GDPR and Blockchain
- 1. General Data Protection Regulation (GDPR) and Blockchain Salman Baset 1
- 2. Outline • GDPR and blockchain - summary • GDPR • What is GDPR? • Who are the actors? • What is personal data? • What are rights of a person? • What are the responsibilities of a controller? • Myths about GDPR • GDPR in action • Blockchain • What is blockchain? • Bitcoin – what is it and how people use it • Who is the data controller in bitcoin? • Types of blockchain • Properties of blockchain that are challenging for GDPR • Permissioned private blockchains and GDPR • GDPR and Blockchain • Possible approaches and their pitfalls 2
- 3. Disclaimer • General Data Protection Regulation (GDPR) is a law. • I am not a lawyer; I am a security professional who has applied GDPR in permissioned private blockchains. • I am involved in various open source blockchain initiatives such as Hyperledger. 3
- 4. GDPR and Blockchain* GDPR compliance is not about the technology, it is about how the technology is used Just like there is no GDPR-compliant Internet. Or there is no GDPR-compliant Artificial Intelligence. Similarly, there is no such thing as GDPR-compliant blockchain technology. There are only GDPR-compliant use cases and applications. The general approach for a use or an application is to avoid storing personal data on blockchain. https://www.eublockchainforum.eu/sites/default/files/reports/20181016_report_gdpr.pdf?width=1024&height=800&iframe=true 4
- 5. What is GDPR? • A law that regulates the processing by an individual, a company, or an organization of personal data relating to individuals in the EU+. https://www.bbc.com/news/world-middle-east-24367705 EU has 28 member states • Switzerland is not a EU member • Norway is not a EU member • Brexit (United Kingdom) and GDPR? Affects every sector, from healthcare, to Internet services, to banking, and beyond. Individuals: applies to EU citizens as well as non-citizens in EU. GDPR came into effect on May 25, 2018. GDPR has 99 Articles and 173 recitals. + https://ec.europa.eu/info/law/law-topic/data-protection/reform/what-does-general-data-protection-regulation-gdpr-govern_en 5
- 6. Who are the actors in GDPR? Data subject. Article 4(1). “‘person data’ means any information relating to an identified or identifiable natural person (‘data subject’)” Example: you S C P Data controller. Article 4(7). … “determines the purpose and means of the processing of personal data”… Example: University is a data controller. Data processor. Article 4(8). “ ‘processor’ means a natural or legal person, public authority, agency or other body which processes personal data on behalf of the controller.” Example: University email service provided by a cloud service provider. DPO Data protection officer. Article 37-39. appointed by a controller and a processor to advise employees and monitor compliance Example: University privacy officer SA Supervisory authority. Article 4(21) and Article 51. An EU country-specific authority for monitoring compliance to GDPR DPB Data Protection Board. Article 68. Ensure consistent application of GDPR. monitor companycountryEU 6
- 7. What is personal data? • Some things are obvious • Name • Biometric data • Racial or ethnic origin • Religious or political beliefs • Health data • Sex life and sexual orientation • Some things are not so obvious • IP address • Cookie ID • Employment and education history 7
- 8. What are the rights of a data subject? Articles 12-23 Some examples in the blockchain context • Right to rectification – Article 16 • Right to be erasure – Article 17 • Right to restriction of processing – Article 18 • Right to data portability – Article 19 S 8
- 9. What are the responsibilities of data controller and processor? • Many • Security of processing – Article 32 • “Taking into account the state of the art, the costs of implementation and the nature, scope, context and purposes of processing as well as the risk of varying likelihood and severity for the rights and freedoms of natural persons, the controller and the processor shall implement appropriate technical and organisational measures to ensure a level of security appropriate to the risk, including inter alia as appropriate: • pseudonymization and encryption of data • the ability to ensure the ongoing confidentiality, integrity, availability and resilience of processing systems and services;” • Notification of a personal data breach to the supervisory authority. Article 33. 9
- 10. Where does a data controller or a processor typically find personal data? • Customer relationship management (CRM) databases • Human resource management (HRM) databases • Web server logs • Data backups / data warehouse 10
