RFID and Agent-Based Computing
- 1. RFID and SAP: A Strategic Vision Leading Edge Forum Technology Grant Jonathan Gregory Computer Sciences Corporation May 2006
- 2. ii Table of Contents Preface...................................................................................................................1 Introduction...........................................................................................................1 Executive Summary .............................................................................................3 Business Case–Based Introduction to Basic Implementations of RFID ........4 Con-Agra ................................................................................................................4 Wal-Mart .................................................................................................................4 The Department of Defense ...................................................................................5 RFID Core Functionality.......................................................................................6 RFID Core Technology.........................................................................................8 RFID Tags ..............................................................................................................8 Unique Identification ...............................................................................................9 Bridging the Gap: The Divide Between the ERP World and the RFID World ..........................................................................................................10 SAP’s RFID Solution: The Auto ID Infrastructure (Aii) Module......................12 Looking Forward: SAP NetWeaver and the Enterprise Services Architecture.........................................................................................................13 Web 2.0 ................................................................................................................14 The Network Effect .............................................................................................16 Agile Systems .....................................................................................................16 Integrated Marine Multi-Agent C2 System (IMMACCS) ..................................17 Battle Scene from the Age of Empires .................................................................18 Asset-Oriented Computing................................................................................18 Revisiting the Marine’s Supply Chain ..............................................................19 Industrial Applications of the Asset Services Model......................................20 Recommendations .............................................................................................24 Appendix .............................................................................................................27 The Aircraft Engine Aftermarket ...........................................................................27 Details on SAP’s “Auto ID Infrastructure” (Aii) Product ........................................28 Complex Event Processing (CEP)........................................................................29 The Own Versus Influence Model .....................................................................31
- 3. 1 Preface Radio frequency identification (RFID) is an exciting technology that can be used anywhere that a unique identification system is needed. It is used to track assets from beer kegs to containers of spent nuclear fuel. It is used to track expensive aircraft maintenance-oriented tools, and used to track library books. It is used by Japanese school children to flag alerts if they encounter a problem when walking to or from school, and used to allow cashless payments for services such as bus transportation in skiing communities via a tagged ski pass. It can make existing processes better, faster, and cheaper — or it may be used to provide totally new sources of information and, in the process, enabling revolutionary new solutions to problems. The world of RFID has many new areas to write about and explore. This is due in part to the foundational shift in computing that RFID represents. RFID offers computing systems a more comprehensive means of gathering input about the real world. Vast amounts of data may be continually collected without human intervention, drastically lowering the cost of data collection. All kinds of assets may now possess an identity enabling visibility into each particular asset’s life cycle. New specialty areas and solutions emerge — RF security, data type standards, sensor data transmission and standards, new protocols, new data processing technologies, etc. Tagged assets reveal the regular departure of physical assets from established business rules or understandings of asset behavior. Information gathered from RFID has shown consumer product managers that supply chains are much less responsive than previously thought. Contractual obligations which previously were assumed to have been kept are now realized to be noncompliant due to new audit trails. The RFID technology reveals process inefficiencies, standards of nonconformance, contractual breaches, and other flaws in asset management processes. Thus, RFID becomes a catalyst for more rapid process improvements. This document will attempt to synthesize the RFID subject into a rational means of understanding the technology, the functionality, and the business implications. After which point, this paper will also attempt to predict future enterprise resource planning (ERP) and online technology and business trends, in order to describe an ideal, futuristic vision for RFID adoption. Such a vision, though largely academic, provides an end state that will help guide strategic goals, influencing present-day adoption decisions. It is easy to “drink the Kool-Aid” when discussing the future of RFID; I have attempted to stay grounded and build futuristic statements on solid, credible, present-day references. Due to the varied interests of the readers of this document, detailed technical comments have been largely compartmentalized in the appendix. Introduction In the days of the automobile’s invention, people initially referred to the contraption as a “horseless carriage.” They had to use the earlier technology to define the later one. Such a characterization was accurate, but did not recognize the automobile’s superior utility. In a similar form, the RFID technology has been referred to as “wireless bar-coding.” This is an accurate depiction; however, it fails to recognize the utility offered by the technology. Small decisions at the beginning of an initiative can have enormous ripple effects as those decisions are propagated. A rule of thumb is that each phase in the product development cycle requires 10 times the work or cost to solve a problem than in the prior phase. The purpose of this paper is to help identify design issues with RFID solutions (specifically the technologies used to process the data streams and derive value from the data) before they are created by offering information that will lead the decision maker to visualize an optimal adoption of the various auto-ID
- 4. 2 technologies given current expectations of the future of IT. Said differently, the paper seeks to introduce core concepts surrounding RFID that will impact the adoption of the technology for years to come. The paper will also offer a broad set of principals for building a road map in order to achieve this vision. This paper will introduce several business cases, followed by a basic functional and technical review of RFID. The paper then turns to the subject of bridging the gap between the RFID data collection world and ERP solutions. This will involve information about present and future ERP solution characteristics, as well as the characteristics of “new” technologies used to glean events from RFID data streams. The future of ERP involves a service-oriented architecture, which dovetails with “Web 2.0” concepts surrounding the next generation of Internet solutions. The Web 2.0 model relies on and demonstrates the “Network Effect,” and several examples of network-centric computing, including a model for asset management, follow.
