McAffee_Security and System Integrity in Embedded Devices
- 1. McAfee Embedded Optimized Security Solutions for Embedded Systems Intel Intelligent Systems Event – Istanbul, Turkey Kathryn Martin – McAfee, OEM Account Manager April 2012
- 2. Agenda McAfee – Security Trends & Threat Landscape McAfee Embedded Security Solution McAfee Software Development Kits for Embedded Systems McAfee Global Threat Intelligence (GTI) McAfee Centralized Embedded Security Management
- 3. Network Security Global Threat Intelligence • Next Generation Firewall • File Reputation • Network Intrusion Prevention • Web Reputation • NAC Gateway • Web Categorization • Network User Behavior Analysis • Message Reputation • Network Threat Behavior Analysis • Network Connection Reputation • Network Threat Response Content Security Endpoint Security • Email Gateway • Anti-Virus & Anti-Spyware • Web Gateway • Host Intrusion Prevention • Data Loss Prevention • Endpoint Encryption • Encryption • Application Whitelisting • Desktop Firewall • Device Control • Policy Auditing Security Management • NAC Endpoint • Email Server AV & Anti-Spam • Policy Management • SharePoint Protection • Security Reporting • Mobile Protection • Mobile Management • Virtual Desktop & Server • Vulnerability Management • Risk Management • Compliance
- 4. Security Trends Threat Landscape The Multi-Million Business
- 5. Increasing Embedded Device Security Threats 5 5 April 10,
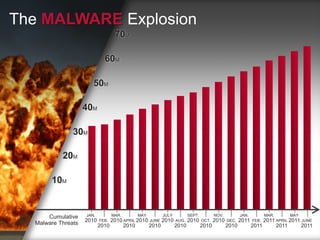
- 6. The MALWARE Explosion 70M 60M 50M 40M 30M 20M 10M Cumulative JAN. MAR. MAY JULY SEPT. NOV. JAN. MAR. MAY 2010 FEB. 2010 APRIL 2010 JUNE 2010 AUG. 2010 OCT. 2010 DEC. 2011 FEB. 2011 APRIL 2011 JUNE Malware Threats 2010 2010 2010 2010 2010 2010 2011 2011 2011
- 7. Threat Landscape Global Malware Vision 2011 Malware (families) Malware (families) +662,900 (DAT related) (DAT related) * 2011 * Autorun Autorun +7,320,000 (Collection) (Collection) Exploits +2,800,000 (Collection) FakeAV, Scareware +8,600,000 (Collection) PassWord Stealers +14,400,000 (Collection) Rootkits +4,600,000 (Collection) Malware Zoo +75,200,000 (Collection)
- 8. Stuxnet: The Anatomy of an Attack • First worm developed with ―nation-state‖ support— WHAT targeted at sabotaging Iran’s nuclear enrichment facility • 60% infected machines in Iran—Iran confirmed damage to nuclear program in Fall 2010 • Highly sophisticated development—used 6 new zero- day vulnerabilities and worked flawlessly on all Windows versions down to Windows 95 • Digitally signed software HOW • Attacked SCADA systems running specific controllers — deep knowledge of control systems • Stealth attack, operated from 2008–2010— infected variable frequency drives with slight adjustment, enough to impact centrifuges
- 9. Explosion of IP Devices in a Connected World DEVICES CONNECTED DEVICES
- 10. Embedded Systems Are Changing Past Today Proprietary OS Windows, Linux Isolated Network Internet Connected High Development Cost Low Development Cost Low Support Cost Higher Support Cost Patching Rare * Patching Common * Limited Security Risk * Standard Security Risk *
- 11. Embedded Development Effects of Change: Higher Support Costs Development Cost Support Time
- 12. Embedded Development Goal: Keep Support Costs Low, Increase Revenue Development Cost Support Time
- 13. Embedded System Challenges Maintaining Security and Control Across the Lifecycle Device Manufacturer Distributor/Dealer Device Owner Security, Control, & Compliance
- 14. McAfee Embedded Security Solutions Key Focus Products for Embedded Application Control and Change Control Security Management (McAfee Embedded Control) (McAfee ePolicy Orchestrator) Content Security Virus Detection & Remediation (McAfee Embedded Reputation SDK) (McAfee Embedded Anti-Virus SDK) Additional Focus Products for Embedded Removable Device Security Host Network Security (McAfee Device Control) (McAfee Host Intrusion Prevention) Database Security Data Security (McAfee Activity Monitor/Virtual (McAfee Endpoint Encryption) Patching/Vulnerability Manager)
- 15. McAfee Embedded Security Protect your device effectively
- 16. McAfee Embedded Security The right security solution for your solutions Black Grey White Kiosks Point of Sale MAC REPUTATION-BASED Smart Meter Printer Firewall ATMs NetBook Email/Web Gateway Medical Devices Consumer PC Servers Web Servers SCADA Dynamic Static