- 11. Myths about GDPR • EU personal data must reside within a data center in EU. • False • GDPR applies when a EU person visits another country • False. Law of another country applies. • There are no exceptions in GDPR. • False. See above about law of another country. Other examples include law enforcement, public safety. • Office address is personal data? • False, but it depends. Your name with office address becomes personal data. 11
- 12. How is GDPR doing since its release? • More companies reporting breaches • Fine imposed on British Airways • https://www.bbc.com/news/business-48905907 • Who is next? J 12
- 13. Outline • GDPR and blockchain - summary • GDPR • What is GDPR? • Who are the actors? • What is personal data? • What are rights of a person? • What are the responsibilities of a controller? • Myths about GDPR • GDPR in action • Blockchain • What is blockchain? • Bitcoin – what is it and how people use it • Who is the data controller in bitcoin? • Types of blockchain • Properties of blockchain that are challenging for GDPR • Permissioned private blockchains and GDPR • GDPR and Blockchain • Possible approaches and their pitfalls 13
- 14. What is blockchain? • NIST.IR.8202 • (first two lines of intro) Blockchains are tamper evident and tamper resistant digital ledgers implemented in a distributed fashion (i.e., without a central repository) and usually without a central authority (i.e., a bank, company, or government). At their basic level, they enable a community of users to record transactions in a shared ledger within that community, such that under normal operation of the blockchain network no transaction can be changed once published. What is a block? – grouping of transactions What is a transaction? – a mechanism to update the ledger Does the definition clearly state the append-only aspect of ledger? 14
- 15. What is a “ledger”? • https://www.merriam-webster.com/dictionary/ledger • a book containing accounts to which debits and credits are posted from books of original entry • a horizontal board used for vertical support (as in scaffolding) • The ledger familiar to “most” of us…? • Personal journal 15
- 16. Ledger vs. personal journal Ledger Personal journal Written on Paper with typically pen Paper, with pen or pencil Can also be written with IT system (e.g., computer, SaaS) IT system (e.g., computer, SaaS) Record of who made changes Important Not so much Common primary application Recording monetary transactions Thoughts Information lay out Structure (tabular), credit/debit, with dates Usually with dates Information is appended? Typically, yes Typically, yes Shared with others Employees (probably). Other entities, no, unless IRS J Depends J 16
- 17. What is a digital ledger? • A ledger stored in a digital form • On a (personal) computer or a set of computers • Can contain data ranging from few bytes to peta bytes, and beyond • What is distributed paper ledger? • Create copies of paper and distribute it to relevant folks whenever there is a change? • What is a distributed digital ledger? (or simply distributed ledger) • Ledgers stored in digital form on a set of computers (e.g., cloud), where data repository is not confined to a single computer (NIST: without central repository). The structure of the information stored within the ledger depends on the application. 17
- 18. Tamper evident and tamper resistant • Immutable: Merriam-Webster • https://www.merriam-webster.com/dictionary/immutable • not capable of or susceptible to change • Why do we write personal checks with a pen and not with a pencil? • May be, no one writes personal checks these days J • tamper evident and tamper resistant – to an extent • Can a (distributed) digital ledger be changed? • Of course! • How to detect changes to a (distributed) digital ledger and prevent changes? • Detect changes: audit logs • Prevent unauthorized changes: authz, authn (requires identity) 18
- 19. [Lack of] Central authority or central repository - Examples • I run a database on my single machine. • Central repository? • Central authority? • A big search engine has a massive farm of distributed machines connected over network, that work together to respond to search queries. • Central repository? • Central authority? • A music file-sharing system (Napster) has a central list of which users have files, but files are downloaded peer-to-peer. • Central authority? • Central repository? • A file-sharing network has a distributed index of files and file chunks. • Central repository? • Central authority? 19 Who is data controller and data processor?