- 5. 3 Executive Summary RFID reduces the cost of data collection, enabling real-time asset data to drive granular asset automation. The technology can be leveraged as part of an infrastructure and computing model, which enables new asset management solutions, or it may be limited to automation of existing processes, which can provide very real (but limited) value. Emerging and existing IT tools and methods will enable dramatic new business models and applications. These tools include global standards, layered business process management (BPM) technologies, object-oriented programming, instant messaging, Web services, as well as new database and event processing models. ERP investments will be utilized as a foundation for core business processes in which specialists within the enterprise add local customization extensions for localized process improvements. The value of a network is determined by its size and the degree of contribution of its component nodes. The “network effect” refers to Reed’s Law, which states that the utility of a network increases exponentially with the number of nodes. This network effect is seen in the phenomena labeled “Web 2.0,” which implements tools that enable bodies of people to contribute to the benefit of the larger system. An ideal RFID-enabled asset management solution will leverage the network effect by empowering process owners distributed throughout an enterprise to contribute to the overall value of the network. Emerging standardized computing models can be made into simple toolsets that utilize standardized interface definitions to Web and enterprise services. RFID data collection employs massive data streams that require new IT-specific toolsets; reveals new information about business activities; and offers information for process improvement methodologies. This will pose new challenges for organizational IT governance. The process by which business processes are developed and modified must be redefined in light of the evolving distribution of process authority. Furthermore, the existing ERP-driven business processes may be extended by disparate business units as well as customized to an asset-specific level.
- 6. 4 Business Case–Based Introduction to Basic Implementations of RFID This section will speak to the very basic uses of RFID, from a business value perspective. These basic implementations can provide tremendous value through significant improvements in existing business processes. Con-Agra Due to an e-Coli threat in 2002, ConAgra was forced to recall 18.6 million pounds of beef, which was more than 50 times the amount that they actually should have had to recall (354,000 pounds). Con-Agra did not have a sufficient audit trail to allow for the substantially smaller, more accurate, recall. The company subsequently left that business.i The use of RFID could have been used to track cattle movement through the supply chain and thus limit the scope of the recall. This instance of RFID is using it to record past events. The Con-Agra case demonstrates the relevance of RFID for product recall purposes. In a similar fashion, automobile tire makers are incorporating RFID tags into their product to help facilitate the same such functionality in the event of a recall. These examples demonstrate the simplest uses of RFID and how they can add value as a stop-gap measure. Here, the data collected is used only for historical purposes, yet the value proposition still justifies the investment. The next example implements RFID as a means of measuring present conditions. Wal-Mart New York Investment House Sandford C. Bernstein & Co estimated that Wal-Mart might save $8.35 billion in total annual savings when RFID is deployed throughout its operations. The largest component of that savings is $6.7 billion saved in automating manual processes by eliminating the need to have people scan bar codes on pallets and cases, reducing labor costs by 15 percent.ii “What Wal-Mart has done was simple. It used RFID data to add one key piece of information: Do we have it in the backroom? It’s just a little tiny tweak — it didn’t change the way it stocks shelves or the printout of the pick list — but the impact is phenomenal.” iii Bill Hardgrave Director, University of Arkansas RFID Research Center Wal-Mart is using RFID to depict present conditions, “Do we have it in the backroom?” to drive automated reordering and receiving. According to the University of Arkansas research, initial estimates of RFID reducing Wal-Mart out- of-stocks at 16 percent were too low. The greatest improvement was seen in goods that sold from six to 15 units per day. These items showed a 62 percent decrease in out-of-stocks.iv The Wal-Mart mandate and business case is very well known, as is the concept of tagging items for recall. The dramatic value potential seems at odds with the observations made by Gartner research vice-president for ERP, Brian Zrimsek, at a symposium in Sydney, Australia, in November 2004. Mr. Zrimsek warned that mere evolutionary enhancements, such as enhancing existing business processes, are missing the power and potential that the RFID technology offers. His assertion is that RFID is a revolutionary technology that is being sub-optimized to fit into evolutionary projects. For example, the Wal-Mart dictate is a “tactical rather than strategic” solution as it is only a better labeling systemv . Mr. Zrimsek noted further that the association between an event triggered by an RFID tag movement and a corresponding business action, (termed “act-on-fact”) is a key RFID return on
