Internet security tutorial
- 2. Internet Security i AbouttheTutorial With the ever-increasing usage of Internet, numerous activities take place in your computer and it can be for either good or bad. These activities vary from identity theft to people who hack into computers and steal private passwords, documents and files. The fact is that everything is online and opens us to these frauds and makes us victims, unless you have taken the necessary steps to protect your computer. In this tutorial, we will discuss how to use Internet in a safe and secure way, and the precautions that we need to take in order to protect ourselves from the open environment of Internet. Audience This tutorial has been prepared mainly for those professionals that are within the IT industry and who are IT specialists, System administrators, Security administrators and in the other applicable departments. This tutorial is intended to make the reader comfortable in getting started with Internet Security and its various other functions. Prerequisites It is a basic tutorial where the reader can easily understand the concepts explained with a simple knowledge of how a company or an organization deals with its Internet Security. However, it will help if you have some prior exposure of cookies, phishing attacks, spamming, setting up firewalls, antiviruses, etc. CopyrightandDisclaimer Copyright 2018 by Tutorials Point (I) Pvt. Ltd. All the content and graphics published in this e-book are the property of Tutorials Point (I) Pvt. Ltd. The user of this e-book is prohibited to reuse, retain, copy, distribute or republish any contents or a part of contents of this e-book in any manner without written consent of the publisher. We strive to update the contents of our website and tutorials as timely and as precisely as possible, however, the contents may contain inaccuracies or errors. Tutorials Point (I) Pvt. Ltd. provides no guarantee regarding the accuracy, timeliness or completeness of our website or its contents including this tutorial. If you discover any errors on our website or in this tutorial, please notify us at contact@tutorialspoint.com
- 3. Internet Security ii TableofContents About the Tutorial....................................................................................................................................i Audience..................................................................................................................................................i Prerequisites............................................................................................................................................i Copyright and Disclaimer .........................................................................................................................i Table of Contents....................................................................................................................................ii 1. INTERNET SECURITY – OVERVIEW .......................................................................................1 Impact from an Internet Breach ..............................................................................................................2 2. INTERNET SECURITY – COOKIES...........................................................................................3 Types of Cookies .....................................................................................................................................3 How to Block Cookies and Delete Them? ................................................................................................4 3. INTERNET SECURITY – PHISHING.......................................................................................10 How to Detect a Phishing Email?...........................................................................................................11 4. INTERNET SECURITY – SOCIAL NETWORK..........................................................................14 5. INTERNET SECURITY – CHROME ........................................................................................16 6. INTERNET SECURITY – MOZILLA ........................................................................................20 7. INTERNET SECURITY - INTERNET EXPLORER.......................................................................23 8. INTERNET SECURITY – SAFARI............................................................................................26 9. INTERNET SECURITY – GAMING.........................................................................................29 10. INTERNET SECURITY – CHILD SAFETY.................................................................................31 Why is it so Important?.........................................................................................................................31 Social Rules Regarding Child Internet Safety .........................................................................................31 Use Software to Keep Track ..................................................................................................................32
- 4. Internet Security iii 11. INTERNET SECURITY – SPAMMING....................................................................................35 Techniques Used by Spammers.............................................................................................................35 Anti–Spam Techniques..........................................................................................................................35 Anti–Spamming Tools ...........................................................................................................................36 12. INTERNET SECURITY – CHATTING......................................................................................38 Risks from Chatting ...............................................................................................................................38 13. INTERNET SECURITY – FILE DOWNLOAD............................................................................39 What can be Potentially Harmful?.........................................................................................................39 How to Minimize the Risks to be Infected from File Download .............................................................39 14. INTERNET SECURITY – TRANSACTIONS..............................................................................42 Check if You are Doing a Secure Transaction? .......................................................................................42 What Should You do as a System Administrator?..................................................................................43 15. INTERNET SECURITY – BANKING........................................................................................44 How to do an e-Banking Transaction Safely?.........................................................................................44 Credit Cards...........................................................................................................................................45 Credit Card Generator...........................................................................................................................46 Credit Card Fraud Detection Techniques ...............................................................................................46 Best Practices to Protect your Bank Transactions..................................................................................48 16. INTERNET SECURITY – E-COMMERCE................................................................................49 Top e-Commerce Platforms...................................................................................................................49 How to Buy in a Secure Way?................................................................................................................52 Setup a Secure Online Shop ..................................................................................................................52 17. INTERNET SECURITY – CERTIFICATES.................................................................................53 Components of a Digital Certificate.......................................................................................................53 Levels of Validations .............................................................................................................................55
- 5. Internet Security iv 18. INTERNET SECURITY – EMAIL SECURITY.............................................................................56 Hardening a Mail Server........................................................................................................................56 Securing Email Accounts........................................................................................................................58 19. INTERNET SECURITY – IDENTITY THEFT .............................................................................60 What is Identity Theft?..........................................................................................................................60 How Does ID Thefts Take Place?............................................................................................................61 20. INTERNET SECURITY – CYBERCRIME ..................................................................................63 Types of Cybercrime..............................................................................................................................63 21. INTERNET SECURITY – LAWS..............................................................................................64 United States Cyber Crime Law .............................................................................................................64 Mexico Cyber Crime Law.......................................................................................................................64 22. INTERNET SECURITY – CHECKLIST......................................................................................66 Basic Checklist.......................................................................................................................................66
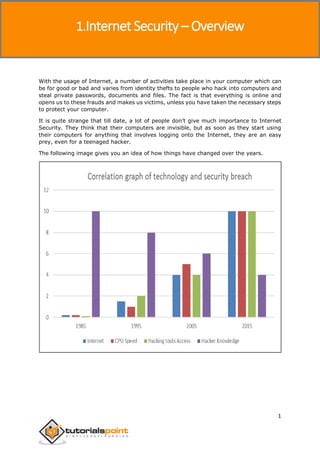
- 6. Internet Security 1 With the usage of Internet, a number of activities take place in your computer which can be for good or bad and varies from identity thefts to people who hack into computers and steal private passwords, documents and files. The fact is that everything is online and opens us to these frauds and makes us victims, unless you have taken the necessary steps to protect your computer. It is quite strange that till date, a lot of people don’t give much importance to Internet Security. They think that their computers are invisible, but as soon as they start using their computers for anything that involves logging onto the Internet, they are an easy prey, even for a teenaged hacker. The following image gives you an idea of how things have changed over the years. 1.Internet Security – Overview
- 7. Internet Security 2 ImpactfromanInternetBreach The potential losses in this “cloud” are discussed as follows. Here is a list of some losses that can have a direct impact on you and others: Losing Your Data – An Internet breach can swipe away all the data that you have gathered over the years. Reputation Loss – Just think your Facebook account or business email have been hacked by a social engineering attack and it sends fake information to your friends, business partners. You will need time to gain back your reputation after such an attack. Or your webpage has been hacked and the hacker puts up an ugly picture on it, so a new customer that is visiting your webpage to get some information will see this picture named “HACKED” and the chances that he will go away without contacting you will be too high. Identity Theft – This is a case where your identity is stolen (photo, name surname, address, and credit card details) and can be used for a crime like making false identity documents or anything else.