- 20. What is Bitcoin? – from the paper Conclusion We have proposed a system for electronic transactions without relying on trust. We started with the usual framework of coins made from digital signatures, which provides strong control of ownership, but is incomplete without a way to prevent double-spending. To solve this, we proposed a peer-to-peer network using proof- of-work to record a public history of transactions that quickly becomes computationally impractical for an attacker to change if honest nodes control a majority of CPU power. The network is robust in its unstructured simplicity. Nodes work all at once with little coordination. They do not need to be identified, since messages are not routed to any particular place and only need to be delivered on a best effort basis. Nodes can leave and rejoin the network at will, accepting the proof-of-work chain as proof of what happened while they were gone. They vote with their CPU power, expressing their acceptance of valid blocks by working on extending them and rejecting invalid blocks by refusing to work on them. Any needed rules and incentives can be enforced with this consensus mechanism. 20
- 21. What is Bitcoin? – from the paper Conclusion We have proposed a system for electronic transactions without relying on trust. We started with the usual framework of coins made from digital signatures, which provides strong control of ownership, but is incomplete without a way to prevent double-spending. To solve this, we proposed a peer-to-peer network using proof- of-work to record a public history of transactions that quickly becomes computationally impractical for an attacker to change if honest nodes control a majority of CPU power. The network is robust in its unstructured simplicity. Nodes work all at once with little coordination. They do not need to be identified, since messages are not routed to any particular place and only need to be delivered on a best effort basis. Nodes can leave and rejoin the network at will, accepting the proof-of-work chain as proof of what happened while they were gone. They vote with their CPU power, expressing their acceptance of valid blocks by working on extending them and rejecting invalid blocks by refusing to work on them. Any needed rules and incentives can be enforced with this consensus mechanism. https://bitcoin.org/bitcoin.pdf So, no non-electronic (aka paper) transactions? all over the world? distributed? anonymity is a goal ? anyone can join and leave consensus algorithm is fixed. interesting 21
- 22. What is Bitcoin? – A geographically distributed peer-to- peer network Bitcoin ledger Bitcoin ledger Bitcoin ledger Bitcoin ledger Bitcoin ledger Bitcoin ledger Bitcoin ledger Bitcoin ledger Bitcoin ledger 22
- 23. Bitcoin: Blocks and Transactions Block N T1 T2: A -> B T3 T4 Block N+1 B->C Block N+2 C->D H(N) H(N+1) T1 T2 T3 T4 H() H() H() H() H() H() H(N) Transaction (oversimplification): - comprises the public key of the sender - Signed structured data (with private key of transaction originator) that indicates some transfer of bitcoins - The structured contains information about transfer of Bitcoins e.g., - S_key, Coin=1, R_key, Coin=2 S_key, Coin=0, R_key, Coin=3 - Public key of receiver 23 Does Bitcoin store personal information? No. However, if public keys can be attributed to a person with high fidelity, there is presently no way to break that linkage. e.g., by purging those transactions from the bitcoin ledger.
- 24. How to people use Bitcoin? • Through an intermediary • Bitcoin exchange • Payment exchange • Directly – by running the software 24
- 25. Who is the data controller / processor for Bitcoin? • Through an intermediary • Bitcoin exchange • Payment exchange • Intermediary becomes the data controller • Directly – by running the software • Can a peer-to-peer network which is not under anyone’s control be a data controller? • Are core software developers of Bitcoin data controllers? 25
- 26. Distributed Ledger Technologies aka Blockchain categorization Drive value of cryptocurrency Cryptocurrency for a business use-case Blockchain for business Anonymous Permissioned CryptocurrencyNon-Cryptocurrency Standards bodies and consortiums 26
- 27. Types of blockchain • What is public blockchain • Ledger is public – accessible by anyone • What is permission-less public blockchain? • Ledger is public, and anyone can join the network. (Bitcoin) • What is permissioned public blockchain • Ledger is public, but approvals required before joining the network. (Sovrin foundation, potentially Hyperledger Fabric also) • What is permissioned private blockchain? • Ledger is private, and approvals required before joining the network (Hyperledger Fabric) • What is permission-less private blockchain? • Good question :). Ledgers are private, but how can anyone join a private blockchain? 27