- 7. 5 investment (ROI) concept. A discussion about a truly revolutionary implementation of RFID will be threaded throughout the remainder of this paper. The “Zrimsek Hurdle” will be the moniker for gauging if a solution, indeed, is revolutionary. The two elements of this hurdle are: 1. Create new business processes or operational models 2. The use of RFID data to enable automation (“act on fact”) The Department of Defense “Marines can see where critical items are, and that changes the dynamic… The dialog (between forward operating bases and the logistic hub) has changed from ‘Where’s my stuff?’ to ‘Why isn’t my stuff moving?’ to ‘I want you to put my stuff on the next truck because I can see it’s there.”vi Alan Estevez Assistant Deputy Undersecretary of Supply Chain Integration, Department of Defense Implementing RFID in the Marine supply chain has cut inventory value in the chain from $127 million to $70 million. Average delivery times have dropped from 28 days to 16 days, the supply backlog of 92,000 shipments has fallen to 11,000.vii In this example, Marines can view the products in the supply chain of interest to them, effectively viewing and influencing the future deliverable date of the product. This differs from the Wal-Mart example as that solution uses a reorder point- planning model that benefits from a stable supply chain, whereas the military supply chain has greater logistical issues and variability. It appears that part of the success in the Marine’s supply chain solution, based on the above quote, is the inclusion of stakeholders in representing their own interests. This is a very “Web 2.0” type concept (a network of interests providing value symbiotically). Nobody is more keenly interested in getting the requested supplies than the soldier making that request. That soldier is what this paper will later refer to as the “local process owner.” A critical component to improving processes is empowering local process owners with tools that they can use to identify and solve problems on their own. More will be discussed on this topic later in the paper. These supply chain enhancements do not pass the Zrimsek Hurdle, as they do not revolutionize business processes or provide “act-on-fact” automation; however, the paradigm shift in empowering local process owners to gain visibility and “speak up” for their assets is a significant step in the right direction (it “changed the dynamic”). The act of noticing that a RFID-tagged pallet has not been moving, and in fact needs to be shipped to a forward location, does not need to be performed by a person. An IT system should be able to automate that functionality. The issue here is that mature IT products that are truly asset- and local process authority-centric are nonexistent. The “Web 2.0” computing model, as well as object-oriented programming, offers a great deal of promise in this area. As with any new technology, adopters require a strong ROI-based case to justify the investment. Revolutionary or paradigm altering implementations of RFID are difficult or impossible to build an ROI case for, given that the solution impact is not fully understood. What was the ROI on the first business PCs? What is the ROI on e-mail? Was the economic (and social) impact of the first intercontinental train or first freeway or the Internet known before building it? Understandably, venture capital and solution providers are focused on products that provide specific solutions, most of which enable vertical integration in specific industries.
- 8. 6 SAP is leveraging its ownership of business processes (as defined in its software products), client base, and substantial size to provide dozens of industry-specific vertical collaboration hubs for supply chain management (SCM) integration. RFID is renewing interest in creating SCM hubs for vertical integration. What RFID will not do is tackle the nontechnical reasons (organizational culture, power struggles, etc.), which are the very human reasons for limited SCM integration and automation. It is no surprise that overwhelmingly powerful customers (Wal-Mart and the DoD) have blazed new trails in SCM integration via RFID. They are organizations powerful enough to enforce a one-sided mandate on their suppliers. As the benefits of RFID compliance are realized through the entire supply chain, industry segments with more equally powered players will increase interest. An example of this is the aerospace industry, with its supply chain of certified, high- value items, with low lot sizes. This industry is one of several forming standards groups hosted by the Electronic Product Code (EPC) global network. These vertical solutions are likely not to pass the Zrimsek Hurdle, as they will automate existing SCM-oriented business processes (not change existing processes); however, they will enable “act of fact” automation. “We do a lot of things now in transactional systems which are triggered by human beings. Somebody inputting a customer order or a goods receipt and so on. This can be automated. If an RFID tag just crosses a reader, it’s done.” Claus Heinrich, SAP Executive Board Member The ability of an ERP vendor to provide both elements of the Zrimsek Hurdle (revolutionize business processes and “act-on-fact” automation”) will, by definition, be impossible until the adoption of “service-oriented architecture” (SOA) or, in SAP’s case, the adoption of the “enterprise services architecture” (ESA). Generally speaking, the ESA is SAP’s implementation of SOA. This software architecture is what enables an ERP system to allow affordable business process transformation. These components will be defined and spoken to in more detail later in the paper. This section discussed a few business cases and current adoption models of the technology. The next section will speak to the basic functionality offered by RFID, which empowers the above business cases. RFID Core Functionality The RFID technology provides a means of accurately and inexpensively collecting real-world data. These new data streams offer information systems substantial new sources of data input, allowing for dramatic new uses of information technology to solve problems. RFID offers three core asset management capabilities: 1. The means of uniquely identifying assets 2. The means of locating assets 3. The means of knowing the condition of assets (through the use of integrated sensors) The first core benefit of RFID is the ability to specifically identify assets. Enormous amounts of asset-specific data are not captured, in part, due to the anonymous nature of nonserialized or unidentified assets. Another reason is the difficulty of collecting and integrating the data in an economical fashion. Both of these reasons for not capturing much more asset-specific data are evaporating; RFID lowers the cost of collecting data because it can happen automatically with no human intervention. More data (about the past history, present environment, and future anticipated use of an asset) may be collected “to” the asset, and the technologies