- 8. Internet Security 3 Cookies are files, generally from the visited webpages, which are stored on a user's computer. They hold a small amount of data, specific to a particular client and website, and can be accessed either by the web server or the client computer which can be usernames, password, session token, etc. This allows the server to deliver a page personalized to a particular user, or the page itself can contain some script which is aware of the data in the cookie and so is able to carry information from one visit to that website. TypesofCookies There are three different types of cookies: Session Cookies: These are mainly used by online shops and allows you to keep items in your basket when shopping online. These cookies expire after a specific time or when the browser is closed. Permanent Cookies: These remain in operation, even when you have closed the browser. They remember your login details and password so you don’t have to type them in every time you use the site. It is recommended that you delete these type of cookies after a specific time. Third-Party Cookies: These are installed by third parties for collecting certain information. For example: Google Maps. The following screenshot shows where the data of a cookie is stored and to do this, I have used a plugin of Firefox which is called Cookies Manager+. It shows the date when a cookie will expire. 2.Internet Security – Cookies
- 9. Internet Security 4 HowtoBlockCookiesandDeleteThem? For security reasons that you think are right, the cookies can be disabled or deleted and it varies according to the Internet browsers. Internet Explorer You can use the following steps to clear cookies in the Internet Explorer. Step 1: Press Start. Step 2: Click Control Panel. Step 3: Double click Internet options. Step 4: Under the General Tab, you will see 'Delete temporary files, history, cookies, saved passwords...' Click Delete.
- 10. Internet Security 5 Step 5: The Delete Browsing History dialog box will appear, click the 'cookies' checkbox Step 6: Click delete button at the bottom of the dialog box Step 7: You will be taken back to the Internet properties dialog box. Click 'ok'. Firefox Keep in mind that the more popular a browser is, the higher the chance that it is being targeted for spyware or malware infection. Step 1: Look at the top end of your Firefox window and you will see a 'Firefox' button. Click on it and click 'Options'.
- 11. Internet Security 6 Step 2: Click on 'Privacy'. Step 3: You will see 'Firefox will:’ Set it to 'Use custom settings for history'. Step 4: Click on the 'Show Cookies' button on the right side. Step 5: If you want to delete cookies set by individual sites, enter the complete domain or partial domain name of the site you want to manage in the search field. Your search will retrieve the list of cookies set for that site. Click 'Remove Cookie'. Step 6: If you want to delete all cookies, click the top of the Firefox window and click on the Firefox button. Click on the History menu and pick out 'Clear Recent History...' Select 'Everything' for the 'Time Range to Clear' option. The click on the downward arrow located next to 'Details'. This will open up the list of items. Click 'Cookies' and make sure all the other items are unselected. Click on the 'Clear Now' button at the bottom. Close your 'Clear Recent History' window. Chrome Step 1: At the top right hand side of your browser toolbar, click on the Chrome icon.
- 12. Internet Security 7 Step 2: Click on Settings. Step 3: Scroll to the bottom and click 'Show advanced settings'. Step 4: Under 'Privacy', you will see 'Content Settings', click on it. Step 5: Under 'Cookies', you will see 'All cookies and site data', click on this. Please note that you can block cookies altogether from being set on your browser by clicking 'Block sites from setting any data.' Unfortunately, many websites you browse will stop working if you do this. It is better if you just periodically clear your cookies manually instead of preventing them from being set by your browser. Step 6: You will see a full listing of all your cookies. You can click REMOVE ALL to clear all your cookies or you can pick a particular website and clear your cookies from that site.
- 13. Internet Security 8 Safari This guide is for OSX Lion: Step 1: Open Safari. Step 2: Click Safari and then on Preferences. Click on 'Privacy’. Step 3: Click on ‘Details’. Step 4: You will see a list of websites that store cookies. You can remove single sites by clicking the 'Remove' button and selecting a site. If you want clear all cookies, click ‘Remove All’. Step 5: When you have finished removing sites, click 'Done'.
- 14. Internet Security 9 End of ebook preview If you liked what you saw… Buy it from our store @ https://store.tutorialspoint.com