce the same output.367 A hashing algorithm used in many blockchain technologies is the Secure Hash Algorithm (SHA)368 with an output size of 256 bits (SHA-256). Many computers support this algorithm in hardware,369 making it fast to compute. This algorithm has an output of 32 (8-bit) characters (shown below, in370 Table 1, as a 64-character hexadecimal string), meaning that there are 2256 ≈ 1077 , or371 115,792,089,237,316,195,423,570,985,008,687,907,853,269,984,665,640,564,039,457,584,007,913,129,639,936372 possible digest values. The algorithm for SHA-256, as well as others, is specified in Federal373 Information Processing Standard (FIPS) 180-4 [4]. The NIST Secure Hashing website [5]374 contains FIPS specifications for all NIST-approved hashing algorithms.375 Table 1: Examples of Inputs and SHA-256 Digest Values376 Input Text SHA-256 Digest Value 1 0x6b86b273ff34fce19d6b804eff5a3f5747ada4eaa22f1d49c01e52ddb7875b4b 2 0xd4735e3a265e16eee03f59718b9b5d03019c07d8b6c51f90da3a666eec13ab35 Hello, World! 0xdffd6021bb2bd5b0af676290809ec3a53191dd81c7f70a4b28688a362182986f 377 Since there is an extremely large number of possible input values and a finite number of possible378 output digest values, it is possible to have a collision where hash(x) = hash(y) (i.e., the hash of379 two different inputs produces the same digest). However, it is highly unlikely for any such input380 x and y that produce the same digest to both be valid in the context of the blockchain system (in381 this case, both being valid blockchain transactions) as well as be computed reasonably close to382 each other in time. The hashing algorithm used (SHA-256) is said to be collision resistant, since383 to find a collision in SHA-256, one would have to execute the algorithm, on average, about 2128 384
- 15. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 13 times. Blockchain technologies take a list of transactions and create a hash “fingerprint” (the385 digest is the fingerprint) for the list. Anyone with the same list of transactions can generate the386 exact same fingerprint. If a single value in a transaction within the list changes, the digest for that387 block changes, making it easy to discover even minor one bit changes.388 2.2 Transactions389 A transaction is a recording of a transfer of assets (digital currency, units of inventory, etc.)390 between parties. An analog to this would be a record in a checking account for each time money391 was deposited or withdrawn. Table 2 shows a notional example of a transaction. Each block in a392 blockchain contains multiple transactions. A single transaction typically requires at least the393 following information fields, but can contain more:394 • Amount – The total amount of the digital asset to transfer.395 • Inputs – A list of the digital assets to be transferred (their total value equals the amount).396 Note that each digital asset is uniquely identified and may have different values from397 other assets. However, assets cannot be added or removed from existing digital assets.398 Instead, digital assets can be split into multiple new digital assets (each with lesser value)399 or combined to form fewer new digital assets (each with a correspondingly greater value).400 • Outputs – The accounts that will be the recipients of the digital assets. Each output401 specifies the value to be transferred to the new owner(s), the identity of the new owner(s),402 and a set of conditions the new owners must meet to receive that value. If the digital403 assets provided are more than required, the extra funds are returned to the sender (this is a404 mechanism to “make change”).405 • Transaction ID/Hash – A unique identifier for each transaction. Some blockchains use406 an ID, and others take a hash of the specific transaction as a unique identifier.407 Table 2: Example Transaction408 Input Output Amount Total Transaction ID: 0xa1b2c3 Account A Account B 0.0321 Account C 2.5000 2.5321 409 Determining the validity of a transaction is important. Just because someone claims a transaction410 took place does not mean it really happened. Transactions are signed and can be verified with411 public/private key pairs at any time.412 2.3 Asymmetric-Key Cryptography413 A fundamental technology utilized by blockchain technologies is asymmetric-key cryptography1 414 (also referred to as public/private key cryptography). Asymmetric-key cryptography uses a pair415 1 FIPS Publication 186-4, Digital Signature Standard [6] specifies a common algorithm for digital signing used in blockchain technologies: Elliptic Curve Digital Signature Algorithm (ECDSA).
- 16. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 14 of keys: a public key and a private key that are mathematically related to each other. The public416 key may be made public without reducing the security of the process, but the private key must417 remain secret if the data is to retain its cryptographic protection. Even though there is a418 relationship between the two keys, the private key cannot efficiently be determined based on419 knowledge of the public key.420 421 Asymmetric key cryptography uses the different keys of the key pair for specific functions,422 dependent on which service is to be provided. For example, when digitally signing data, the423 cryptographic algorithm utilizes the private key to sign. The signature can then be verified using424 the corresponding public key.425 Asymmetric-Key Cryptography Utilization in Blockchain Systems:426 • Private keys are used to digitally sign transactions.427 • Public keys are used to derive addresses, allowing for a one-to-many approach for428 pseudonymity (one public key pair can yield multiple addresses; in some cases, multiple429 public key pairs are utilized to create multiple addresses).430 • Public keys are used to verify signatures generated with private keys.431 • Asymmetric-key cryptography provides the ability to verify that the user transferring432 value to another user is in possession of the private key capable of signing the value.433 2.4 Addresses and Address Derivation434 A user’s address is a short, alphanumeric string derived from the user’s public key using a hash435 function, along with some additional data (used to detect errors). Addresses are used to send and436 receive digital assets. Most blockchain systems make use of addresses as the “to” and “from”437 endpoints in a transaction. Addresses are shorter than the public keys and are not secret. To438 generate an address, it typically means taking a public key, hashing it, and converting the hash to439 text:440 public key hash function address441 Users can generate as many private/public key pairs, and therefore addresses as desired, allowing442 for a varying degree of pseudo-anonymity. Addresses act as the public-facing “identity” on a443 blockchain for a user, and oftentimes an address will be converted into a QR code for easier use.444 When a blockchain distributes digital assets, it does so by assigning them to an address. To spend445 that digital asset, a user must prove possession of the address’s corresponding private key. By446 digitally signing a transaction with the private key, the transaction can be verified with the public447 key.448 2.4.1 Private Key Storage449 Most users of a blockchain system do not record their private keys manually, rather, software450 commonly called a wallet securely stores them. The wallet can store private keys, public keys,451 and associated addresses. The wallet software can also calculate the total number of assets a user452 may have.453
- 17. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 15 A private key is usually generated using a secure random function, meaning that reconstructing it454 is difficult, if not impossible. If a user loses a private key, then any asset associated with that key455 is lost. If a private key is stolen, the attacker will have full access to all assets controlled by that456 private key. The security of private keys is so important that many users use special secure457 hardware to store it.458 Private key storage is an extremely important aspect of blockchain technology. When it is459 reported in the news that “Bitcoin was stolen from…”, it almost certainly means the private keys460 were found and used to sign a transaction sending the money to a new account, not that the461 system was compromised. Note that because blockchain data cannot generally be changed, once462 a criminal steals a private key and publicly moves the associated funds to another account, it463 cannot be undone.464 2.5 Ledgers465 A ledger is a collection of transactions. Throughout history, pen and paper ledgers have been466 used to keep track of the exchange of goods and services. More recently, ledgers have been467 stored digitally, often in large databases owned and operated solely by centralized “trusted” third468 parties on behalf of a community of users (i.e., the third party is the owner of the ledger).469 Centralized ledgers may have shortcomings, such as:470 • They may be lost or destroyed; a user must trust that the owner is properly backing up the471 system.472 • The transactions may not be valid; a user must trust that the owner is validating each473 received transaction.474 • The transaction list may not be complete; a user must trust that the owner is including all475 valid transactions that have been received.476 • The transaction data may have been altered; a user must trust that the owner is not477 altering past transactions.478 Of course, it is in the best interest of any centralized ledger to backup data, validate transactions,479 include all valid transactions, and not to alter history.480 A ledger implemented using a blockchain can mitigate these issues through the use of a481 distributed consensus mechanism. One aspect of this is that the blockchain ledger will be copied482 and distributed amongst every node within the system. Figure 1 depicts a simple network with483 four nodes, where each has a copy of a ledger of transactions.484
- 18. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 16 485 Figure 1 - A simple network maintaining a copy of a ledger across nodes486 New transactions are submitted to a node (as seen in Figure 2), which will then alert the rest of487 the network that a new transaction has arrived (as seen in Figure 3).488
- 19. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 17 489 Figure 2 - Submitting a Transaction to a Node, waiting in the Pending Transaction List490 At this point, it is a pending transaction, and not included in a block within the ledger.491
- 20. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 18 492 Figure 3 - Transaction 4 information transmitted from node to node493 Eventually, a node will include this new transaction within a block and complete the system’s494 required consensus method (explained later). This new block will be distributed across the495 system and all ledgers will be updated to include the new transaction (as seen in Figure 4).496
- 21. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 19 497 Figure 4 - Transaction 4 has been included into a block, nodes are transmitting the information; the final498 node has not yet received the latest information499 Whenever new users join the system, they receive a full copy of the blockchain, making loss or500 destruction of the ledger difficult. All transactions are stored in blocks within the blockchain501 (transactions discussed in Section 2.2).502 503 2.6 Blocks504 Users may submit candidate transactions to the ledger by sending these transactions to some of505 the nodes participating in the blockchain. Submitted transactions are propagated to the other506 nodes in the network (but this by itself does not include the transaction in the blockchain). The507 distributed transactions then wait in a queue, or transaction pool, until they are added to the508 blockchain by a mining node.509 Mining nodes are the subset of nodes that maintain the blockchain by publishing new blocks.510 Transaction are added to the blockchain when a mining node publishes a block. A block contains511 a set of validated transactions. ‘Validity’ is ensured by checking that the providers of funds in512 each transaction (listed in the transaction’s ‘input’ values) have each cryptographically signed513 the transaction. This verifies that the providers of funds for a transaction had access to the private514 key which could sign over the available funds. The other mining nodes will check the validity of515 all transactions in a published block and will not accept a block if it contains any invalid516 transactions.517
- 22. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 20 After creation, each block is hashed thereby creating a digest that represents the block. The518 change of even a single bit in the block would completely change the hash value. The block’s519 hash digest is used to help protect the block from change since all nodes will have a copy of the520 block’s hash and can then check to make sure that the block has not been changed.521 The actual construction of a block is slightly more complicated. The data fields comprising a522 block typically consist of the following:523 • The block number, also known as block height524 • The current block hash value525 • The previous block hash value526 • The Merkle tree root hash (defined below)527 • A timestamp528 • The size of the block529 • The nonce value, which is a number manipulated by the mining node to solve the hash530 puzzle that gives them the right to publish the block (see Section 4.1 for details)531 • A list of transactions included within the block532 533 Rather than storing the hash of every transaction within the header of a block, a data structure534 known as a Merkle tree is utilized. A Merkle tree combines the hash values of data together until535 there is a singular root (a Merkle tree root hash). The root is an efficient mechanism used to536 summarize the transactions in a block and verify the presence of a transaction within a block.537 This structure ensures that the data sent in a distributed network is valid, since any alteration to538 the underlying data would be detected and can be discarded. Figure 5 shows an example of a539 Merkle tree:540 • The bottom row represents the data to be summarized, in the case of blockchains this is541 the transaction data.542 • The second to bottom row shows that data being hashed.543 • The hashed data from the second row is then combined and then hashed on the third to544 bottom row.545 • Finally, the top row shows the Root hash, which combines and hashes H4 and H5. The546 root hash is a hash of all previous combinations and hashes made.547
- 23. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 21 548 Figure 5: Example of a Merkle Tree549 Figure 6 shows the relationship between a Merkle tree and a block. The bottom row of the tree550 contains blockchain transactions Tx0 through Tx3. The Merkle root is stored within the block551 header.552 The entire block header is hashed; the block header hash value is stored within the block itself, as553 well as within in the next block, and this helps provide the immutability of transactions since the554 Merkle root hash will not match if any change is made to the transactions.555
- 24. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 22 556 Figure 6: Blockchain with Merkle Tree557
- 25. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 23 2.7 Chaining Blocks558 Blocks are chained together through each block containing the hash of the previous block’s559 header, thus forming the blockchain. If a previously published block were changed, it would560 have a different hash. This in turn would cause all subsequent blocks to also have different561 hashes since they include the hash of the previous block. This makes it possible to easily detect562 and reject any changes to previously published blocks. Figure 7 shows a generic chain of blocks.563 564 Figure 7: Generic Chain of Blocks565 3 Blockchains in Operation566 In the previous section, we provided a static view of the components of a generic blockchain. In567 this section, we discuss how a blockchain is expanded through the addition of new blocks568 representing sets of transactions. We discuss here a permissionless blockchain that utilizes the569 proof of work consensus method (the most popular method to date and the one used by Bitcoin570 and its derivatives). Information on other consensus methods is discussed in Section 4 below.571 Blockchains are maintained through the consensus of a set of computers running blockchain572 software, known as mining nodes. There is no central authority determining which node573 publishes the next block on the blockchain. Each node maintains a copy of the blockchain and574 may propose a new block to the other mining nodes. Invalid blocks will be detected and rejected575 because it is difficult to compute a valid block, but computationally easy to verify one. Mining is576 an intentionally resource-intensive task, taking large amounts of processing power, memory, or577 both, depending on the specific blockchain application. The consensus protocol that determines578 which new block gets added to the blockchain is discussed in Section 4.579 As mentioned earlier, any computer running blockchain software is considered a node of that580 blockchain. There are generally two types of nodes: full nodes and lightweight nodes. The job of581 a full node is to store the blockchain data, pass along the data to other nodes, and ensure newly582 added blocks are valid. Validation entails ensuring that the format of the block is correct, all583 hashes in the new block were computed correctly, the new block contains the hash of the584 previous block, and each transaction in the block is valid and signed by the appropriate parties.585 Full nodes may also act as mining nodes (i.e., generating new blocks). Lightweight nodes do not586 need to store full copies of the blockchain and often pass their data on to full nodes to be587
- 26. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 24 processed. Lightweight nodes are generally found on smartphones and Internet of Things (IoT)588 devices—devices with limited computational and/or storage capability. Any node may propose589 new transactions, and these proposed transactions are propagated between nodes until they are590 eventually added to a block.591 Proposed transactions within a blockchain system are stored on mining nodes within an unspent592 transaction pool—waiting to be included within a block as depicted in Figure 8.593 594 Figure 8: Transaction Being Added to Unspent Transaction Pool595 When mining nodes put together a new candidate block, they include a set of unspent596 transactions. They may take a combination of older transactions that have been waiting for some597 time and newer transactions that offer a higher payment (in the form of a transaction fee paid by598 the user who submitted the transaction). The mining node checks that each transaction is itself599 valid since the other nodes would reject the block if it included invalid transactions. At this point,600 the mining node fills out all information required by the block structure discussed in Section 2.6,601 except the nonce.602 Some blockchain systems require a form of sacrifice to create the next block – such as expending603 time and effort, or staking for the privilege. For systems, which require time and effort, the604 mining node calculates many random nonce values to attempt to solve a computationally605 difficult puzzle. The winning mining node gets the right to publish the next block (see Section606 4.1). Usually, mining nodes try many nonce values before solving a puzzle. Once a puzzle is607 solved with a particular nonce, the node creates a hash of the block’s data and stores it within the608
- 27. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 25 block itself. Figure 9 depicts the high-level structure of the constructed block. The block is then609 sent out to other nodes for verification; if everything is verified, the nodes accept it as the latest610 block and continue to pass it along. Section 4.4 discusses what happens if multiple mining nodes611 solve the challenge in the same timeframe, creating multiple competing ‘next’ blocks.612 613 Figure 9: Finalized Block (Generalized)614 615
- 28. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 26 4 Consensus616 In our generic presentation of a blockchain from the previous section, many mining nodes are617 competing at the same time to solve a puzzle to gain the right of publishing the next block (and if618 applicable, a financial award). They are generally mutually distrusting users that may only know619 each other by their public addresses. Each user may be motivated by a desire for financial gain,620 not the well-being of the other mining nodes or even the network as a whole. In such a situation,621 why would a user propagate a block solved by another user? Also, who resolves conflicts when622 multiple mining nodes solve a block at approximately the same time? To make this work,623 blockchains use a variety of consensus models that enable a group of mutually distrusting users624 to work together.625 Note that when a user joins a blockchain system, the user agrees to the initial state of the system.626 This is recorded in the only pre-configured block, the genesis block. Every blockchain has a627 published genesis block and every block must be added to the blockchain after it, based on an628 agreed-upon consensus method. Regardless of the method, however, each block must be valid629 and thus can be validated independently by each user in the blockchain network. By combining630 the initial state and the ability to verify every block since then, users can agree on the current631 state of the blockchain. Note that if there were ever two valid chains presented to a user, the632 default mechanism, in most blockchain systems, is that the longer chain is ‘more’ valid and633 should be adopted (this happens occasionally and will be discussed later).634 The following properties are then in place:635 • The initial state of the system is agreed upon.636 • Users agree to the consensus method by which blocks are added to the system.637 • Every block is linked to the previous block with a hash (except for the first ‘genesis’638 block, which has no previous block, and usually has a hash value of all 0’s for the639 previous block).640 • Users can verify every block.641 In practice, node software handles all the details. Key to the blockchain approach is that there is642 no need to have a trusted third party to give the state of the system—every user within the system643 can verify the system’s integrity. To add a new block to the blockchain, all participating nodes644 must come to a common agreement over time, however, so some temporary disagreement is645 permitted. The method of agreement (or consensus) must work even in the presence of possibly646 malicious users attempting to disrupt or take over the blockchain. This section discusses several647 major consensus models, as well as conflict resolution.648 4.1 Proof of Work Consensus Model649 In the proof of work 2 model, a user gets the right to publish the next block by solving a650 computationally intensive puzzle. The solution to this puzzle is the “proof” they have performed651 2 Proof of work is often abbreviated PoW.