- 9. 7 and business models of the “Web 2.0” phenomena demonstrate economical ways of integrating data into services rendering value. An RFID tag provides a unique number identifying each specific asset and a very low cost mechanism for collecting data. Once an asset is identified, data may be collected to that specific asset. Data can build into information with value as the ecosystem of interests surrounding that asset consume and provide data specific to that asset. With RFID, one can ask and answer the following questions: Using Identity • Is there a relationship between a performance metric (e.g., product defects, returns, supply chain velocity) and a possible cause or contributor to that performance (e.g., raw material used, engineering change on subassemblies, supplier, assembler, lot, tooling, worker, worker or tool certification)? This is clearly a means of continuous improvement. Incorporating Sensors One patriot missile in a lot of 20 was mistakenly dropped. Handlers lost track of which missile had been dropped, so all 20 missiles had to be shipped back to the United States, overhauled, and returned at a cost of $21 million. Further questions may be asked and answered when including sensors: • Report what happened to an asset in transit (e.g., an aircraft engine or patriot missile, shipped in a sea van container, is dropped from a damaging height; an RF tag integrated with a shock sensor can record and communicate that event) • Is there a relationship between a performance metric and a sensor reading (sensors include light, temperature, shock, vibration, motion, radiological, call buttons to signify events)? • Report what is happening right now (e.g., a motion-activated tag transmits while the plant is closed, raising a theft alert) • Warn what might happen (e.g., a tag with a temperature sensor detects a temperature that will destroy perishable goods, which raises an appropriate alert) Leveraging Location By knowing the location of an object (and the time of the location read) one can answer the following questions: • Where is the asset right now (an obvious, but highly useful function) • Is the asset where it is supposed to be, according to its workflow system? • Is the asset combined with other assets that break a business rule or could pose a hazard (e.g., environmental health and safety (EH&S) risks or regulations that require chemicals to be separated) In preparing for the War in Iraq, a sea van container carrying medical supplies was erroneously removed from its vessel at a port in Hong Kong. Before the vessel could leave, the application monitoring the RFID tag on the sea van container alerted military logistical personnel, who were able to get the container placed back on the vessel before it left for the Middle East. It would have taken months to have corrected the distribution error.
- 10. 8 Finally, this data can be incorporated into automation solutions that perform the following: • As soon as a particular asset is detected as having arrived at the dock door, a certified worker is notified to process it for a rush order • Predict a bottleneck in operations before it occurs and take corrective action • Combinations of chemicals that are not supposed to be transported together are mistakenly placed on the same truck, which approaches a gate to exit a plant location. The RFID data triggers an alert and a security gate is prevented from opening • When any condition or situation a (knowledge) worker can think of occurs, do whatever the (knowledge) worker intends or instructs. These conditions and actions may be served by Web or enterprise services The RFID technology, combined with robust systems and applications, can be a component to moving the “tense” of business management of assets from past tense (what happened), to present tense (what’s happening now), to the future tense (what’s about to happen). RFID Core Technology This section will offer a basic introduction to RFID technology. An RFID system is composed of tags, which are placed on assets and transmit unique data to readers (also called access points) via an “RF” (radio frequency) signal. The access points transmit data to core IT systems, which process the data and possibly interface with external networks that contain further data about the tagged asset. This is similar to how a garage door opener works and is seen in current everyday activities such as the E-Z Pass automated toll collection, key-card entries to buildings or rooms, and store security tags used on items such as clothing to prevent shoplifting. RFID Tags RFID technology can be broken down into the categories of “active” tags (aRFID), which are battery powered and have a longer read range (up to several kilometers), and “passive” tags (pRFID), which cost less, have no battery, and have a shorter read range (usually under 12 feet). An active tag may be used to determine an asset’s location, even when the asset is not in close proximity to a reader, whereas a passive tag’s location is typically only known when the tag passes by a fixed gate. For this reason, it is important to distinguish between active and passive tags from a continuous data perspective. An active tag in range of an RF access point will continually generate location-based information. Inferences may be drawn between the location of such an asset and the machine used to finish it, the tooling used to calibrate it, the employee performing the work, the supplier of the subcomponent or raw material, etc. Tag frequencies, sizes, form factors and costs vary widely. There are also hybrid tags that include sensors of various kinds, which may or may not be battery powered. Passive RFID tags, given their short-range capabilities, are typically collected upon movement through a gate — such as a loading dock doorway. Asset identity and location is collected automatically and without human error. It is important to note that the passive technology encounters real physical limitations when in environments unfriendly to electromagnetic fields. Dense liquids and metals can disrupt RF communication and limit the readability of tags located in the middle of a pallet. Technology improvements (such as ultra-wide band communication) and process solutions (such as storing all pallet content on a single pallet-connected active tag) work around these limits of physics. Note that the RFID communication
