Implementing and auditing security controls part 1
- 1. Implementing & Auditing 20 Critical Security Controls. D e f e n s i a 2 0 1 2 Rafel Ivgi This book introduces the 20 most critical security controls that any CIO must implement in his network environment in order to survive the current cyber- attacks of this era.
- 2. 1 | P a g e TABLE OF CONTENTS TABLE OF CONTENTS ..................................................................................................................... 1 Introduction to Security Controls.................................................................................................... 9 Insider versus outsider threats ..................................................................................................... 9 Insider attacks Sophistication vs. Motivation Matrix:........................................................... 10 General Risk Threat Agents, Distribution and Motives ............................................................ 16 Conclusions ........................................................................................................................... 26 US federal Guidelines, Recommendations & Requirements..................................................... 26 FISMA - Federal Information Security Management Act..................................................... 26 FISMA’s RISK MANAGEMENT FRAMEWORK (RMF)................................................. 27 United States Government Configuration Baseline (USGCB).................................................. 28 The Security Content Automation Protocol (SCAP)................................................................. 28 NIST: FIPS 200 AND SP 800-53 - IMPLEMENTING INFORMATION SECURITY STANDARDS AND GUIDELINES......................................................................................... 30 The 20 critical controls.............................................................................................................. 38 Most commonly implemented controls..................................................................................... 38 Least commonly implemented controls..................................................................................... 39 The Process.................................................................................................................................... 39 How to create strategy for data protection and prioritize the implementation of security ........ 39 The common inventory of Information Security Threats to an Organization: ...................... 40 The Organizational Data Lifecycle: ...................................................................................... 40 Creating a security strategy to protect the data per system: .................................................. 41 Creating an organizational scale data security strategy:........................................................ 42 Controls based on the likelihood of security threats.................................................................. 45 Risk Management.................................................................................................................. 45 Calculating Risks, Security Metrics and Risk Measurement Tools ...................................... 45 Implement specific techniques and tools to protect data and systems....................................... 47 Protecting Data...................................................................................................................... 47 Common DRM techniques.................................................................................................... 48 Technologies DRM is used to Protect:.................................................................................. 48
- 3. 2 | P a g e DRM and documents............................................................................................................. 48 Watermarks ........................................................................................................................... 49 Laws regarding DRM............................................................................................................ 49 Digital Millennium Copyright Act ........................................................................................ 49 Audit the identified and implemented controls to ensure that they operate effectively and that they comply with established standards .................................................................................... 58 Preventing physical intrusions....................................................................................................... 59 Using Mantraps ......................................................................................................................... 59 Spinning Glass Doors............................................................................................................ 59 Turnstiles............................................................................................................................... 60 Combining man traps with security cameras and facial recognition......................................... 61 Using swipe based biometric authorization devices.................................................................. 63 Strong Authentication................................................................................................................ 64 Combining Fingerprint swipe with PIN code:....................................................................... 64 Fingerprint Swipe + Magnetic Card...................................................................................... 64 Keyboard with Security......................................................................................................... 65 Not Secure............................................................................................................................. 65 Secure.................................................................................................................................... 65 Extremely Secure................................................................................................................... 66 Using white noise generators to disturb eavesdropping............................................................ 66 Low Cost Hardware Solutions............................................................................................... 66 IPhone Applications .................................................................................................................. 68 Studio Six Digital - AudioTools - Generator......................................................................... 68 Rabble Noise Generator ........................................................................................................ 69 Features ..................................................................................................................................... 69 Distortion & Reverberation Generator .................................................................................. 70 Laptop & PC Configurations......................................................................................................... 71 VDI............................................................................................................................................ 71 Motivations for VDI.............................................................................................................. 71 Poll Results: Is VDI More Expensive Than PC?................................................................... 72 Annual Facilities Costs PC vs. VDI ...................................................................................... 72 Comparing Endpoint PC Security to VDI Security............................................................... 73
- 4. 3 | P a g e VDI Security Comparison: Citrix XenDesktop vs. VMWare View...................................... 74 Data as a service........................................................................................................................ 76 Benefits.................................................................................................................................. 76 Security.................................................................................................................................. 77 PC Metal Locking ..................................................................................................................... 77 Disabling Internal/External USB, DVD, CD-ROM Boot ......................................................... 78 Setting Bios Passwords ............................................................................................................. 81 User Account Control............................................................................................................ 81 Internet Explorer’s 9 Protected Mode ................................................................................... 84 Memory Protection Mechanisms............................................................................................... 84 Security Cookie (Canary)...................................................................................................... 84 SafeSEH ................................................................................................................................ 85 Address space layout randomization (ASLR) ....................................................................... 87 Visualization of ASLR Changes to system Memory per Boot.............................................. 88 NX (No eXecute – Hardware DEP) ...................................................................................... 88 DEP and ASLR Protection Activation State: ........................................................................ 90 Data Execution Prevention - DEP ......................................................................................... 92 DEP, ASLR, IE Protected Mode and UAC’s Impact on Security in Windows: ................... 92 Encrypting Laptops ................................................................................................................... 93 Managed Solution – Mcafee / Symantec............................................................................... 93 Encryption Product Comparison for Apple Macintosh ......................................................... 93 Product Feature Comparison Table....................................................................................... 94 Layering & Partition Type Support............................................................................................... 95 Modes of operation........................................................................................................................ 96 Non-Managed - TrueCrypt.................................................................................................... 97 Setting Laptops “Out of Organization Personal Firewall Policy” ......................................... 99 Network Equipment .................................................................................................................... 102 Understanding Layer 2 & 3 Security....................................................................................... 102 Layer 3+ Security.................................................................................................................... 155 An example of the right way to divide VLANs to matching logical business units............ 157 Maximizing Your Network Security with Private VLANs (PVLAN) .................................... 158
- 5. 4 | P a g e Configuring PVLAN ........................................................................................................... 161 Upgrading Router/Switch Firmware ....................................................................................... 163 Buying new equipment, new security features........................................................................ 165 Secure Configuration Management (SCM)................................................................................. 167 Introduction ............................................................................................................................. 167 Maintenance systems........................................................................................................... 167 Mapping supported devices..................................................................................................... 170 Inventory Scanner................................................................................................................ 171 Completing the gaps with scripts ............................................................................................ 176 Creating Device Groups (Security Level, Same Version…)................................................... 177 Creating Policies...................................................................................................................... 177 Attachments and Guidelines................................................................................................ 179 Auditing to verify security in practice..................................................................................... 187 Case Studies Summary: Top 10 Mistakes - Managing Windows Networks............................... 192 “The shoemaker's son always goes barefoot”...................................................................... 192 Domain Administrators on Users VLAN............................................................................ 192 Domain Administrator with a Weak Password ................................................................... 193 Domain Administrator without the Conficker Patch (MS08-067) ...................................... 194 (LM and NTLM v1) vs. (NTLM v.2)...................................................................................... 195 Pass the Hash Attack............................................................................................................... 197 Daily logon as a Domain Administrator.............................................................................. 198 Using Domain Administrator for Services.......................................................................... 198 Managing the network with Local Administrator Accounts ............................................... 199 The NetLogon Folder .......................................................................................................... 199 LSA Secrets & Protected Storage........................................................................................ 201 Cached Logons.................................................................................................................... 205 Password History................................................................................................................. 206 Users as Local Administrators............................................................................................. 206 Forgetting to Harden: RestrictAnonymous=1 ..................................................................... 207 Weak Passwords / No Complexity Enforcement ................................................................ 207 Guess what the password was? (gma )............................................................................. 207
- 6. 5 | P a g e Firewalls...................................................................................................................................... 208 Understanding Firewalls (1, 2, 3, 4, 5 generations)................................................................. 208 First generation: packet filters............................................................................................. 208 Second generation: "stateful" filters.................................................................................... 209 Third generation: application layer...................................................................................... 209 Application firewall............................................................................................................. 209 The Common Firewall’s Limits .......................................................................................... 211 Implementing Application Aware Firewalls ....................................................................... 212 Securely Enabling Applications Based on Users & Groups................................................ 214 High Performance Threat Prevention.................................................................................. 216 Checkpoint R75 – Application Control Blade..................................................................... 218 Utilizing Firewalls for Maximum Security ............................................................................. 220 Implementing a Back-Bone Application-Aware Firewall....................................................... 220 Network Inventory & Monitoring ............................................................................................... 220 How to map your network connections?................................................................................. 220 How to discover all network devices?................................................................................. 221 How to discover all cross-network installed software?........................................................... 221 NAC ............................................................................................................................................ 222 The Problem: Ethernet Network......................................................................................... 222 What is a NAC originally? .................................................................................................. 223 Today’s NAC?..................................................................................................................... 223 Why Invent Today’s NAC?................................................................................................. 223 Dynamic Solution for a Dynamic Environment.................................................................. 224 Did We EVER Manage Who Gets IP Access?.................................................................... 224 What is a NAC?................................................................................................................... 224 Simple Explanation ............................................................................................................. 225 Goals of NAC...................................................................................................................... 225 NAC Approaches................................................................................................................. 226 General Basic NAC Deployment ........................................................................................ 228 NAC Deployment Types:.................................................................................................... 228 NAC Acceptance Tests........................................................................................................ 229
- 7. 6 | P a g e NAC Vulnerabilities............................................................................................................ 230 The common attack – Bypassing & Killing the NAC......................................................... 231 Open Source Solutions ........................................................................................................ 232 SIEM - (Security Information Event Management).................................................................... 238 SIEM Capabilities ............................................................................................................... 238 SIEM Architecture .................................................................................................................. 239 SIEM Logics........................................................................................................................ 242 Planning for the right amounts of data .................................................................................... 243 Introduction ......................................................................................................................... 243 SIEM Benchmarking Process.............................................................................................. 244 The Baseline Network......................................................................................................... 246 SIEM Storage and Analysis................................................................................................. 249 Baseline Network Device Map............................................................................................ 251 EPS Calculation Worksheet ................................................................................................ 252 Common SIEM Report Types................................................................................................. 252 Custom Reports ................................................................................................................... 253 Defining the right Rules – It’s all about the rules.................................................................... 253 IDS/IPS........................................................................................................................................ 254 IPS Types ................................................................................................................................ 255 Detection Methods .................................................................................................................. 255 Signature Catalog:................................................................................................................... 256 Alert Monitoring: .................................................................................................................... 257 Security Reporting:.................................................................................................................. 258 Alert Monitor:.......................................................................................................................... 259 Anti-Virus:............................................................................................................................... 260 Web content protection & filtering.............................................................................................. 260 Session Hi-Jacking and Internal Network Man-In-The-Middle.............................................. 260 XSS Attack Vector .............................................................................................................. 260 The Man-In-The-Middle Attack Vector.............................................................................. 261 HTML5 and New Client-Side Risks ....................................................................................... 266 Cookie/Repository User Tracking....................................................................................... 266
- 8. 7 | P a g e User TraceBack Techniques................................................................................................ 268 MAC ADDRESS Detection Of All Network Interfaces via JAVA .................................... 269 XSS + Browser Location Services ...................................................................................... 270 Use your power to protect and enforce – GPO........................................................................ 273 Choosing, Implementing and Testing Web Application Firewalls ......................................... 280 Detecting Web Application Firewalls ................................................................................. 280 Bypassing Web Application Firewalls ................................................................................ 283 HTTP Parameter Pollution (HPP) ....................................................................................... 283 Examples:............................................................................................................................ 284 Circumvention of default WAF filtering mechanisms ........................................................ 286 High Level Distributed Denial of Service............................................................................... 296 Protecting DNS Servers & Detecting DNS Enumeration Attacks .......................................... 300 Detecting Sub Domains....................................................................................................... 303 Securing Web Servers ................................................................................................................. 304 Components of a generic web application system................................................................... 305 Multi-tier architecture.............................................................................................................. 306 Securing Virtual Hosts – Preventing Detection of Virtual Hosts........................................ 307 Protecting against Google Hacking..................................................................................... 308 Securing IIS 7/7.5 + Microsoft SQL Server 2008................................................................... 310 IIS Dynamic IP Restrictions Module: The mod_evasive of IIS.......................................... 310 Hardening IIS SSL with IISCrypto – Disabling Weak Ciphers .......................................... 311 Hardening IIS 7.5 on Windows 2008 Server R2 SP1.......................................................... 312 Apache Hardening............................................................................................................... 316 Mod_Evasive – Anti-D.O.S Apache Module...................................................................... 317 SELinux – Optional Hardening:.............................................................................................. 318 SELinux Apache Hardening................................................................................................ 318 SELinux for other services (Experts Only) ............................................................................. 319 Enable Hardened HTTP ...................................................................................................... 319 Email protection & filtering ........................................................................................................ 322 Sending Spoofed Emails – Bypassing SPF with a 8$ Domain............................................ 325 VPN Security............................................................................................................................... 326
- 9. 8 | P a g e Identifying VPNs & Firewalls (Fingerprinting VPNS)........................................................... 326 Offline password cracking................................................................................................... 327 VPN IKE User Enumeration ............................................................................................... 330 VPN PPTP User Enumeration............................................................................................. 331 VPN Clients Man-In-The-Middle Downgrade Attacks........................................................... 332 Downgrade Attacks - IPSEC Failure................................................................................... 332 Downgrade Attacks – PPTP ................................................................................................ 332 PPTP:................................................................................................................................... 333 PPTP Brute Force................................................................................................................ 333 Hacking VPNs with “Aggressive Mode Enabled”.................................................................. 334 Endpoint Security........................................................................................................................ 341 Penetration tests and red team exercises ..................................................................................... 341 Implementing identity & access management creating backups, BCP & DRP .......................... 341 Security Metrics .......................................................................................................................... 342 Incident Reponses........................................................................................................................ 342 Creating an audit ......................................................................................................................... 342 Conclusions ................................................................................................................................. 343
- 10. 9 | P a g e Introduction to Security Controls Insider versus outsider threats External: external threats originate from sources outside of the organization and its network of partners. Examples include former employees, lone hackers, organized criminal groups, and government entities. External agents also include environmental events such as floods, earthquakes, and power disruptions .Typically, no trust or privilege is implied for external entities. Internal: Internal threats are those originating from within the organization. This encompasses company executives, employees, independent contractors, interns, etc. ., as well as internal infrastructure. Insiders are trusted and privileged (some more than others). Partners aka “External Insiders”/”Trusted Business Partners (TBP)”: Partners include any third party sharing a business relationship with the organization. This includes suppliers, vendors, hosting providers, outsourced IT support, etc... some level of trust and privilege is usually implied between business partners External – Internal – Partner Incident Distribution from the Last 8 Years: As we can see, the rise in the amount of external attacks is rising every year, whereas the amount of internal attacks is reduced along the years. It is critical not to confuse the reference for “internal” as the factor the malicious intension comes from and not the source of the attack. For example, a remote external attacker can take over one machine and use it to execute internal network attacks. In this example, the attacker is still external, even though the type of attack is an internal network attack.