- 29. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 27 work. The puzzle is designed such that solving the puzzle is difficult, but checking that a solution652 is valid is easy. This enables all other mining nodes to easily validate any proposed next blocks,653 and any proposed block that did not satisfy the puzzle would be rejected. A common puzzle654 method is to require that the hash of the block be less than a certain value. Mining nodes then655 make many small changes to the block (the nonce) trying to find a block hash that meets the656 requirement. For each attempt, the mining node must compute the hash for the entire block657 header, which is a computationally intensive process. The required value may be modified over658 time to adjust the difficulty to influence how often blocks are being published. For example,659 Bitcoin, which uses the proof of work model, adjusts the puzzle difficulty every two weeks to660 influence the block publication rate to be around once every ten minutes.661 An important aspect of this model is that the past work put into a puzzle does not influence one’s662 likelihood of solving future puzzles. Hashing a candidate block one thousand or one million663 times (with different nonce values) only increases the likelihood of solving the current puzzle (as664 the nonce input space is being reduced with each hash calculation), it does not increase the user’s665 likelihood of solving any future puzzles, and therefore each puzzle to solve for a block is666 independent and requires the same amount of work. This means that when a user receives a667 completed block from another user, they are incentivized to include the new block because they668 know the other mining nodes will include it and start building off it. If they refuse to accept the669 new block, they will be building off a shorter chain of blocks and (as mentioned previously) by670 default, the longest valid chain is adopted.671 As an example, consider a puzzle where, using the SHA-256 algorithm, a computer must find a672 hash value meeting the following target criteria:673 SHA256(“blockchain” + Nonce) = Hash Value starting with “000000”674 In this example, the text string “blockchain” is appended with a nonce value and then the675 hash value is calculated. The nonce values used will be numeric values only. This is a relatively676 easy puzzle to solve and some sample output follows:677 SHA256("blockchain0") =678 0xbd4824d8ee63fc82392a6441444166d22ed84eaa6dab11d4923075975acab938679 (not solved)680 SHA256("blockchain1") =681 0xdb0b9c1cb5e9c680dfff7482f1a8efad0e786f41b6b89a758fb26d9e223e0a10682 (not solved)683 …684 SHA256("blockchain10730895") =685 0x000000ca1415e0bec568f6f605fcc83d18cac7a4e6c219a957c10c6879d67587686 (solved)687 To solve this puzzle, it took 10,730,896 guesses (completed in 54 seconds on relatively old688 hardware, starting at 0 and testing one value at a time). However, each additional “leading zero”689 value increases the difficulty. By increasing the target by one additional leading zero690 (“0000000”), the same hardware took 934,224,175 guesses to solve the puzzle (completed in 1691 hour, 18 minutes, 12 seconds):692
- 30. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 28 SHA256("blockchain934224174") =693 0x0000000e2ae7e4240df80692b7e586ea7a977eacbd031819d0e603257edb3a81694 There is no shortcut to this process; mining nodes must expend computation effort, time, and695 resources to find the correct nonce value for the target.696 Once a user has performed this work, they send their block with a valid nonce to the other nodes697 in the network. The recipient nodes verify that this work was done properly, add the block to698 their copy of the blockchain, and resend the block to their peer nodes. In this manner, the new699 block gets quickly distributed throughout the network of participating nodes. Verification of the700 nonce is easy since only a single hash needs to be done to check to see if it solves the puzzle.701 The proof of work consensus model is designed for the case where there is little to no trust702 amongst users of the system. It ensures mining nodes cannot game the system3 by always being703 able to solve the puzzles and thereby control the blockchain and the transactions added to it.704 However, a major pitfall of the proof of work consensus model is its excessive use of energy in705 solving the puzzles. This is not trivial; for example, currently the Bitcoin blockchain uses more706 electricity than the entire country of Ireland, and it has been speculated that it will consume as707 much electricity as the entire country of Denmark by 2020 [7][8][9]. Software and hardware708 continually improve, with the result that puzzles can be solved more efficiently, but blockchain709 networks are growing, and the puzzle targets get harder as more mining nodes participate.710 Due to the increasing difficulty of the proof of work puzzles, it is becoming harder for any one711 computer to solve a puzzle. Therefore, mining nodes have organized themselves into “pools” or712 “collectives” whereby they collectively solve puzzles. This is because it is possible to distribute713 the work between two or more nodes across a collective to share the workload and rewards.714 Splitting the example program into quarters, each node can take an equal amount of the nonce715 value range to test:716 • Node 1: check nonce 0000000000 to 0536870911717 • Node 2: check nonce 0536870912 to 1073741823718 • Node 3: check nonce 1073741824 to 1610612735719 • Node 4: check nonce 1610612736 to 2147483647720 The following result was the first to be found to solve the puzzle:721 SHA256("blockchain1700876653") =722 0x00000003ba55d20c9cbd1b6fb34dd81c3553360ed918d07acf16dc9e75d7c7f1723 This is a completely new nonce, but one that solved the puzzle. It took 90,263,918 guesses724 (completed in 10 minutes, 14 seconds). Dividing up the work amongst many more machines725 yields much better results, as well as more consistent rewards in a proof of work model.726 3 Use the rules and procedures meant to protect the system to actually manipulate the system for a desired result.
- 31. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 29 4.2 Proof of Stake Consensus Model727 The proof of stake model is based on the idea that the more stake4 a user has in the system, the728 more likely it will want the system to succeed, and the less likely it will want to subvert it. Proof729 of stake blockchain systems use the amount of stake a user has as a determining factor for new730 block creation. The methods for how the blockchain system uses the stakes can vary – from731 random selection of staked users, to multi-round voting, to a coin aging system. Regardless of732 the exact approach, users with more stake are more likely to produce new blocks.733 With this consensus model, there is no need to perform resource intensive computations (time,734 electricity, processing power) as found in proof of work. Since this consensus method utilizes735 less resources, some blockchains have decided to forego a reward for new block creation; these736 systems are designed so that all the cryptocurrency is already distributed among users rather than737 new coins being generated at a constant pace.738 Within a proof of stake blockchain system, where the choice of block creator is a random choice739 (sometimes referred to as Chain-based proof of stake), the blockchain system will look at all740 users with stake and choose amongst them based on their stake to overall system stake ratio. So,741 if a user had 42% of the stake they would be chosen 42% of the time; those with 1% would be742 chosen 1% of the time.743 When the choice of block creator is a multi-round voting system (sometime referred to as744 Byzantine Fault Tolerance proof of stake [10]) there is added complexity. The blockchain system745 will select several staked users to create proposed blocks. The system will then ask all staked746 users to vote for the next block. After several rounds of this voting, a new block is decided upon.747 This method allows all staked users to have a voice in the block selection process for every new748 block.749 Finally, there is a method of proof of stake which allows users to create blocks by “spending”750 aged cryptocurrency (sometimes referred to as “Coin age” proof of stake). The user’s staked751 cryptocurrency has an additional “age” property, and after a certain amount of time (such as 30752 days) the staked cryptocurrency can be “spent” and allow the user to create a new block on the753 blockchain. The “spent” cryptocurrency then has its “age” reset to 0, and it cannot be used again754 until after the requisite time has passed. This method allows for users with more stake to create755 more blocks, but to not dominate the system – since they have a cooldown timer attached to756 every cryptocurrency spent creating blocks.757 Under proof of stake systems, the “rich” can more easily stake more of the digital assets, earning758 themselves more assets; however, to obtain the majority of assets within a system in order to759 “control” it is generally cost prohibitive.760 4 Stake is an amount of cryptocurrency that the user has invested into the system, either by locking it via a special transaction type, or by sending it to a specific address; the amount of staked cryptocurrency is generally no longer able to be spent. The likelihood of a user creating a new block is tied to the ratio of their stake to the overall blockchain system amount of staked cryptocurrency.
- 32. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 30 4.3 Round Robin Consensus Model761 In some blockchain systems there does exist some level of trust between mining nodes. In this762 case, there is no need for a complicated consensus mechanisms to determine which participant763 adds the next block to the chain. This consensus model is often used for private blockchains and764 is called round robin, where nodes take turns in creating blocks. To handle situations where a765 mining node is not available when it is their turn, these systems may include an element of766 randomness to enable available nodes to publish blocks so that unavailable nodes will not cause767 a halt in block production. This model ensures no one node creates the majority of the blocks, it768 benefits from a straightforward approach, it lacks cryptographic puzzles, and has low power769 requirements.770 Unfortunately, due to the need for some level of trust amongst nodes, round robin does not work771 well in the permissionless open networks used by most blockchain based cryptocurrencies772 because malicious nodes can continuously add additional nodes to increase the odds of773 subverting the network.774 4.4 Ledger Conflicts and Resolutions775 As discussed previously, it is possible that multiple blocks will be published at approximately the776 same time. This can cause differing versions of a blockchain to exist at any given moment; these777 must be resolved quickly in order to have consistency in the blockchain. In this section, we778 discuss how these situations are handled.779 With any distributed network, some systems within the network will be behind on information or780 have alternative information. This depends on network latency between nodes and the proximity781 of groups of nodes. Blockchain systems that allow any node to generate blocks are more prone to782 have conflicts due to this openness. A major part of agreeing on the state of the blockchain783 system (coming to consensus) is resolving conflicting data.784 For example, if node_A creates block_n(A) and distributes it to some peers, and node_B785 creates block_n(B) and distributes it to some peers, there will be a conflict. block_n will786 not be the same across the network. This conflict is shown in Figure 11, node_a’s ledger is in787 red, and node_b’s ledger is in blue; they each made block_n, but have different transactions788 within them (block_n(A) contains Transaction 3, but not Transaction 4, while block_n(B)789 contains Transaction 4 but not Transaction 3).790
- 33. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 31 791 Figure 10: Distributed Network in Conflict792 Conflicts temporarily generate different versions of the blockchain, which is depicted in Figure793 11. These differing versions are not “wrong”; rather, they were created with the information the794 node had available. The competing blocks will likely have differing transactions within the795 transaction list, so those with block_n(A) may see transfers of digital assets not present in796 block_n(B). If the blockchain deals with digital currency, money may both be spent and797 unspent, depending on which version of the blockchain is being viewed.798 799 Figure 11: Blockchains in Conflict800 Conflicts are usually quickly resolved. Most blockchain systems will wait until the next block is801 generated and use that chain as the “official” blockchain, thus adopting the “longer blockchain”.802 As in Figure 12, the blue blockchain becomes the “official” chain, as it got the next valid block.803 Any transaction that was present in the chain that was not selected, but not present in the new804 “official” chain, is returned to the unspent transaction pool. Note that this set of waiting805
- 34. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 32 transactions is maintained locally at each node (there is no central server in the architecture).806 807 Figure 12: Chain B Adds the Next Block808
- 35. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 33 5 Forking809 Updating technology can be difficult at the best of times, such as when systems are centralized.810 When a system is comprised of many users, distributed around the world, and governed by the811 consensus of the users, it becomes extremely difficult. Changes to the blockchain software and812 implementation are called forks.813 5.1 Soft Forks814 A soft fork is a change to the technology that will not completely prevent users who do not adopt815 the change (e.g., an update to the latest version) from using the changed blockchain system.816 Since non-updated nodes will recognize the new blocks as valid, a soft fork can be backwards817 compatible, only requiring that a majority of nodes upgrade to enforce the new soft fork rules.818 An example of a soft fork occurred on Bitcoin when a new consensus rule was added to support819 escrow5 and time-locked refunds. In 2014, a proposal was made to repurpose an operation code820 that performed no operation (OP_NOP2) to CHECKLOCKTIMEVERIFY, which allows a821 transaction output to be made unspendable at a point in the future [11]. For future clients that822 implement this change, the blockchain interpreter will perform this new operation, but for clients823 that do not support the change, the script is still valid, and execution will continue as if a NOP 6 824 had been executed.825 5.2 Hard Forks826 A hard fork is a change to the technology that will completely prevent users who do not adopt it827 from using the changed blockchain system. Under a hard fork, the blockchain protocol will828 change in a manner that requires users to either upgrade to stay with the developer’s “main fork”829 or to continue on the original path without the upgrades. Users on different hard forks cannot830 interact with one another. Any change to the block structure, such as the hashing algorithm831 choice, will require a hard fork.832 A well-known example of a hard fork is from Ethereum. In 2016, a smart contract was833 constructed on Ethereum called the Decentralized Autonomous Organization (DAO). Due to834 flaws in how the smart contract was constructed, an attacker extracted Ether, the cryptocurrency835 used by Ethereum, essentially allowing theft of $50 million [12]. A hard fork proposal was voted836 on by Ether holders, and 89 percent agreed to hard fork and create a new version of the837 blockchain that returned the stolen funds.838 With cryptocurrencies, if there is a hard fork and the blockchain splits, the coins each person has839 at the time of the split will be mirrored on each fork. If all the activity moves to the new chain,840 the old one will eventually not be used. In the case of the Ethereum hard fork, the vast majority841 5 Funds placed into a third party to be disseminated based on conditions (via multi-signature transactions) 6 NOP meaning No Operation