- 11. 9 solution is dependent on the data collection environment, which will result in varied infrastructure costs. Active RFID tags offer a larger read range, and therefore do not require a gate to pass through for collecting data. While a gate on a passive tag collects asset location at a particular time, active solutions allow for continuous data streams denoting asset location. As with passive tags, active tag communication to access points may be impacted by environmental factors. A tag in an outdoor environment will encounter less interference than a tag in an indoor environment; say on a shop floor with large heavy machinery running. Location-based mechanisms include TDOA (time delay on arrival) and signal strength–based mechanisms. The TDOA method measures the amount of time that it takes for an active tag’s signal to be captured by three access points. With that information, the access points can triangulate the asset location. This method encounters an issue when interference delays a signal so as to misrepresent the distance of the tag from one or more of the readers. The interference of a particular indoor location will increase the density of access points required to make accurate, location-based reads. Outdoor environments enjoy much less interference and add the capability of integrating GPS-based location mechanisms into the RF tags. A portable deployment kit provided by Savi Technology provides a mobile RFID solution that extends the military supply chain into expeditionary operations where there is no established RF infrastructure. This solution connects portable RF readers (access points) to core systems via iridium satellite links. Initial units are being deployed to Southwest Asia.viii DoD is also testing RFID tags (dubbed the third-generation RFID with satellite communications or “3G RFID w/SATCOM”) that incorporate GPS location sensing and satellite communication to enable global tag location (within 3.5 feet) at any time.ix x The 3G RFID w/ SATCOM tags offer an RFID “tag” that is globally visible via satellite. There is no reader or local infrastructure required to interrogate the tag. While the “tag” cost will surely be high, in time the costs of all technologies decrease due to the cycles of consumption volumes that drive mass production, which lowers costs and spawns more consumption. Is this the future of closed-loop use of RFID? Unique Identification A fundamental concept of RFID is the notion of unique identification. If a bar-coded item is scanned twice, the system will reflect the existence of two items; the system failed to recognize that the same asset was scanned twice. RFID tags have a higher data capacity which allows for each item to be serialized; so if the item is scanned multiple times in an RFID-enabled system, the system will recognize the dual scans and filter out the erroneous data. Another advantage of an RF tag’s greater data capacity is the ability of RF tags to transmit self- describing data. For example, a tag can describe what the data is that it is transmitting. It can indicate that it is transmitting a VIN number with the number value, whereas a typical barcode only holds a value. Typically, the context of the bar code directs the person scanning the item to properly classify the data. For example, a worker at a receiving dock uses a bar code scanner to populate fields in an application running on a fixed or handheld PC. The worker determines which application to run, which field in the application to capture the data to, and the worker makes judgments on what to scan. If this worker saw a package of Doritos brand chips from someone’s lunch pail, they would know better than to try and scan that bar code into their application. The system relies on the worker’s judgment, which invites some degree of risk as people are fallible. People can
- 12. 10 scan the same items twice, or miss items. If the Doritos chips had an RF tag, the item would be possibly be read by an RF system; however, the self-describing data (indicating the grocers’ data standards) would tell the system that the scanned item was not relevant to the application. The EPC global data standard for RF tags includes a product classification code (which is defined by a global repository of product codes) and serial number for uniquely identifying the tagged object. The product classification code may be utilized to filter data streams (for example, filtering out the Doritos tag data) for relevant tags. It may also be leveraged in process control. An IT system can use the EPC standardized data, (and the global product code repository) to know what kinds of products it is reading, even if it does not have data about the particular serial numbers of the assets being read. This could be used by a system to validate asset combinations. For example, medical drug combinations could be checked automatically for violations of established medical rules; subassemblies on system-level products such as jet engines or automobiles validated in the manufacturing or aftermarket space; sea van containers of goods automatically scanned to apply export restrictions, tariffs, or other rules. Bridging the Gap: The Divide Between the ERP World and the RFID World The Wal-Mart example previously noted offered a potential savings of over $8 billion; however, the solution is estimated to collect over 7 terabytes of pRFID data per day once fully implemented. In comparison, a large ERP transactional system holds about 5 terabytes of data. The Library of Congress contains about 20 terabytes. The enormous volumes of continuously flowing RFID data requires new solutions that employ event filtering and distribute business logic that previously would have been stored on ERP or other core computing systems. The “traditional” model of storing data to disk for later batch processing does not work in this environment. Database “on disk” Structured query language Database “in memory” Event processing language Differences in Processing Differences in Data: Entity level data Manageable volumes Long-term data retention Low level, raw data Large volumes Temporal data RFID and Auto ID Environment The ERP data and processing model, depicted on the left side of the above diagram, is disk-based. It utilizes relational databases to manipulate manageable volumes of data that are retained for the long term. Data entry is highly refined (e.g., input a sales order line item for a particular company code) and requires a trained person to input much of the data. Data is processed from the disk, or database cache, utilizing a form of structured query language (SQL). SQL leverages relational database concepts to join tables of information with “key” linkages.