- 11. 10 | P a g e Insider attacks Sophistication vs. Motivation Matrix: Examining Six Cases of Insider Originated Incident:
- 12. 11 | P a g e Organizational Divisions – Influence vs. Interest in inspected Incidents:
- 13. 12 | P a g e Types of internal Agents by Percent:
- 14. 13 | P a g e
- 15. 14 | P a g e
- 16. 15 | P a g e
- 17. 16 | P a g e General Risk Threat Agents, Distribution and Motives Threat Categories in Practice Over time:
- 18. 17 | P a g e Distribution of threat agent type by stolen records: Distribution by motive:
- 19. 18 | P a g e Distribution by origin organization type: Distribution by origin geo-location:
- 20. 19 | P a g e Malware Functionality:
- 21. 20 | P a g e Hacking Methods Used: Hacking Vectors Used:
- 22. 21 | P a g e Social Engineering Types Percentage: Social Engineering Vectors Percentage: Social Engineering Targets Percentage: Compromised Assets Percentage:
- 23. 22 | P a g e
- 24. 23 | P a g e Targeted vs. Opportunistic in All vs. Large Organizations: Time from initial attack to data exfiltration until compromise discovery:
- 25. 24 | P a g e Breach Discovery Methods: Breached Organizations Information Security vs. PCI-DSS and Common Standards:
- 26. 25 | P a g e
- 27. 26 | P a g e Conclusions 1. Attacks are aimed at all companies, large companies are targeted with more attacks 2. External attacks mainly originates from organized crime groups 3. Most attacks originate from east Europe 4. Attacks mostly involve personal or financial gain 5. The rise in the last years is in external hacking and malware infiltration 6. Hacking software were mostly Keyloggers and backdoors 7. Hacking methods were mostly password guessing and use of stolen credentials 8. Hacking Vectors were mostly remote access and backdoors 9. social engineering attacks were mostly by pretexting & bribery on the phone and in person of regular employees and cashiers 10. Hacked machines were mostly Point-Of-Sale and desktop workstations 11. Most organizations were attacked randomly, large ones were targeted 12. It mostly took minutes to successful penetration, minutes for data exfiltration and months to discover the incidents 13. Most breaches were reported by law agencies and third party fraud detection 14. Most organization were very far from being compliant to security standards US federal Guidelines, Recommendations & Requirements FISMA - Federal Information Security Management Act FISMA final requirements specification is available at: http://csrc.nist.gov/drivers/documents/FISMA-final.pdf FISMA’s Vision To promote the development of key security standards and guidelines to support the implementation of and compliance with the Federal Information Security Management Act including: Standards for categorizing information and information systems by mission impact Standards for minimum security requirements for information and information systems Guidance for selecting appropriate security controls for information systems Guidance for assessing security controls in information systems and determining security control effectiveness Guidance for the security authorization of information systems
- 28. 27 | P a g e Guidance for monitoring the security controls and the security authorization of information systems FISMA’s Objectives The implementation of cost-effective, risk-based information security programs The establishment of a level of security due diligence for federal agencies and contractors supporting the federal government More consistent and cost-effective application of security controls across the federal information technology infrastructure More consistent, comparable, and repeatable security control assessments A better understanding of enterprise-wide mission risks resulting from the operation of information systems More complete, reliable, and trustworthy information for authorizing officials-- facilitating more informed security authorization decisions More secure information systems within the federal government including the critical infrastructure of the United States FISMA’s RISK MANAGEMENT FRAMEWORK (RMF)
- 29. 28 | P a g e United States Government Configuration Baseline (USGCB) United States Government Configuration Baseline (USGCB) evolved from the “FDCC - Federal Desktop Core Configuration”. USGCB is a Federal government-wide initiative that provides guidance to agencies on what should be done to improve and maintain an effective configuration settings focusing primarily on security. The USGCB offers the latest revisions of the most hardened windows environment security settings, which have been tested to enable sufficient usability: Hardened and Compliant Microsoft Windows Group Policy Collection http://usgcb.nist.gov/usgcb/content/gpos/USGCB-GPOs.zip Hardened and Compliant Microsoft Windows Security Settings Specification Excel http://usgcb.nist.gov/usgcb/documentation/USGCB-Windows-Settings.xls The Security Content Automation Protocol (SCAP) The Security Content Automation Protocol (SCAP) is a suite of specifications that standardize the format and nomenclature by which software flaw and security configuration information is communicated, both to machines and humans. SCAP is a multi-purpose framework of specifications that support automated configuration, vulnerability and patch checking, technical control compliance activities, and security measurement. Goals for the development of SCAP include standardizing system security management, promoting interoperability of security products, and fostering the use of standard expressions of security content. SCAP version 1.2 is comprised of eleven component specifications in five categories: 1. Languages. The SCAP languages provide standard vocabularies and conventions for expressing security policy, technical check mechanisms, and assessment results. The SCAP language specifications are Extensible Configuration Checklist Description Format (XCCDF), Open Vulnerability and Assessment Language (OVAL®), and Open Checklist Interactive Language (OCIL™). 2. Reporting formats. The SCAP reporting formats provide the necessary constructs to express collected information in standardized formats. The SCAP reporting format specifications are Asset Reporting Format (ARF) and Asset Identification. Although
- 30. 29 | P a g e Asset Identification is not explicitly a reporting format, SCAP uses it as a key component in identifying the assets that reports relate to. 3. Enumerations. Each SCAP enumeration defines a standard nomenclature (naming format) and an official dictionary or list of items expressed using that nomenclature. The SCAP enumeration specifications are Common Platform Enumeration (CPE™), Common Configuration Enumeration (CCE™), and Common Vulnerabilities and Exposures (CVE®). 4. Measurement and scoring systems. In SCAP this refers to evaluating specific characteristics of a security weakness (for example, software vulnerabilities and security configuration issues) and, based on those characteristics, generating a score that reflects their relative severity. The SCAP measurement and scoring system specifications are Common Vulnerability Scoring System (CVSS) and Common Configuration Scoring System (CCSS). 5. Integrity. An SCAP integrity specification helps to preserve the integrity of SCAP content and results. Trust Model for Security Automation Data (TMSAD) is the SCAP integrity specification. SCAP utilizes software flaw and security configuration standard reference data. This reference data is provided by the National Vulnerability Database (NVD), which is managed by NIST and sponsored by the Department of Homeland Security (DHS). The latest full specification of SCAP is available at: http://csrc.nist.gov/publications/nistpubs/800-126-rev2/SP800-126r2.pdf The latest SCAP content for Windows 7, Windows 7 Firewall, and Internet Explorer 8 http://usgcb.nist.gov/usgcb/content/scap/USGCB-Major-Version-1.2.x.0.zip Obtaining FISMA, NIST and SCAP compliant Security Checklists:
- 31. 30 | P a g e Example download link: http://iase.disa.mil/stigs/os/windows/u_windows_2008_r2_dc_v1r3_stig_benchmark_201201 27.zip NIST: FIPS 200 AND SP 800-53 - IMPLEMENTING INFORMATION SECURITY STANDARDS AND GUIDELINES NIST’s SP 800-53 focuses on the selection and implementation of appropriate security controls for an information system or a system-of-systems. These are important tasks that can have major implications on the operations and assets of an organization as well as the welfare of individuals and the Nation. Security controls are the management, operational, and technical safeguards or countermeasures employed within an organizational information system to protect the confidentiality, integrity, and availability of the system and its information. There are several important questions that should be answered by organizational officials when addressing the security considerations for their information systems:
- 32. 31 | P a g e • What security controls are needed to adequately mitigate the risk incurred by the use of information and information systems in the execution of organizational missions and business functions? • Have the selected security controls been implemented or is there a realistic plan for their implementation? • What is the desired or required level of assurance (i.e., grounds for confidence) that the selected security controls, as implemented, are effective in their application? The answers to these questions are not given in isolation but rather in the context of an effective information security program for the organization that identifies, mitigates as deemed necessary, and monitors on an ongoing basis, risks arising from its information and information systems. SECURITY CONTROL ORGANIZATION AND STRUCTURE Security controls described in this publication have a well-defined organization and structure. For ease of use in the security control selection and specification process, controls are organized into seventeen families. Each security control family contains security controls related to the security functionality of the family. A two-character identifier is assigned to uniquely identify each security control family. In addition, there are three general classes of security controls: management, operational, and technical. Table 1-1 summarizes the classes and families in the security control catalog and the associated security control family identifiers:
- 33. 32 | P a g e NIST 800-53 Risk Management Framework and the information security standards and guidance documents associated with each activity:
- 34. 33 | P a g e NIST 800-53 Security Control Selection Process:
- 35. 34 | P a g e NIST 800-53 Security Control Baselines:
- 36. 35 | P a g e NIST 800-53 Security Control Priority & Baseline Allocation Examples:
- 37. 36 | P a g e NIST 800-53 Mapping Specified Security Controls to ISO 27001: NIST 800-53 Controls Table is available at: http://csrc.nist.gov/groups/SMA/fasp/documents/security_controls/SP800-53Table.xls Security Test and Evaluation (ST&E) Plan Template is available at: http://csrc.nist.gov/groups/SMA/fasp/documents/security_controls/App_CA_STE_Plan_Templat e_030408.doc
- 38. 37 | P a g e
- 39. 38 | P a g e The 20 critical controls 1. Live Monitoring and Real-Time Alerting of security events and anomalies (SIEM integrated into AD, IPS, Automatic Inventory and etc…) 2. Data Recovery Capability 3. Effective network segmentation and compartmentalization of management and administration networks 4. Secure Configurations for Network Devices such as Firewalls, Routers, and Switches 5. Applying suitable, different reoccurring automatic update/patching policies for all software on all asset types (endpoint, server, laptop, mission critical, internet exposed…) 6. Revoking and limiting local administrator privileges in all systems, especially endpoints 7. Boundary Defense 8. Policy Hardening – Utilizing Group Policy For Security 9. Implementation of an IDM (Identity Management) & SSO for all users, combined with a strong authentication (two-factor). 10. Implementing a Back-Bone Application-Aware Firewall (Limitation and Control of Network Ports, Protocols, and Services by User * MAC * IP) 11. Inventory of Authorized and Unauthorized Devices 12. Data Loss Prevention 13. Security Skills Assessment and Appropriate Training to Fill Gaps 14. An incident response policy to minimize all potential risks during a breach 15. Inventory of Authorized and Unauthorized Software 16. Device Control Management – MDM (Mobile Device Management), Wireless/Cellular Modems, Mobile Storage, Digital Cameras 17. Secure Configurations for Hardware and Software on Laptops, Workstations, and Servers 18. Malware Defenses (AV, HIPS) 19. Controlled Access Based on the Need to Know 20. Penetration Tests and Red Team Exercises Most commonly implemented controls Most commonly implemented controls 1. Firewall on External Network (Internet) 2. Endpoint Security (Anti-Virus + Basic Device Control) 3. Boundary Defense 4. Data Recovery Capability 5. Malware Defenses 6. Penetration Tests and Red Team Exercises 7. Continuous Vulnerability Assessment and Remediation 8. Controlled Use of Administrative Network Privileges 9. Network Account Monitoring and Control 10. Controlled Access Based on Need to Know
- 40. 39 | P a g e Least commonly implemented controls 1. Protect equipment from unauthorized access 2. Secure offices and rooms 3. Secure the physical perimeter of the organization’s buildings (internally) 4. Track the location of removable computer media 5. Manage visitor access to secure areas within the buildings 6. Measure security compliance at a third-party facility 7. Restrict access to the facility from the delivery or loading area 8. Protect unattended equipment 9. Apply digital signatures to protect the authenticity and integrity of electronic information 10. Detect unauthorized access to physical facilities The Process How to create strategy for data protection and prioritize the implementation of security
- 41. 40 | P a g e The common inventory of Information Security Threats to an Organization: The Organizational Data Lifecycle:
- 42. 41 | P a g e Creating a security strategy to protect the data per system: 1. Defining the organizational approach to security a. Organization’s “Risk Appetite” b. Current/Future Insurance coverage plans 2. Mapping all the organizational data systems a. Inspecting Documentations b. Requesting Information from Team Leaders and System Mangers c. Network Scanning – Mapping “Forgotten” systems 3. Inspecting the regulations the organization must comply to a. Government Regulations (DoD, CC, FIPS, NIST SP 800-37,NIST 800-53(A), FISMA) b. Industry Standards and Regulations (ISO17799/BS7799, ITIL/ISO-IEC 20000 and COBIT) c. International Regulations (ISO 27001, PCI-DSS, SOX, COSO, HIPPA , BITS (banking industry standards)) 4. Assigning numerical values to systems data by importance Data Acquisition/ Creation Data Storage Data Use Data Sharing/Mo difying Data Destructing
- 43. 42 | P a g e a. System/Asset quantified value by regulation requirements (by what the regulation considers sensitive data, i.e. customer names, address, email DB) b. Identifying The Critical Data Of Each Data System - System/Asset quantified value by system’s customer availability requirements (i.e. customer, minor/major business partner, internal use, backup/DR) i. System/Asset quantified value by data sensitivity defined by System Manager/Data Owner together with the CISO c. Identifying The Data Usage, accessibility and Usability Requirements Of Each Data types of each System 5. Analyzing system threats and attack vectors to the data a. Is the data encrypted? Where is the key located? Who has access to the key? b. Is the system under real-time security monitoring? c. What are the availability requirements of the system? d. Which networks the system is exposed to? e. Does the system get security updates automatically? f. Which services does the system listen on? g. How many people have privileged access to the system? h. Is the system integrated with a strong authentication mechanism? 6. Prioritizing work process and defining Data Protection Requirements by data value and regulation requirements a. Data Protection Requirements of Most enforced regulations b. Data Protection Requirements of Most business enabling regulations c. Aligning to the management’s organizational approach to security d. Researching remediation solutions and determining their TCO for 5-10 years 7. Confronting the results with management a. Setting up recurring meetings with management regarding information security (Yearly Plan, Strategic Plan, Current & Emerging Threats, Discovered Incidents) b. Presenting the calculated risk (by ALE, ARO) c. Presenting the potential set of remediation solutions vs. costs required d. Establishing decisions per threat or/and per system e. Requesting corrections to the current budget Creating an organizational scale data security strategy: 1. Defining the organizational approach to security a. Organization’s “Risk Appetite” and Data Leakage approach b. Current/Future Insurance coverage plans
- 44. 43 | P a g e 2. Mapping the major organizational data systems 3. Inspecting the regulations the organization must comply to a. Government Regulations (DoD, CC, FIPS, NIST SP 800-37,NIST 800-53(A), FISMA) b. Industry Standards and Regulations (ISO17799/BS7799, ITIL/ISO-IEC 20000 and COBIT) c. International Regulations (ISO 27001, PCI-DSS, SOX, COSO, HIPPA , BITS (banking industry standards)) 4. Assigning numerical values to major systems data by importance a. System/Asset quantified value by regulation requirements (by what the regulation considers sensitive data, i.e. customer names, address, email DB) b. Identifying The Critical Data Of Each Data System - System/Asset quantified value by system’s customer availability requirements (i.e. customer, minor/major business partner, internal use, backup/DR)
