Introduction to security_and_crypto
- 1. Introduction to Security and Crypto
- 2. Agenda Basics of security Basics of cryptography Symmetric Crypto DES example, block chaining Key exchange, Asymetric Crypto RSA example Public Key Infrastructure Trust Provisionning Attacks and how to cope with it Attacks on Algorithms Attacks on Implementations Attacks on Protocols Two Examples A7 FS-application Trust provisioning + Offline Authentication TLS and support of A70CM 2
- 3. Embedded NFC 3 Basics of Security
- 4. Security Goals Confidentiality: Eavesdropping possible? At 10 at my place Alice At 10 at my place Anneliese Authenticity: Sender correct? Mon, at 10 at my place. Alice Tue, at 10 at my place. Alice Integrity: Message modified? Alice Non-Repudiation: Message signed? But also: Availability (i.e.: preventing denial of service), Privacy (personal data towards merchant or third parties) 4
- 5. Security Goals and Algorithms Confidentiality: Symmetric Crypto Authenticity: Asymmetric Crypto / Signature / Hash Integrity: Hash / Signature / MAC Non-repudiation: Hash / Signature Symmetric Crypto DES, Triple-DES, AES Asymmetric Crypto RSA, ECC Hash SHA Signature Hash + Asymmetric Crypto MAC Hash / Symmetric Crypto 5
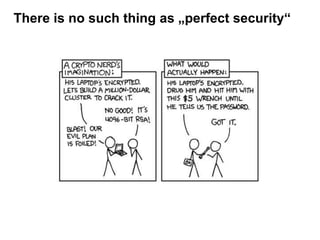
- 6. There is no such thing as „perfect security“ There is no such thing as “perfect security” – A secure system makes an attack more expensive than the value of the advantage gained by the attacker. 6
- 7. Attacks & Principles Kerckhoffs’ principle: The attacker always knows the algorithm; the only information unknown to him/her is the key. Brute force attack – Exhaustive search over all keys – Single plaintext-ciphertext-pair may be enough to determine the correct key – Cannot be avoided – Goal: Make it practically infeasible, i.e. key space is so large that the search takes more than a lifetime Side Channel Attacks: – Even if a cryptographic algorithm offers high level of security, its implementation may still leak information about secrets or keys: timing behavior, current consumption, electromagnetic radiation etc establish so called side channels for secret information. There is no such thing as “perfect security” – A secure system makes an attack more expensive than the value of the advantage gained by the attacker.
- 8. There is no such thing as „perfect security“
- 9. Embedded NFC 9 Basics of Cryptography Symmetric Crypto
- 10. Symmetric Encryption PlaintextPlaintext Encryption DES Triple-DES AES Decryption DES-1 Triple-DES-1 AES-1 Ciphertext Key Key Confidentiality: Eavesdropping not easily possible 10
- 11. 1. Introduction - What is Android ? 2. Platform Architecture 3. Platform Components 4. Platform Initialization 5. How to get Android sources A bit of history… The Caesar cipher
- 12. 1. Introduction - What is Android ? 2. Platform Architecture 3. Platform Components 4. Platform Initialization 5. How to get Android sources Block Ciphers DES Block Chaining
- 13. Symmetric Encryption : DES
- 14. Symmetric block ciphers: DES and AES Plaintext is divided into blocks m1, m2, ... of the same length Every block is encrypted under the same key. Typical block lengths: DES – 64 bit, AES – 128 bit Typical key lengths: DES – 56 bit; AES – 128, 192, 256 bit Algorithm Block c2 Block c1Block m4 Block m3 14
- 15. DES - Data Encryption Standard Most important example for Feistel ciphers (ie: same operations to encrypt and decrypt) Published in 1977 as a standard for the American governmental institutions Significant weakness: 56 bit key is too short 1999 Deep Crack: 100.000 PCs computed key within 22 hours and 15 minutes Input 64 bit Output 64 bit Permutation IP –1 round i round 16 Round key i Round key 16 Key 56 bit Permutation IP R16 F K16 F K1 L0 R0 L1 R1 L15 R15 L16 R16 15
- 16. Modes of Operation Algorithm Block c2 Block c1Block m4 Block m3 Modes of Operation – How to ensure that the ordering of blocks is not changed by an attacker? – Dependencies between encrypted blocks: Cipher Block Chaining (CBC)
- 17. Problems of block encryption m1 c1 m2 c2 m3 c3 (3)DES Enciphering (3)DES Enciphering (3)DES Enciphering Electronic Code Book Mode: Identical blocks are identically encrypted. ECB-Example: 17