- 13. 11 The right side of the figure depicts the RFID environment. This environment has automated streams of data continually flowing from RFID readers. The data is unrefined, often transmitted in bursts, and (as the Wal-Mart example showed) provides much more data than typical IT systems are designed to process. This environment can demand the use of “In Memory” databases1 . There are several reasons to use memory instead of disk when processing streams of data. Memory is about a thousand times faster than disk, enabling better throughput. Also, the data is not necessarily useful after a few moments, so storing to disk adds no value for the long term. Solutions implemented for the ultra- high volumes of streaming data found in financial securities trading show an even more highly performing means of processing streams of data. These solutions bypass memory and send data streams directly to the processor (roughly similar to how a network router works). In place of SQL, event processing language (EPL) may be used to answer questions like “tell me when these two events occur within 30 seconds” — or, better yet, “tell me when these two events do not occur within 30 seconds.” SQL is not built to answer questions such as this. The EPL construct also relates to a technology concept known as complex event processing (CEP), which tracks timing and causality of activities within the IT landscape. CEP is a very new concept that can also provide system health and security functionality (see the appendix entry on CEP for more details). A good primitive example of an in-memory database is a Microsoft Excel spreadsheet. As each cell is updated, any related calculations occur immediately. The cell data is processed in real time and is not stored on disk (until the user decides to save the spreadsheet). There is no disk-based computing in Microsoft Excel. In-Memory Database Excel Example Asset ID Pedigree Location (X,Y) Zone Alert Console 0000001 Dynamite 1, 1 1 ALERT! Dynamite Near Welder! 0000002 Toolkit 4, 3 2 0000003 Extinguisher 7, 2 3 0000004 Welder 3, 1 1 0000005 Truck 5, 3 2 0000006 Safety Kit 5, 3 2 Rule Definition Zone Definition Dynamite Can’t work with Welder Zone 1 is where x is between 1–3 Welder Requires Extinguisher Zone 2 is where x is between 3–6 Truck Requires Safety Kit Zone 3 is where x is between 6–9 Here is a spreadsheet depicting the application of an EH&S rule that is designed to prevent situations where two active tagged items (Dynamite and Welder) should not be in the same zone. The X, Y values depict grid locations provided by a location appliance that processes TDOA, signal strength, or GPS-based location data. The X, Y values are continually updated in real time, the Excel example translates the X, Y data into zones, and pedigree-based rules are built to raise 1 Also known as a “Real-time In-memory Event-drive Database” (RIED). Gartner projects that commercial RIED solutions will grow significantly in the next 2 – 5 years
- 14. 12 alerts when zone violations occur. Here the EPC global-provided pedigree standard can be used. The above in-memory database example demonstrates real-time processing of multiple variables (e.g., location of dynamite boxes and location of welders). These databases could process large numbers of complex rules in real time, which this paper will refer to as “multi-variable” data processing. An important distinction needs to be made between multi-variable data processing and “serial” (or single variable) data processing. Traditional solution platforms enable scalable serial data processing solutions (SAP’s Auto ID Infrastructure (Aii) is an example, which this paper will discuss). These solutions process one record of data at a time, limiting the ability of the system to scale applications such as the above Excel-based alert utility. SAP’s RFID Solution: The Auto ID Infrastructure (Aii) Module Given their control over centralized business processes, SAP has an enormous competitive advantage when selling RFID middleware to its installed base. SAP offers Aii as a middleware package that provides several out-of-the-box automated functions as well as a platform (built on the same basis structure as R/3) for solution development that includes the ABAP and Java development environments. Two flavors of the latest Aii version (4.0) offer either a standalone solution, which requires 2 “custom” interfaces, or an integrated solution, which offers connections into “XI” (eXchange Infrastructure: SAP’s EAI module), EM (Event Manager), and R/3 (transactional system). The integrated solution includes R/3 core code modifications that integrate with the out-of-the-box Aii solution. The Aii solution may be a central instance located in the data center housing the R/3 instance, or it may be a distributed solution, allowing for multiple Aii instances in the various divisions of a corporation. Aii offers value in the extension of standard SAP business processes (as defined in the R/3 transactional system) to incorporate RFID data collection. It is highly likely that SAP will continue to develop RFID process extensions in Aii, as well as incorporate Aii into the dozens of vertical industry SCM hubs it is developing. There is also value in incorporating standard Aii functionality into existing mobile applications served by SAP. The out-of-the-box Aii process extensions apply only to standard SAP business processes. For example, customized shipping solutions in SAP will prevent the enterprise from utilizing the out-of-the-box shipping solution built in Aii. The value proposition of the Aii functionality, therefore, is highly dependant on the degree of process customization made in the R/3 product. A potential benefit of