- 45. 44 | P a g e i. System/Asset quantified value by data sensitivity defined by System Manager/Data Owner together with the CISO 5. Identifying and Detecting the highest common denominator in data attributes: a. Highest intersecting Data Accessibility (Setup Complexity, Training Complexity, Access Complexity, Client/Clientless, OS, Networks, Entities, Formats, Time Frames, Access Level) b. Highest intersecting Data Sharing requirements (Setup Complexity, Training Complexity, Sharing Complexity, Networks, Entities, Formats) c. Highest intersecting Data types of each System (DOC, XLS, PPT, PDF,TXT, Data in Databases, i.e. Credit Card Information) d. Most common size of a single data unit/file 6. Analyzing system threats and attack vectors to the data a. Is the data encrypted? Where is the key located? Who has access to the key? b. How is the data used? Over which networks? c. Where is the data stored permanently? Temporarily? (Clients Outlook? Laptops? Are laptops encrypted?) d. How is the data shared? With whom? e. What types/formats is the data used with? Modifiable/Writable (DOC, XLS) or Read Only (PDF, XPS)? f. Does the data contain identifying information? (Authors, Watermarks, Digital Signature) g. Does each single copy of the data is generated and marked for each specific entity it is shared with? h. Are the major systems providing the data under real-time security monitoring? i. What are the availability requirements of the data/system? j. How many people have privileged access to the data/system? k. Is the data access system integrated with a strong authentication mechanism? l. Is the data protected with a DRM (Digital Rights Management) solution? m. Is the data protected with a DLP (Data Leakage Prevention) solution? n. What are the possible data exfiltration vectors for the specific data types and existing environments? (Internet , Cellular Internet, Wireless, Bluetooth, Mass Storage (DOK, Camera, USB HDD), CD, DVD, Screen Capture, Physical Screen Photo) 7. Prioritizing work process and defining Data Protection Requirements by data value and regulation requirements a. Data Protection Requirements of Most enforced regulations b. Data Protection Requirements of Most business enabling regulations c. Aligning to the management’s organizational approach to security d. Considering the major usability requirements collected from data owners
- 46. 45 | P a g e e. Researching remediation solutions and determining their TCO for 5-10 years 8. Operating the management a. Setting up recurring meetings with management regarding information security data protection strategy (Yearly Plan, Strategic Plan, Current & Emerging Threats, Discovered Data Security Incidents) b. Presenting the overall cross-organizational calculated risk (by ALE, ARO) c. Presenting the potential set of cross-organizational remediation solutions vs. costs required d. Establishing decisions per threat or/and per major data system e. Requesting corrections to the current budget Controls based on the likelihood of security threats Risk Management Calculating Risks, Security Metrics and Risk Measurement Tools 1. BITS Key Risk Measurement Tool
- 47. 46 | P a g e
- 48. 47 | P a g e Implement specific techniques and tools to protect data and systems Protecting Data DRM - Digital Rights Management Digital rights management (DRM) is a class of access control technologies that are used by hardware manufacturers, publishers, copyright holders and individuals with the intent to limit the use of digital content and devices after sale. DRM is any technology that inhibits uses of digital content that are not desired or intended by the content provider. Copy protections which can be circumvented without modifying the file or device, such as serial numbers or key files are not generally considered to be DRM. DRM also includes specific instances of digital works or devices. Companies such as Amazon, AOL, Apple Inc., the BBC, Microsoft and Sony use digital rights management protections. Works can become permanently inaccessible if the DRM scheme changes or if the service is discontinued. Proponents argue that digital locks should be considered necessary to prevent "intellectual property" from being copied freely, just as physical locks are needed to prevent personal property from being stolen.
- 49. 48 | P a g e Digital locks placed in accordance with DRM policies can also restrict users from doing something perfectly legal, such as making backup copies of CDs or DVDs, lending materials out through a library, accessing works in the public domain, or using copyrighted materials for research and education under fair use laws. Common DRM techniques 1. Restrictive Licensing Agreements: The access to digital materials, copyright and public domain are controlled. Some restrictive licenses are imposed on consumers as a condition of entering a website or when downloading software. 2. Encryption 3. Scrambling of expressive material 4. Embedding of a tag (digital watermarking): This technology is designed to control access and reproduction of online information. This includes backup copies for personal use. Technologies DRM is used to Protect: 1. DRM and film 2. DRM and television 3. DRM and music 4. Audio CDs 5. Internet music 6. Computer games 7. E-books DRM and documents Enterprise digital rights management (E-DRM or ERM) is the application of DRM technology to the control of access to corporate documents such as Microsoft Word, PDF, and AutoCAD files, emails, and intranet web pages rather than to the control of consumer media. E-DRM, now more commonly referenced as IRM (Information Rights Management), is generally intended to prevent the unauthorized use (such as industrial or corporate espionage or inadvertent release) of proprietary documents. IRM typically integrates with content management system software. DRM has been used by organizations such as the British Library in its secure electronic delivery service to permit worldwide access to substantial numbers of rare (and in many cases unique) documents which, for legal reasons, were previously only available to authorized individuals actually visiting the Library's document Centre at Boston Spa in England.
- 50. 49 | P a g e Watermarks Digital watermarks are features of media that are added during production or distribution. Digital watermarks involve data that is arguably steganographically embedded within the audio or video data. Watermarks can be used for different purposes that may include: recording the copyright owner recording the distributor recording the distribution chain identifying the purchaser of the music Watermarks are not complete DRM mechanisms in their own right, but are used as part of a system for Digital Rights Management, such as helping provide prosecution evidence for purely legal avenues of rights management, rather than direct technological restriction. Laws regarding DRM Digital Millennium Copyright Act In 1998 the Digital Millennium Copyright Act (DMCA) was passed in the United States to impose criminal penalties on those who make available technologies whose primary purpose and function is to circumvent content protection technologies. IRM – Information Rights Management Information Rights Management (IRM) is a term that applies to a technology which protects sensitive information from unauthorized access. It is sometimes referred to as (E-DRM) or Enterprise Digital Rights Management. This can cause confusion because Digital Rights Management (DRM) technologies are typically associated with business to consumer systems designed to protect rich media such as music and video. IRM is a technology which allows for information (mostly in the form of documents) to be ‘remote controlled’. This means that information and its control can now be separately created, viewed, edited & distributed. Some existing IRM systems have been ongoing development of DRM style systems; however a true IRM system will have some important differences and is typically used to protect information in a business to business model, such as financial data, intellectual property and executive communications. IRM currently applies mainly to documents and emails. IRM technologies allow for several levels of security. Functionality offered by IRM usually comprises: Industry standard encryption of the information. Strong in use protection, such as controlling copy & paste, preventing screen shots and printing. A rights model/policy which allows for easy mapping of business classifications to information. Offline use allowing for users to create/access IRM sealed documents without needing network access for certain periods of time.
- 51. 50 | P a g e Full auditing of both access to documents as well as changes to the rights/policy by business users An example of IRM in use would be to secure a sensitive engineering document being distributed in an environment where the document's recipients could not necessarily be trusted. Alternatively, an e-mail could be secured with IRM, so if it accidentally is forwarded to an untrusted party, only authorized users would gain access. Note that a well-designed IRM system will not limit the ability for information to be shared; rather rules are only enforced when people attempt to gain access. This is important as often people share sensitive information with users who should legitimately have access but don't, and the technology needs to facilitate the easy request of access back to the business owners. IRM is far more secure than shared secret passwords; key management is used to protect the information whilst it is at rest on a hard disk, network drive or other storage device. Crucially IRM continues to protect and control access to the document when it is in use. Functionality such as preventing screen shots, disallowing the copying of data from the secure document to an insecure environment and guarding the information from programmatic attack, are key elements of an effective IRM solution. Seclore Technology from India has made very promising and authentic tools for IRM. Zafesoft Inc., a Silicon Valley (California) company has created a solution for securing documents and the information in them as well as images (including medical images). Information Rights Management is also known by the following names: Enterprise Rights Management Enterprise DRM or Enterprise Digital Rights Management Document Rights Management Intelligent Rights Management Common IRM Solutions: 1. Covertix SmartCipher - Information Rights Management solutions 2. Seclore Technology - Information Rights Management solutions 3. Zafesoft Inc. - Information Security and Rights Management solutions 4. Microsoft - Rights Management solutions 5. Secure Islands - Rights Management solutions
- 52. 51 | P a g e Product Example: Secure Islands IQPROTECTOR FILE PROTECTION System Architecture: Feature Set: Feature Benefit Automatic classification at content creation 100% content identification accuracy, simple deployment, no repository scanning required Automatic protection based on central policy Enterprise has complete control over what, why, when and how to protect data, completely transparent to the end user Content marking – classification-driven addition of visual labels to documents Increase security awareness by visualizing document classification, raise both compliance and user accountability Scanner Mode Server Classification and encryption of pre-existing content on file servers, NAS, SAN, and ECM repositories Optional user classification – enabling the Increased user accountability, added classification
- 53. 52 | P a g e Feature Benefit user to decide the type of classification required for a given document or mail accuracy Extends AD-RMS file format support (multi format) Protection for additional file formats, without application integration Protection of client- or application-based content Applies RMS protection on files and data exported from applications without integration Metadata labeling for DLP, FCI, eDiscovery, archiving Lowers the burden on DLP by accurately identifying, classifying and tagging sensitive enterprise data early in the data lifecycle to allow effective DLP enforcement Protect documents upon access Apply AD-RMS protection on pre-existing content Extendable to other encryption schemes Conversion of AD-RMS protected data to other protection schemes Audit and report on every action on files everywhere Monitoring and audit mechanisms operate throughout the information lifecycle
- 54. 53 | P a g e Management Panel: DLP - Data Leakage Prevention Data Loss Prevention (DLP) is a computer security term referring to systems that enable organizations to reduce the corporate risk of the unintentional disclosure of confidential information. These system identify, monitor, and protect confidential data while in use (e.g. endpoint actions), in motion (e.g. network actions), and at rest (e.g. data storage) through deep content inspection, contextual security analysis of transaction (attributes of originator, data object, medium, timing, recipient/destination and so on) and with a centralized management framework. Vendors Semantics: 1. Data Leak Prevention 2. Information Leak Detection and Prevention (ILDP) 3. Information Leak Prevention (ILP) 4. Content Monitoring and Filtering (CMF) 5. Information Protection and Control (IPC) 6. Extrusion Prevention System 7. Identification & Prevention of Data Exfiltration Deployment and Coverage Network DLP (aka Data in Motion <DiM>)
- 55. 54 | P a g e Typically a software or hardware solution that is installed at network egress points near the perimeter. It analyzes network traffic to detect sensitive data that is being sent in violation of information security policies. Storage DLP (aka Data at Rest <DaR>) Data-loss prevention of stored data typically involves a Data Security Software installed on your computer to prevent unauthorized access to the data stored on your hard drive and USB/External drives. Endpoint DLP (aka Data in Use <DiU>) Such systems run on end-user workstations or servers in the organization. Like network-based systems, endpoint-based can address internal as well as external communications, and can therefore be used to control information flow between groups or types of users (e.g. 'Chinese walls'). They can also control email and Instant Messaging communications before they are stored in the corporate archive, such that a blocked communication (i.e., one that was never sent, and therefore not subject to retention rules) will not be identified in a subsequent legal discovery situation. Endpoint systems have the advantage that they can monitor and control access to physical devices (such as mobile devices with data storage capabilities) and in some cases can access information before it has been encrypted. Some endpoint-based systems can also provide application controls to block attempted transmissions of confidential information, and provide immediate feedback to the user. They have the disadvantage that they need to be installed on every workstation in the network, cannot be used on mobile devices (e.g., cell phones and PDAs) or where they cannot be practically installed (for example on a workstation in an internet café).
- 56. 55 | P a g e Open Source Solutions: OpenDLP
- 57. 56 | P a g e
- 58. 57 | P a g e MyDLP Community Edition
- 59. 58 | P a g e Audit the identified and implemented controls to ensure that they operate effectively and that they comply with established standards 1. Feature and Acceptance Testing 1.1. Verify the features designed in the controls work properly. For example, verify that only the specifically defined websites are protected by the Web Application Firewalls and that the ones which are not compatible are not harmed. 2. Recurring Vulnerability Assessment 2.1. Verify Patching Systems work properly in practice 2.2. Verify passwords match complexity requirements in practice 2.3. Recurring verification of personnel alertness to security events 3. Penetration Testing 3.1. Verify logs quality in practice 3.2. Verify Real-Time Protection/Response Systems work properly in practice 3.3. Verify Real-Time/Scheduled Alerting mechanisms work properly in practice
- 60. 59 | P a g e Preventing physical intrusions Using Mantraps A man trap aka “interlock” aka “air locks” is a small space having two sets of interlocking doors such that the first set of doors must close before the second set opens. Identification may be required for each door, sometimes even possibly different measures for each door. For example, a key may open the first door, but a personal identification number entered on a number pad opens the second. Other methods of opening doors include proximity cards or biometric devices such as fingerprint readers or iris recognition scans. Metal detectors are often built in in order to prevent entrance of people carrying weapons. Such use is particularly frequent in banks and jewelry shops. Mantraps may be configured so that when an alarm is activated, all doors lock and trap the suspect between the doors in the "dead space" or lock just one door to deny access to a secure space such as a data center or research lab. An Effective man trap will only physically contain one person at a time in order to avoid Tail-Gating or Piggy-Backing. Spinning Glass Doors
- 61. 60 | P a g e Turnstiles
- 62. 61 | P a g e Combining man traps with security cameras and facial recognition It is very effective to combine a man trap with a close camera, this results in a time stamped close-up face picture of everyone who entered and left the secure area. In addition, it is extremely effective to combine the man traps camera results with facial recognition solutions in order get a full protection and detection security system.
