Meet up slides_mumbai_05022020_final
- 1. [02nd May 2020]: [Securing Data Transmission and Logging Mechanism using Splunk & Mule 4 Dockerization] [Mumbai - India]
- 2. All contents © MuleSoft Inc. 2 • 1.Please keep yourself muted unless you have any question. • 2.We encourage keeping your video for making our meetup interactive. • 3.You'll can also write down your questions in chat section. • 4.Once you join write down your name in chat section so we will have an attendance. • 5.As this is our first online Meetup we appreciate your valuable feedback. Thanks. Guidelines for Mumbai MuleSoft Meetup #10 [Online]
- 3. All contents © MuleSoft Inc. 3 • Training and certification update: • MuleSoft training is hosting FREE instructor lectures through the end of May to accompany our free self-paced Development Fundamentals course. • Also, any certification set to expire on or after Feb 1, 2020 is now valid through July 31, 2020. • Please participate! >> Share this link >> Training slides • MuleSoft Global Connect is Virtual! Register for free to be a part. https://connect.mulesoft.com/ Important Announcement
- 4. All contents © MuleSoft Inc. Agenda 4 Introductions Secure Data Transmission Logging Mechanism Using SPLUNK Dockers Containers Demo and Configurations to create Mule 4 image Networking time
- 5. All contents © MuleSoft Inc. Introductions 5 • About the organizers: – Sudeshna Mitra – Manish Yadav – Akshata Sawant • About the sponsors: MuleSoft A SHOW OF HANDS: Who is new to this MeetUp?
- 6. All contents © MuleSoft Inc. Speaker 6
- 8. All contents © MuleSoft Inc. Why Security of data is Important ? 8
- 9. All contents © MuleSoft Inc. Session will cover 9 • What is Encryption/Decryption Process? • What are its benefits? • How can we achieve encryption /decryption of data using Mulesoft? • What are the different methods to achieve it? • Tools used – Mulesoft, GPA, Kleopatra • Demos • Question and answers
- 10. All contents © MuleSoft Inc. 10
- 11. All contents © MuleSoft Inc. 11 • Sensitive information can be protected; others cannot view it and cannot be stolen over the internet. • Information can be shared securely within a group of users or company departments. • Files are compressed to a smaller size before being sent over the network. • There is no need to purchase private key or certificates. • Secure mail and text cannot be infiltrated by hackers or infected and misused through email attacks. • Future-proof technology and complete compatibility with other applications. • In-built key manager to securely manage yours and others' keys. • Provides absolute assurance that data receives or sent has not been modified in transit. • Provides protection against viruses and the newest blended email threat. Advantages of Security
- 12. All contents © MuleSoft Inc. 12 MuleSoft provides various encryption strategies to encrypt your messages. Encryption strategy Description JCE encrypter Encrypts stream, byte[], or string. XML encrypter Encrypts string; encrypts individual fields using xpath expressions. PGP encrypter Encrypts stream, byte[], or string; applies tighter security (relative to JCE and XML); increases processing load (relative to JCE and XML).
- 13. All contents © MuleSoft Inc. 13 Using password and keys
- 14. All contents © MuleSoft Inc. 14 Mule 3 Vs. Mule 4 for plugin installation
- 15. All contents © MuleSoft Inc. 15 Mule 3 Vs. Mule 4 for operations
- 16. All contents © MuleSoft Inc. 16 Mule 3 ----- Encryption Process To download module for mule 4
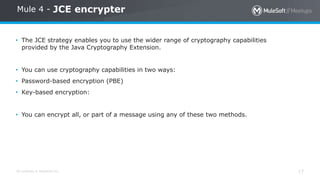
- 17. All contents © MuleSoft Inc. 17 Mule 4 - JCE encrypter • The JCE strategy enables you to use the wider range of cryptography capabilities provided by the Java Cryptography Extension. • You can use cryptography capabilities in two ways: • Password-based encryption (PBE) • Key-based encryption: • You can encrypt all, or part of a message using any of these two methods.
- 18. All contents © MuleSoft Inc. 18 Mule 4 - XML encrypter • The XML strategy enables you to use the wider range of cryptography capabilities • Key-based encryption • Encrypts string; encrypts individual fields using xpath expressions.
- 19. All contents © MuleSoft Inc. 19 Mule 4 - PGP encrypter • Mule can encrypt all or part of a message using Pretty Good Privacy (PGP). PGP combines data compression and data encryption to secure messages. The compression reduces the size of the payload to help reduce the transmission time later on your application. • This section addresses these scenarios: • Encryption: Using another party’s public key to encrypt an outgoing message in a Mule app. • Decryption: Using your own private key to decrypt an incoming message in a Mule app.