- 17. Challenges - for Embedded Device/System Manufactures Unauthorized applications System Zero day downtime threats Rise in Security Secure support costs Control content Compliance Patching Device and updates management Traditional Compliance AV overhead drift
- 18. McAfee Embedded Security Single Solution for Challenge Resolution Prevention of Known & Accountability & Zero-Day Attacks Device Longevity • Dynamic whitelisting • What can change • No signatures to update • Who can change it • Only approved software Security Control • When it can change and applications run • How it can change • Patch on your schedule Compliance Compliance Ready • PCI • HIPAA • NERC • Fed. Regulations 18
- 19. The Embedded Security Product McAfee Embedded Control 1. Application control • Controls what software installs and runs • Prevents malware • Memory Protection • Reduces patching frequency Gain • Image deviation reporting Control 2. Change control • Enforces software change policy • Prevents out-of-policy changes • File integrity monitoring for compliance
- 20. McAfee Embedded Control How it works: Build the Inventory Preparation Stage Production Stage 0 1 2 3 Create Enable Solidified Solidified Inventory McAfee Disk Image Production Mode Automated Establish gold or Gold or audited Real-time continuous inventory creation audited image image solidification The solidification process requires no user intervention, and copies of solidified images can be distributed to other devices. 20
- 21. McAfee Embedded Control How it works: Maintain State With Trusted Change Solidified Authorized Returned to Production Mode Update Mode Solidified Mode Authorized Admin. AuthorizedU pdaters Secure Signed Updates Update Windows 21
- 22. McAfee Embedded Control Quick and Simple Setup • Once deployed, no re-configuration required • Nearly zero performance overhead • Small footprint 8-12MB RAM, ~25 MB HDD • Supports software distribution mechanisms • Broad platform support: • Microsoft OS since NT4 – Windows 8 (2012) • Multiple Linux Distributions (RHLE, SLES, etc.) • Solaris 8, 9, 10 (SPARC) • HPUX 11.11, .23, .31, • AIX 5.3, 6.1 • Wind River Linux 22
- 23. Blacklisting versus Whitelisting • Currently • No Signatures Required 80 Million Signatures of • Only Approved applications Malware known to McAfee allowed to execute • Every Day more than 60.000 • Protection against known unique threats newly identified threats and unknown threats • No protection against Rootkits (Zero-Day Exploits) • No protection against • Protection against rootkits Exploitation • Whitelist is dynamically evolving during lifetime
- 24. McAfee Embedded Security To secure solution for your solution Black Grey White Kiosks Point of Sale MAC REPUTATION-BASED Smart Meter Printer Firewall ATMs NetBook Email/Web Gateway Medical Devices Consumer PC Servers Web Servers SCADA Dynamic Static
- 25. McAfee Embedded Anti-Virus SDK Review Key Features, Functions, and Benefits Scan Engine SDK – Comprehensive detection so threats are isolated before they can spread – Removal of viruses, worms, and other malicious code – Reliable and accurate detection, without a costly false-alarm problem – Effective scanning of compressed, archived, and packed files – Support for a wide range of platforms – Scan engine SDK for easy integration into third-party applications
- 26. McAfee Embedded Security To secure solution for your solution Black Grey White Kiosks Point of Sale MAC REPUTATION-BASED Smart Meter Printer Firewall ATMs NetBook Email/Web Gateway Medical Devices Consumer PC Servers Web Servers SCADA Dynamic Static
- 27. McAfee Security Connected McAfee Global Threat Intelligence (GTI)
- 28. McAfee Global Threat Intelligence (GTI) • 75 Billion Malware Reputation Queries/Month • 20 Billion Email Reputation Queries/Month • 2 Billion IP Population Queries/Month Volume • 300 Million IPS Attacks/Month • 100 Million IP Port Reputation Queries/Month • 100+ BILLION QUERIES • Malware: 60 Million Endpoints Breadth • Email: 30 Million Nodes and • Web: 45 Million Endpoint and Gateway Users Depth • Intrusions: 4 Million Nodes • 100+ MILLION NODES, 120 COUNTRIES
- 29. What It Takes to Make An Organization Safe Global Threat Intelligence Threat Reputation Network Web Mail 3rd Party Firewall Gateway Gateway Host AV Host IPS IPS Feed .