- 63. 62 | P a g e
- 64. 63 | P a g e Using swipe based biometric authorization devices Not Secure When you use a fingerprint biometrics device, after its scans your fingerprint, the fingerprint stays on the device, can be re-used and also replicated and stolen. Secure Fingerprint Swipe-Scanners, are secure, since you physical delete/“run-over” your own fingerprint when you swipe your finger. Extremely Secure – Full Hand Swipe Full Hand Fingerprint is very hard to obtain and extremely challenging to spoof. Notice that this solution is also swipe based and doesn’t risk the user’s fingerprint.
- 65. 64 | P a g e Strong Authentication Combining Fingerprint swipe with PIN code: Fingerprint Swipe + Magnetic Card Not Secure
- 66. 65 | P a g e Secure Keyboard with Security Not Secure Secure
- 67. 66 | P a g e Extremely Secure Using white noise generators to disturb eavesdropping Low Cost Hardware Solutions 1. Make other noise coming into an area less distracting or 2. To reduce the chance of overhearing adjacent conversations or 3. To reduce the chance of having your conversation overheard by someone else. 4. to aid in alleviating the effects of tinnitus by providing a low-level broad-band noise to help achieve the "habituation" of tinnitus.
- 68. 67 | P a g e Common Technical Specifications: Weight: 12 oz. (340.2 g) Audio Frequency Range: 300Hz - 3KHz Output Sound Level: MAX 92 dB @ 4 ft. Power: two 9 volt alkaline batteries or AC transformer (120 or 240 VAC)
- 69. 68 | P a g e IPhone Applications Studio Six Digital - AudioTools - Generator Sine Wave 1000Hz 6.85dBu 10k 6.87dBu 31Hz 6.75dBu Pink Noise Full bandwidth -20.0dBu Octave band 1k -31.0dBu octave band 125 -31.0dBu Octave band 31 -31.0dBu Octave band 16k -31.0dBu White Noise Full band -28.9dBu Octave bands vary Square Wave 63Hz 3.43dBu 1000Hz 3.44dBu
- 70. 69 | P a g e Rabble Noise Generator Features Was designed by TSCM/counter-surveillance professionals and will protect you against all types of eavesdropping when used in correspondence with the recommendations. Employs a new approach to the problem of conversation protection. Uses a new, speech-like noise which, in the most of cases, has proven to be more efficient when compared to white noise. The noise has been 'compiled' using real human conversations and is similar to the noise of a 'rabble' in busy public places. This type of noise is the most effective when creating interference to voice recorders and listening devices, especially when the size of the protective device is critical. Kinds of listening devices rendered useless by the new “Rabbler”: Voice recorders Radio microphones GSM/3G “bugs” Body-carried video cameras - watches, ties, etc. (jamming of acoustics) Wired microphones Any other type of audio surveillance The Rabbler creates additional barrier interference which masks your speech. It is when a certain noise level is reached that listening devices will record or transmit information, it is extremely difficult, or impossible, to extract the speech component. Since the generator creates a 'speech-like' noise, the cleaning of this sound is extremely difficult or most likely impossible, if the level of noise is sufficient.
- 71. 70 | P a g e Distortion & Reverberation Generator DRUID D-06 Top-of-the-line protection system. This is the only device in the world which can give 100% protection to your conversations against interception or recording. The DRUID D-06 creates powerful interference against all kinds of listening devices! Even if a person is standing next to the participants, they will not be able to understand what is being said. The headsets allow the users to hear each other clearly while the DRUID's central unit produces interference. Powered from 220V or the internal rechargeable battery with a resource time of 3—6 hours. The unit is supplied in a carry case. Not all listening devices can be detected by existing methods. The DRUID D-06 is a unique system for providing protection of human's speech. Remotely controlled radio microphones, wired microphones, passive resonators, miniature voice recorders practically all these devices cannot be detected by conventional methods. Even a modern cellular phone may contain a digital voice recorder; this means that any phone lying on the desktop could be used by an adversary to record a conversation. The generated audio interference cannot be cleared by any noise-clearance methods. At the same time the produced interference does not create any inconvenience to the participants of the negotiation thanks to the special headsets. The DRUID headset allows users to hear each other with crystal clear quality.
- 72. 71 | P a g e Laptop & PC Configurations VDI Motivations for VDI
- 73. 72 | P a g e Poll Results: Is VDI More Expensive Than PC? Annual Facilities Costs PC vs. VDI
- 74. 73 | P a g e Comparing Endpoint PC Security to VDI Security Parameter PC VDI Thin Client/Chip PC Allows working locally if network is down Easy to maintain security Hardware Renewal Complete Hardware should be renewed every (~800$) 5 years Complete Hardware should be renewed every (~400$) 8+ years Privilege Escalation Allows Taking Over Endpoint Taking Over An Entire Server Full Compatibility with External devices, Smart Cards Physical Security Is NOT A Risk No Hard Disk Encryption Is Required Endpoint Backup & Roaming Profiles is not a must Not Vulnerable to Boot Kits and MBR/Bios Viruses
- 75. 74 | P a g e VDI Security Comparison: Citrix XenDesktop vs. VMWare View Security Feature VMWare View 4.6 Citrix XenDesktop 5 Client Authentication Methods Active Directory Kerberos Realm in mixed AD/MIT Kerberos environments RSA SecurID X.509 Certificate Active Directory Kerberos Realm in mixed AD/MIT Kerberos environments RSA SecurID X.509 Certificate Support for 2-factor authentication? Yes Yes Control redirection/mapping of local host hard drives Yes Yes Control Host Clipboard redirection for text copy/paste Yes Yes Control Host Clipboard redirection for files and folders? No, files and folders cannot be copied between host and view using PCoIP Yes Full Screen only mode with no toggle to local host OS Yes, but only with hardware thin client Yes, but only with type 1 deployment Single sign-on support Yes Yes Granular USB redirection control No, just basic usb redirect on or off Yes, very granular criteria including: VID, PID, REL, Class, SubClass, Prot tags in the USB device descriptor field Alow Read-only access to USB Hard drives No, but you can use GPO MSFT policies to accomplish this Yes, very granular criteria including: VID, PID, REL, Class, SubClass, Prot tags in the USB device descriptor field Communication Protocol Used RDP or PCoIP ICA Are communications encrypted natively Yes, if using PCoIP to a Windows 2008 security server. AES 128-bit SSL Yes, if connecting to a Citrix security gateway. AES 128- bit SSL VDI communications can run over a 3rd party SSLVPN connection? Yes Yes VDI can USB sync iOS devices like iPhone and iPad Yes Yes Ability to run VDI client in offline or local mode Yes, as a type 2 hypervisor (i.e. application on an existing OS) Yes, as a type 1 bare metal hypervisor (i.e. boot directly into VDI client) The install of XenClient offline mode requires you to destroy or overwrite your current host OS. It also requires hardware virtualization found only on Intel
- 76. 75 | P a g e vPro family of CPU's. The benefit is that it has better performance because it is access the hardware directly and not through a guest OS like a type 2 hypervisor. The potential drawback is that it dedicates that host to being just a XenClient unless you enable dual booting. In some cases this is actually a plus since it solves the security issues that come with having a guest OS that VDI runs on top off. Ability to manage offline VDI clients Yes, you can also force the user to periodically check-in their VDI so it is properly backed up and updated. No, but automated backups are performed by the client Ability to encrypt VDI files and folders on the guest OS Yes Yes, called XenVault. Uses up to 256-bit AES encryption. Can be wiped centrally/remotely if needed Lockout VDI if communication to server is lost for X time period? Yes Unknown Microsoft Active Directory is required for policy settings of VDI? No Yes Control mapping to host drives Yes, RDP only Yes Built-in bandwidth protocol management Yes, using PCoIP Yes, Limit bandwidth per session Restrict access based on time/location/device type No Yes Restrict VDI functionality based on time/location/device type No Yes IPv6 Support No No FIPS 140-2 Compliant Yes Yes VDI Security Best Practices Whitepaper Published Yes Yes Embedded firewall at VDI headend Yes, vShield Yes, Citrix Secure Gateway VDI Anti-virus offload to virtual appliance Yes, vShield Endpoint required. Removes requirement for AV clients on each VDI host. Yes, using integration with Mcafee MOVE A/V. Removes requirement for AV clients on each VDI host Supports multiple AD forests and multiple AD domains Yes Yes As you can see, both vendors have compelling offers with their own strengths and weaknesses. I don't see a huge security advantage of one over the other. Instead, your choice will depend on your specific requirements more than anything else. Technology changes rapidly, especially in the VDI space, so be sure to validate what I have here with other sources or the vendors
- 77. 76 | P a g e themselves. If you see something that has become no longer true please post a comment and I will update this posting. If you know of some security comparisons I should have included please post them as well. Data as a service Data as a service, or DaaS, is a cousin of software as a service. Like all members of the "as a Service" (aaS) family, DaaS is based on the concept that the product, data in this case, can be provided on demand to the user regardless of geographic or organizational separation of provider and consumer. Additionally, the emergence of service-oriented architecture (SOA) has rendered the actual platform on which the data resides also irrelevant. This development has enabled the recent emergence of the relatively new concept of DaaS. Traditionally, most enterprises have used data stored in a self-contained repository, for which software was specifically developed to access and present the data in a human-readable form. One result of this paradigm is the bundling of both the data and the software needed to interpret it into a single package, sold as a consumer product. As the number of bundled software/data packages proliferated and required interaction among one another, another layer of interface was required. These interfaces, collectively known as enterprise application integration (EAI), often tended to encourage vendor lock-in, as it is generally easy to integrate applications that are built upon the same foundation technology. The result of the combined software/data consumer package and required EAI middleware has been an increased amount of software for organizations to manage and maintain, simply for the use of particular data. In addition to routine maintenance costs, a cascading amount of software updates are required as the format of the data changes. The existence of this situation contributes to the attractiveness of DaaS to data consumers because it allows for the separation of data cost and usage from that of a specific software or platform. Benefits Data as a Service brings the notion that data quality can happen in a centralized place, cleansing and enriching data and offering it to different systems, applications or users, irrespective of where they were in the organization or on the network. As such, Data as Service solutions provide the following advantages: Agility – Customers can move quickly due to the simplicity of the data access and the fact that they don’t need extensive knowledge of the underlying data. If customers require a slightly different data structure or has location specific requirements, the implementation is easy because the changes are minimal. Cost-effectiveness – Providers can build the base with the data experts and outsource the presentation layer, which makes for very cost effective user interfaces and makes change requests at the presentation layer much more feasible. Data quality – Access to the data is controlled through the data services, which tends to improve data quality because there is a single point for updates. Once those services are tested thoroughly, they only need to be regression tested if they remain unchanged for the next deployment.
- 78. 77 | P a g e Security Like any other cloud based service there are several main issues: 1. Network downtime – vendor or client downtime for maintenance, disaster or Denial of Service attacks completely deny the ability of the user’s to work 2. Data Security – Data is physically stored on the vendor’s remote servers and may read, modified and deleted by: mistake, bribery, extortion and etc… 3. Data Security – Over the internet - All the information is transferred on the wire and physically leaves the organizations computers. This enables countries and enemies to record, decrypt traffic and obtain secret information PC Metal Locking
- 79. 78 | P a g e Disabling Internal/External USB, DVD, CD-ROM Boot Organizations should implement an intensive Endpoint Security Solution for Device Control. The solution must cover the following aspects: 1. Protected Physical Interfaces 1.1.1.USB 1.1.2.FireWire 1.1.3.PCMCIA 1.1.4.Secure Digital (SD) 1.1.5.Parallel 1.1.6.Serial 1.1.7.Modem 1.1.8.Internal Ports 2. Protected Wireless Interfaces 2.1.1.Wi-Fi 2.1.2.Bluetooth 2.1.3.Infra-Red (IrDA) 2.1.4.Protected Storage Devices 3. External Hard Drives 3.1.1.Removable Storage Devices 3.1.2.CD / DVD Drives 3.1.3.Floppy Drives 3.1.4.Tape Drives
- 80. 79 | P a g e Security Policy - Flexible Strategy, Simple Implementation Different organizations have different needs and different corporate cultures. That’s why device control solutions allows administrators to first choose their endpoint security strategy, and then implement it in line with their unique organizational needs. Device control solutions creates forensic logs of all data moving in and out of the organization, allowing administrators to create policies that don’t necessarily restrict device usage, but allow full visibility of device activity and content traffic. Through a flexible management console, device control solutions allow administrators to create comprehensive and granular endpoint security policies. Device control solutions - Features and Benefits Granular control - detects and restricts devices by device type, device model or unique serial number. Data awareness - control the transfer of files both to and from external storage devices according to the file types. Removable media encryption - encrypts corporate data in motion on removable storage devices, external hard drives, and CD/DVDs. Track offline usage of removable storage - tracks file transfers to/from encrypted devices on non-corporate computers (offline). Built-in compliance policies - includes detailed configurations for achieving security policies that are mapped to specific regulatory compliance standards such as PCI, HIPAA and SOX. Granular Wi-Fi control - by MAC address, SSID, or the security level of the network Anti bridging - prevents hybrid network bridging by blocking Wi-Fi, Bluetooth, Modems or IrDA while the PC is connected to the wired corporate LAN. Anti-hardware Keylogger - blocks or detects both USB and PS/2 hardware Keyloggers. U3 and auto run control - turns U3 USB drives into regular USB drives while attached to organization endpoints, protecting against auto-launch programs by blocking auto run. Flexible and intuitive management - automatically synchronizes with Microsoft Active Directory and Novell eDirectory. If the organization decides to allow USB device usage such as USB Disk-On-Keys and USB Storage devices, it should use secure solutions. Secure Disk-On-Key solutions are: 4. Encrypted and: Requires a password Requires a certificate and a password Requires a biometric fingerprint Requires a certificate and a biometric fingerprint 5. Device has a physical switch between two modes: Read Only Read and Write
- 81. 80 | P a g e Biometric Integrated USB Devices: Biometric Integrated USB Devices:
- 82. 81 | P a g e Setting Bios Passwords BIOS passwords can add an extra layer of security for desktop and laptop computers. They are used to either prevent a user from changing the BIOS settings or to prevent the PC from booting without a password. Unfortunately, BIOS passwords can also be a liability if a user forgets their password, or changes the password to intentionally lock out the corporate IT department. Sending the unit back to the manufacturer to have the BIOS reset can be expensive and is usually not covered in the warranty. Never fear, all is not lost. There are a few known backdoors and other tricks of the trade that can be used to bypass or reset the BIOS Upgrading to Windows 7 + UAC User Account Control User Account Control (UAC) helps defend your PC against hackers and malicious software. Any time a program wants to make a major change to your computer, UAC lets you know and asks for permission. In Windows 7, UAC is now less intrusive and more flexible. Fewer Windows 7 programs and tasks require your consent. If you have administrator privileges on your PC, you can also fine-tune UAC's notification settings in Control Panel.