Aii is the development platform that it provides. This is the same basis platform, NetWeaver, upon which other SAP components are built. The underlying basis technology at the core of the Application Server is one of serial (not multivariable) data analysis. (The Aii module processes one record at a time, and is not designed to analyze multiple variables in memory. SAP could possibly leverage the Live Cache technology used in its Advanced Planning and Optimization module to provide such in-memory functionality.) This poses an acceptable limitation on the functionality offered by Aii, as that functionality is limited to serial process extensions of core R/3 business processes. If needed, an in-memory database could be stood up easily between Aii and RFID readers. That database would be able to capture SAP-relevant events and pass them on to Aii, XI, or even R/3 for processing. Further details on this and other elements of Aii are available in the appendix.
- 15. 13 Looking Forward: SAP NetWeaver and the Enterprise Services Architecture In the late 1990s, ERP vendors found customer dissatisfaction with their products in the area of enabling business process change. The companywide standardization of data and processes (which consolidated numerous legacy applications) that made ERP valuable to large corporations brought with it a monolithic system that raised barriers to business process change. Process or data changes intended to suit one division may impact other divisions. This was the seedling for the present ESA initiative. The ESA is SAP’s implementation of the SOA. The ESA breaks down enterprise IT functionality into component services that may be inexpensively organized into applications with BPM tools. This allows different divisions to customize applications without impacting other portions of the organization. The BPM tools interface is much like Visio, except the blocks in the resulting diagram are programmatically linked to services with standardized interfaces. An example to help in understanding this follows. A general contractor decides to build a division of houses. He opens the yellow pages, looks up “services” such as roofers, foundation contractors, framers, financers, realtors, landscapers, etc. The general contractor organizes these component services in such a way as to build and sell houses. In the same way, autonomous enterprise services are found in a kind of yellow pages directory that have standard interface definitions, organized using BPM tools to build applications. An example of the usage of this computing model is found at a large military aircraft manufacturer, which implemented an Intalio BPM solution to streamline spare parts order validations. The problem they had was that aircraft spare parts orders would be validated in SAP one error at a time (SAP would kick out the sales order on the first error, so if there were 20 errors in the order, the system would kick the sales order out 20 times for correction before being able to finally process the order). A solution that would have required 3,000 person days to build in SAP, took 300 person days to build with a BPM solution that employed SAP function modules and programs as services. This solution cost less to maintain than an internal ERP customization, which would require additional work (validating and adapting the solution) for every ERP software upgrade. The BPM solution resides outside of SAP and, therefore, avoids the costs associated with upgrading custom ERP applications. Several BPM tools, technologies, and standards have been developed in anticipation of a steady increase in SOA/ESA-enabled solutions. SAP and IBM coauthored a position paper called “BPEL for People,” which builds upon the established “Business Processes Execution Language (BPEL)” standard to add components that programmatically define how business processes interact with applications users. Given the marketing attention and investment statements made by SAP, it appears that emerging standards (such as BPEL) will be incorporated into the NetWeaver/ESA solution set to offer an internal, intranet-based BPM tools (in fact, the XI EAI tool offered by SAP is BPEL-compliant). SAP is leading the way in Gartner’s “magic quadrant,” which measures vision and ability to execute. The SAP Aii solution does not initially pass the Zrimsek Hurdle as it, by definition, does not create new business processes; rather Aii’s role is to extend and automate existing R/3 business processes. However, the Aii development platform offered may be used to define and automate new solutions. The ESA introduces the ability to rapidly change and customize business processes, which opens the door to change ERP from a monolithic implementation of standard processes to a solution that allows specialty areas (e.g., the above example’s military spare parts order fulfillment department) within the organization to make the system work for