- 30. Why McAfee Is Best Positioned to Deliver GTI 360˚ Correlation Across All Threat Vectors • IP addresses distributing • Mail/spam sending activity • URLs hosting malware • Web access/referer activity • Mail/spam including it • Malware hosting activity • Botnet affiliation • Hosted files • IPS attacks caused • Popups • Affiliations Web Reputation File Reputation • DNS hosting activity • Botnet/DDoS activity Network Connection Reputation • Mail/spam sending activity •Message Reputation Mail/spam sending activity • Web access activity • Intrusion attacks launched • Malware hosting activity • IP addresses of attackers • Network probing activity • Web hosting/phishing activity • Presence of malware • Botnet/DDoS activity • DNS hosting activity • Intrusion attacks launched
- 31. McAfee Embedded Reputation SDK Review Key Features, Functions, and Benefits The McAfee Embedded Reputation SDK is a software library that provides an API for obtaining reputations and categories from McAfee’s GTI Cloud. Reputation SDK Web Security • URL Categorization • Web Reputation Reputation SDK Email and Network Protection • IP Reputation (anti-spam) • Message Reputation (anti-spam) • Connection Reputation Embedded Reputation SDK Real-time Lookups via our GTI cloud service Supported Platforms • Windows, Solaris, Linux and BSD (specific x86 versions)
- 32. McAfee Embedded Security Management McAfee ePolicy Orchestrator (ePO)
- 33. McAfee ePolicy Orchestrator Centralized Security Management Extensible Automated Unified Enterprise-ready • Automate solutions • Streamline • Central point of • Distributed with open API processes reference architecture • Leverage • Speed incident • Enterprise-wide supports ecosystem responses visibility deployments of • Connect to your IT • Reduce audit • Reduce any size infrastructure fatigue management • Flexible reference complexity architecture McAfee ePolicy Orchestrator 33
- 34. McAfee ePolicy Orchestrator Key Feature Overview • End-to-End Visibility • Rogue System Detection – Unified point of reference across – Identify and manage all networked security solutions assets to lower risk • Personalized Command Center • Powerful Workflows – Tune work environment to optimize – Automate common routines, streamline efficiencies processes across systems • Drag-and-Drop Dashboards and • Enterprise-ready Actionable Reports – Flexible, scalable architecture minimizes – Immediate insight to action slashes CAPex and OPex response times • Extensible Framework • Role-based Access Control – Increase value of existing security – Distribute administration and assets, optimize for future needs information McAfee ePolicy Orchestor 34
- 36. OEM Case Study NCR Financial Solutions Global leader in assisted and self-service retail and financial systems, shipping 60,000+ ATMs/year with McAfee Embedded Security • Problem Definition • Lack of zero-day security • Unauthorized software changes on production ATMs • What NCR Needed • Provide zero-day comprehensive security • Transparent, small footprint & no overhead • Deploy and forget, without ongoing updates • Cost effective • Why Embedded Security • Insider threat mitigation, no unauthorized changes • Complete ATM channel change control for PCI compliance • Standardized on NCR APTRA platform • How They Did It • Utilizing process and certificate-based updaters for secure change control • Built a repeatable process for specific application and OS auditing ―With this technology and compliance-ready ATMs, our bank customers don’t have 36 to worry about security issues affecting their business or their consumer.‖ McAfee Internal Use Only Confidential
- 37. OEM Case Study NEC Infrontia POS NEC Infrontia is a leading developer of point-of-sale systems, and currently ships more than 15,000 POS systems in Japan with McAfee Embedded Security • Problem Definition • High partner support costs related to security problems • Frequent OS patching • Minimal to no PCI compliance • What NEC Needed • Reduce patching on Windows XP Embedded OS • No performance draining security • Need for service provider partners to make changes • Compliance • Why Embedded Security • Prevents unapproved installs to reduce in-field breakage • Reduces number of touch points to the device • Minimizes the need to frequently patch the OS • Change control provides tight control over what is installed • Delivers PCI compliant device to retailers ―Embedding McAfee gives us complete control and certainty over what changes on each device.‖ 37 Confidential McAfee Internal Use Only