- 83. 82 | P a g e User Account Control (UAC) is a feature in Windows that can help you stay in control of your computer by informing you when a program makes a change that requires administrator-level permission. UAC works by adjusting the permission level of your user account. If you’re doing tasks that can be done as a standard user, such as reading e-mail, listening to music, or creating documents, you have the permissions of a standard user—even if you’re logged on as an administrator. When changes are going to be made to your computer that requires administrator-level permission, UAC notifies you. If you are an administrator, you can click Yes to continue. If you are not an administrator, someone with an administrator account on the computer will have to enter their password for you to continue. If you give permission, you are temporarily given the rights of an administrator to complete the task and then your permissions are returned back to that of a standard user. This makes it so that even if you're using an administrator account, changes cannot be made to your computer without you knowing about it, which can help prevent malicious software (malware) and spyware from being installed on or making changes to your computer. When your permission or password is needed to complete a task, UAC will notify you with one of four different types of dialog boxes. The table below describes the different types of dialog boxes used to notify you and guidance on how to respond to them. Icon Type Description A setting or feature that is part of Windows needs your permission to start. This item has a valid digital signature that verifies that Microsoft is the publisher of this item. If you get this type of dialog box, it's usually safe to continue. If you are unsure, check the name of the program or function to decide
- 84. 83 | P a g e Icon Type Description if it’s something you want to run. A program that is not part of Windows needs your permission to start. This program has a valid digital signature, which helps to ensure that the program is what it claims to be and verifies the identity of the publisher of the program. If you get this type of dialog box, make sure the program is the one that you want to run and that you trust the publisher. A program with an unknown publisher needs your permission to start. This program doesn't have a valid digital signature from its publisher. This doesn't necessarily indicate danger, as many older, legitimate programs lack signatures. However, you should use extra caution and only allow a program to run if you obtained it from a trusted source, such as the original CD or a publisher's website. If you are unsure, look up the name of the program on the Internet to determine if it is a known program or malicious software. You have been blocked by your system administrator from running this program. This program has been blocked because it is known to be untrusted. To run this program, you need to contact your system administrator. We recommend that you log on to your computer with a standard user account most of the time. You can browse the Internet, send e-mail, and use a word processor, all without an administrator account. When you want to perform an administrative task, such as installing a new program or changing a setting that will affect other users, you don't have to switch to an administrator account; Windows will prompt you for permission or an administrator password before performing the task. We also recommend that you create standard user accounts for all the people who use your computer.
- 85. 84 | P a g e Internet Explorer’s 9 Protected Mode Memory Protection Mechanisms Security Cookie (Canary) • This mechanism was created to avoid successful code execution when overwriting stack variables. • The mechanism creates a random value on process runtime, plants it before the functions return pointer and verifying it before calling the “ret” command. • While the application is attacked, and the return address is overwritten, this value is also overwritten, the memory overwrite is being detected and the application does not call the return command. (it usually closes itself)
- 86. 85 | P a g e • This way, there is no way to overwrote the return address (EIP) without the software knowing it and protecting itself SafeSEH • This mechanism was invented to prevent attackers from executing code by overwriting the error handler pointer • SHE overwrites were used to bypass the Stack’s Security Cookie by overwriting the exception handler and causing an exception, therefore executing code before the function returns and before the stack cookie is being verified.
- 87. 86 | P a g e • SafeSEH denies the ability of an attacker to execute code by overwriting the SHE handler by maintaining a white-list of allowed SHE function pointers, gathered at compilation time and there no unauthorized dynamically added/written SHE pointer will be executed. • The problem with this method is that old unsafe libraries that are loaded into the process at known addresses can be used as trampolines to execute code.
- 88. 87 | P a g e Address space layout randomization (ASLR) Address space layout randomization (ASLR) is a computer security method which involves randomly arranging the positions of key data areas, usually including the base of the executable and position of libraries, heap, and stack, in a process’s address space. Benefits Address space randomization hinders some types of security attacks by making it more difficult for an attacker to predict target addresses. For example, attackers trying to execute return-to-libc attacks must locate the code to be executed, while other attackers trying to execute shellcode injected on the stack have to find the stack first. In both cases, the related memory addresses are obscured from the attackers. These values have to be guessed, and a mistaken guess is not usually recoverable due to the application crashing. The most critical benefits are: • ASLR is a mechanism which randomizes the modules addresses in the application’s memory space, creating an unpredictable process layout and denying attackers from knowing the memory addresses of useful code and system calls. • The system calls/APIs addresses are being randomizes with each system reboot • The application’s modules addresses are being randomizes with process initialization • ASLR eliminates SafeSEH bypassing with old libraries, stack cookie bypass using return- to-libc attacks and disabling DEP using return-to-libc.
- 89. 88 | P a g e Visualization of ASLR Changes to system Memory per Boot NX (No eXecute – Hardware DEP) • NX is a bit in each the PageEntry which tells the CPU/Operating System if the bytes in this memory page is code and is meant and allowed to be executed. • This bits purpose is denying attackers from executing code while attacking applications • When the attacker executes the attack, he makes a jump into his own code, when DEP is enables the application closes right after the jump, since it is not allowed to execute code from user/attacker influenced memory locations such as the Stack and the Head.
- 90. 89 | P a g e
- 91. 90 | P a g e DEP and ASLR Protection Activation State:
- 92. 91 | P a g e
- 93. 92 | P a g e Data Execution Prevention - DEP When DEP detects that code data is trying execute from a data memory region: DEP, ASLR, IE Protected Mode and UAC’s Impact on Security in Windows: 1. All the following statements ignore the possibility of privilege escalation and remote kernel exploits aside. These will only be fully mitigated once the entire kernel memory space will be completely randomized by ASLR. 2. The potential damage of all social engineering attacks automatically downgraded to accessing information at the current user’s level. Attacker cannot take over the machine, cannot install malicious software and drivers that are required to attack and take over the network. (clicking a inserting a malicious CD, USB, Clicking a virus, infected cracks) 3. Combination of Internet Explorer 9 “Protected Mode” with UAC reduces the risk of internet exploits to the bare minimum possible. When a successful exploitation may only achieve guest privilege and rights. 4. Integration of DEP and ASLR results in mitigation 99% of the known exploitation techniques as of today. Therefore, they provide the ultimate protection, better than any external software such as Smart Anti-Virus or HIPS memory patches. 5. Combination of Windows 7/2008, SafeSEH, DEP, ASLR, UAC and Internet Explorer Protected Mode provides a security baseline 100 times stronger than Windows XP and 2003 Server.
- 94. 93 | P a g e Encrypting Laptops Laptops are a growing practice in most organizations. As the amount of employees who use laptops grown, so does the amount of sensitive data stored on them. The common attacker is fully aware that it is fairly easy and possible to steal a laptop and: 1. Obtain all of the sensitive data on it. 2. Use stored credentials on it to connect to the company’s VPN and online systems Besides the risks for a laptop’s data when it is stolen, there are few other reasons to use Full disk encryption: 1. Full disk encryption protects the data itself 2. Full disk encryption protects the operating systems data and avoid “Winlogon Bypass” with well-known boot-CDs such as “ERD Commander” Managed Solution – Mcafee / Symantec On windows, the solutions are pretty much the same. When it comes to encrypting and managing operating systems other than windows, Mcafee is much more grown as a product. As MAC adoption to enterprise has grown, it cannot be disregarded in the comparison. Encryption Product Comparison for Apple Macintosh Product Name Company Name First released Maintained? BestCrypt Jetico 1993 SecureDoc WinMagic Inc. 1997 PGPDisk PGP Corporation 1998 Check Point FDE Check Point Software 1999 FileVault Apple Inc. 2003 TrueCrypt TrueCrypt Foundation 2004 Bloombase Keyparc Bloombase 2007 McAfee Endpoint Encryption McAfee, Inc. 2007 SafeGuard Enterprise Sophos (Utimaco) 2007 Symantec Endpoint Encryption Symantec 2008 FileVault 2 Apple Inc. 2011
- 95. 94 | P a g e Relevant Features for Full Disk Encryption Product Comparison 1. Hidden containers: Whether hidden containers (an encrypted container (A) within another encrypted container (B) so the existence of container A cannot be established) can be created for deniable encryption. Note that some modes of operation like CBC with a plain IV can be more prone to watermarking attacks than others. 2. Pre-boot authentication: Whether authentication can be required before booting the computer, thus allowing one to encrypt the boot disk. 3. Custom authentication: Whether custom authentication mechanisms can be implemented with third-party applications.[clarification needed] 4. Multiple keys: Whether an encrypted volume can have more than one active key. 5. Passphrase strengthening: Whether key strengthening is used with plain text passwords to frustrate dictionary attacks, usually using PBKDF2. 6. Hardware acceleration: Whether dedicated cryptographic accelerator expansion cards can be taken advantage of. 7. Trusted Platform Module: Whether the implementation can use a TPM cryptoprocessor. 8. Filesystems: what Filesystems are supported? 9. Two-factor authentication: Whether optional security tokens (hardware security modules, such as Aladdin eToken and smart cards) are supported (for example using PKCS#11) Product Feature Comparison Table Name Hidden container s Pre-boot authenticatio n Custom authenticatio n Multipl e keys Passphrase strengthenin g Hardware acceleratio n TP M Filesystems Two-factor authenticatio n BestCrypt OS Bloombase ? ? Check Point FDE ? ? ? ? FileVault 2 HFS+ PGPDisk ? ? ? McAfee Endpoint OS SafeGuard Ent. OS SecureDoc ? Symantec Endpoi nt NTFS,FAT3 2 TrueCrypt only on Windows OS
- 96. 95 | P a g e Aloaha Secure Stick NTFS,FAT3 2 Layering & Partition Type Support 1. Whole disk: Whether the whole physical disk or logical volume can be encrypted, including the partition tables and master boot record. Note that this does not imply that the encrypted disk can be used as the boot disk itself; refer to "pre-boot authentication" in the features comparison table. 2. Partition: Whether individual disk partitions can be encrypted. 3. File: Whether the encrypted container can be stored in a file (usually implemented as encrypted loop devices). 4. Swap space: Whether the swap space (called a "pagefile" on Windows) can be encrypted individually/explicitly. 5. Hibernation file: Whether the hibernation file is encrypted (if hibernation is supported). Name Whole disk Partition File Swap space Hibernation file BestCrypt Bloombase Keyparc Check Point Full Disk Encryption ? FileVault 2 PGPDisk McAfee Endpoint Encryption (SafeBoot) SafeGuard Enterprise Each sector on disk is encrypted SecureDoc Symantec Endpoint Encryption TrueCrypt
- 97. 96 | P a g e Modes of operation Different modes of operation supported by the software. Note that an encrypted volume can only use one mode of operation. 1. CBC with predictable IVs: The CBC (cipher block chaining) mode where initialization vectors are statically derived from the sector number and are not secret; this means that IVs are re-used when overwriting a sector and the vectors can easily be guessed by an attacker, leading to watermarking attacks. 2. CBC with secret IVs: The CBC mode where initialization vectors are statically derived from the encryption key and sector number. The IVs are secret, but they are re-used with overwrites. Methods for this include ESSIV and encrypted sector numbers (CGD). 3. CBC with random per-sector keys: The CBC mode where random keys are generated for each sector when it is written to, thus does not exhibit the typical weaknesses of CBC with re-used initialization vectors. The individual sector keys are stored on disk and encrypted with a master key. (See GBDE for details) 4. LRW: The Liskov-Rivest-Wagner tweak able narrow-block mode, a mode of operation specifically designed for disk encryption. Superseded by the more secure XTS mode due to security concerns. 5. XTS: XEX-based Tweaked Codebook mode (TCB) with Cipher Text Stealing (CTS), the SISWG (IEEE P1619) standard for disk encryption. Name CBC w/ predictable IVs CBC w/ secret IVs CBC w/ random per- sector keys LRW XTS BestCrypt Bloombase Keyparc ? ? ? ? Check Point Full Disk Encryption ? ? ? ? ? FileVault FileVault 2 PGPDisk ? ? ? ? ? McAfee Endpoint Encryption (SafeBoot) SafeGuard Enterprise ? ? ? ? ? SecureDoc ? ? ? ? ? Symantec Endpoint Encryption
- 98. 97 | P a g e TrueCrypt Legacy support Legacy support Non-Managed - TrueCrypt TrueCrypt is a free software application used for on-the-fly encryption (OTFE). It can create a virtual encrypted disk within a file or encrypt a partition or (under Microsoft Windows except Windows 2000) the entire storage device (pre-boot authentication). Operating systems TrueCrypt supports Microsoft Windows, Mac OS X, FreeBSD, and Linux operating systems (using FUSE). Both 32-bit and 64-bit versions of these operating systems are supported, except for Windows IA-64 (not supported) and Mac OS X 10.6 Snow Leopard (runs as a 32-bit process). The version for Windows 7, Windows Vista, or Windows XP can encrypt the boot partition or entire boot drive. There is an independent, compatible implementation, tcplay, for Dragonfly BSD and Linux. Cryptographic algorithms Individual algorithms supported by TrueCrypt are AES, Serpent, and Twofish. Additionally, five different combinations of cascaded algorithms are available: AES-Twofish, AES-Twofish- Serpent, Serpent-AES, Serpent-Twofish-AES and Twofish-Serpent. The cryptographic hash functions used by TrueCrypt are RIPEMD-160, SHA-512, and Whirlpool. Modes of operation TrueCrypt currently uses the XTS mode of operation. Prior to this, TrueCrypt used LRW mode in versions 4.1 through 4.3a, and CBC mode in versions 4.0 and earlier. XTS mode is thought to be more secure than LRW mode, which in turn is more secure than CBC mode. Although new volumes can only be created in XTS mode, TrueCrypt is backward compatible with older volumes using LRW mode and CBC mode. Later versions produce a security warning when mounting CBC mode volumes and recommend that they be replaced with new volumes in XTS mode.