- 20. All contents © MuleSoft Inc. 20 Mule 4 - PGP encrypter Encrypted message
- 22. All contents © MuleSoft Inc. Why logging is Important ? 22 ?
- 23. All contents © MuleSoft Inc. Logger component in Mulesoft 23 Levels: 1. DEBUG 2. ERROR 3. INFO 4. TRACE 5. WARN
- 24. All contents © MuleSoft Inc. 24 • Splunk is a software platform to search, analyze and visualize the machine-generated data gathered from the websites, applications, sensors, devices etc. which make up your IT infrastructure and business. Splunk performs capturing, indexing, and correlating the real-time data in a searchable container from which it can produce graphs, reports, alerts, dashboards, and visualizations. • Benefits : – Splunk Automatically collects the data in Real-time from Multiple systems. – Splunk can accept any data like csv, json, log formats, xml etc. – Splunk can give Alerts/Everts Notifications. – Using Splunk data and analytics, Dashboards can be created. – And Many more… What is SPLUNK ?
- 25. All contents © MuleSoft Inc. 25 Features of SPLUNK:
- 26. All contents © MuleSoft Inc. 26 How SPLUNK Look Like ?
- 27. All contents © MuleSoft Inc. 27 • With the help of default + custom fields given Below: – Index – Its kind of Directory – host (default) – source (default) – sourceType (default) – flowName – Severity – message – messageType – messageSize – event – KPI – Correlation id – Marker How SPLUNK can be effective in terms of Logging?
- 28. All contents © MuleSoft Inc. 28 • An index is a collection of directories and files . • By default, All events will be stored under “main” index. The default Splunk Enterprise index. All processed external data is stored here unless otherwise specified • Create the new index by navigating to settings->indexes->create New – Enter your index name – The index data type. For event data, click Events. This is the default data type. – Set the size for your index , default is 500 GB. Splunk Query : index=“dev_mulesoft” Index
- 29. All contents © MuleSoft Inc. 29 Why there is a need to have multiple indexes ? • To control user access. • To speed searches in certain situations.
- 30. All contents © MuleSoft Inc. 30 • A default field that contains the host name that generate an event. • the host field is used in searches to narrow the search results to events that originate from a specific device. • Each event has a host name. • For example ,it can be “Mulesoft” , “Java” etc. • If no other host rules are specified for a source, Splunk software assigns the host field a default value that applies to all data coming into the instance from any input. • Splunk Query : index=“dev_mulesoft” host=mulesoft Host:
- 31. All contents © MuleSoft Inc. 31 • The source of an event is the name of the file, stream, or other input from which the event originates. • For example : “application name” , “Configuration.xml name” etc. • The source type of an event is the format of the data input from which it originates like for windows .evt files from event viewer • For example : “Any point studio” , “application name” etc. • Splunk Query : index=“dev_mulesoft” source=customer-exp-api Source and sourceType:
- 32. All contents © MuleSoft Inc. 32 • flowName is a custom field that can be created in order to track the flow level events logged in SPLUNK. • Severity field can be created in order to track the success and failure events logged in SPLUNK. • Which can accept the only below values from API: – Success/INFO – Failure/ERROR – Splunk Query : index=“dev_mulesoft” flowname=customer-exp-api-post – Splunk Query : index=“dev_mulesoft” severity=Success flowName and severity:
- 33. All contents © MuleSoft Inc. 33 • message is the field which holds the actual Payload or data in each event. • messageType field can be created to hold the datatype of particular message in each event. • For example : “order”, “customer”, “employee” etc. • messageSize field can be created to describe the size of particular message in the event. message, messageType and messageSize
- 34. All contents © MuleSoft Inc. 34 • A Correlation ID, also known as a Transit ID, is a unique identifier value that is attached to requests and messages that allow reference to a particular transaction or event chain. • By using this field, we can get the result of each transaction in one go. • For example : Experience , Process and System layer logs. • Splunk Query : index="test_mulesoft" 4cd2dc81-3daf-11ea-bf82- 0a7661ac9eeb Correlation id
- 35. All contents © MuleSoft Inc. 35 • We can create event field to track the end to end transaction of Mulesoft API. • which can accept the values given below: – Received and sent – Source and target • It can also be used to analyze the transactions in case of any errors. • Splunk Query : index=“dev_mulesoft” event=received Event:
- 36. All contents © MuleSoft Inc. 36 • In Marker property you can set information of the particular event. • This field can be act as optional though. • For example : – Order information received from SAP – Data successfully sent to Salesforce. Marker
- 37. All contents © MuleSoft Inc. 37 • A Key Performance Indicator (KPI) is a measurable value that demonstrates how effectively a company is achieving key business objectives. Organizations use KPIs to evaluate their success at reaching targets. • Its an mandatory criteria to implement the Dashboards which are known as KPI dashboards. • KPI Dashboards are the perfect tool for your performance tracking reports as they can be used to visually depict the performance of an enterprise, a specific department, or a key business operation. KPI (Key Performance Indicators)
- 38. All contents © MuleSoft Inc. 38 For Example :
- 39. All contents © MuleSoft Inc. 39 • { “message” : “{…}”, <- for eg: customer data JSON “host” : “Mulesoft”, “source” : “sales-exp-api”, “sourceType” : “Anypoint studio”, “flowName” : “customer-order-post-flow”, “severity” : “INFO”, “messageType : “Customer”, “messageSize” : “500KB”, “event” : “Received”, “correlationId : “8d82dce0-87dc-11ea-96a3-12c261b2ccf9”, “KPI” : { key: quantity, value: 5 }, “marker” : “Customer data received from SAP” } SPLUNK event will look like?