- 36. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 34 of support moved to the new fork, and the old fork was renamed to Ethereum Classic, which has842 only a fraction of the original user base.843 5.3 Cryptographic Changes and Forks844 If flaws are found in the cryptographic technologies for a blockchain application, the only845 solution may be to create a hard fork, depending on the significance of the flaw. For example, if846 a flaw was found in the underlying algorithms, there could be a fork requiring all future clients to847 use a stronger algorithm. Until more than 50 percent of the network is on the new software848 version, the vulnerability could still exist. Switching to a new hashing algorithm could pose a849 significant practical problem because it could invalidate all existing specialized mining850 hardware.851 Hypothetically, if SHA-256 were discovered to have a flaw, there would need to be a hard fork852 to migrate to a new hash algorithm. The block that switches over to the new hash algorithm853 would “lock” all previous blocks into SHA-256 (for verification), and all new blocks would need854 to utilize the new hashing algorithm. For example, Bitcoin uses SHA-256 hashes, which is easy855 and fast to implement in hardware ASICs. Other cryptocurrencies such as Ethereum use Keccak-856 256 (based on SHA-3) [13], while Litecoin uses the scrypt hashing algorithm.857 One possibility for the need to change cryptographic features present in a blockchain system858 would be the development of a practical quantum computer system, which would be capable of859 greatly weakening (and in some cases, rendering useless) existing cryptographic algorithms.860 NIST Internal Report (NISTIR) 8105, Report on Post-Quantum Cryptography [14] provides a861 table describing the impact of quantum computing on common cryptographic algorithms. Table862 3 replicates this table.863 Table 3: Impact of Quantum Computing on Common Cryptographic Algorithms864 Cryptographic Algorithm Type Purpose Impact from Large-Scale Quantum Computer AES Symmetric key Encryption Larger key sizes needed SHA-2, SHA-3 N/A Hash functions Larger output needed RSA Public key Signatures, key establishment No longer secure ECDSA, ECDH (Elliptic Curve Cryptography) Public key Signatures, key exchange No longer secure DSA (Finite Field Cryptography) Public key Signatures, key exchange No longer secure 865 The cryptographic algorithms utilized within most blockchain technologies for public/private key866 pairs will need to be replaced if a powerful quantum computer become a reality. This is because867 algorithms that rely on the computational complexity of integer factorization (such as RSA) or868 work on solving discrete logarithms (such as DSA and Diffie-Hellman) are very susceptible to869 quantum computing. The hashing algorithms and Merkle trees that are the other basis for870 blockchains are much less susceptible to quantum computing attacks, but are still weakened871 when quantum computers become a reality.872
- 37. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 35 6 Smart Contracts873 A smart contract is a collection of code and data (sometimes referred to as functions and state)874 that is deployed to a blockchain (e.g., Ethereum). Future transactions sent to the blockchain can875 then send data to public methods offered by the smart contract. The contract executes the876 appropriate method with the user provided data to perform a service. The code, being on the877 blockchain, is immutable and therefore can be used (among other purposes) as a trusted third878 party for financial transactions that are more complex than simply sending funds between879 accounts. A smart contract can perform calculations, store information, and automatically send880 funds to other accounts. It doesn’t necessarily even have to perform a financial function. For881 example, the authors of this document have created smart contracts that publicly generate882 trustworthy random numbers [15].883 In practice, all mining nodes execute the smart contract code simultaneously when mining new884 blocks. Thus, smart contract execution may be more expensive than the simple fund transfers in885 other blockchain based cryptocurrencies. Often, the user issuing a transaction to a smart contract886 will have to pay for the cost of the code execution in addition to the normal transaction fees.887 There is a limit on how much execution time can be consumed by a call to a smart contract. If888 this limit is exceeded, execution stops and the transaction is discarded. This mechanism not only889 rewards the miners for executing the smart contract code, but also prevents malicious users from890 deploying and then accessing smart contracts that will perform a denial of service on the mining891 nodes by consuming all resources (e.g., using infinite loops).892
- 38. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 36 7 Blockchain Categorization893 Blockchains are generally categorized based on the permission model, which determines who894 can access them. If anyone can read and write to a blockchain, it is permissionless. If only895 particular users can read and write to it, it is permissioned. In simple terms, a permissioned896 blockchain is similar to a corporate intranet that is controlled, while a permissionless blockchain897 is like the public internet, where anyone can participate.898 7.1 Permissioned899 Permissioned blockchains defy the original conception of the Bitcoin blockchain where everyone900 can read and write to the blockchain, and the ledger is transparent/public. Organizations that901 wish to work together, but do not fully trust one another, can establish a permissioned blockchain902 and invite business partners to record their transactions on a shared distributed ledger. This903 permissioned blockchain can have the same traceability of assets as they pass through the904 blockchain, as well as the same distributed, resilient, and redundant data storage system as a905 permissionless blockchain. These organizations can determine the consensus mechanism to be906 used, based on how much they trust one another.907 Permissioned blockchains can be set up so anyone can read them, but only selected members can908 record transactions on them. This type of blockchain would provide full insight into the internal909 interactions of the organization by anyone who has an interest, but the public at large would not910 be able to interfere with the data. Permissioned blockchains can also be set up so anyone can911 record transactions on the blockchain, but only selected members can read the data.912 7.1.1 Application Considerations for Permissioned Blockchains913 While permissioned blockchains are often considered an improvement over current systems,914 certain design characteristics must be considered carefully to ensure security. For example, when915 using a database, it is possible to have detailed permission granularity, such as allowing certain916 users to perform specific queries or only allowing certain users to write to specific tables.917 Applications that use a blockchain may need to consider whether the permissions supported by918 the blockchain are granular enough to permit enough roles to be created within the system919 (permissions allow for more traditional roles, such as administrator, user, validator, auditor, etc.).920 This also applies to how permissions are administered. Once a user is given write access to the921 blockchain, is it possible to revoke that permission? Most blockchain implementations are922 immutable, which can make permissions more complicated.923 Trust is another critical consideration when deciding to build an application on a blockchain.924 Within a permissioned blockchain system the method of consensus is generally less925 computationally intensive – therefore it could be possible for users to act maliciously. However,926 the trust does not need to extend to all users. It is possible for the maintainer of the blockchain to927 designate a limited set of mining nodes. If these are trustworthy, it is then unnecessary for the928 user population at large to be trustworthy as the miners will enforce the blockchain rules.929
- 39. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 37 Another important consideration is having a tamper-evident design. If a malicious mining node930 tried to change a block, they might for example forge a transaction to give themselves money.931 Would this kind of change be detected? Are there systems in place to determine what happened?932 Immutability is important and is one of the founding principles of the blockchain. In general,933 malicious transactions that enter the blockchain cannot be undone, even if they are identified. To934 do so requires rewriting published blocks which essentially forks the blockchain and requires the935 approval of the majority of mining nodes. In a permissioned system this can be easier since the936 mining nodes are generally a trusted set that have a special relationship. It is much more difficult,937 but technically possible, for a permissionless systems such as Bitcoin.938 7.1.2 Use Case Examples939 The following sections depict examples of use cases (not an exhaustive list). Inclusion or940 exclusion from this section does not validate or invalidate any potential use case.941 Banking942 Suppose a number of banks want to keep a private, distributed ledger available to only the943 participating banks. This would provide the ability to record transactions from each bank in a944 way that is visible to the participants, but not the public. However, to do this as a private945 blockchain (to avoid having to use an expensive proof of work algorithm), each bank takes turns946 signing the blocks under a distributed consensus algorithm such as Byzantine Paxos [16].947 There are a few interesting considerations when using a private blockchain with few participants,948 such as the ability to overcome its immutability. If there was some major disaster or exception949 situation, the banks could coordinate to roll back the blockchain and write a different transaction.950 Additionally, the transactions would not be anonymous because a banking ID would be needed951 to join.952 Supply Chain953 Recording the transfer of physical goods from a producer, to a shipping terminal, to a ship, to a954 cargo train, to a delivery truck and to a store is an appealing application of blockchain955 technology. A blockchain could play a crucial role in trust and transparency with end customers.956 The blockchain could also be used to monitor supplier actions. Suppliers can record the product957 produced (such as X number of widgets on a certain date) in a way that other viewers of the958 blockchain can verify. With a blockchain, it is possible for warehouses to manage logistics959 efficiently by avoiding overstocking.960 Insurance and Healthcare961 Whenever someone visits a care provider, a myriad of transactions take place behind the scenes.962 Administrative transactions from nurses, doctors, staff, medical providers, insurance companies,963 and pharmacies could all be written to a blockchain. Transactions (such as checking benefits,964 eligibility, coverage, and the available medicine supply) could be read from the blockchain.965
- 40. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 38 Currently, records of these transactions reside in disparate systems, sharing results at the end of966 an (often manual) process.967 7.2 Permissionless968 Permissionless blockchains are decentralized platforms with no central authority and are open to969 participation without users requesting access. Permissionless blockchains often utilize a970 consensus method that requires more than a trivial effort in order to prevent bad users from971 easily subverting the system. Such consensus methods include proof of work and proof of stake972 methods. The reason a permissionless blockchain can work is because there are rewards for973 participating in the process.974 7.2.1 Application Considerations for Permissionless Blockchains975 When deciding whether to utilize a permissionless blockchain, one must consider whether the976 application needs the following qualities:977 • Public facing data – Since permissionless ledgers tend to allow anyone to inspect and978 contribute to the blockchain, the data is generally public. Does the data for the application979 need to be available to everyone? Is there any harm to having public data?980 • Full transactional history – Due to the open nature of data for these systems, anyone981 can track the transfer of assets between accounts, from the creation of assets, to each982 transaction in progress.983 • False data attempts – Since anyone could contribute to the blockchain, some could984 submit false data to the blockchain, mimicking data from valid sources. Is there a way for985 the application to ensure it only gathers data from reputable sources?986 • Data immutability – Many applications follow the “CRUD” (create, read, update,987 delete) functions for data. With a blockchain, there is only “CR” (create, read). There are988 methods that can be employed to “deprecate” older data if a newer version is found, but989 there is no removal process for the original data. Can the application handle (possibly990 outdated) immutable data? Does the data lend itself to being immutable?991 • Transactional throughput capacity – Currently transactions on blockchains are not992 conducted at the same pace as other solutions (e.g., blocks are not added quickly enough),993 so some slowdown while waiting for data to be posted may be incurred. Can the994 application handle that?995 7.2.2 Use Case Examples996 The following sections depict examples of use cases (not an exhaustive list). Inclusion or997 exclusion from this section does not validate or invalidate any potential use case.998 Trusted Timestamping999 Trusted timestamping is a way to prove that certain information existed at a given point [17].1000 The use of a blockchain allows a party to prove they had access to a piece of data in a way that1001 cannot be repudiated. For example, if a person wanted to prove they had possession of a file,1002
- 41. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 39 they could hash the file and record the hash value as an annotation to a transaction. Then, if he or1003 she ever needs to prove possession of the file, it is recorded publicly.1004 Other use cases of leveraging timestamping on a blockchain include proving a task was1005 completed on a certain date, proving possession of a photo, proving a contract was signed, or1006 proving events occurred.1007 Energy Industry1008 Another blockchain application is the recording of autonomous, machine-to-machine1009 transactions regarding electricity use [18]. This would take advantage of digital platform1010 opportunities and changing business models for tracing transactions on the smart grid. One1011 notable use case in the energy industry for the blockchain is in recording certificates. There are1012 different power plants generating energy and creating certificates that attest to the amount of1013 energy produced for subsequent exchange. Currently, there are problems such as emission1014 certificates being spent twice, as well as the need to address regulatory challenges and provide1015 more uniform access for everybody in the market. A blockchain can effectively track the1016 issuance and spending of these energy certificates.1017 Another example of how blockchains are applicable in the energy industry is in the trading of1018 excess renewable energy. Buildings can be wired with devices measuring energy usage and1019 recording it to a blockchain, enabling excess energy to be sold and bought on a market.1020
- 42. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 40 8 Blockchain Platforms1021 Many blockchains are in use today, primarily for digital cash solutions. This section discusses a1022 selection of blockchain platforms to highlight the technical differences and approaches being1023 used. This is not an endorsement of any of these platforms, nor should it be construed as a list of1024 the most popular or important platforms.7 1025 8.1 Cryptocurrencies1026 Numerous applications of blockchain technologies are primarily oriented around moving1027 currency from one account to another. This section profiles several examples of such blockchain1028 applications.1029 8.1.1 Bitcoin (BTC)1030 Bitcoin is a digital cash system that has been previously discussed as the pioneer in using a1031 blockchain. New blocks are created approximately once every 10 minutes using SHA-2561032 hashing to link them together. It is a proof of work system where mining nodes must find a1033 nonce to include in their block such that the hash of the block is less than some predetermined1034 difficulty value. The difficulty is adjusted up or down to attempt to achieve the 10-minute target1035 for block creation. Early in Bitcoin’s history, individual computers could mine and publish1036 blocks; currently Bitcoin requires specialized hardware, large datacenters, or many individuals1037 working together in a mining pool to win the competition to publish blocks.1038 With Bitcoin, the paying of transaction fees is technically optional since the mining nodes get1039 most of their funds through the publication of blocks. This fee is designed to be a small fee for1040 each transaction, but it can and has become large due to a substantial backlog of pending1041 transactions. Paying a higher transaction fee can give a transaction a greater priority for getting1042 added to the blockchain. Initially, mining nodes got 50 Bitcoin for each block, and only half of1043 that after a certain number of blocks. For example, the reward for mining a block was 12.51044 Bitcoins in July 2016. Per the Bitcoin protocol, this reward will halve every 210,000 blocks1045 (around four years) and will decrease to zero once 21 million Bitcoins have been produced [19].1046 Bitcoin mining will continue at that point, but the reward will be completely derived from1047 transaction fees.1048 One last technical note of interest is that each Bitcoin transaction contains code written in a1049 language called Script. This code represents a simple program that specifies the transaction. It1050 contains no loops and is highly restricted with regards to functionality (i.e., it is not Turing1051 complete8 ). Bitcoin transactions today use only a small portion of the available features of Script.1052 In practice, most Bitcoin transactions use one of just a few templates of code for the movement1053 of funds between parties.1054 7 The website Map of Coins (http://mapofcoins.com/) provides a good example of a number of blockchain systems, but is still far from being a complete listing 8 A Turing complete system (computer system, programming language, etc.) can be used for any algorithm, regardless of complexity, to find a solution.