- 99. 98 | P a g e First Time Full Disk Encryption Takes Just a Few Hours Typing Password Is Required On Boot:
- 100. 99 | P a g e Hidden Volumes Supported Setting Laptops “Out of Organization Personal Firewall Policy” The Threats of Using a Laptop outside of the organization 1. Attacking the laptop via hostile networks by connecting to communication ports it is listening on, such as file sharing and remote desktop. 2. User unknowingly or malicious user intentionally downloading hostile files such as: Malware, Spyware, Virus, Worm, Trojan horse, Keylogger, Fraudware, RansomWare. So that in the user’s next connection to the organization’s network, he project risk on the users and servers he can access on the network level. The complexity of choosing the methods of blocking potentially hostile communication: 1. The ideal solution to defense the organization’s laptops outside of its perimeter is defining a list of approved communication ports and protocols. (Port & Protocol Whitelist) 2. The problem in choosing the ideal solution is that limiting the communication to specific services (while listing) breaks the normal functioning of any software which uses ports or protocols that were not defined. Some of this software might be low risk applications such as Computer games, video Streaming Servers and etc…
- 101. 100 | P a g e 3. Therefore, the recommended method at this point is blocking the communication using Black List method while we select a list of applications and protocols of applications with high risk such as: Remote Control, File Sharing, VPN Clients and the most commonly used Trojan horses. CommentLocal PortsRemote PortsApplicationPurpose 3389 (TCP/UDP) 3389 (TCP/UDP)Microsoft RDP Remote Control Software (With File Sharing) 3283 (TCP/UDP) 5900, 5988 (TCP) 3283 (TCP/UDP) 5900, 5988 (TCP) Apple Remote Desktop None80, 5938 (TCP)TeamViewer 2002 (TCP)80, 443 (TCP)LogMeIn 443 (TCP) 5800/5900 (TCP) 6800/6900 (TCP) 443 (TCP)ShowMyPC 5632 (TCP/UDP) 5632 (TCP/UDP)PCAnywhere 5500, 5900, 5901, 5800 (TCP) 5500, 5900, 5901, 5800 (TCP) VNC RealVNC TightVNC UltraVNC None80, 443 (TCP) Bomgar Zoho Meeting/Assist 5279, 4279 (TCP) 5279, 4279 (TCP)Anyplace Control None80, 443 (TCP)TouchMyPC None80, 443 (TCP)RSupport RemoteCall None80, 443 (TCP)BeamYourScreen None 80, 443, 7612, 7616, 7617 (TCP) ISL Online / ISL Light 139, 445139, 445 (TCP)NetBIOSNetwork File
- 102. 101 | P a g e CommentLocal PortsRemote PortsApplicationPurpose (TCP)Samba (Linux)Sharing 548 (TCP)548 (TCP)Apple File Sharing Old Emule Client Port 4672 (TCP)4672 (TCP) Emule eDonkey P2P File Sharing Old Emule Client Port 4662 (UDP)4662 (UDP) Emule Web Server 4711 (TCP)4711 (TCP) 1214 (TCP)1214 (TCP)Kazza None6699 (TCP)iMesh None6346 (TCP/UDP)Gnutella None6881 - 6889 (TCP/UDP)Azureus None 411, 1025 to 32000 (TCP/UDP) DC++ None6346, 6347 (TCP/UDP)Limewire None 41170 – 41350 (TCP/UDP) Blubster None3689 (TCP/UDP)iTunes 80 (TCP) 443 (TCP) NoneSkype P2P Chat/Voice With File Sharing None 1863, 5190, 6891-6901 (TCP/UDP) MSN Messenger None 5190 (TCP/UDP) 4000 (UDP) ICQ None5010 (TCP)Yahoo Messenger None5190 (TCP/UDP) AOL Instant Messenger None8080, 8090 (TCP)WebcamXPVideo/Voice Sharing (Streaming Servers) None8000, 8001 (TCP)Winamp Streaming None 5061, 10000 – 20000 (UDP) Vonage VOIP Software None11675 (TCP/UDP)VPhone
- 103. 102 | P a g e CommentLocal PortsRemote PortsApplicationPurpose None 8767, 14534, 51234 (TCP/UDP) TeamSpeak 1-1024None FTP, Telnet, SNMP, IMAP, POP3, SMTP, HTTP, HTTPS, HTTP-Proxy… Common Server Listening Ports 1194, 5000 (UDP) 1194, 5000 (UDP)OpenVPN VPN Servers None1723 (TCP)Generic PPTP 1701, 500 (UDP) 1701, 500 (UDP)Juniper 500, 4500, 10000 (UDP) 500, 4500, 10000 (UDP)Cisco 500, 2746, 18233 (UDP) 500, 2746, 18233 (UDP) 18231, 18232 (TCP) Check-Point 1224 (UDP)1224 (TCP/UDP)VPNz 2865 (UDP)2865 (TCP/UDP)pit-vpn Network Equipment Understanding Layer 2 & 3 Security 1. Layer 2 Attack Landscape 2. Attacks and Counter Measures a. VLAN Hopping b. MAC Attacks c. DHCP Attacks d. ARP Attacks e. Spoofing Attacks f. General Attacks
- 104. 103 | P a g e
- 105. 104 | P a g e
- 106. 105 | P a g e
- 107. 106 | P a g e
- 108. 107 | P a g e
- 109. 108 | P a g e
- 110. 109 | P a g e
- 111. 110 | P a g e
- 112. 111 | P a g e
- 113. 112 | P a g e
- 114. 113 | P a g e
- 115. 114 | P a g e
- 116. 115 | P a g e
- 117. 116 | P a g e
- 118. 117 | P a g e
- 119. 118 | P a g e
- 120. 119 | P a g e
- 121. 120 | P a g e
- 122. 121 | P a g e
- 123. 122 | P a g e
- 124. 123 | P a g e
- 125. 124 | P a g e
- 126. 125 | P a g e
- 127. 126 | P a g e
- 128. 127 | P a g e
- 129. 128 | P a g e
- 130. 129 | P a g e
- 131. 130 | P a g e
- 132. 131 | P a g e
- 133. 132 | P a g e
- 134. 133 | P a g e
- 135. 134 | P a g e
- 136. 135 | P a g e
- 137. 136 | P a g e
- 138. 137 | P a g e
- 139. 138 | P a g e
- 140. 139 | P a g e
- 141. 140 | P a g e
- 142. 141 | P a g e
- 143. 142 | P a g e
- 144. 143 | P a g e
- 145. 144 | P a g e
- 146. 145 | P a g e
- 147. 146 | P a g e
- 148. 147 | P a g e
- 149. 148 | P a g e
- 150. 149 | P a g e
- 151. 150 | P a g e
- 152. 151 | P a g e
- 153. 152 | P a g e
- 154. 153 | P a g e
- 155. 154 | P a g e
- 156. 155 | P a g e Layer 3+ Security 1. Access Control Lists (ACLs) a. VLANs are the most cost effective solution for Layer 2 security, but they DO NOT PROVIDE ANY LAYER 3 SECURITY. b. This means that ANY ATTACK ON AN IP LEVEL CAN BE EXECUTED WITH VLANS c. In order to implement Layer 3 security, it is best to change the network design to have an “Application Aware Back-Bone Firewall” configured as a Trunk before the backbone router. d. The low-cost, manual, semi-solution is implementing Layer 3 Access List Rules (ACLs) which define which VLANs can access which other networks/VLANs. e. ACLs are very hard to maintain and require constant updates by network personnel. 2. Utilizing Security Features implemented in major vendors network equipment. These features include: a. DDoS Protection
- 157. 156 | P a g e b. Security ACLs and VACLs c. QoS Rate Limiting d. uRPF Check e. Traffic Storm Control f. Network Under SYN Attack g. ARP Policing h. Recommended Rate-Limiter Configuration i. Hardware-Based Rate Limiters on the PFC3 j. Configuring Sticky ARP 3. Quality of Service (QoS) a. Limiting each VLAN to a specific amount of traffic from the entire bandwidth b. Limiting each User in each VLAN to a specific amount of traffic from maximum bandwidth limit assigned to that VLAN c. These allow network stability and clear operation in case of worms and viruses d. These allow immediate alerts on “VLAN bandwidth QoS capacity hit” that should be integrated into a SIEM with a response script to shut down the specific port. Such an alert would clearly notify of an abnormal activity with specific VLAN label explaining the logical organizational unit and the specific IP in that VLAN.
- 158. 157 | P a g e An example of the right way to divide VLANs to matching logical business units
- 159. 158 | P a g e Maximizing Your Network Security with Private VLANs (PVLAN) As discussed in the "Protected Ports (PVLAN Edge") section, the PVLAN feature prevents interhost communications providing port-based security among adjacent ports within a VLAN across one or more switches. PVLAN provides Layer 2 isolation to quarantine hosts from one another among ports within the same PVLAN. Access ports in a PVLAN are allowed to communicate only with the certain designated router ports. In most cases, this is the default gateway IP address. Private VLANs and normal VLANs can coexist on the same switch. The PVLAN feature allows segregating traffic at Layer 2, thereby transforming a broadcast segment into a non-broadcast multi-access-like segment. To prevent interhost and inter-server communication, PVLAN can be used efficiently because the number of subnets or VLANs is greatly reduced, although the segmented approach within a single network segment is still achieved. The number is reduced because there is no need to create extra subnet/VLANs. NOTE The PVLAN feature is not available on all Cisco switches. Refer to Table 4-1 for a list of supported platforms. Table 4-1. VLAN Support on Catalyst Switches Platform Software Version Isolated VLAN PVLAN Edge (Protected Port) Community VLAN Catalyst 8500 Not Supported — — — Catalyst 6500/6000—CatOS on Supervisor and Cisco IOS on MSFC 5.4(1) on Supervisor and 12.0(7)XE1 on MSFC Yes N/A Yes Catalyst 6500/6000—Cisco IOS System software 12.1(8a)EX, 12.1(11b)E1 Yes N/A Yes Catalyst 5500/5000 Not Supported — — — Catalyst 4500/4000—CatOS 6.2(1) Yes N/A Yes Catalyst 4500/4000—Cisco IOS 12.1(8a)EW Yes N/A 12.2(20)EW Catalyst 3750 12.2(20)SE—EMI Yes 12.1(11)AX Yes Catalyst 3750 Metro 12.1(14)AX No Yes No Catalyst 3560 12.2(20)SE—EMI Yes 12.1(19)EA1 Yes Catalyst 3550 12.1(4)EA1 No Yes Not Currently Supported
- 160. 159 | P a g e Platform Software Version Isolated VLAN PVLAN Edge (Protected Port) Community VLAN Catalyst 2970 12.1(11)AX No Yes No Catalyst 2955 12.1(6)EA2 No Yes No Catalyst 2950 12.0(5.2)WC1, 12.1(4)EA1 No Yes Not Currently Supported Catalyst 2900XL/3500XL 12.0(5)XU (on 8MB switches only) No Yes No Catalyst 2948G-L3 / 4908G- L3 Not Supported — — — Catalyst 2948G/2980G 6.2 Yes N/A Yes Catalyst 2940 12.1(13)AY No Yes No Catalyst 1900 Not Supported — — — The list that follows describes three types of PVLAN ports, as shown in Figure 4-1a: Promiscuous: A promiscuous port can communicate with all interfaces, including the isolated and community ports within a PVLAN. The function of the promiscuous port is to move traffic between ports in community or isolated VLANs. It can use access lists to identify which traffic can pass between these VLANs. Only one promiscuous port is allowed per single PVLAN, and it serves all the community and isolated VLANs in the Private VLAN. Isolated: An isolated PVLAN port has complete Layer 2 segregation from all the other ports within the same PVLAN, but not from the promiscuous ports. Traffic from the isolated port is forwarded only to the promiscuous ports and none other. Community: Community ports are logically combined groups of ports in a common community and can pass traffic among themselves and with promiscuous ports. Ports are separated at Layer 2 from all other interfaces in other communities or isolated ports within their PVLAN.
- 161. 160 | P a g e Figure 4-1a PVLAN Components It is possible for isolated and community port traffic to enter or leave the switch through a trunk interface because trunks support VLANs carrying traffic among isolated, community, and promiscuous ports. Hence, PVLAN ports are associated with a separate set of VLANs that are used to create the PVLAN structure. A PVLAN uses VLANs in following three ways: As a primary VLAN: Carries traffic from a promiscuous port to isolated, community, and other promiscuous ports in the same primary VLAN. As an isolated VLAN: Carries traffic from isolated ports to a promiscuous port. Ports in the isolated VLAN cannot communicate at Layer 2 with any other port within the Private VLAN (either another community VLAN port or a port in the same isolated VLAN). To communicate with other ports, it must go through the promiscuous port. As a community VLAN: Carries traffic between community ports within the same community VLAN and to promiscuous ports. Ports in the community VLAN can communicate at Layer 2 with each other (only within the same community VLAN) but cannot communicate with ports in other community or isolated VLANs. To communicate with other ports, they must go through the promiscuous port. Multiple community VLANs can be configured in a PVLAN. Figure 4-1a depicts the basic PVLAN components and the different types of PVLAN ports. The isolated and community VLANs are also called secondary VLANs. PVLANs can be extended across multiple devices by trunking the primary, isolated, and community VLANs to other devices that support PVLANs. In summary, a Private VLAN contains three elements: the Private VLAN itself, the secondary VLANs (known as the community VLAN and isolated VLAN), and the promiscuous port.