- 18. CBC Mode Cipher Block Chaining Mode: Identical blocks are differently encrypted. CBC-Example: m1 c1 m2 c2 m3 c3 (3)DES Enciphering (3)DES Enciphering (3)DES Enciphering IV 18
- 19. Triple-DES Triple-DES = triple encryption using DES with two or three external keys: DES(k1, DES-1(k2, DES(k1,m))) 1. Question: Why is the decryption DES-1 in the middle? Compatibility: When implementing Triple-DES and choosing k1 = k2, then one gets the single DES. Therefore, only one algorithm needs to be implemented to get Triple-DES and single DES. 2. Question: Why is not Double-DES used instead of Triple-DES? Meet-in-the-middle attack! Security comparison – Two keys – NIST estimation: effectively 80 bits – Three keys – NIST estimation: effectively 112 bits 19
- 20. AES – Scheme AES is standardized for key lengths of 128 bit, 192 bit, 256 bit, and block size of 128 bit. The number of rounds depends on key length used: 10 up to 14 Round Function: 20 plaintext Round key 0 Round 1 (round key 1) Round 2 (round key 2) Round n (round key n) ciphertext ByteSub ShiftRow MixColumn AddRoundKey
- 21. Security Goals and Algorithms; HASH Function Confidentiality: Symmetric Crypto Authentication: Asymmetric Crypto / Signature / Hash Integrity: Hash / Signature / MAC Non-repudiation: Hash / Signature Symmetric Crypto DES, Triple-DES, AES Asymmetric Crypto RSA, ECC Hash SHA Signature Hash + Asymmetric Crypto MAC Hash / Symmetric Crypto
- 22. Hashfunctions Analogy: digital fingerprints Compression: Data of arbitrary length is mapped to n bits. (Typical values: 128/160 bits) Cryptographic properties Preimage of a hash is hard to find. Two data elements with the same hash value are hard to find (Collisions). Data Hash
- 23. Hashfunctions Compression: Data of arbitrary length is mapped to n bits. Preimage of a hash is hard to find. One-wayness: Given h(m) finding m is infeasible. Two data elements with the same hash value are hard to find (Collisions). Collision resistance: It is infeasible to find m and m‘ which are mapped to the same value. (birthday paradox; output should be at least 160 bits) m m' m m' m h(m)
- 24. Secure Hash Algorithm (SHA) First version: SHA-0 (160 bit output) in early 90s SHA-1 only a minor change to SHA-0 Chinese Research Group attacked SHA-1: – On collision resistance only expected effort: 280, real effort 263 (Birthday paradox) – Applicability highly depends on application SHA-224,256,512 etc … xxx giving the length of output SHA-3 in review and selection process
- 25. Message Authentication Codes: MAC, HASH At 10 at my place Alice At 10 at my place Anneliese The active attacker: Who is the origin of a message? Authentication verifies MAC = HK(m) ? K m, MAC computes MAC = HK(m) K Message Authentication Code (“symmetric signature”) A authenticates her message by computing a tag MAC and sends it together with the message to B. B can verify this tag by re-computing it and check whether the two results match. The function H can be either a hash function (SHA, MD5), or a symetric block cipher based on DES or AES (CMAC,…). Integrity: Message can’t be easily modified 25 m,
- 26. 1. Introduction - What is Android ? 2. Platform Architecture 3. Platform Components 4. Platform Initialization 5. How to get Android sources Key Exchange Asymmetric Crypto
- 27. What about the Keys? Alice and Bob need to share the same key. How to share it securely? Pre distribution? (ie: keys exchanges in a “secure environment”) – Trust provisionning (see later) Secured Key Exchange – Diffie Hellman and asymetric cryptography 27
- 28. Diffie Hellmann Key Exchange Private “keys” Public “keys” 28
- 29. Asymmetric Crypto: The Idea PlaintextPlaintext Encryption RSA ECC Decryption RSA ECC Ciphertext Bob‘s Public Key Bob‘s Private Key 29
- 30. Asymmetric Crypto: Signatures Plaintext verifiedPlaintext, Hash Signature Generation (Decryption) RSA ECC Signature Verification (Encryption and Compare with Hash) RSA ECC Plaintext, Hash, Signature Bob‘s Private Key Bob‘s Public Key 30
- 31. Principles of Asymmetric Encryption Everyone can put a letter into Bob‘s mailbox. Everyone can encrypt message for Bob. Everyone can verify Bob’s signature Only Bob can open his mailbox with his private key. Only Bob can decrypt with his private key. Only Bob can create his own signature Bob Hello Bob, .... ... Encryption Decryption Hello Bob, .... ... 31