- 43. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 41 8.1.2 Bitcoin Cash (BCC)1055 In July 2017, approximately 80 to 90 percent of the Bitcoin computing power voted to1056 incorporate Segregated Witness (SegWit, where transactions are split into two segments:1057 transactional data, and signature data), which made it possible to reduce the amount of data being1058 verified in each block. Signature data can account for up to 65 percent of a transaction block, so1059 a change in how signatures are implemented could be useful. When SegWit was activated, it1060 caused a hard fork, and all the mining nodes and users who did not want to change started calling1061 the original Bitcoin blockchain Bitcoin Cash (BCC). Technically, Bitcoin is a fork and Bitcoin1062 Cash is the original blockchain. When the hard fork occurred, people had access to the same1063 amount of coins on Bitcoin and Bitcoin Cash.1064 8.1.3 Litecoin (LTC)1065 Litecoin is inspired by and is very similar to Bitcoin, but aims to provide faster confirmation1066 times. Litecoin has implemented SegWit, splitting transactions into two segments and hiding an1067 increased block size [20]. The “witness” signature is separated from the Merkle tree. Another1068 difference between Bitcoin and Litecoin is Litecoin uses the Scrypt algorithm for hashing instead1069 of SHA-256. The Scrypt algorithm is more difficult to solve than SHA-256 because it uses more1070 memory, which makes development of custom application-specific integrated circuits (ASICs)1071 more difficult. There is a larger maximum number of coins which can be mined (84 million1072 Litecoins). Litecoin is a complement to Bitcoin, with higher transaction volumes, and not1073 designed to replace it [21].1074 8.1.4 Ethereum (ETH)1075 Ethereum is a blockchain platform focused on providing smart contracts. Smart contracts are1076 programs that exist on the blockchain that can be accessed by Ethereum users. They can both1077 receive and send funds while performing arbitrary computation. A properly designed contract1078 can act as a trusted third party in financial transactions since its code is both public and1079 immutable. Ethereum’s transaction programming language is Turing complete. Mining nodes1080 receive funds through mining and transaction fees.1081 Ethereum also has a concept called “gas” used to power the transactional computations (and is1082 generally around 1/100,000 of an Ether). Every transaction consumes gas as it executes, and the1083 originator of a particular transaction must pay sufficient gas, or the execution of the transaction1084 aborts. There is a maximum gas limit per smart contract (currently three million gas) to prevent1085 computationally expensive programs from being submitted to the Ethereum mining nodes. This1086 is because all mining nodes must execute the transactions in parallel [22].1087 The submission of a transaction to an Ethereum contract causes a program to be run in parallel1088 on the mining nodes’ computers. The resulting state of the contract is stored on the blockchain1089 by the user that publishes the next block.1090 8.1.5 Ethereum Classic (ETC)1091 Ethereum Classic was created when Ethereum hard forked after the DAO hack [12]. An attacker1092 had drained approximately $50 million, and the Ethereum Foundation created a hard fork to1093
- 44. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 42 move the stolen funds back to a state before the attack took place. Users who owned Ethereum1094 before the DAO hard fork had the same amount of Ethereum Classic (ETC) after the fork. The1095 reason it exists is because a number of users of the Ethereum blockchain rejected the fork for1096 philosophical reasons [23], including the principle that the blockchain cannot be changed, and1097 decided to keep using the unforked Ethereum blockchain. The mining and software is largely the1098 same between Ethereum and Ethereum Classic, with the difference being that Ethereum is a fork1099 and the more popular chain.1100 8.1.6 Dash (DASH)1101 Dash is a cryptocurrency built with the objective of providing faster transactions. It uses a1102 “masternode” network and can make transactions within four seconds [24]. Dash uses1103 deterministic ordering for the masternodes by using the hash and proof of work for each block.1104 Interestingly, becoming a masternode requires 1000 Dash collateral, which makes it very1105 expensive (nearly impossible) to control more than 50 percent of the network [25]. The collateral1106 requirement for masternodes seeks to alleviate the problems of untrusted nodes in a peer-to-peer1107 network.1108 Dash uses a different hashing algorithm than most, x11. This consists of using all 11 SHA-31109 contestant algorithms (including BLAKE, JH, Keccak, and Skein), with each hash being1110 submitted to the next algorithm in the chain [25]. The reasoning is that multiple algorithm use1111 makes it harder for an ASIC to be created that targets solving these hashes in hardware.1112 8.1.7 Ripple (XRP)1113 Ripple is the name of both a cryptocurrency and the payment network on which it is transferred.1114 The goal of Ripple is to build on the approach of Bitcoin and to connect different payment1115 systems together. It has a fixed supply of 100 billion XRP, with half of them designated for1116 circulation [26]. Ripple clients do not need to download the entire blockchain, making it easy for1117 clients to join in seconds. Additionally, there is no mining reward for running a server because1118 each transaction costs a small amount of Ripple, similar to Ethereum gas. Therefore, there are no1119 mining nodes or mining pools; instead, about one-thousandth of a cent from each transaction is1120 destroyed [27]. Ripple is not designed with explicit goals for anonymity, but it does have features1121 providing privacy, such as using proxied gateway payments.1122 8.2 Hyperledger1123 Hyperledger is a group of projects aiming to create enterprise-grade, open-source distributed1124 ledgers [28]. The Hyperledger Project is supported and hosted by the Linux Foundation.1125 Although hosted by the Linux Foundation, each project was developed and contributed by1126 different sources. There are several projects within the Hyperledger Project, each one providing a1127 blockchain platform to solve specific problems.1128 8.2.1 Hyperledger Fabric1129 This is a modular, permissioned blockchain that can run smart contracts (called chaincode) [29].1130 The Fabric blockchain was initially contributed to the Hyperledger Project by Digital Asset and1131 IBM.1132
- 45. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 43 8.2.2 Hyperledger Sawtooth1133 This is a modular distributed ledger using proof of elapsed time as the consensus protocol. In a1134 proof of elapsed time system, every participant requests a “wait time” from a hardware enclave (a1135 trusted and secure feature available on some hardware), which distributes wait times randomly.1136 Whichever participant was awarded the shortest time creates the next block in the chain. The use1137 of Hyperledger Sawtooth is tightly coupled to hardware that supports the hardware enclave1138 feature. Hyperledger Sawtooth was initially contributed by Intel.1139 8.2.3 Hyperledger Iroha1140 This acts as an Identity/Know Your Customer (KYC) service using blockchain technologies,1141 which allows institutions to share data and manage identity. Hyperledger Iroha was initially1142 contributed by Soramitsu, Hitachi, NTT Data, and Colu.1143 8.2.4 Hyperledger Burrow1144 Hyperledger Burrow is a permissioned smart contract-enabled blockchain platform. It accepts1145 Ethereum-based smart contract code. Hyperledger Burrow was originally contributed by Monax1146 and co-sponsored by Intel.1147 8.2.5 Hyperledger Indy1148 This is an independent identity platform providing provenance for trust transactions and1149 accountability. It supports user-controlled exchanges of verifiable claims about identifying1150 information, as well as revocation models. It supports three important privacy features:1151 Decentralized Identifiers (DIDs), pointers to off-ledger sources so that no personal data is written1152 to the ledger, and zero-knowledge-proofs. The Indy code is being contributed to the Hyperledger1153 Project by the Sovrin Foundation.1154 8.3 MultiChain1155 MultiChain is an open source blockchain platform that enables anyone to setup, configure, and1156 deploy a private, semi-private, or public blockchain. MultiChain is a fork of Bitcoin, but with1157 many modifications. Users can determine whether there is to be an associated cryptocurrency, as1158 well as the consensus method (round robin or proof of work). In the default configuration,1159 MultiChain is a private, permissioned-based blockchain using round-robin consensus. This1160 means that the first person to set up the blockchain acts as an administrator and initial node; all1161 additional users must direct their MultiChain blockchain clients to this first node, and the1162 administrator must grant them permissions.1163 MultiChain Streams [30] are a unique feature; they are described as “shared immutable key-1164 value time series databases” which are stored on a blockchain.1165
- 46. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 44 9 Blockchain Limitations and Misconceptions1166 There is a tendency to overhype and overuse most nascent technology. Many projects will1167 attempt to incorporate the technology, even if it is unnecessary. This stems from the technology1168 being relatively new and not well understood, or the technology being surrounded by1169 misconceptions. Blockchain technology has not been immune. This section highlights some of1170 the limitations and misconceptions of blockchain technology.1171 9.1 Blockchain Control1172 A common misconception is that permissionless blockchains are systems without control and1173 ownership. The phrase “no one controls a blockchain!” is often exclaimed; however, while no1174 user, government, or country controls a blockchain, there is still a group of core developers who1175 are responsible for the system’s development. These developers may act in the interest of the1176 community at large, but they still maintain some level of control. For example, in 2013 Bitcoin1177 developers released a new version of the most popular Bitcoin client which introduced a flaw1178 and started two competing chains-of-blocks. The developers had to decide to either keep the new1179 version (which had not yet been adopted by everyone) or revert to the old version [31]. Either1180 choice would result in one chain being discarded—and some people’s monetary transactions1181 becoming invalid.1182 The developers made a choice, reverted to the old version, and successfully controlled the1183 progress of the Bitcoin blockchain. This example was an unintentional fork; however, developers1184 can purposely build new clients, and with enough adoption from the user base, a successful fork1185 can be created. These forks are often discussed at length and given a long adoption period before1186 being made mandatory to continue recording transactions on the new “main” fork.1187 The phrase “no one controls a blockchain!” would be better stated as, “no one controls with1188 whom and when you can perform transactations, within the rules of the blockchain system.”1189 9.2 Malicious Users1190 While the blockchain system can enforce transaction rules and specifications, it cannot enforce a1191 code of conduct. This is problematic in permissionless blockchain systems, since users are1192 pseudonymous and there is not a one-to-one mapping between blockchain nodes and users of the1193 system. Permissionless blockchains provide incentive (e.g., a cryptocurrency) to motivate users1194 to act fairly; however, some may choose to act maliciously if that provides greater incentives.1195 The largest problem for malicious users is getting enough power (be it a stake in the system,1196 processing power, etc.) to cause damage. Once a large enough malicious collusion is created,1197 malicious mining actions can include:1198 • Ignoring transactions from specific users, nodes, or even entire countries.1199 • Creating an altered, alternative chain in secret, then submitting it once the alternative1200 chain is longer than the real chain. The honest nodes will switch to the chain that has the1201 most “work” done (per the blockchain protocol). This could attack the concept of1202 “immutability” within a blockchain system [32].1203
- 47. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 45 • Refusing to transmit blocks to other nodes, essentially disrupting the distribution of1204 information.1205 While malicious users can be annoyances and create short-term harm, blockchains can perform1206 hard forks to combat them. Whether damages done (money lost) would be reversed would be up1207 to the developers and users of the blockchain system.1208 9.3 No Trust1209 Another common misinterpretation comes from people hearing that there is no “trusted third1210 party” in a blockchain and assuming blockchain systems are “trustless” environments. While1211 there is no trusted third party certifying transactions in permissionless blockchain systems (in1212 permissioned systems it is less clear, as administrators of those systems act as an administrator of1213 trust by granting users admission and permissions), there is still a great deal of trust needed to1214 work within a blockchain system:1215 • There is trust in the cryptographic technologies utilized. For example, cryptographic1216 algorithms or implementations can have flaws, and smart contracts can have unintended1217 loopholes and flaws.1218 • There is trust in the developers of the software to produce software that is as bug-free as1219 possible.1220 • There is trust that most users of the blockchain are not colluding in secret. If a single1221 group or individual can control more than 50 percent of all block creation power, it is1222 possible to subvert a permissionless blockchain system. However, generally obtaining the1223 necessary computational power is prohibitively expensive.1224 • There is trust that nodes are accepting and processing transactions fairly.1225 9.4 Resource Usage1226 Blockchain technology has enabled a worldwide network of value where every transaction is1227 verified and the blockchain is kept in sync amongst a multitude of users. For blockchain systems1228 utilizing proof of work, this means there is a large number of users churning away processing1229 time and consuming a lot of electricity. A proof of work method is a great solution for “hard to1230 create, easy to verify” proofs, but as discussed in Section 4.1, it requires significant resource1231 usage.1232 An additional strain on resources occurs whenever a new full node is created; the node must1233 obtain (usually through downloading) most of or all the blockchain data (Bitcoin’s blockchain1234 data is over 100 gigabytes in size as of this writing) [33]. This process uses a lot of network1235 bandwidth.1236 Blockchains are often compared to databases, and while they both store information, blockchains1237 have limits on the amount of data that can be stored and are not meant to be a general storage1238 medium. In order to quickly calculate hashes on transactions and distribute transactions amongst1239 the network, transactions need to be relatively small. Large amounts of data are usually stored1240 “off chain,” with “pointers/references” or hashes of the data stored within the blockchain itself.1241 Blockchains also benefit from data being immutable, which is not a trait general purpose data1242 usually needs.1243
- 48. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 46 9.5 Transfer of Burden of Credential Storage to Users1244 Since blockchains are not centralized, there is no intrinsic central place for user key1245 management. Users must manage their own private keys, meaning if one is lost, anything related1246 to that private key is lost (digital assets, etc.). There is no “forgot my password” or “recover my1247 account” feature for blockchain systems. While centralized management solutions can be put1248 into place, they create the same problems current systems have: central points of failure.1249 9.6 Private/Public Key Infrastructure and Identity1250 Some people, when hearing that blockchain technology incorporates a public/private key1251 infrastructure, immediately believe it intrinsically supports identity. This is not the case, as there1252 is not a one-to-one relationship of private key pairs to users (a user can have multiple private1253 keys), nor is there a one-to-one relationship between blockchain addresses and public keys1254 (multiple addresses can be derived from a single public key). Nodes on the Bitcoin blockchain1255 validate transactions before they are added to a block and subsequently incorporated into the1256 blockchain. One stage of this validation requires the user that initiated the transaction to sign the1257 transaction with a private key. Blockchain nodes verify the signature to prove the user does in1258 fact own the Bitcoin value being transferred.1259 Digital signatures are often used to prove identity in the cybersecurity world, and this can lead to1260 confusion about the potential application of a blockchain to identity management. A1261 blockchain’s transaction signature verification process links transactions to the owners of private1262 keys, but provides no facility for associating real-world identities with these owners. In some1263 cases, it is possible to connect real-world identities with private keys, but these connections are1264 made through processes outside, and not explicitly supported by, the blockchain. For example, a1265 law enforcement agency could request records, from an exchange, that would connect1266 transactions to specific individuals. Another example is an individual posting an address online1267 for donations.1268 While it is possible to use blockchains in identity management frameworks that require a1269 distributed ledger component, it is important to understand that typical blockchain1270 implementations are not designed to serve as standalone identity management systems. There is1271 more to having secure digital identities than simply implementing a blockchain.1272 1273
- 49. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 47 10 Conclusions1274 Blockchains are a significant new avenue for technological advancements, enabling secure1275 transactions without the need for a central authority. Starting in 2009, with Bitcoin leveraging1276 blockchain technology, there has been an increasing number of blockchain based1277 cryptocurrencies. Possibly more importantly, new applications beyond the realm of currencies1278 are building upon the fundamentals of blockchain technology.1279 The first applications were digital currencies with the distribution of a global ledger containing1280 all transactions. These transactions are secured with cryptographic hashes, and transactions are1281 signed and verified using public/private key pairs. The transaction history is summarized with1282 Merkle trees, to efficiently and securely record a chain of events in a way that any attempt to edit1283 or change a past transaction will also require a recalculation of all subsequent blocks of1284 transactions.1285 The use of blockchains is still in its early stages, but it is built on widely understood and sound1286 cryptographic principles. Moving forward, it is likely that blockchains will be another tool that1287 can be used to solve newer sets of problems. Financial organizations are likely to be the1288 businesses most impacted by blockchains. They may need to adapt or even completely change1289 their practices to focus on being platforms for value exchange and not just places to store value.1290 Blockchains are also digitizing assets other than money. Companies that need to maintain a1291 public record, such as holding land title, marriage, or birth records, should consider how their1292 problem sets might be addressed by blockchain technologies. Blockchains also have strong1293 potential for storing and recording supply chain records. A blockchain can record each step in a1294 product's life, from when it was created in a factory, to when it was shipped and subsequently1295 delivered to a store, and finally to when a consumer purchased it. There may even be new1296 industries, such as digital notaries who can prove a person had access to a specific piece of1297 information by recording the hash of it into the blockchain. There are many potential uses and1298 opportunities for blockchain technologies.1299 As detailed throughout this publication, a blockchain relies on existing network, cryptographic,1300 and recordkeeping technologies but uses them in a new manner. It will be important that1301 organizations are able to look at the technologies and both the advantages and disadvantages of1302 using them. Once a blockchain is implemented and widely adopted, it becomes very difficult to1303 change it without forking. Once something is recorded in a blockchain, it is usually there forever,1304 even when there is a mistake. For some organizations these are desirable features. For others,1305 these may be deal breakers preventing the adoption of blockchain.1306 Blockchain technologies have the power to disrupt many industries. To avoid missed1307 opportunities and undesirable surprises, organizations should start investigating whether or not a1308 blockchain can help them.1309
- 50. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 48 Appendix A—Acronyms1310 Selected acronyms and abbreviations used in this paper are defined below.1311 ASIC Application-Specific Integrated Circuit BCC Bitcoin Cash BFT Byzantine Fault Tolerant BTC Bitcoin CPU Central Processing Unit CR Create, Read CRUD Create, Read, Update, Delete DAO Decentralized Autonomous Organization DID Decentralized Identifier DSA Digital Signature Algorithm ECDSA Elliptic Curve Digital Signature Algorithm ETC Ethereum Classic ETH Ethereum EVM Ethereum Virtual Machine FIPS Federal Information Processing Standard FOIA Freedom of Information Act GPU Graphics Processing Unit I2P Invisible Internet Project IoT Internet of Things IR Internal Report ITL Information Technology Laboratory KYC Know Your Customer NIST National Institute of Standards and Technology
- 51. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 49 NISTIR National Institute of Standards and Technology Internal Report RSA Rivest-Shamir-Adleman SegWit Segregated Witness SHA Secure Hash Algorithm XMR Monero XRP Ripple 1312 1313
- 52. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 50 Appendix B—Glossary1314 Selected terms used in this paper are defined below.1315 Address A short, alphanumeric string derived from a user’s public key using a hash function, with additional data to detect errors. Addresses are used to send and receive digital assets. Assets Anything that can be transferred. Block A set of validated transactions. Block header The portion of the block that contains information about the block itself (block metadata), usually including the timestamp for posting the block, the Merkle tree root hash, the previous block’s hash, and the cryptographic nonce (if needed). Blockchain A distributed digital ledger of cryptographically signed transactions that are grouped into blocks. Each block is cryptographically linked to the previous one after validation and undergoing a consensus decision. As new blocks are added, older blocks become more difficult to modify. New blocks are replicated across all copies of the ledger within the network, and any conflicts are resolved automatically using established rules. Byzantine Fault Tolerant proof of stake consensus model A proof of stake consensus model where the blockchain decides the next block by allowing all staked members to “vote” on which submitted block to include next. Centralized network A network configuration where participants must communicate with a central authority to communicate with one another. Since all participants must go through a single centralized source, the loss of that source would prevent all participants from communicating. Chain-based proof of stake consensus model A proof of stake consensus model where the blockchain system decides the next block through pseudo-random selection, based on a personal stake to overall system asset ratio. Conflict One or more participants disagree on the state of the system.