- 40. All contents © MuleSoft Inc. 40 • Makes life easy for developers especially when there is a need to troubleshoot the application, detect issues, review the performance of the application, etc. • Easy to utilize other features of SPLUNK like Alerts , Reports, Dashboards and Visualization etc which takes your business to the next level. Benefits of Smart logging in SPLUNK:
- 42. All contents © MuleSoft Inc. What is Docker? 42 • Developing apps today requires so much more than writing code. Multiple languages, frameworks, architectures, and discontinuous interfaces between tools for each lifecycle stage creates enormous complexity. Docker simplifies and accelerates your workflow, while giving developers the freedom to innovate with their choice of tools, application stacks, and deployment environments for each project. • In 2013, Docker introduced what would become the industry standard for containers. Containers are a standardized unit of software that allows developers to isolate their app from its environment, solving the “it works on my machine” headache. For millions of developers today, Docker is the de facto standard to build and share containerized apps - from desktop, to the cloud.
- 43. All contents © MuleSoft Inc. Container: A standardized unit of software Containers? 43 • A container is a standard unit of software that packages up code and all its dependencies so the application runs quickly and reliably from one computing environment to another. A Docker container image is a lightweight, standalone, executable package of software that includes everything needed to run an application: code, runtime, system tools, system libraries and settings. • Container images become containers at runtime and in the case of Docker containers - images become containers when they run on Docker Engine. Available for both Linux and Windows-based applications, containerized software will always run the same, regardless of the infrastructure. Containers isolate software from its environment and ensure that it works uniformly despite differences for instance between development and staging.
- 44. All contents © MuleSoft Inc. Docker-Container: What's in it for us? What is good about all this? 44 • Standard: Docker created the industry standard for containers, so they could be portable anywhere • Lightweight: Containers share the machine’s OS system kernel and therefore do not require an OS per application, driving higher server efficiencies and reducing server and licensing costs • Secure: Applications are safer in containers and Docker provides the strongest default isolation capabilities in the industry
- 45. All contents © MuleSoft Inc. Container Vs VM Hey but we have VM’s then why Container? 45 Containers VM An abstraction at the app layer that packages code and dependencies together. Multiple containers can run on the same machine and share the OS kernel with other containers, each running as isolated processes in user space. Containers take up less space than VMs (container images are typically tens of MBs in size), can handle more applications and require fewer VMs and Operating systems. (VMs) are an abstraction of physical hardware turning one server into many servers. The hypervisor allows multiple VMs to run on a single machine. Each VM includes a full copy of an OS, the app, necessary binaries and libraries - taking up tens of GBs. VMs can also be slow to boot.
- 46. [Demo and Configurations to create Mule 4 image]
- 47. All contents © MuleSoft Inc. Prerequisites Demo Time !!! 47 • Windows Docker Desktop is installed on your machine. https://hub.docker.com/search?q=&type=edition&offering=community&sort=updat ed_at&order=desc • Make sure you have switched to Linux based containers. Click on Docker Desktop icon and click on “Switch to Linux Containers”. • Anypoint Studio (7.4.2) is installed and you have a valid license (or trial) version of Mule Runtime “mule-ee-distribution-standalone-4.2.2.zip” placed in your system. • A Sample Hello-World Application created in Mule 4 and create a deployable archive out of it using Studio Export capability. We will not go in detail about this as this tutorial assumes that audience already has a brief knowledge of Mule based application development.