- 28. Blockchain properties that are challenging for GDPR • Distributed – distributed without consent • Immutable – existing data cannot be changed • Permanent - existing data cannot be changed. Record is permanent 28
- 29. What is Hyperledger? • Hyperledger is an open source collaborative effort created to advance cross-industry blockchain technologies. It is a global collaboration, hosted by The Linux Foundation, including leaders in finance, banking, Internet of Things, supply chains, manufacturing and Technology. • Launched in February 2016 https://www.hyperledger.org/about Frameworks Tools Hyperledger Indy Hyperledger Fabric Hyperledger Iroha Hyperledger Sawtooth Hyperledger Burrow Hyperledger Composer Hyperledger Explorer Hyperledger Cello 29 Hyperledger Ursa
- 30. Overview of Hyperledger Fabric – Key Design Goals • The four P’s • Permissioned • Privacy • Pluggability • Performance 30
- 31. Permissioned: Existing members determine who can join the network, and update configuration Public blockchains • Download software and connect to network • Configuration updated through developer or community consensus Hyperledger Fabric • Policy-based mechanism to admit new members and to update configuration 6/8 votes (admit A: majority vote) A A B I want to invite A to network A B A B A B A B A B A B A B B I want to invite B to network A B 3/8 votes (reject B: majority vote) Permissioned != Private 31
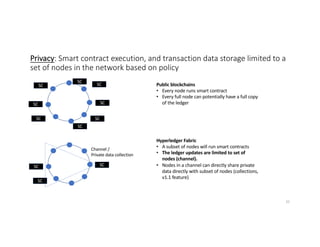
- 32. Privacy: Smart contract execution, and transaction data storage limited to a set of nodes in the network based on policy Public blockchains • Every node runs smart contract • Every full node can potentially have a full copy of the ledger Hyperledger Fabric • A subset of nodes will run smart contracts • The ledger updates are limited to set of nodes (channel). • Nodes in a channel can directly share private data directly with subset of nodes (collections, v1.1 feature) SC SC SC SC SC SC SC SC SCSC SC Channel / Private data collection 32
- 33. Pluggability: consensus, identity provider, crypto, data format, smart contract language Public blockchains • Fixed or hard to change consensus algorithm (proof of work) • Fixed encryption (e.g., secp256k1) • Identity = public key - self • Domain specific language (DSL) for writing smart contracts Hyperledger Fabric • Pluggable consensus algorithm (PBFT, Kafka) • Pluggable crypto service provider • Pluggable identity provider, zero knowledge proofs • General data format, key / value pair • General purpose languages for writing smart contracts (Javascript, Go) 33
- 34. Hyperledger Fabric and GDPR • Transaction (oversimplification): • comprises X.509 certificate of originator containing its public key • As well as entities signing (voting) on this request • No structure of data being stored • Key / value • X.509 certificate may contain personal data - see screenshot • Values may contain personal data 34
- 35. Possible approaches for GDPR and Blockchain – and their pitfalls • Avoid storing personal data on blockchain • Anonymize data and store on blockchain • Not much business value • Encrypt data and store on blockchain • Encryption can be broken one day • Pseudonymize personal data • A random identifier stored in blockchain in lieu of personal data • An off-blockchain database stores the link between random identifier and personal data • Logical deletion achieved by deleting personal data from off-blockchain database • Permissioned private blockchains • Establishing a governance process of which information will be stored in blockchain is critical go ensuring adherence to GDPR 35
- 36. Conclusion • Start with big picture – establish governance process • Avoid storing personal data on blockchain • If blockchain is unavoidable, consider permissioned private blockchains • Be as clear and as transparent to your users 36



















![[Lack of] Central authority or central repository - Examples
• I run a database on my single machine.
• Central repository?
• Central authority?
• A big search engine has a massive farm of distributed machines connected over network, that work
together to respond to search queries.
• Central repository?
• Central authority?
• A music file-sharing system (Napster) has a central list of which users have files, but files are
downloaded peer-to-peer.
• Central authority?
• Central repository?
• A file-sharing network has a distributed index of files and file chunks.
• Central repository?
• Central authority?
19
Who is data controller and data processor?](https://image.slidesharecdn.com/gdprblockchainslideshare-190731150437/85/GDPR-and-Blockchain-19-320.jpg)