- 162. 161 | P a g e Figure 4-1b PVLAN Traffic Flow Policies Configuring PVLAN NOTE When enabling PVLAN, it is important to remember to configure the switch as VTP transparent mode before you can create a PVLAN. PVLANs are configured in the context of a single switch and cannot have members on other switches. Perform the following steps to configure the PVLAN feature: Step 1 Create the primary and secondary PVLANs. For example, configure VLAN 101 as a primary VLAN, VLANs 201 to 202 as community VLANs, and VLAN 301 as an isolated VLAN. o Hostname(config)# vlan 101 o Hostname(config-vlan)# private-vlan primary o Hostname(config)# vlan 201 o Hostname(config-vlan)# private-vlan community o Hostname(config)# vlan 202 o Hostname(config-vlan)# private-vlan community o Hostname(config)# vlan 301
- 163. 162 | P a g e o Hostname(config-vlan)# private-vlan isolated Step 2 Associate the secondary VLANs to the primary PVLAN. For example, associate community VLANs 201 to 202 and isolated VLAN 301 with the primary VLAN 101. o Hostname(config)# vlan 101 o Hostname(config-vlan)# private-vlan association 201-202,301 o Hostname(config-vlan)# exit NOTE Only one isolated VLAN can be mapped to a primary VLAN, but multiple community VLANs can be mapped to a primary VLAN. Step 3 Map secondary VLANs to the SVI (Switched Virtual Interface), which is the Layer 3 VLAN interface of a primary VLAN to allow Layer 3 switching of PVLAN ingress traffic. o For example, permit routing of secondary VLAN ingress traffic from VLANs 201 to 202 and 301 to the private VLAN 101 SVI (Layer 3 interface). o Hostname(config)# interface vlan 101 o Hostname(config-if)# private-vlan mapping add 201-202,301 Step 4 Configure a Layer 2 interface as an isolated or community port, and associate the Layer 2 port to the primary VLAN and selected secondary VLAN pair. For example, configure interface FastEthernet 1/1 as a PVLAN host port in community VLAN 201, map it to a private-secondary PVLAN pair, configure FastEthernet 1/2 as a PVLAN host port in isolated VLAN 301, and map it to a private-secondary PVLAN pair. o Hostname(config)# interface Fastethernet 1/1 o Hostname(config-if)# switchport mode private-vlan host o Hostname(config-if)# switchport private-vlan host-association 101 201 o Hostname(config)# interface Fastethernet 1/2 o Hostname(config-if)# switchport mode private-vlan host o Hostname(config-if)# switchport private-vlan host-association 101 301 Step 5 Configure a Layer 2 interface as a PVLAN promiscuous port and map the PVLAN promiscuous port to the primary VLAN and to the selected secondary VLAN pair. For example, configure interface FastEthernet 1/10 as a PVLAN promiscuous port, and map it to a private-secondary PVLAN pair. o Hostname(config)# interface Fastethernet 1/10 o Hostname(config-if)# switchport mode private-vlan promiscuous
- 164. 163 | P a g e o Hostname(config-if)# switchport private-vlan mapping 101 201-202,301 Use the show interface private-vlan mapping command and the show interface [interface-id] switchport command to verify the configuration. Upgrading Router/Switch Firmware Write Unsaved configurations ciscorouter# write memory Building configuration… [OK] Check space on Flash Memory ciscorouter# show flash Backup Startup Configuration Setup a TFTP server in the same IP range as the Cisco device to back up the config, IOS image and also for later to upload the new IOS image. ciscorouter# copy startup-config tftp Address or name of remote host []? 192.168.1.50 Destination filename [startup-config]?
- 165. 164 | P a g e !! 1278 bytes c opied in 0.100 secs Backup Current IOS Image ciscorouter# copy flash: tftp: Source filename []? xxxxx-xx-xx.121-x.XB Address or name of remote host []? 192.168.1.150 Destination filename [xxxxx-xx-xx.121-x.XB]? Now, we are all set. Load the new IOS image from the TFTP onto the flash ciscorouter# copy tftp: flash: Address or name of remote host []? 192.168.1.150 Source filename []? xxxxx-xx-xx.121-x.XB Destination filename [xxxxx-xx-xx.121-x.XB]? %Warning:There is a file already existing with this name Do you want to over write? [confirm] Accessing tftp://192.168.1.150/xxxxx-xx-xx.121-x.XB… Erase flash: before copying? [confirm] Erasing the flash filesystem will remove all files! Continue? [confirm] Erasing device… eeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee ee …erased Erase of flash: complete Loading xxxxx-xx-xx.121-x.XB from 192.168.1.150 (via Ethernet0): !!!!!!!!!!!!!!!!!!!! ….. …. … .. [OK - 3802992/7605248 bytes] Verifying checksum… OK (0x1ABC) 3802992 bytes copied in 68.236 secs (65568 bytes/sec) This may error if there isn't enough memory in which case, you need to delete the existing image and copy the newer image onto the router or switch. On a Cisco Catalyst 3560 ciscorouter# delete /force /recurssive flash:/c3560-ipbase-mz.122-35.SE5 ciscorouter#sh flash: Directory of flash:/ 3 -rwx 1216 Mar 1 1993 00:10:27 +00:00 config.text 4 -rwx 5 Mar 1 1993 00:10:27 +00:00 private-config.text 15998976 bytes total (15995904 bytes free) That deletes the existing image and the show command just show that. Now copy the newer image onto the flash
- 166. 165 | P a g e ciscorouter#copy tftp: flash: Address or name of remote host []? 10.10.10.2 Source filename []? c3560-ipbasek9-mz.122-40.SE.bin Destination filename [c3560-ipbasek9-mz.122-40.SE.bin]? Accessing tftp://10.10.10.2/c3560-ipbasek9-mz.122-40.SE.bin… Loading c3560-ipbasek9-mz.122-40.SE.bin from 10.10.10.2 (via Vlan1): !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!! [OK - 8295106 bytes] 8295106 bytes copied in 124.571 secs (66589 bytes/sec) Check if the version is upgraded ciscorouter# sh flash Update the system config to boot with new image. ciscorouter(config)#boot system flash:/c3560-ipbasek9-mz.122-40.SE.bin If it looks ok. Reload the Cisco Router ciscorouter# reload When is back online check if the cisco device has booted with the new Cisco IOS image. ciscorouter# sh ver Buying new equipment, new security features The main reasons to buy new network equipment such as switches and routers are: 1. Today’s network equipment is faster, better, more secure by default, supports latest security and networking technologies and provides better services. 2. Most of the security features previously discussed is mostly supported on switches from 2007 forward. (BDPU Guard, IP Source Guard, DHCP Snooping, Dynamic ARP Inspection) 3. The current switches provide better remote management features that are required by third party security controls such as NAC (Network Access Control) and SIEM (Security Information Event Management) 4. Latest routers also support SECURE MANAGEMENT with SNMP v3, encrypted connection requiring username and password to manage the network.
- 167. 166 | P a g e
- 168. 167 | P a g e Secure Configuration Management (SCM) Introduction Configuration management (CM) is a process for establishing and maintaining consistency of a product’s performance, functional and physical attributes with its requirements, design and operational information throughout its life. The CM process is widely used by military engineering organizations to manage complex systems, such as weapon systems, vehicles, and information systems. Outside of the military, the CM process is now used with many domain models in the civil engineering and other industrial engineering segments such as roads, bridges, canals, dams, and buildings. Maintenance systems Configuration management is used to maintain an understanding of the status of complex assets with a view to maintaining the highest level of serviceability for the lowest cost. Specifically, it aims to ensure that operations are not disrupted due to the asset (or parts of the asset) overrunning limits of planned lifespan or below quality levels. In the military, this type of activity is often classed as "mission readiness", and seeks to define which assets are available and for which type of mission; a classic example is whether aircraft on- board an aircraft carrier are equipped with bombs for ground support or missiles for defense. A theory of configuration maintenance was worked out by Mark Burgess, with a practical implementation on present day computer systems in the software Cfengine able to perform real time repair as well as preventive maintenance. Preventive maintenance Understanding the "as is" state of an asset and its major components is an essential element in preventive maintenance as used in maintenance, repair, and overhaul and enterprise asset management systems. Predictive maintenance Many types of component use electronic sensors to capture data which provides live condition monitoring. This data is analyzed on board or at a remote location by computer to evaluate its current serviceability and increasingly its likely future state using algorithms which predict potential future failures based on previous examples of failure through field experience and modeling. This is the basis for "predictive maintenance".
- 169. 168 | P a g e Availability of accurate and timely data is essential in order for CM to provide operational value and a lack of this can often be a limiting factor. Capturing and disseminating the operating data to the various support organizations is becoming an industry in itself. The consumers of this data have grown more numerous and complex with the growth of programs offered by original equipment manufacturers (OEMs). These are designed to offer operators guaranteed availability and make the picture more complex with the operator managing the asset but the OEM taking on the liability to ensure its serviceability. In such a situation, individual components within an asset may communicate directly to an analysis center provided by the OEM or an independent analyst. Key Security Configuration Management Features: 1. Security Configuration Management: 1.1. Ensures that endpoint operating systems and applications are securely configured and in compliance with industry best practices and regulatory standards. 2. Out-of-the-box Checklist Templates: 2.1. Microsoft Windows Security Guides 2.2. NIST Special Publication 800-68 2.3. Defense Information Systems Agency (DISA) Security 2.4. Technical Implementation Guides (STIG) 2.5. National Security Agency (NSA) 2.6. Office of Management and Budget (OMB) Federal 2.7. Desktop Core Configurations (FDCC) 3. NIST-Validated for Accuracy: NIST validation ensures accurate assessments of policy Checklists and configurations as defined in the National Vulnerability Database. 4. Continuous Policy Assessment and Enforcement: Delivers ongoing and flexible mechanism to assess and apply appropriate policies to applicable systems with Content Wizard. 5. Fully Customizable: Open standards implementation ensures policy management via an extendable and customizable architecture providing the ability to add, create, define, edit and import/export security configuration policies and checklists based on industry standards in an easy-to-edit XML format. 6. Centrally managed through the Endpoint Management and Security Suite for improved visibility and reduced complexity. Security Configuration and Posture Reporting: Automates security checks including: 6.1. Event log policy settings 6.2. File permission settings 6.3. Local policies group
- 170. 169 | P a g e 6.4. System services group 6.5. Network settings 6.6. System settings 6.7. Windows components 6.8. Local user policy setting 6.9. Security patches 6.10. Firewall settings 6.11. IE settings 6.12. Application settings Comprehensive Security Configuration Reporting Secure Configuration Manager provides the industry's first solution that covers all aspects of the evolving vulnerability management process. It provides you with all of the tools necessary to effectively manage your information security environment—from notification and advisory services that provide you with the latest in vulnerability alerts to patch and configuration remediation that ensures you are protected against those vulnerabilities. Notification and Advisory Though security products depend on current, up-to-date knowledge to maximize results; researching and compiling new vulnerabilities and keeping up with Microsoft patch databases will give you gray hair. National Vulnerability Database provides the latest information on vulnerabilities and exploits through AutoSync capabilities in Vulnerability Manager. AutoSync provides a common pipe for publishing and delivering vulnerability knowledge as well as other security-related content including patch databases, regulation templates and even sample policy templates. AutoSync can be configured to pull new updates hourly, daily or in the middle of the night to ensure that your vulnerability scans aren't using stale knowledge. Policy and Regulatory Compliance Auditing Today, companies not only face difficulties enforcing corporate security policies, but now they must also meet security requirements from vague government regulations. Companies must now be much more proactive and thorough in their security audits. Secure Configuration Manager provides the tools necessary to audit security controls across a heterogeneous environment, ensuring compliance with company policies and regulations. Provides thousands of out-of-the-box checks to evaluate the most common security controls. Additionally, Secure Configuration Manager provides templates organized by regulations such as Sarbanes-Oxley, HIPAA, FERC and GLBA or by best practices such as SANS Top 20, Center for Internet Security, workstation hardening and other operating system baselines.
- 171. 170 | P a g e Controls assessments can be run as-needed or scheduled to occur regularly to ensure on going policy compliance. Risk-based reports highlighting your most critical and most at-risk systems provide executive-level summaries and supply the information necessary for taking corrective actions. Delta reports enable you to quickly and easily know what has changed on a system since the last audit. This is a great "last step" in a compliance remediation project to verify that the necessary changes have been put in place. Vulnerability Scanning takes a unique approach by not only providing the vulnerability alert content, but also including actionable vulnerability templates that enable you to immediately assess your environment to determine which systems are exposed to the vulnerability and which systems have already been exploited. As the vulnerability matures, AutoSync will automatically keep you apprised of any updates to the vulnerability content and the vulnerability signature. Even though you may have prevented the exploit, you should still periodically check for any regression to your system. Better yet, roll the vulnerability signatures into your technical standards to optimize your policy compliance efforts. Patch and Configuration Management Reduce the risks in your environment by being sure that your systems are up to date with the latest vendor security patches. Secure Configuration Manager has the power to identify missing patches on Windows, UNIX and Linux platforms. Moreover, Secure Configuration Manager assists patch management efforts on Windows workstations and servers by assessing automatic update settings and identifying patch installation failures and other events related to patch deployments—all from a central console. Secure Configuration Manager enables you to effectively remediate exceptions from policies by providing detailed recommendations and, in many cases, the ability to take action directly from the console. Specifically, it enables users to manage user and group accounts, modify security policies or change file and share permissions directly from the console. Many actions can be taken directly in response to policy violations or discovered vulnerabilities. Mapping supported devices How can software inventory software help me manage network assets?