- 53. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 51 Conflict resolution A predefined method for coming to a consensus on the state of the system (e.g., when portions of the system participants claim there is State_A and the rest of the participants claim there is State_B, there is a conflict – the system will automatically resolve this conflict by choosing the “Valid” state as being the one from whichever group adds the next block of data; any transactions “lost” by the state not chosen are added back into the unspent transaction pool). Consensus algorithm A predefined method to determine whether some data can be committed to a data store. Also known as a consensus model. Cryptocurrency A digital asset/credit/unit within the system, which is cryptographically sent from one user to another user. In the case of cryptocurrency creation (such as the reward for mining), the system itself generates and distributes the currency via the same cryptographic mechanisms. These assets are transferred from one wallet to another by using digital signatures with public/private key pairs. Cryptographic hash function A function that maps a bit string of arbitrary length to a fixed-length bit string. Approved hash functions satisfy the following properties: 1. (One-way) It is computationally infeasible to find any input that maps to any pre-specified output, and 2. (Collision resistant) It is computationally infeasible to find any two distinct inputs that map to the same output. From NIST SP 800-175B Guideline for Using Cryptographic Standards in the Federal Government: Cryptographic Mechanisms, http://dx.doi.org/10.6028/NIST.SP.800-175B Cryptographic nonce An arbitrary number (usually randomly selected) that is used once. Decentralized network A network configuration where there are multiple authorities that serve as a centralized hub for a subsection of participants. Since some participants are behind a centralized hub, the loss of that hub will prevent those participants from communicating.
- 54. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 52 Digital signature A cryptographic technique that utilizes private/public keys to determine authenticity (i.e., users can verify that the message was signed with a private key corresponding to the specified public key), non-repudiation (a user cannot deny having sent a message) and integrity (that the message was not altered during transmission). Distributed network A network configuration where every participant can communicate with one another without going through a centralized point. Since there are multiple pathways for communication, the loss of any participant will not prevent communication. Also known as peer-to- peer. Fork A change to blockchain software and implementation. Full node A blockchain node that stores the blockchain data, passes along the data to other nodes, and ensures that newly added blocks are valid. Genesis block The first block of a blockchain system; it records the initial state of the system. Hard fork A fork that will completely prevent users who do not adopt it from using the changed blockchain system. Users must either upgrade to stay with the developer’s main fork or continue on the original path without upgrades. Users on different hard forks cannot interact with one another. Hash chain An append-only data structure where data is bundled into blocks that include a hash of the previous block’s data within the newest block. This data structure provides evidence of tampering because any modification to a block’s data will change the hash digest recorded by the following block. Hash digest The output of a hash function (e.g., hash(data) = digest). Also known as a digest. Hashing A method of calculating a relatively unique output (called a hash digest) for an input of nearly any size (a file, text, image, etc.) Hash algorithms are designed to be one-way; calculating the digest of an input is simple, but reconstructing the input from the digest is significantly difficult, and to be collision-resistant, so that it is computationally infeasible to find two inputs which result in the same digest. Additionally, the smallest change of input, even a single bit, will result in a completely different output digest. Immutable Data that can only be written, not modified. Ledger A collection of transactions recorded chronologically. Lightweight node A blockchain node that does not need to store a full copy of the blockchain and often passes its data to full nodes to be processed.
- 55. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 53 Merkle tree A data structure where the data is hashed and combined until there is a singular root hash that represents the entire structure. Mining The act of performing the required work (as defined by the system’s consensus algorithm) to add the next block to the system and usually rewarded with a cryptocurrency. Also known as minting. Mining Node One of a subset of nodes in charge of maintaining the blockchain. Also known as a minter. Node An individual system within the blockchain. Permissioned A system where every user must have their permissions assigned by an administrator. Permissionless A system where all users’ permissions are equal and not set by any administrator. Permissions Allowable user actions (e.g., read, write, execute). Proof of stake consensus model A consensus model where the blockchain network is secured by users locking an amount of cryptocurrency into the blockchain system, a process called staking. Participants with more stake in the system are more likely to want it to succeed and to not be subverted, which gives them more weight during consensus. Proof of work consensus model A consensus model where a mining node obtains the right to publish the next block by expending time, energy, and computational cycles to solve a hard-to-solve, but easy-to-verify problem (e.g., finding the nonce which, when combined with the data to be added to the block, will result in a specific output pattern). Public/private key cryptography A cryptographic system where users have a private key that is kept secret and used to generate a public key (which is freely provided to others). Users can digitally sign data with their private key, and the resulting signature can be verified by anyone using the corresponding public key. Also known as asymmetric cryptography. Round robin consensus model A consensus model for private blockchains where nodes are pseudo- randomly selected to create blocks, but a node must wait several block- creation cycles before being chosen again to add another new block. This model ensures that no one participant creates the majority of the blocks, and it benefits from a straightforward approach, lacking cryptographic puzzles, and having low power requirements.
- 56. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 54 Soft fork A fork that will not completely prevent users who do not adopt it from using the changed blockchain system. A soft fork can be backwards compatible, only requiring that a majority of mining nodes upgrade to enforce the new soft fork rules. Transaction A recording of a transfer of assets (digital currency, units of inventory, etc.) between parties. Transaction pool A distributed queue where candidate transactions wait until they are added to the blockchain. Also known as Unspent transaction pool. Turing complete A system (computer system, programming language, etc.) that can be used for any algorithm, regardless of complexity, to find a solution. User Any single person, group, business, or organization which is using or operating a blockchain node Wallet Software used to manage public/private keys and addresses used for transactions. 1316
- 57. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 55 Appendix C—References1317 [1] Clarke, A.C., “Hazards of Prophecy: The Failure of Imagination,” from Profiles of the Future: An Inquiry into the Limits of the Possible, 1962. [2] Narayanan, A., Bonneau, J., Felten, E., Miller, A., and Goldfede, S., Bitcoin and Cryptocurrency Technologies: A Comprehensive Introduction, Princeton University Press, 2016. [3] Nakamoto, S., “Bitcoin: A Peer-to-Peer Electronic Cash System,” 2008. https://bitcoin.org/bitcoin.pdf [4] National Institute of Standards and Technology (NIST), Federal Information Processing Standards (FIPS) Publication 180-4, Secure Hash Standard (SHS), August 2015. https://doi.org/10.6028/NIST.FIPS.180-4 [5] National Institute of Standards and Technology (NIST), Secure Hashing website, https://csrc.nist.gov/projects/hash-functions [6] National Institute of Standards and Technology (NIST), Federal Information Processing Standards (FIPS) Publication 186-4, Digital Signature Standard, July 2013. https://doi.org/10.6028/NIST.FIPS.186-4 [7] Deetman, S., “Bitcoin Could Consume as Much Electricity as Denmark by 2020,” Motherboard, March 29, 2016. https://motherboard.vice.com/en_us/article/bitcoin-could-consume-as-much- electricity-as-denmark-by-2020 [8] Hern, A., “Bitcoin mining consumes more electricity a year than Ireland,” The Guardian, November 27, 2017. https://www.theguardian.com/technology/2017/nov/27/bitcoin-mining-consumes- electricity-ireland [9] Power Compare, https://powercompare.co.uk/bitcoin/ [10] Bahsoun, J.P., Guerraoui, R., and Shoker, A., “Making BFT Protocols Really Adaptive,” 2015 IEEE International Parallel and Distributed Processing Symposium, Hyderabad, India, pp. 904-913, 2015. https://doi.org/10.1109/IPDPS.2015.21 [11] Todd, P., Bitcoin Improvement Proposal (BIP) 65, “OP_CHECKLOCKTIMEVERIFY,” October 1, 2014. https://github.com/bitcoin/bips/blob/master/bip-0065.mediawiki [12] Wong, J. and Kar, I., “Everything you need to know about the Ethereum ‘hard fork,’” Quartz Media, July 18, 2016. https://qz.com/730004/everything-you-need- to-know-about-the-ethereum-hard-fork/ [13] National Institute of Standards and Technology (NIST), Federal Information Processing Standards (FIPS) Publication 202, SHA-3 Standard: Permutation- Based Hash and Extendable-Output Functions, August 2015. https://doi.org/10.6028/NIST.FIPS.202
- 58. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 56 [14] Chen, L., Jordan, S., Liu, Y.-K., Moody, D., Peralta, R., Perlner, R., and Smith- Tone, D., National Institute of Standards and Technology (NIST), NIST Internal Report (NISTIR) 8105, Report on Post-Quantum Cryptography, April 2016. https://doi.org/10.6028/NIST.IR.8105 [15] Mell, P., Kelsey, J., and Shook, J., “Cryptocurrency Smart Contracts for Distributed Consensus of Public Randomness.” October 7, 2017. https://doi.org/10.1007/978-3-319-69084-1_31 [16] Lamport, L., “Leaderless Byzantine Paxos,” Distributed Computing: 25th International Symposium: DISC 2011, p. 141-142, December 27, 2011. https://www.microsoft.com/en-us/research/publication/leaderless-byzantine-paxos [17] Gipp, B., Meuschke, N., and Gernandt, A., “Decentralized Trusted Timestamping using the Crypto Currency Bitcoin,” in Proceedings of the iConference 2015, Newport Beach, California, 2015. [18] Mattila, J., Seppälä, T., Naucler, C., Stahl, R., Tikkanen, M., Bådenlid, A., and Seppälä, J., The Research Institute of the Finnish Economy (ETLA) Working Papers No. 43, “Industrial Blockchain Platforms: An Exercise in Use Case Development in the Energy Industry,” The Research Institute of the Finnish Economy, October 11, 2016. https://www.etla.fi/wp-content/uploads/ETLA- Working-Papers-43.pdf [19] Donnelly, J., “What is the 'Halving'? A Primer to Bitcoin's Big Mining Change,” CoinDesk, June 12, 2016. https://www.coindesk.com/making-sense-bitcoins- halving/ [20] Hertig, A., “Litecoin’s SegWit Activation: Why it Matters and What’s Next,” CoinDesk, April 26, 2017. https://www.coindesk.com/litecoins-segwit-activation- why-it-matters-and-whats-next/ [21] Litecoin Project. https://litecoin.org/ [22] Wood, G., “Ethereum: A Secure Decentralised Generalised Transaction Ledger.” https://bravenewcoin.com/assets/Whitepapers/Ethereum-A-Secure-Decentralised- Generalised-Transaction-Ledger-Yellow-Paper.pdf [23] Pearson, J., “The Ethereum Hard Fork Spawned a Shaky Rebellion,” Motherboard, July 27, 2016. https://motherboard.vice.com/en_us/article/the- ethereum-hard-fork-spawned-a-shaky-rebellion-ethereum-classic-etc-eth [24] “What Is Dash?”, WeUseCoins. https://www.weusecoins.com/what-is-dash/ [25] Duffield, E. and Diaz, D., “Dash: A Privacy-Centric Crypto-Currency.” https://github.com/dashpay/dash/wiki/Whitepaper [26] “Introduction to Ripple for Bitcoiners,” last modified December 10, 2013. https://wiki.ripple.com/Introduction_to_Ripple_for_Bitcoiners [27] Brown, A., “10 things you need to know about Ripple,” CoinDesk, May 17, 2013. https://www.coindesk.com/10-things-you-need-to-know-about-ripple/
- 59. NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW 57 [28] “Hyperledger Business Blockchain Technologies,” The Linux Foundation. https://www.hyperledger.org/projects [29] Cachin, C., “Architecture of the Hyperledger blockchain fabric,” in Workshop on Distributed Cryptocurrencies and Consensus Ledgers, July 2016. [30] Greenspan, G., “Introducing MultiChain Streams,” MultiChain, September 15, 2016. http://www.multichain.com/blog/2016/09/introducing-multichain-streams/ [31] Narayanan, A., “Analyzing the 2013 Bitcoin fork: centralized decision-making saved the day,” MultiChain, July 28, 2015. https://freedom-to- tinker.com/2015/07/28/analyzing-the-2013-bitcoin-fork-centralized-decision- making-saved-the-day [32] Greenspan, G., “The Blockchain Immutability Myth,” MultiChain, May 4, 2017. https://www.multichain.com/blog/2017/05/blockchain-immutability-myth/ [33] “Bitcoin blockchain size reaches 100 GB,” Coinfox, December 19, 2016. http://www.coinfox.info/news/6700-bitcoin-blockchain-size-reaches-100-gb 1318






![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
iv
Executive Summary112
Blockchains are immutable digital ledger systems implemented in a distributed fashion (i.e.,113
without a central repository) and usually without a central authority. At their most basic level,114
they enable a community of users to record transactions in a ledger that is public to that115
community, such that no transaction can be changed once published. In 2008, the blockchain116
idea was combined in an innovative way with several other technologies and computing concepts117
to enable the creation of modern cryptocurrencies: electronic money protected through118
cryptographic mechanisms instead of a central repository. The first such blockchain based119
approach was Bitcoin. These currency blockchain systems are novel in that they store value, not120
just information. The value is attached to a digital wallet—an electronic device (or software) that121
allows an individual to make electronic transactions. The wallets are used to sign transactions122
sent from one wallet to another, recording the transferred value publicly, allowing all participants123
of the network to independently verify the validity of the transactions. Each participant can keep124
a full record of all transactions, making the network resilient to attempts to alter that record (or125
forge transactions) later.126
Because there are countless news articles and videos describing the “magic” of the blockchain,127
this paper aims to describe the method behind the magic (i.e., how a blockchain system works).128
Arthur C. Clarke once wrote, “Any sufficiently advanced technology is indistinguishable from129
magic” [1]. Clarke’s statement is a perfect representation for the emerging use cases for130
blockchain technology. There is a high level of hype around the use of blockchains, yet the131
technology is not well understood. It is not magical; it will not solve all problems. As with all132
new technology, there is a tendency to want to apply it to every sector in every way imaginable.133
This document attempts bring a high-level understanding of the technology so that it can be134
applied effectively.135
As stated above, blockchain technology is the foundation of modern cryptocurrencies, so named136
because of blockchain’s heavy usage of cryptographic functions. Users utilize public and private137
keys to digitally sign and securely transact within the system. Users of the blockchain may solve138
puzzles using cryptographic hashing in hopes of being rewarded with a fixed amount of the139
cryptocurrency. However, blockchain technology is more broadly applicable than its application140
to cryptocurrencies. In this work, we try to show this broader applicability while still focusing to141
a large extent on the cryptocurrency use case (since that is the primary use case today).142
Organizations considering implementing blockchain technology need to understand important143
aspects of the technology. For example, what happens when an organization implements a144
blockchain system and then decides they need to make modifications to the data stored? When145
using a database, this can be accomplished through a simple query (or major changes can be146
made by updating the database schema or software). However, on a blockchain, it is much more147
difficult to change data or update the ‘database’ software. Organizations need to understand the148
extreme difficulty in changing anything that is already on the blockchain, and that changes to the149
blockchain software may cause forking of the blockchain. Another critical aspect of blockchain150
technology is how the participants agree that a transaction is valid. This is called “reaching151
consensus”, and there are many models for doing so, each with positives and negatives for a152
specific business case.153](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-6-320.jpg)




![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
9
1 Introduction264
Blockchains are immutable digital ledger systems implemented in a distributed fashion (i.e.,265
without a central repository) and usually without a central authority. At their most basic level,266
they enable a community of users to record transactions in a ledger that is public to that267
community, such that no transaction can be changed once published. This technology became268
widely known starting in 2008 when it was applied to enable the emergence of electronic269
currencies where digital transfers of money take place in distributed systems. It has enabled the270
success of e-commerce systems such as Bitcoin, Ethereum, Ripple, and Litecoin. Because of this,271
blockchains are often viewed as bound to Bitcoin or possibly e-currency solutions in general.272
However, the technology is more broadly useful and is available for a variety of applications.273
The numerous components of blockchain technology along with its reliance on cryptographic274
primitives and distributed systems can make it challenging to understand. However, each275
component can be described simply and used as a building block to understand the larger276