- 48. All contents © MuleSoft Inc. Local settings: Configurations to create Mule 4 image 48 • 1. Create a folder on your desktop to place the required items for this PoC. For example: • C:UsersankurDesktopDocker Demo • Place following items in this folder: • a) mule-ee-distribution-standalone-4.2.2.zip • b) mule-hello.jar • c) muleLicenseKey.lic (this is provided by your respective MuleSoft Customer Success Manager) • d) DockerFile • 2. Now check if the Docker Desktop is up and running. • 3. Populate DockerFile: • Github Link : https://github.com/ancur4u/DockerDemo
- 49. All contents © MuleSoft Inc. 49 Encryption strategies - https://docs.mulesoft.com/mule-runtime/4.2/cryptography Kleopatra tool - https://www.openpgp.org/software/kleopatra/ GPA tool - https://www.gnupg.org/related_software/gpa/index.html pgp-encryption and decryption - https://dzone.com/articles/pgp-encryption-and-decryption-with-mule-esb Splunk documentation - https://docs.splunk.com/Documentation Reference links
- 50. All contents © MuleSoft Inc. Take a stand ! 50 • Nominate yourself for the next meetup speaker and suggest a topic as well.
- 51. All contents © MuleSoft Inc. What’s next 51 • Share: – Tweet your pictures with the hashtag #MuleMeetup #MuleSoftMeetup – Invite your network to join: https://meetups.mulesoft.com/mumbai/ • Feedback: – Contact your organizers Manish Yadav, Sudeshna Mitra and Akshata Sawant to suggest topics – Tweet your organizers at @SudeshnaMitra14, @Manish_Kyadav, @sawantakshata02 – Contact MuleSoft at meetup@mulesoft.com for ways to improve the program – Follow us on Instagram (mumbai_mulesoftofficialpage) – Your Feedback is Food for us • Our next meetup: – Date: TBD – Location: Mumbai – Topic: TBD
- 52. Networking time Introduce yourself to your neighbors!
- 53. See you next time Please send topic suggestions to the organizer
- 54. THANK YOU

![[02nd May 2020]: [Securing Data Transmission and Logging
Mechanism using Splunk & Mule 4 Dockerization]
[Mumbai - India]](https://image.slidesharecdn.com/meetupslidesmumbai05022020final-200503150416/85/Meet-up-slides_mumbai_05022020_final-1-320.jpg)
![All contents © MuleSoft Inc. 2
• 1.Please keep yourself muted unless you have any question.
• 2.We encourage keeping your video for making our meetup
interactive.
• 3.You'll can also write down your questions in chat section.
• 4.Once you join write down your name in chat section so we will
have an attendance.
• 5.As this is our first online Meetup we appreciate your valuable
feedback. Thanks.
Guidelines for Mumbai MuleSoft Meetup #10 [Online]](https://image.slidesharecdn.com/meetupslidesmumbai05022020final-200503150416/85/Meet-up-slides_mumbai_05022020_final-2-320.jpg)




![[Secure data transmission]](https://image.slidesharecdn.com/meetupslidesmumbai05022020final-200503150416/85/Meet-up-slides_mumbai_05022020_final-7-320.jpg)




![All contents © MuleSoft Inc. 12
MuleSoft provides various encryption strategies to
encrypt your messages.
Encryption strategy Description
JCE encrypter
Encrypts stream, byte[], or
string.
XML encrypter
Encrypts string; encrypts
individual fields using xpath
expressions.
PGP encrypter
Encrypts stream, byte[], or
string; applies tighter
security (relative to JCE and
XML); increases processing
load (relative to JCE and
XML).](https://image.slidesharecdn.com/meetupslidesmumbai05022020final-200503150416/85/Meet-up-slides_mumbai_05022020_final-12-320.jpg)







![[Logging Mechanism Using
SPLUNK]](https://image.slidesharecdn.com/meetupslidesmumbai05022020final-200503150416/85/Meet-up-slides_mumbai_05022020_final-21-320.jpg)



















![[Docker and Containers]](https://image.slidesharecdn.com/meetupslidesmumbai05022020final-200503150416/85/Meet-up-slides_mumbai_05022020_final-41-320.jpg)




![[Demo and Configurations to
create Mule 4 image]](https://image.slidesharecdn.com/meetupslidesmumbai05022020final-200503150416/85/Meet-up-slides_mumbai_05022020_final-46-320.jpg)