- 32. Comparison Symmetric - Asymmetric Symmetric Algorithms Asymmetric Algorithms Number Many Few Security Can be very good Can be very good Performance In general: good Bad Key exchange necessary? Yes No Digital Signatures No Yes Typical Application Encryption Digital Signatures Key Exchange
- 33. 1. Introduction - What is Android ? 2. Platform Architecture 3. Platform Components 4. Platform Initialization 5. How to get Android sources Asymmetric Crypto: RSA
- 34. RSA Based on the so called factorization problem: – Given two prime numbers, it is easy to multiply them. Given the product, it is difficult to find the prime numbers. RSA Keys – Every participant has – a modulus n = p*q (public), the product of two large prime numbers – a public exponent e (for performance reasons, one often chooses small prime numbers with few 1’s) – a private exponent d. A: nA,eA B: nB,eB C : nC,eC dA dC dB 34
- 35. RSA - Operation Encryption The sender computes c = me mod n, where m is the message, (n, e) is the public key of the receiver, and c is the cipher text. Decryption The receiver computes cd mod n, where c is the cipher text and d is the private key of the receiver. It holds: cd mod n = med mod n = m. For signing it is the other way round: • Signing is the same operation as decrypting • Verifying a signature is the same operation as encrypting 35
- 36. RSA – Some Math Primes p, q ; n = p*q Thus, φ(n) = (p-1)*(q-1) = |{ x | x and n are coprime }|. Euler‘s Theorem: cφ(n) mod n = 1 mod n Let e, d such that – e and φ(n) are coprime, thus inverse of e mod φ(n) exists – e*d = 1 mod φ(n) Let‘s prove RSA: – cd mod n = (me)d mod n = med mod n // substitution = m1+k*φ(n) mod n = m1 * mk*φ(n) mod n // definition modulo = m1 * (mφ(n)) k mod n = m * 1k mod n // Euler‘s Theorem = m c = me mod n and m = cd mod n - Why?
- 37. RSA Size of the RSA keys – The bit length of the modulus is called the size of an RSA key. The public exponent is usually a lot shorter; the private exponent is of the same length as the modulus. – Today, everything larger than 1024 2048 bit is considered to be secure. Implementation – Chinese Remainder Theorem (CRT) is a mathematical fact that allows to make decryption and signing significantly more efficient. Has to be carefully implemented in order to be secure. – Implementation without CRT is often called “straight forward” – significantly less performance, but usually less security issues as well
- 38. Embedded NFC 38 Public Key Infrastructure
- 39. Threat: Authenticity of Public Keys Attack Mr. X replaces B’s public key EB by his own public key EX. Consequences: – Encryption: Only X can read messages that are meant for B. – Signature: B’s signatures are not verifiable – B’s signatures are invalid! X can sign messages that are verified as Bob’s signatures. A : EA B : E B E X C : E C U : E U V : E V 39
- 40. Certificates Name and public key are signed by a trustworthy institution (certification authority, CA). Message (name, public key) and the CA’s signature on it are called “certificate”: Cert(A) = {A, EA}, DCA{A, EA} Format of Certificates have to be specified – X.509 for example Tree-like structure possible – path of trust Banco di Santo Spirito DCAA, EA Cert(A) DA 40
- 41. Random numbers Facts: – In cryptography, often “unpredictable” numbers are needed (for keys for example). – Example: Generate a 128 bit AES key – required is, that even if an attacker “knows” 127 bits of this key, he should not be able to guess the missing bit with a better probability than ½. – There is NO mathematical way to determine whether the outcome of an “random number generator” is unpredictable!!!! – The best thing offered by mathematicians are statistical tests: but they can only test whether a sequence of random numbers has a specific structure or property (and hence is NOT unpredictable). A statistical test never gives a POSITIVE result. Passing a test, only means a sequence does not have one specific (of many) negative properties.
- 43. Block Diagram of Random Number Generator