complex system. We provide an informal concise description of blockchain technology:277
Blockchains are distributed digital ledgers of cryptographically signed transactions that are278
grouped into blocks. Each block is cryptographically linked to the previous one after279
validation and undergoing a consensus decision. As new blocks are added, older blocks280
become more difficult to modify. New blocks are replicated across all copies of the ledger281
within the network, and any conflicts are resolved automatically using established rules.282
1.1 Background and History283
The core ideas behind blockchain technology emerged in 1991 when a signed chain of284
information was used as an electronic ledger for digitally signing documents in a way that could285
easily show none of the signed documents in the collection had been changed [2]. It was first286
applied to digital cash in 2008 in the initial paper describing the Bitcoin electronic cash solution,287
Bitcoin: A Peer to Peer Electronic Cash System [3], which was published pseudonymously by288
Satoshi Nakamoto. The actual author(s) and owner of the first Bitcoins remain a mystery. Since289
then, blockchain technology has become tightly linked to Bitcoin and is often assumed to be used290
for monetary transactions (although it is not restricted to simple fund transfers). Nakamoto’s291
paper contained the blueprint that most modern digital cash schemes follow, with many292
variations. Bitcoin is in fact the first of many applications or use cases for a blockchain.293
Many electronic cash schemes existed prior to Bitcoin, but none of them achieved widespread294
use. By adopting blockchain technology, Bitcoin achieved compelling capabilities that promoted295
its use. The use of a blockchain enabled Bitcoin to be implemented in a distributed fashion so296
that no single user controlled the currency and no single point of failure existed. Its primary297
benefit was to enable direct electronic financial transactions between users without the need for a298
third party. It also enabled the issuance of new currency in a fair fashion to those users299
(sometimes called miners or minters) maintaining the blockchain that, among other factors,300
enabled lower transaction costs for using the system. The payment of the mining nodes enabled301
distributed administration of the system without the need to organize those maintaining the302
system. By using a distributed blockchain and consensus-based maintenance, a self-policing303
mechanism was created that ensured that only valid transactions were added to the blockchain.304](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-11-320.jpg)


![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
12
2 Blockchain Architecture350
Blockchain systems can seem complex; however, they can be easily understood by examining351
each component technology individually. At a high level, blockchains utilize well-known352
computer science mechanisms (linked lists, distributed networking) as well as cryptographic353
primitives (hashing, digital signatures, public/private keys) mixed with financial concepts (such354
as ledgers).355
2.1 Hashes356
An important component of the blockchain technology is the use of cryptographic hash functions357
for many operations, such as hashing the content of a block. Hashing is a method of calculating a358
relatively unique fixed-size output (called a message digest, or just digest) for an input of nearly359
any size (e.g., a file, some text, or an image). Even the smallest change of input (e.g., a single bit)360
will result in a completely different output digest. Table 1 shows simple examples of this. Hash361
algorithms are designed to be one-way (known as being preimage resistant): it is computationally362
infeasible to find any input that maps to any pre-specified output. If a particular output is desired,363
many inputs must be tried by passing them through the hash function until an input is found that364
produces the desired result. Hash algorithms are also designed to be collision resistant (known as365
second preimage resistant): it is computationally infeasible to find two or more inputs that366
produce the same output.367
A hashing algorithm used in many blockchain technologies is the Secure Hash Algorithm (SHA)368
with an output size of 256 bits (SHA-256). Many computers support this algorithm in hardware,369
making it fast to compute. This algorithm has an output of 32 (8-bit) characters (shown below, in370
Table 1, as a 64-character hexadecimal string), meaning that there are 2256
≈ 1077
, or371
115,792,089,237,316,195,423,570,985,008,687,907,853,269,984,665,640,564,039,457,584,007,913,129,639,936372
possible digest values. The algorithm for SHA-256, as well as others, is specified in Federal373
Information Processing Standard (FIPS) 180-4 [4]. The NIST Secure Hashing website [5]374
contains FIPS specifications for all NIST-approved hashing algorithms.375
Table 1: Examples of Inputs and SHA-256 Digest Values376
Input Text SHA-256 Digest Value
1 0x6b86b273ff34fce19d6b804eff5a3f5747ada4eaa22f1d49c01e52ddb7875b4b
2 0xd4735e3a265e16eee03f59718b9b5d03019c07d8b6c51f90da3a666eec13ab35
Hello, World! 0xdffd6021bb2bd5b0af676290809ec3a53191dd81c7f70a4b28688a362182986f
377
Since there is an extremely large number of possible input values and a finite number of possible378
output digest values, it is possible to have a collision where hash(x) = hash(y) (i.e., the hash of379
two different inputs produces the same digest). However, it is highly unlikely for any such input380
x and y that produce the same digest to both be valid in the context of the blockchain system (in381
this case, both being valid blockchain transactions) as well as be computed reasonably close to382
each other in time. The hashing algorithm used (SHA-256) is said to be collision resistant, since383
to find a collision in SHA-256, one would have to execute the algorithm, on average, about 2128
384](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-14-320.jpg)
![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
13
times. Blockchain technologies take a list of transactions and create a hash “fingerprint” (the385
digest is the fingerprint) for the list. Anyone with the same list of transactions can generate the386
exact same fingerprint. If a single value in a transaction within the list changes, the digest for that387
block changes, making it easy to discover even minor one bit changes.388
2.2 Transactions389
A transaction is a recording of a transfer of assets (digital currency, units of inventory, etc.)390
between parties. An analog to this would be a record in a checking account for each time money391
was deposited or withdrawn. Table 2 shows a notional example of a transaction. Each block in a392
blockchain contains multiple transactions. A single transaction typically requires at least the393
following information fields, but can contain more:394
• Amount – The total amount of the digital asset to transfer.395
• Inputs – A list of the digital assets to be transferred (their total value equals the amount).396
Note that each digital asset is uniquely identified and may have different values from397
other assets. However, assets cannot be added or removed from existing digital assets.398
Instead, digital assets can be split into multiple new digital assets (each with lesser value)399
or combined to form fewer new digital assets (each with a correspondingly greater value).400
• Outputs – The accounts that will be the recipients of the digital assets. Each output401
specifies the value to be transferred to the new owner(s), the identity of the new owner(s),402
and a set of conditions the new owners must meet to receive that value. If the digital403
assets provided are more than required, the extra funds are returned to the sender (this is a404
mechanism to “make change”).405
• Transaction ID/Hash – A unique identifier for each transaction. Some blockchains use406
an ID, and others take a hash of the specific transaction as a unique identifier.407
Table 2: Example Transaction408
Input Output Amount Total
Transaction ID: 0xa1b2c3
Account A Account B 0.0321
Account C 2.5000
2.5321
409
Determining the validity of a transaction is important. Just because someone claims a transaction410
took place does not mean it really happened. Transactions are signed and can be verified with411
public/private key pairs at any time.412
2.3 Asymmetric-Key Cryptography413
A fundamental technology utilized by blockchain technologies is asymmetric-key cryptography1
414
(also referred to as public/private key cryptography). Asymmetric-key cryptography uses a pair415
1
FIPS Publication 186-4, Digital Signature Standard [6] specifies a common algorithm for digital signing used in blockchain
technologies: Elliptic Curve Digital Signature Algorithm (ECDSA).](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-15-320.jpg)



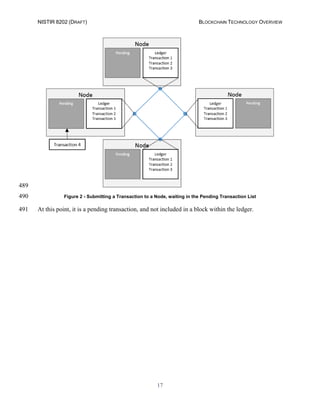










![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
28
SHA256("blockchain934224174") =693
0x0000000e2ae7e4240df80692b7e586ea7a977eacbd031819d0e603257edb3a81694
There is no shortcut to this process; mining nodes must expend computation effort, time, and695
resources to find the correct nonce value for the target.696
Once a user has performed this work, they send their block with a valid nonce to the other nodes697
in the network. The recipient nodes verify that this work was done properly, add the block to698
their copy of the blockchain, and resend the block to their peer nodes. In this manner, the new699
block gets quickly distributed throughout the network of participating nodes. Verification of the700
nonce is easy since only a single hash needs to be done to check to see if it solves the puzzle.701
The proof of work consensus model is designed for the case where there is little to no trust702
amongst users of the system. It ensures mining nodes cannot game the system3
by always being703
able to solve the puzzles and thereby control the blockchain and the transactions added to it.704
However, a major pitfall of the proof of work consensus model is its excessive use of energy in705
solving the puzzles. This is not trivial; for example, currently the Bitcoin blockchain uses more706
electricity than the entire country of Ireland, and it has been speculated that it will consume as707
much electricity as the entire country of Denmark by 2020 [7][8][9]. Software and hardware708
continually improve, with the result that puzzles can be solved more efficiently, but blockchain709
networks are growing, and the puzzle targets get harder as more mining nodes participate.710
Due to the increasing difficulty of the proof of work puzzles, it is becoming harder for any one711
computer to solve a puzzle. Therefore, mining nodes have organized themselves into “pools” or712
“collectives” whereby they collectively solve puzzles. This is because it is possible to distribute713
the work between two or more nodes across a collective to share the workload and rewards.714
Splitting the example program into quarters, each node can take an equal amount of the nonce715
value range to test:716
• Node 1: check nonce 0000000000 to 0536870911717
• Node 2: check nonce 0536870912 to 1073741823718
• Node 3: check nonce 1073741824 to 1610612735719
• Node 4: check nonce 1610612736 to 2147483647720
The following result was the first to be found to solve the puzzle:721
SHA256("blockchain1700876653") =722
0x00000003ba55d20c9cbd1b6fb34dd81c3553360ed918d07acf16dc9e75d7c7f1723
This is a completely new nonce, but one that solved the puzzle. It took 90,263,918 guesses724
(completed in 10 minutes, 14 seconds). Dividing up the work amongst many more machines725
yields much better results, as well as more consistent rewards in a proof of work model.726
3
Use the rules and procedures meant to protect the system to actually manipulate the system for a desired result.](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-30-320.jpg)
![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
29
4.2 Proof of Stake Consensus Model727
The proof of stake model is based on the idea that the more stake4
a user has in the system, the728
more likely it will want the system to succeed, and the less likely it will want to subvert it. Proof729
of stake blockchain systems use the amount of stake a user has as a determining factor for new730
block creation. The methods for how the blockchain system uses the stakes can vary – from731
random selection of staked users, to multi-round voting, to a coin aging system. Regardless of732
the exact approach, users with more stake are more likely to produce new blocks.733
With this consensus model, there is no need to perform resource intensive computations (time,734
electricity, processing power) as found in proof of work. Since this consensus method utilizes735
less resources, some blockchains have decided to forego a reward for new block creation; these736
systems are designed so that all the cryptocurrency is already distributed among users rather than737
new coins being generated at a constant pace.738
Within a proof of stake blockchain system, where the choice of block creator is a random choice739
(sometimes referred to as Chain-based proof of stake), the blockchain system will look at all740
users with stake and choose amongst them based on their stake to overall system stake ratio. So,741
if a user had 42% of the stake they would be chosen 42% of the time; those with 1% would be742
chosen 1% of the time.743
When the choice of block creator is a multi-round voting system (sometime referred to as744
Byzantine Fault Tolerance proof of stake [10]) there is added complexity. The blockchain system745
will select several staked users to create proposed blocks. The system will then ask all staked746
users to vote for the next block. After several rounds of this voting, a new block is decided upon.747
This method allows all staked users to have a voice in the block selection process for every new748
block.749
Finally, there is a method of proof of stake which allows users to create blocks by “spending”750
aged cryptocurrency (sometimes referred to as “Coin age” proof of stake). The user’s staked751
cryptocurrency has an additional “age” property, and after a certain amount of time (such as 30752
days) the staked cryptocurrency can be “spent” and allow the user to create a new block on the753
blockchain. The “spent” cryptocurrency then has its “age” reset to 0, and it cannot be used again754
until after the requisite time has passed. This method allows for users with more stake to create755
more blocks, but to not dominate the system – since they have a cooldown timer attached to756
every cryptocurrency spent creating blocks.757
Under proof of stake systems, the “rich” can more easily stake more of the digital assets, earning758
themselves more assets; however, to obtain the majority of assets within a system in order to759
“control” it is generally cost prohibitive.760
4
Stake is an amount of cryptocurrency that the user has invested into the system, either by locking it via a special transaction
type, or by sending it to a specific address; the amount of staked cryptocurrency is generally no longer able to be spent. The
likelihood of a user creating a new block is tied to the ratio of their stake to the overall blockchain system amount of staked
cryptocurrency.](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-31-320.jpg)



![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
33
5 Forking809
Updating technology can be difficult at the best of times, such as when systems are centralized.810
When a system is comprised of many users, distributed around the world, and governed by the811
consensus of the users, it becomes extremely difficult. Changes to the blockchain software and812
implementation are called forks.813
5.1 Soft Forks814
A soft fork is a change to the technology that will not completely prevent users who do not adopt815
the change (e.g., an update to the latest version) from using the changed blockchain system.816
Since non-updated nodes will recognize the new blocks as valid, a soft fork can be backwards817
compatible, only requiring that a majority of nodes upgrade to enforce the new soft fork rules.818
An example of a soft fork occurred on Bitcoin when a new consensus rule was added to support819
escrow5
and time-locked refunds. In 2014, a proposal was made to repurpose an operation code820
that performed no operation (OP_NOP2) to CHECKLOCKTIMEVERIFY, which allows a821
transaction output to be made unspendable at a point in the future [11]. For future clients that822
implement this change, the blockchain interpreter will perform this new operation, but for clients823
that do not support the change, the script is still valid, and execution will continue as if a NOP 6
824
had been executed.825
5.2 Hard Forks826
A hard fork is a change to the technology that will completely prevent users who do not adopt it827
from using the changed blockchain system. Under a hard fork, the blockchain protocol will828
change in a manner that requires users to either upgrade to stay with the developer’s “main fork”829
or to continue on the original path without the upgrades. Users on different hard forks cannot830
interact with one another. Any change to the block structure, such as the hashing algorithm831
choice, will require a hard fork.832
A well-known example of a hard fork is from Ethereum. In 2016, a smart contract was833
constructed on Ethereum called the Decentralized Autonomous Organization (DAO). Due to834
flaws in how the smart contract was constructed, an attacker extracted Ether, the cryptocurrency835
used by Ethereum, essentially allowing theft of $50 million [12]. A hard fork proposal was voted836
on by Ether holders, and 89 percent agreed to hard fork and create a new version of the837
blockchain that returned the stolen funds.838
With cryptocurrencies, if there is a hard fork and the blockchain splits, the coins each person has839
at the time of the split will be mirrored on each fork. If all the activity moves to the new chain,840
the old one will eventually not be used. In the case of the Ethereum hard fork, the vast majority841
5
Funds placed into a third party to be disseminated based on conditions (via multi-signature transactions)
6
NOP meaning No Operation](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-35-320.jpg)
![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
34
of support moved to the new fork, and the old fork was renamed to Ethereum Classic, which has842
only a fraction of the original user base.843
5.3 Cryptographic Changes and Forks844
If flaws are found in the cryptographic technologies for a blockchain application, the only845
solution may be to create a hard fork, depending on the significance of the flaw. For example, if846
a flaw was found in the underlying algorithms, there could be a fork requiring all future clients to847