- 38. OEM Case Study Merge Healthcare MRI Merge Healthcare’s CADstream™, the standard in CAD for magnetic resonance imaging (MRI), ships with McAfee Embedded Security • Problem Definition • Unavailability caused by unauthorized changes • Rampant field maintenance from unauthorized software modifications • Current security solution resource intensive • No Compliance • What Merge Healthcare Needed • Blocking unapproved installs to reduce in-hospital breakage • Less frequent OS patching cycles • Low overhead keeps system running smooth at hospitals • Provides zero-day protection for sustainable FDA compliance • Change control dictates what can be changed or installed • Why Embedded Security • Minimal overhead required • Protection in a standalone mode • Code protection from unwanted and unauthorized change ―Integrating McAfee Embedded Security into CADstream improved CADstream security, availability, and support.‖ Confidential McAfee Internal Use Only
- 39. OEM Case Study Sharp MFPs Global leader in developing integrated business solutions, shipping more than 15,000 MX-series MFPs in Japan with McAfee Embedded Security • Problem Definition • Lack of control and minimal device security • High field maintenance costs tied to unauthorized changes • No PCI compliance or zero-day protection • What Sharp Needed • Single solution for security and compliance • Minimal device overhead • Why Embedded Security • Prevents zero-day attacks and unnecessary field maintenance • Allows for controlled configuration changes • Improved service availability • Helps ensure PCI compliance • How They Did It • Created template policies for configuration and system protection • Trusted only the processes they wanted for application updates ―McAfee locks-down our office automation printers and multifunction peripherals 39 by preventing unauthorized access and software changes.‖ Confidential McAfee Internal Use Only
- 40. McAfee Trusted Security Partner for Embedded Developers PARTNERSHIP TECHNOLOGY McAfee Embedded Security EXPERTISE NEXT STEPS Identify & Scope and OEM evaluate conduct proof partnership needs of concept agreement
- 42. McAfee Embedded Security Compliance: PCI DSS Requirements Section 5 • Whitelisting approach provides complete malware Use and regularly update protection without need for updates anti-virus software Section 6 • Zero-day protection and change reconciliation with Develop and maintain change management systems secure systems and apps Section 10 • File change tracking on cardholder data, user Track and monitor all activity, and unauthorized change attempts access to cardholder data Section 11 • Comprehensive file integrity monitoring and Regularly test security malware protection systems and processes 42
- 43. McAfee Embedded Security Compliance: NERC CIP-007 Guidelines CIP-007-1-R1 • Application control protects the state of systems Ensure cyber assets and changes and keeps security controls pristine, while change to assets do not adversly affect control tracks changes specified in the requirement cyber security controls and during an audit CIP-007-1-R2 • Application control maintains the state of the Ensure ports and services system and prevents configuration changes to required for normal standards set by the ―responsible entity‖ operations are enabled CIP-007-1-R3 • Application control provides a compensating Security patch management for measure to mitigate risk exposure when the tracking, evaluating, testing, and security patch or patch management program installing cyber security patches cannot be accomplished CIP-007-1-R4 • Application control and whitelisting-based Use anti-virus and malware approach provides complete proactive malware prevention to detect, prevent, protection without need for updates or signatures deter, and mitigate malware CIP-007-1-R6 • Change control provides file integrity monitoring, Ensure Cyber Assets implement system alerts, and login attempts, while application automated tools or process control can lock the system controls to monitor system events 43