- 172. 171 | P a g e If you’re in the IT space, it's important to have an accurate network inventory. For instance, keeping track of what software is connected to your network can save you time, money, and bandwidth. Quality software inventory software will let you keep track of software licenses to make sure you're in compliance. Knowing who has what licenses can help with loss prevention. Convenience plays a role as well: it can be annoying when an employee tells you he has a problem with software but doesn't provide any information. With a good network inventory in place, you can look and see what pesky software he installed and quickly address the issue. How is a network inventory collected? There are two primary ways that network inventory collectors work: by scanning devices via scanning agent or via an agentless scanner. Scanning agents need to be deployed on each computer on your network. When in place, these agents scan the computer and report back to a central database with the information they've gathered. On the plus side, scanning agents don't have to connect to a device to scan it, so you don't have to worry about firewalls and antivirus programs blocking the connection. All you need to do is make sure it’s set at the correct admin level and can connect to the central installation. On the down side, you'll have to install the agent on every computer in your network, and update them all when new versions are released. Agentless scanners don't require anything to be installed on each device in your network as all the devices are scanned from a central installation. If your network is set up correctly and maintained properly, using an agentless scanner can be much easier. Can a network inventory include multiple networks? If your company manages networks at multiple sites, you'll need to make sure you're able to get an inventory snapshot for each site. This can be done in a variety of ways including using a simple agentless scanner over a VPN connection, or using remote scanners that will report back to a central installation. Scanning over a VPN can slow down your network traffic significantly, so if you like to run a scan during business hours, be sure to use a remote scanning solution. Inventory Scanner
- 173. 172 | P a g e












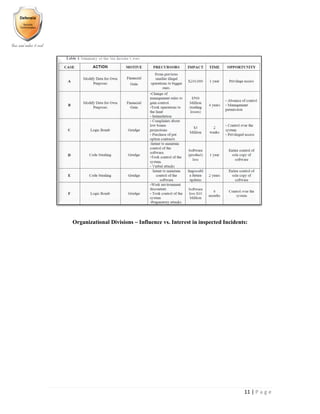


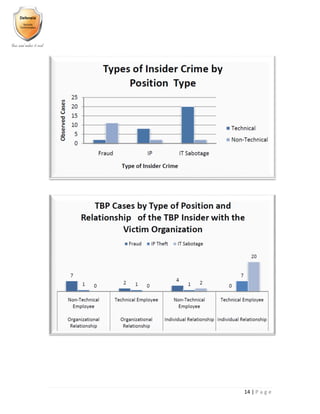

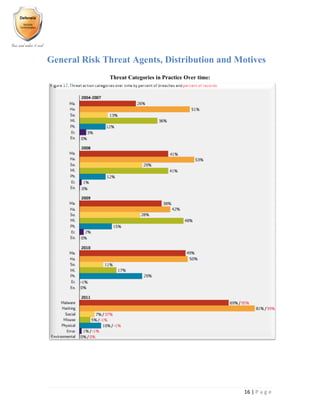



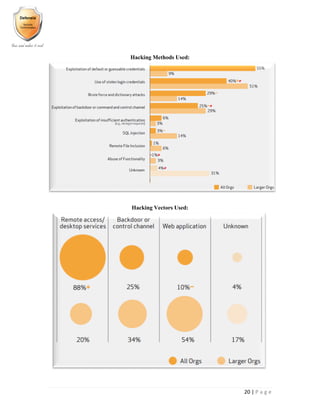

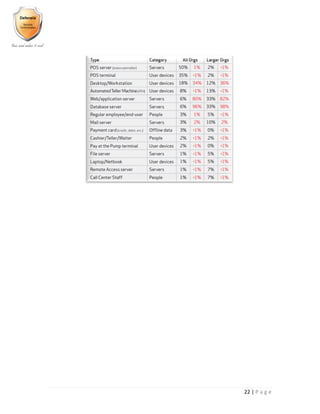
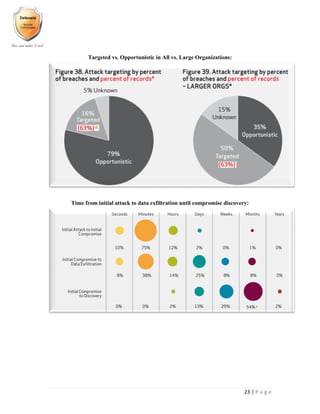







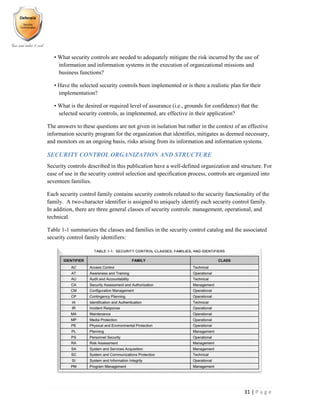














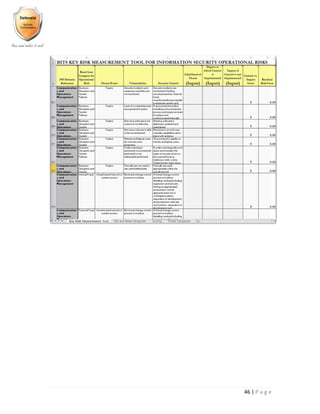













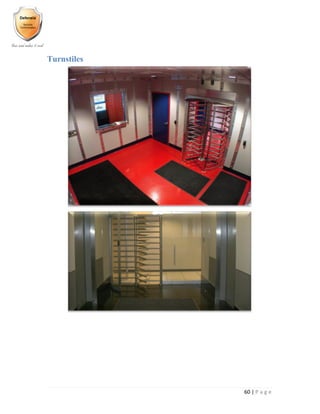


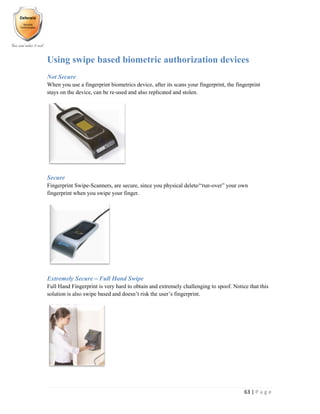









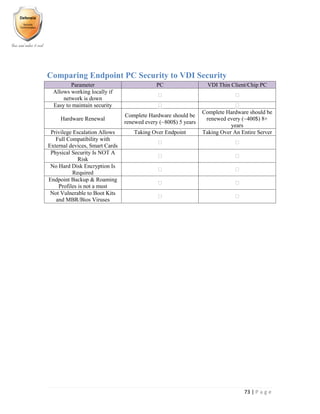




















![94 | P a g e
Relevant Features for Full Disk Encryption Product Comparison
1. Hidden containers: Whether hidden containers (an encrypted container (A) within another
encrypted container (B) so the existence of container A cannot be established) can be
created for deniable encryption. Note that some modes of operation like CBC with a plain
IV can be more prone to watermarking attacks than others.
2. Pre-boot authentication: Whether authentication can be required before booting the
computer, thus allowing one to encrypt the boot disk.
3. Custom authentication: Whether custom authentication mechanisms can be implemented
with third-party applications.[clarification needed]
4. Multiple keys: Whether an encrypted volume can have more than one active key.
5. Passphrase strengthening: Whether key strengthening is used with plain text passwords to
frustrate dictionary attacks, usually using PBKDF2.
6. Hardware acceleration: Whether dedicated cryptographic accelerator expansion cards can
be taken advantage of.
7. Trusted Platform Module: Whether the implementation can use a TPM cryptoprocessor.
8. Filesystems: what Filesystems are supported?
9. Two-factor authentication: Whether optional security tokens (hardware security modules,
such as Aladdin eToken and smart cards) are supported (for example using PKCS#11)
Product Feature Comparison Table
Name
Hidden
container
s
Pre-boot
authenticatio
n
Custom
authenticatio
n
Multipl
e keys
Passphrase
strengthenin
g
Hardware
acceleratio
n
TP
M
Filesystems
Two-factor
authenticatio
n
BestCrypt OS
Bloombase ? ?
Check Point FDE ? ? ? ?
FileVault 2 HFS+
PGPDisk ? ? ?
McAfee
Endpoint
OS
SafeGuard Ent. OS
SecureDoc ?
Symantec Endpoi
nt
NTFS,FAT3
2
TrueCrypt
only on
Windows
OS ](https://image.slidesharecdn.com/implementingandauditingsecuritycontrols-part1-170328160745/85/Implementing-and-auditing-security-controls-part-1-95-320.jpg)















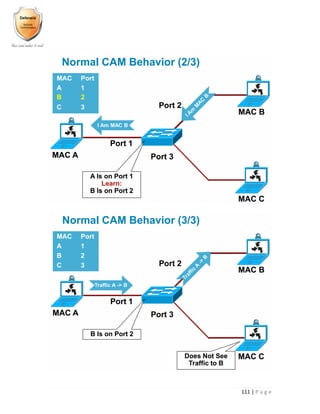
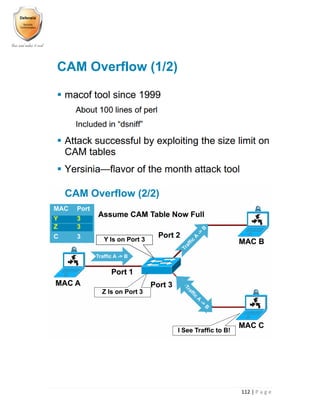

























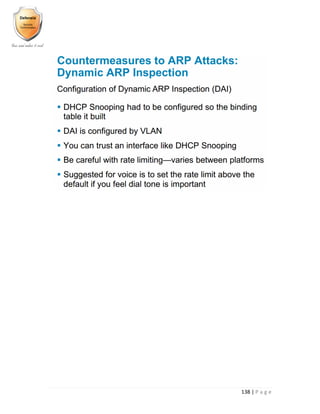
























![163 | P a g e
o Hostname(config-if)# switchport private-vlan mapping 101 201-202,301
Use the show interface private-vlan mapping command and the show interface [interface-id]
switchport command to verify the configuration.
Upgrading Router/Switch Firmware
Write Unsaved configurations
ciscorouter# write memory
Building configuration…
[OK]
Check space on Flash Memory
ciscorouter# show flash
Backup Startup Configuration
Setup a TFTP server in the same IP range as the Cisco device to back up the config, IOS image and also for
later to upload the new IOS image.
ciscorouter# copy startup-config tftp
Address or name of remote host []? 192.168.1.50
Destination filename [startup-config]?](https://image.slidesharecdn.com/implementingandauditingsecuritycontrols-part1-170328160745/85/Implementing-and-auditing-security-controls-part-1-164-320.jpg)
![164 | P a g e
!!
1278 bytes c opied in 0.100 secs
Backup Current IOS Image
ciscorouter# copy flash: tftp:
Source filename []? xxxxx-xx-xx.121-x.XB
Address or name of remote host []? 192.168.1.150
Destination filename [xxxxx-xx-xx.121-x.XB]?
Now, we are all set. Load the new IOS image from the TFTP onto the flash
ciscorouter# copy tftp: flash:
Address or name of remote host []? 192.168.1.150
Source filename []? xxxxx-xx-xx.121-x.XB
Destination filename [xxxxx-xx-xx.121-x.XB]?
%Warning:There is a file already existing with this name
Do you want to over write? [confirm]
Accessing tftp://192.168.1.150/xxxxx-xx-xx.121-x.XB…
Erase flash: before copying? [confirm]
Erasing the flash filesystem will remove all files! Continue? [confirm]
Erasing device… eeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee
ee …erased
Erase of flash: complete
Loading xxxxx-xx-xx.121-x.XB from 192.168.1.150 (via Ethernet0): !!!!!!!!!!!!!!!!!!!!
…..
….
…
..
[OK - 3802992/7605248 bytes]
Verifying checksum… OK (0x1ABC)
3802992 bytes copied in 68.236 secs (65568 bytes/sec)
This may error if there isn't enough memory in which case, you need to delete the existing image and copy
the newer image onto the router or switch.
On a Cisco Catalyst 3560
ciscorouter# delete /force /recurssive flash:/c3560-ipbase-mz.122-35.SE5
ciscorouter#sh flash:
Directory of flash:/
3 -rwx 1216 Mar 1 1993 00:10:27 +00:00 config.text
4 -rwx 5 Mar 1 1993 00:10:27 +00:00 private-config.text
15998976 bytes total (15995904 bytes free)
That deletes the existing image and the show command just show that.
Now copy the newer image onto the flash](https://image.slidesharecdn.com/implementingandauditingsecuritycontrols-part1-170328160745/85/Implementing-and-auditing-security-controls-part-1-165-320.jpg)
![165 | P a g e
ciscorouter#copy tftp: flash:
Address or name of remote host []? 10.10.10.2
Source filename []? c3560-ipbasek9-mz.122-40.SE.bin
Destination filename [c3560-ipbasek9-mz.122-40.SE.bin]?
Accessing tftp://10.10.10.2/c3560-ipbasek9-mz.122-40.SE.bin…
Loading c3560-ipbasek9-mz.122-40.SE.bin from 10.10.10.2 (via Vlan1):
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!
[OK - 8295106 bytes]
8295106 bytes copied in 124.571 secs (66589 bytes/sec)
Check if the version is upgraded
ciscorouter# sh flash
Update the system config to boot with new image.
ciscorouter(config)#boot system flash:/c3560-ipbasek9-mz.122-40.SE.bin
If it looks ok. Reload the Cisco Router
ciscorouter# reload
When is back online check if the cisco device has booted with the new Cisco IOS image.
ciscorouter# sh ver
Buying new equipment, new security features
The main reasons to buy new network equipment such as switches and routers are:
1. Today’s network equipment is faster, better, more secure by default, supports latest
security and networking technologies and provides better services.
2. Most of the security features previously discussed is mostly supported on switches from
2007 forward. (BDPU Guard, IP Source Guard, DHCP Snooping, Dynamic ARP
Inspection)
3. The current switches provide better remote management features that are required by
third party security controls such as NAC (Network Access Control) and SIEM (Security
Information Event Management)
4. Latest routers also support SECURE MANAGEMENT with SNMP v3, encrypted
connection requiring username and password to manage the network.](https://image.slidesharecdn.com/implementingandauditingsecuritycontrols-part1-170328160745/85/Implementing-and-auditing-security-controls-part-1-166-320.jpg)