use a stronger algorithm. Until more than 50 percent of the network is on the new software848
version, the vulnerability could still exist. Switching to a new hashing algorithm could pose a849
significant practical problem because it could invalidate all existing specialized mining850
hardware.851
Hypothetically, if SHA-256 were discovered to have a flaw, there would need to be a hard fork852
to migrate to a new hash algorithm. The block that switches over to the new hash algorithm853
would “lock” all previous blocks into SHA-256 (for verification), and all new blocks would need854
to utilize the new hashing algorithm. For example, Bitcoin uses SHA-256 hashes, which is easy855
and fast to implement in hardware ASICs. Other cryptocurrencies such as Ethereum use Keccak-856
256 (based on SHA-3) [13], while Litecoin uses the scrypt hashing algorithm.857
One possibility for the need to change cryptographic features present in a blockchain system858
would be the development of a practical quantum computer system, which would be capable of859
greatly weakening (and in some cases, rendering useless) existing cryptographic algorithms.860
NIST Internal Report (NISTIR) 8105, Report on Post-Quantum Cryptography [14] provides a861
table describing the impact of quantum computing on common cryptographic algorithms. Table862
3 replicates this table.863
Table 3: Impact of Quantum Computing on Common Cryptographic Algorithms864
Cryptographic Algorithm Type Purpose Impact from Large-Scale
Quantum Computer
AES Symmetric key Encryption Larger key sizes needed
SHA-2, SHA-3 N/A Hash functions Larger output needed
RSA Public key Signatures, key establishment No longer secure
ECDSA, ECDH (Elliptic Curve
Cryptography)
Public key Signatures, key exchange No longer secure
DSA (Finite Field
Cryptography)
Public key Signatures, key exchange No longer secure
865
The cryptographic algorithms utilized within most blockchain technologies for public/private key866
pairs will need to be replaced if a powerful quantum computer become a reality. This is because867
algorithms that rely on the computational complexity of integer factorization (such as RSA) or868
work on solving discrete logarithms (such as DSA and Diffie-Hellman) are very susceptible to869
quantum computing. The hashing algorithms and Merkle trees that are the other basis for870
blockchains are much less susceptible to quantum computing attacks, but are still weakened871
when quantum computers become a reality.872](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-36-320.jpg)
![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
35
6 Smart Contracts873
A smart contract is a collection of code and data (sometimes referred to as functions and state)874
that is deployed to a blockchain (e.g., Ethereum). Future transactions sent to the blockchain can875
then send data to public methods offered by the smart contract. The contract executes the876
appropriate method with the user provided data to perform a service. The code, being on the877
blockchain, is immutable and therefore can be used (among other purposes) as a trusted third878
party for financial transactions that are more complex than simply sending funds between879
accounts. A smart contract can perform calculations, store information, and automatically send880
funds to other accounts. It doesn’t necessarily even have to perform a financial function. For881
example, the authors of this document have created smart contracts that publicly generate882
trustworthy random numbers [15].883
In practice, all mining nodes execute the smart contract code simultaneously when mining new884
blocks. Thus, smart contract execution may be more expensive than the simple fund transfers in885
other blockchain based cryptocurrencies. Often, the user issuing a transaction to a smart contract886
will have to pay for the cost of the code execution in addition to the normal transaction fees.887
There is a limit on how much execution time can be consumed by a call to a smart contract. If888
this limit is exceeded, execution stops and the transaction is discarded. This mechanism not only889
rewards the miners for executing the smart contract code, but also prevents malicious users from890
deploying and then accessing smart contracts that will perform a denial of service on the mining891
nodes by consuming all resources (e.g., using infinite loops).892](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-37-320.jpg)

![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
37
Another important consideration is having a tamper-evident design. If a malicious mining node930
tried to change a block, they might for example forge a transaction to give themselves money.931
Would this kind of change be detected? Are there systems in place to determine what happened?932
Immutability is important and is one of the founding principles of the blockchain. In general,933
malicious transactions that enter the blockchain cannot be undone, even if they are identified. To934
do so requires rewriting published blocks which essentially forks the blockchain and requires the935
approval of the majority of mining nodes. In a permissioned system this can be easier since the936
mining nodes are generally a trusted set that have a special relationship. It is much more difficult,937
but technically possible, for a permissionless systems such as Bitcoin.938
7.1.2 Use Case Examples939
The following sections depict examples of use cases (not an exhaustive list). Inclusion or940
exclusion from this section does not validate or invalidate any potential use case.941
Banking942
Suppose a number of banks want to keep a private, distributed ledger available to only the943
participating banks. This would provide the ability to record transactions from each bank in a944
way that is visible to the participants, but not the public. However, to do this as a private945
blockchain (to avoid having to use an expensive proof of work algorithm), each bank takes turns946
signing the blocks under a distributed consensus algorithm such as Byzantine Paxos [16].947
There are a few interesting considerations when using a private blockchain with few participants,948
such as the ability to overcome its immutability. If there was some major disaster or exception949
situation, the banks could coordinate to roll back the blockchain and write a different transaction.950
Additionally, the transactions would not be anonymous because a banking ID would be needed951
to join.952
Supply Chain953
Recording the transfer of physical goods from a producer, to a shipping terminal, to a ship, to a954
cargo train, to a delivery truck and to a store is an appealing application of blockchain955
technology. A blockchain could play a crucial role in trust and transparency with end customers.956
The blockchain could also be used to monitor supplier actions. Suppliers can record the product957
produced (such as X number of widgets on a certain date) in a way that other viewers of the958
blockchain can verify. With a blockchain, it is possible for warehouses to manage logistics959
efficiently by avoiding overstocking.960
Insurance and Healthcare961
Whenever someone visits a care provider, a myriad of transactions take place behind the scenes.962
Administrative transactions from nurses, doctors, staff, medical providers, insurance companies,963
and pharmacies could all be written to a blockchain. Transactions (such as checking benefits,964
eligibility, coverage, and the available medicine supply) could be read from the blockchain.965](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-39-320.jpg)
![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
38
Currently, records of these transactions reside in disparate systems, sharing results at the end of966
an (often manual) process.967
7.2 Permissionless968
Permissionless blockchains are decentralized platforms with no central authority and are open to969
participation without users requesting access. Permissionless blockchains often utilize a970
consensus method that requires more than a trivial effort in order to prevent bad users from971
easily subverting the system. Such consensus methods include proof of work and proof of stake972
methods. The reason a permissionless blockchain can work is because there are rewards for973
participating in the process.974
7.2.1 Application Considerations for Permissionless Blockchains975
When deciding whether to utilize a permissionless blockchain, one must consider whether the976
application needs the following qualities:977
• Public facing data – Since permissionless ledgers tend to allow anyone to inspect and978
contribute to the blockchain, the data is generally public. Does the data for the application979
need to be available to everyone? Is there any harm to having public data?980
• Full transactional history – Due to the open nature of data for these systems, anyone981
can track the transfer of assets between accounts, from the creation of assets, to each982
transaction in progress.983
• False data attempts – Since anyone could contribute to the blockchain, some could984
submit false data to the blockchain, mimicking data from valid sources. Is there a way for985
the application to ensure it only gathers data from reputable sources?986
• Data immutability – Many applications follow the “CRUD” (create, read, update,987
delete) functions for data. With a blockchain, there is only “CR” (create, read). There are988
methods that can be employed to “deprecate” older data if a newer version is found, but989
there is no removal process for the original data. Can the application handle (possibly990
outdated) immutable data? Does the data lend itself to being immutable?991
• Transactional throughput capacity – Currently transactions on blockchains are not992
conducted at the same pace as other solutions (e.g., blocks are not added quickly enough),993
so some slowdown while waiting for data to be posted may be incurred. Can the994
application handle that?995
7.2.2 Use Case Examples996
The following sections depict examples of use cases (not an exhaustive list). Inclusion or997
exclusion from this section does not validate or invalidate any potential use case.998
Trusted Timestamping999
Trusted timestamping is a way to prove that certain information existed at a given point [17].1000
The use of a blockchain allows a party to prove they had access to a piece of data in a way that1001
cannot be repudiated. For example, if a person wanted to prove they had possession of a file,1002](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-40-320.jpg)
![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
39
they could hash the file and record the hash value as an annotation to a transaction. Then, if he or1003
she ever needs to prove possession of the file, it is recorded publicly.1004
Other use cases of leveraging timestamping on a blockchain include proving a task was1005
completed on a certain date, proving possession of a photo, proving a contract was signed, or1006
proving events occurred.1007
Energy Industry1008
Another blockchain application is the recording of autonomous, machine-to-machine1009
transactions regarding electricity use [18]. This would take advantage of digital platform1010
opportunities and changing business models for tracing transactions on the smart grid. One1011
notable use case in the energy industry for the blockchain is in recording certificates. There are1012
different power plants generating energy and creating certificates that attest to the amount of1013
energy produced for subsequent exchange. Currently, there are problems such as emission1014
certificates being spent twice, as well as the need to address regulatory challenges and provide1015
more uniform access for everybody in the market. A blockchain can effectively track the1016
issuance and spending of these energy certificates.1017
Another example of how blockchains are applicable in the energy industry is in the trading of1018
excess renewable energy. Buildings can be wired with devices measuring energy usage and1019
recording it to a blockchain, enabling excess energy to be sold and bought on a market.1020](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-41-320.jpg)
![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
40
8 Blockchain Platforms1021
Many blockchains are in use today, primarily for digital cash solutions. This section discusses a1022
selection of blockchain platforms to highlight the technical differences and approaches being1023
used. This is not an endorsement of any of these platforms, nor should it be construed as a list of1024
the most popular or important platforms.7
1025
8.1 Cryptocurrencies1026
Numerous applications of blockchain technologies are primarily oriented around moving1027
currency from one account to another. This section profiles several examples of such blockchain1028
applications.1029
8.1.1 Bitcoin (BTC)1030
Bitcoin is a digital cash system that has been previously discussed as the pioneer in using a1031
blockchain. New blocks are created approximately once every 10 minutes using SHA-2561032
hashing to link them together. It is a proof of work system where mining nodes must find a1033
nonce to include in their block such that the hash of the block is less than some predetermined1034
difficulty value. The difficulty is adjusted up or down to attempt to achieve the 10-minute target1035
for block creation. Early in Bitcoin’s history, individual computers could mine and publish1036
blocks; currently Bitcoin requires specialized hardware, large datacenters, or many individuals1037
working together in a mining pool to win the competition to publish blocks.1038
With Bitcoin, the paying of transaction fees is technically optional since the mining nodes get1039
most of their funds through the publication of blocks. This fee is designed to be a small fee for1040
each transaction, but it can and has become large due to a substantial backlog of pending1041
transactions. Paying a higher transaction fee can give a transaction a greater priority for getting1042
added to the blockchain. Initially, mining nodes got 50 Bitcoin for each block, and only half of1043
that after a certain number of blocks. For example, the reward for mining a block was 12.51044
Bitcoins in July 2016. Per the Bitcoin protocol, this reward will halve every 210,000 blocks1045
(around four years) and will decrease to zero once 21 million Bitcoins have been produced [19].1046
Bitcoin mining will continue at that point, but the reward will be completely derived from1047
transaction fees.1048
One last technical note of interest is that each Bitcoin transaction contains code written in a1049
language called Script. This code represents a simple program that specifies the transaction. It1050
contains no loops and is highly restricted with regards to functionality (i.e., it is not Turing1051
complete8
). Bitcoin transactions today use only a small portion of the available features of Script.1052
In practice, most Bitcoin transactions use one of just a few templates of code for the movement1053
of funds between parties.1054
7
The website Map of Coins (http://mapofcoins.com/) provides a good example of a number of blockchain systems, but is still far
from being a complete listing
8
A Turing complete system (computer system, programming language, etc.) can be used for any algorithm, regardless of
complexity, to find a solution.](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-42-320.jpg)
![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
41
8.1.2 Bitcoin Cash (BCC)1055
In July 2017, approximately 80 to 90 percent of the Bitcoin computing power voted to1056
incorporate Segregated Witness (SegWit, where transactions are split into two segments:1057
transactional data, and signature data), which made it possible to reduce the amount of data being1058
verified in each block. Signature data can account for up to 65 percent of a transaction block, so1059
a change in how signatures are implemented could be useful. When SegWit was activated, it1060
caused a hard fork, and all the mining nodes and users who did not want to change started calling1061
the original Bitcoin blockchain Bitcoin Cash (BCC). Technically, Bitcoin is a fork and Bitcoin1062
Cash is the original blockchain. When the hard fork occurred, people had access to the same1063
amount of coins on Bitcoin and Bitcoin Cash.1064
8.1.3 Litecoin (LTC)1065
Litecoin is inspired by and is very similar to Bitcoin, but aims to provide faster confirmation1066
times. Litecoin has implemented SegWit, splitting transactions into two segments and hiding an1067
increased block size [20]. The “witness” signature is separated from the Merkle tree. Another1068
difference between Bitcoin and Litecoin is Litecoin uses the Scrypt algorithm for hashing instead1069
of SHA-256. The Scrypt algorithm is more difficult to solve than SHA-256 because it uses more1070
memory, which makes development of custom application-specific integrated circuits (ASICs)1071
more difficult. There is a larger maximum number of coins which can be mined (84 million1072
Litecoins). Litecoin is a complement to Bitcoin, with higher transaction volumes, and not1073
designed to replace it [21].1074
8.1.4 Ethereum (ETH)1075
Ethereum is a blockchain platform focused on providing smart contracts. Smart contracts are1076
programs that exist on the blockchain that can be accessed by Ethereum users. They can both1077
receive and send funds while performing arbitrary computation. A properly designed contract1078
can act as a trusted third party in financial transactions since its code is both public and1079
immutable. Ethereum’s transaction programming language is Turing complete. Mining nodes1080
receive funds through mining and transaction fees.1081
Ethereum also has a concept called “gas” used to power the transactional computations (and is1082
generally around 1/100,000 of an Ether). Every transaction consumes gas as it executes, and the1083
originator of a particular transaction must pay sufficient gas, or the execution of the transaction1084
aborts. There is a maximum gas limit per smart contract (currently three million gas) to prevent1085
computationally expensive programs from being submitted to the Ethereum mining nodes. This1086
is because all mining nodes must execute the transactions in parallel [22].1087
The submission of a transaction to an Ethereum contract causes a program to be run in parallel1088
on the mining nodes’ computers. The resulting state of the contract is stored on the blockchain1089
by the user that publishes the next block.1090
8.1.5 Ethereum Classic (ETC)1091
Ethereum Classic was created when Ethereum hard forked after the DAO hack [12]. An attacker1092
had drained approximately $50 million, and the Ethereum Foundation created a hard fork to1093](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-43-320.jpg)
![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
42
move the stolen funds back to a state before the attack took place. Users who owned Ethereum1094
before the DAO hard fork had the same amount of Ethereum Classic (ETC) after the fork. The1095
reason it exists is because a number of users of the Ethereum blockchain rejected the fork for1096
philosophical reasons [23], including the principle that the blockchain cannot be changed, and1097
decided to keep using the unforked Ethereum blockchain. The mining and software is largely the1098
same between Ethereum and Ethereum Classic, with the difference being that Ethereum is a fork1099
and the more popular chain.1100
8.1.6 Dash (DASH)1101
Dash is a cryptocurrency built with the objective of providing faster transactions. It uses a1102
“masternode” network and can make transactions within four seconds [24]. Dash uses1103
deterministic ordering for the masternodes by using the hash and proof of work for each block.1104
Interestingly, becoming a masternode requires 1000 Dash collateral, which makes it very1105
expensive (nearly impossible) to control more than 50 percent of the network [25]. The collateral1106
requirement for masternodes seeks to alleviate the problems of untrusted nodes in a peer-to-peer1107
network.1108
Dash uses a different hashing algorithm than most, x11. This consists of using all 11 SHA-31109
contestant algorithms (including BLAKE, JH, Keccak, and Skein), with each hash being1110
submitted to the next algorithm in the chain [25]. The reasoning is that multiple algorithm use1111
makes it harder for an ASIC to be created that targets solving these hashes in hardware.1112
8.1.7 Ripple (XRP)1113
Ripple is the name of both a cryptocurrency and the payment network on which it is transferred.1114
The goal of Ripple is to build on the approach of Bitcoin and to connect different payment1115
systems together. It has a fixed supply of 100 billion XRP, with half of them designated for1116
circulation [26]. Ripple clients do not need to download the entire blockchain, making it easy for1117
clients to join in seconds. Additionally, there is no mining reward for running a server because1118
each transaction costs a small amount of Ripple, similar to Ethereum gas. Therefore, there are no1119
mining nodes or mining pools; instead, about one-thousandth of a cent from each transaction is1120
destroyed [27]. Ripple is not designed with explicit goals for anonymity, but it does have features1121
providing privacy, such as using proxied gateway payments.1122
8.2 Hyperledger1123
Hyperledger is a group of projects aiming to create enterprise-grade, open-source distributed1124
ledgers [28]. The Hyperledger Project is supported and hosted by the Linux Foundation.1125
Although hosted by the Linux Foundation, each project was developed and contributed by1126
different sources. There are several projects within the Hyperledger Project, each one providing a1127
blockchain platform to solve specific problems.1128
8.2.1 Hyperledger Fabric1129
This is a modular, permissioned blockchain that can run smart contracts (called chaincode) [29].1130
The Fabric blockchain was initially contributed to the Hyperledger Project by Digital Asset and1131
IBM.1132](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-44-320.jpg)
![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
43
8.2.2 Hyperledger Sawtooth1133
This is a modular distributed ledger using proof of elapsed time as the consensus protocol. In a1134
proof of elapsed time system, every participant requests a “wait time” from a hardware enclave (a1135
trusted and secure feature available on some hardware), which distributes wait times randomly.1136
Whichever participant was awarded the shortest time creates the next block in the chain. The use1137
of Hyperledger Sawtooth is tightly coupled to hardware that supports the hardware enclave1138
feature. Hyperledger Sawtooth was initially contributed by Intel.1139
8.2.3 Hyperledger Iroha1140
This acts as an Identity/Know Your Customer (KYC) service using blockchain technologies,1141
which allows institutions to share data and manage identity. Hyperledger Iroha was initially1142
contributed by Soramitsu, Hitachi, NTT Data, and Colu.1143
8.2.4 Hyperledger Burrow1144
Hyperledger Burrow is a permissioned smart contract-enabled blockchain platform. It accepts1145
Ethereum-based smart contract code. Hyperledger Burrow was originally contributed by Monax1146
and co-sponsored by Intel.1147
8.2.5 Hyperledger Indy1148
This is an independent identity platform providing provenance for trust transactions and1149
accountability. It supports user-controlled exchanges of verifiable claims about identifying1150
information, as well as revocation models. It supports three important privacy features:1151
Decentralized Identifiers (DIDs), pointers to off-ledger sources so that no personal data is written1152
to the ledger, and zero-knowledge-proofs. The Indy code is being contributed to the Hyperledger1153
Project by the Sovrin Foundation.1154
8.3 MultiChain1155
MultiChain is an open source blockchain platform that enables anyone to setup, configure, and1156
deploy a private, semi-private, or public blockchain. MultiChain is a fork of Bitcoin, but with1157
many modifications. Users can determine whether there is to be an associated cryptocurrency, as1158
well as the consensus method (round robin or proof of work). In the default configuration,1159
MultiChain is a private, permissioned-based blockchain using round-robin consensus. This1160
means that the first person to set up the blockchain acts as an administrator and initial node; all1161
additional users must direct their MultiChain blockchain clients to this first node, and the1162
administrator must grant them permissions.1163
MultiChain Streams [30] are a unique feature; they are described as “shared immutable key-1164
value time series databases” which are stored on a blockchain.1165](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-45-320.jpg)
![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
44
9 Blockchain Limitations and Misconceptions1166
There is a tendency to overhype and overuse most nascent technology. Many projects will1167
attempt to incorporate the technology, even if it is unnecessary. This stems from the technology1168
being relatively new and not well understood, or the technology being surrounded by1169
misconceptions. Blockchain technology has not been immune. This section highlights some of1170
the limitations and misconceptions of blockchain technology.1171
9.1 Blockchain Control1172
A common misconception is that permissionless blockchains are systems without control and1173
ownership. The phrase “no one controls a blockchain!” is often exclaimed; however, while no1174
user, government, or country controls a blockchain, there is still a group of core developers who1175
are responsible for the system’s development. These developers may act in the interest of the1176
community at large, but they still maintain some level of control. For example, in 2013 Bitcoin1177
developers released a new version of the most popular Bitcoin client which introduced a flaw1178
and started two competing chains-of-blocks. The developers had to decide to either keep the new1179
version (which had not yet been adopted by everyone) or revert to the old version [31]. Either1180
choice would result in one chain being discarded—and some people’s monetary transactions1181
becoming invalid.1182
The developers made a choice, reverted to the old version, and successfully controlled the1183
progress of the Bitcoin blockchain. This example was an unintentional fork; however, developers1184
can purposely build new clients, and with enough adoption from the user base, a successful fork1185
can be created. These forks are often discussed at length and given a long adoption period before1186
being made mandatory to continue recording transactions on the new “main” fork.1187
The phrase “no one controls a blockchain!” would be better stated as, “no one controls with1188
whom and when you can perform transactations, within the rules of the blockchain system.”1189
9.2 Malicious Users1190
While the blockchain system can enforce transaction rules and specifications, it cannot enforce a1191
code of conduct. This is problematic in permissionless blockchain systems, since users are1192
pseudonymous and there is not a one-to-one mapping between blockchain nodes and users of the1193
system. Permissionless blockchains provide incentive (e.g., a cryptocurrency) to motivate users1194
to act fairly; however, some may choose to act maliciously if that provides greater incentives.1195
The largest problem for malicious users is getting enough power (be it a stake in the system,1196
processing power, etc.) to cause damage. Once a large enough malicious collusion is created,1197
malicious mining actions can include:1198
• Ignoring transactions from specific users, nodes, or even entire countries.1199
• Creating an altered, alternative chain in secret, then submitting it once the alternative1200
chain is longer than the real chain. The honest nodes will switch to the chain that has the1201
most “work” done (per the blockchain protocol). This could attack the concept of1202
“immutability” within a blockchain system [32].1203](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-46-320.jpg)
![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
45
• Refusing to transmit blocks to other nodes, essentially disrupting the distribution of1204
information.1205
While malicious users can be annoyances and create short-term harm, blockchains can perform1206
hard forks to combat them. Whether damages done (money lost) would be reversed would be up1207
to the developers and users of the blockchain system.1208
9.3 No Trust1209
Another common misinterpretation comes from people hearing that there is no “trusted third1210
party” in a blockchain and assuming blockchain systems are “trustless” environments. While1211
there is no trusted third party certifying transactions in permissionless blockchain systems (in1212
permissioned systems it is less clear, as administrators of those systems act as an administrator of1213
trust by granting users admission and permissions), there is still a great deal of trust needed to1214
work within a blockchain system:1215
• There is trust in the cryptographic technologies utilized. For example, cryptographic1216
algorithms or implementations can have flaws, and smart contracts can have unintended1217
loopholes and flaws.1218
• There is trust in the developers of the software to produce software that is as bug-free as1219
possible.1220
• There is trust that most users of the blockchain are not colluding in secret. If a single1221
group or individual can control more than 50 percent of all block creation power, it is1222
possible to subvert a permissionless blockchain system. However, generally obtaining the1223
necessary computational power is prohibitively expensive.1224
• There is trust that nodes are accepting and processing transactions fairly.1225
9.4 Resource Usage1226
Blockchain technology has enabled a worldwide network of value where every transaction is1227
verified and the blockchain is kept in sync amongst a multitude of users. For blockchain systems1228
utilizing proof of work, this means there is a large number of users churning away processing1229
time and consuming a lot of electricity. A proof of work method is a great solution for “hard to1230
create, easy to verify” proofs, but as discussed in Section 4.1, it requires significant resource1231
usage.1232
An additional strain on resources occurs whenever a new full node is created; the node must1233
obtain (usually through downloading) most of or all the blockchain data (Bitcoin’s blockchain1234
data is over 100 gigabytes in size as of this writing) [33]. This process uses a lot of network1235
bandwidth.1236
Blockchains are often compared to databases, and while they both store information, blockchains1237
have limits on the amount of data that can be stored and are not meant to be a general storage1238
medium. In order to quickly calculate hashes on transactions and distribute transactions amongst1239
the network, transactions need to be relatively small. Large amounts of data are usually stored1240
“off chain,” with “pointers/references” or hashes of the data stored within the blockchain itself.1241
Blockchains also benefit from data being immutable, which is not a trait general purpose data1242
usually needs.1243](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-47-320.jpg)









![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
55
Appendix C—References1317
[1] Clarke, A.C., “Hazards of Prophecy: The Failure of Imagination,” from Profiles of
the Future: An Inquiry into the Limits of the Possible, 1962.
[2] Narayanan, A., Bonneau, J., Felten, E., Miller, A., and Goldfede, S., Bitcoin and
Cryptocurrency Technologies: A Comprehensive Introduction, Princeton
University Press, 2016.
[3] Nakamoto, S., “Bitcoin: A Peer-to-Peer Electronic Cash System,” 2008.
https://bitcoin.org/bitcoin.pdf
[4] National Institute of Standards and Technology (NIST), Federal Information
Processing Standards (FIPS) Publication 180-4, Secure Hash Standard (SHS),
August 2015. https://doi.org/10.6028/NIST.FIPS.180-4
[5] National Institute of Standards and Technology (NIST), Secure Hashing website,
https://csrc.nist.gov/projects/hash-functions
[6] National Institute of Standards and Technology (NIST), Federal Information
Processing Standards (FIPS) Publication 186-4, Digital Signature Standard, July
2013. https://doi.org/10.6028/NIST.FIPS.186-4
[7] Deetman, S., “Bitcoin Could Consume as Much Electricity as Denmark by 2020,”
Motherboard, March 29, 2016.
https://motherboard.vice.com/en_us/article/bitcoin-could-consume-as-much-
electricity-as-denmark-by-2020
[8] Hern, A., “Bitcoin mining consumes more electricity a year than Ireland,” The
Guardian, November 27, 2017.
https://www.theguardian.com/technology/2017/nov/27/bitcoin-mining-consumes-
electricity-ireland
[9] Power Compare, https://powercompare.co.uk/bitcoin/
[10] Bahsoun, J.P., Guerraoui, R., and Shoker, A., “Making BFT Protocols Really
Adaptive,” 2015 IEEE International Parallel and Distributed Processing
Symposium, Hyderabad, India, pp. 904-913, 2015.
https://doi.org/10.1109/IPDPS.2015.21
[11] Todd, P., Bitcoin Improvement Proposal (BIP) 65,
“OP_CHECKLOCKTIMEVERIFY,” October 1, 2014.
https://github.com/bitcoin/bips/blob/master/bip-0065.mediawiki
[12] Wong, J. and Kar, I., “Everything you need to know about the Ethereum ‘hard
fork,’” Quartz Media, July 18, 2016. https://qz.com/730004/everything-you-need-
to-know-about-the-ethereum-hard-fork/
[13] National Institute of Standards and Technology (NIST), Federal Information
Processing Standards (FIPS) Publication 202, SHA-3 Standard: Permutation-
Based Hash and Extendable-Output Functions, August 2015.
https://doi.org/10.6028/NIST.FIPS.202](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-57-320.jpg)
![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
56
[14] Chen, L., Jordan, S., Liu, Y.-K., Moody, D., Peralta, R., Perlner, R., and Smith-
Tone, D., National Institute of Standards and Technology (NIST), NIST Internal
Report (NISTIR) 8105, Report on Post-Quantum Cryptography, April 2016.
https://doi.org/10.6028/NIST.IR.8105
[15] Mell, P., Kelsey, J., and Shook, J., “Cryptocurrency Smart Contracts for
Distributed Consensus of Public Randomness.” October 7, 2017.
https://doi.org/10.1007/978-3-319-69084-1_31
[16] Lamport, L., “Leaderless Byzantine Paxos,” Distributed Computing: 25th
International Symposium: DISC 2011, p. 141-142, December 27, 2011.
https://www.microsoft.com/en-us/research/publication/leaderless-byzantine-paxos
[17] Gipp, B., Meuschke, N., and Gernandt, A., “Decentralized Trusted Timestamping
using the Crypto Currency Bitcoin,” in Proceedings of the iConference 2015,
Newport Beach, California, 2015.
[18] Mattila, J., Seppälä, T., Naucler, C., Stahl, R., Tikkanen, M., Bådenlid, A., and
Seppälä, J., The Research Institute of the Finnish Economy (ETLA) Working
Papers No. 43, “Industrial Blockchain Platforms: An Exercise in Use Case
Development in the Energy Industry,” The Research Institute of the Finnish
Economy, October 11, 2016. https://www.etla.fi/wp-content/uploads/ETLA-
Working-Papers-43.pdf
[19] Donnelly, J., “What is the 'Halving'? A Primer to Bitcoin's Big Mining Change,”
CoinDesk, June 12, 2016. https://www.coindesk.com/making-sense-bitcoins-
halving/
[20] Hertig, A., “Litecoin’s SegWit Activation: Why it Matters and What’s Next,”
CoinDesk, April 26, 2017. https://www.coindesk.com/litecoins-segwit-activation-
why-it-matters-and-whats-next/
[21] Litecoin Project. https://litecoin.org/
[22] Wood, G., “Ethereum: A Secure Decentralised Generalised Transaction Ledger.”
https://bravenewcoin.com/assets/Whitepapers/Ethereum-A-Secure-Decentralised-
Generalised-Transaction-Ledger-Yellow-Paper.pdf
[23] Pearson, J., “The Ethereum Hard Fork Spawned a Shaky Rebellion,”
Motherboard, July 27, 2016. https://motherboard.vice.com/en_us/article/the-
ethereum-hard-fork-spawned-a-shaky-rebellion-ethereum-classic-etc-eth
[24] “What Is Dash?”, WeUseCoins. https://www.weusecoins.com/what-is-dash/
[25] Duffield, E. and Diaz, D., “Dash: A Privacy-Centric Crypto-Currency.”
https://github.com/dashpay/dash/wiki/Whitepaper
[26] “Introduction to Ripple for Bitcoiners,” last modified December 10, 2013.
https://wiki.ripple.com/Introduction_to_Ripple_for_Bitcoiners
[27] Brown, A., “10 things you need to know about Ripple,” CoinDesk, May 17, 2013.
https://www.coindesk.com/10-things-you-need-to-know-about-ripple/](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-58-320.jpg)
![NISTIR 8202 (DRAFT) BLOCKCHAIN TECHNOLOGY OVERVIEW
57
[28] “Hyperledger Business Blockchain Technologies,” The Linux Foundation.
https://www.hyperledger.org/projects
[29] Cachin, C., “Architecture of the Hyperledger blockchain fabric,” in Workshop on
Distributed Cryptocurrencies and Consensus Ledgers, July 2016.
[30] Greenspan, G., “Introducing MultiChain Streams,” MultiChain, September 15,
2016. http://www.multichain.com/blog/2016/09/introducing-multichain-streams/
[31] Narayanan, A., “Analyzing the 2013 Bitcoin fork: centralized decision-making
saved the day,” MultiChain, July 28, 2015. https://freedom-to-
tinker.com/2015/07/28/analyzing-the-2013-bitcoin-fork-centralized-decision-
making-saved-the-day
[32] Greenspan, G., “The Blockchain Immutability Myth,” MultiChain, May 4, 2017.
https://www.multichain.com/blog/2017/05/blockchain-immutability-myth/
[33] “Bitcoin blockchain size reaches 100 GB,” Coinfox, December 19, 2016.
http://www.coinfox.info/news/6700-bitcoin-blockchain-size-reaches-100-gb
1318](https://image.slidesharecdn.com/draftnistir8202-180205204035/85/Draft-NISTIR-8202-59-320.jpg)