- 16. 14 them. When predicting the optimal use of RFID in ERP, it is important to anticipate the future ERP environment. The ESA model offers a means of building adaptive business processes and a means of integrating functionality from external infrastructures (including Internet services and EPC global network data) into business processes and product offerings. It is this environment that RFID will mature in, as well as the larger Web 2.0 environment. Web 2.0 The Web 2.0 concept is a broad recognition of the changing nature of the online experience. It is partially enabled by the same concepts as an ESA or SOA. The Internet is becoming increasingly personalized and participatory for an increasingly connected population. Portable devices abound with new experiences for the mobile user, and new avenues for marketers to establish direct relationships with consumers. The cell phone has become a new transaction platform. A cell phone camera can be used to take a picture of a “spot code,” a symbol which is interpreted and resolved into a URL or Web service. The spot code shown below takes the user to CSC’s Leading Edge Forum Web site. Likewise, a universal identifier (UID — a two-dimensional part marking that is globally unique2 ) could be interpreted and resolved into a Web service that can provide services specific to the item scanned (for example, take a picture of a spot-code or UID on a copier machine to access a Web service that collects or displays maintenance history data, service manuals, or provides a service to reorder supplies). With a cell phone, a marketer can gain access to customer identity (thorough the cell phone account), preferences and purchasing history (through the customer’s online profile), where they are (via location tracking services on cell phones), and what service or even what specific item they are interested in (via scanning of spot code, UID, or RFID scan, which is a feature in some cell phones used in Asia). Products need not be located in stores for whimsical consumers to scan and purchase on demand at any location. Spot Code Universal Identifier (UID) Google has indicated investment in a service that would allow a consumer to compare prices in real time. Using this service, a consumer takes a picture of the bar code on an item (presumably in a store, but it could be a purchased product as well), the service looks up and provides a list of similar items, with their sale prices in proximity to the user, and offers directions to each location. The next step could be to allow online price comparisons and ordering of the same product. Google CEO Eric Schmidt has stated that he wishes to connect the world’s buyers and sellers. Surely RFID plays a large role in this goal. 2 The DoD estimates that there will be 100 million parts marked with UIDs by 2010.
- 17. 15 Speaking on how Google’s business model relates to RFID: “I think it’s interesting to think about what happens when you know where everything is…with RFID we have the ability to know where a good portion of the physical things in the world are and what happens to business models then…it’s going to change the way we do business”xi Dr. John R. Williams Director MIT AutoID Lab (Selected as one of the 50 most powerful people in networking) The comment by Dr. Williams suggests that asset location, which will be afforded by RFID, will become a publicly accessible set of data that may be utilized by solution providers such as Google. Such an intersection between asset location data and the rich functionality of Internet solutions offers a paradigm change open to new business models. The next wave of Internet-based solutions (Web 2.0) demonstrates how cheaply and easily data can be captured and computed at very large scales. The Web 2.0 model also shows that the resulting computed information is consumed in very small units. For example, Google AdWords services a $6 billion industry served at about 50 cents a shot. The zillow.com site will provide comparative market analysis real estate estimates anywhere in the nation instantaneously and for free. “The broad and rich foundation of the Internet will unleash a ‘services wave’ of applications and experiences available instantly over the Internet to millions of users…This coming ‘services wave’ will be very disruptive…The next sea change is upon us. “xii xiii William H. Gates Chairman and Chief Software Architect, Microsoft Corporation Apparently Microsoft is taking this sea change seriously, as the corporation recently adjusted projected development spending in fiscal year 2007 to be $2 billion more than expected. “It sounds like you’re building a Google or a Yahoo inside the company,” said Goldman Sachs & Co. analyst Rick Sherlund to Microsoft CFO Chris Liddell.xiv Web 2.0 demonstrates a few noteworthy points: • Technology is becoming a forum for expressing a person’s identity • Solutions offer focused information drawn from large amounts of data • Service performance and ease of use is a critical success factor • Software as a service, either for free (with targeted advertising providing the funding for the business model) or for a small charge • Increased ease of online payment for services Not all of the processed data is consumed. Zillow.com presumably has every address in the United States computed; surely not every address will be requested. In addition: • Solutions may be utilized as component services in an SOA, which leverages standard and inexpensive integration toolsets • Users are transacting and contributing online in new ways, with new devices, (note the cell phone) with greater degrees of personalization
- 18. 16 The Network Effect David P. Reed asserted that the utility of large networks can scale exponentially with the size of the network. This “network effect” is canonized as Reed’s Law. This utility is demonstrated in the number of users of telephones. If only a few people have a telephone, the utility of having one is much less. The example of the Marine’s supply chain improvements relies on a network of interested parties speaking up for their shipments. Ebay relies on networks of buyers and sellers working through its online auction site. Value is derived from networks, and is increasingly valuable when the network allows and enables contribution by nodes (network participants). The network effect is a large component of the success of Web 2.0. Some Web 2.0 models rely on high consumer volumes, providing small bits of value, to justify large IT investment solutions (e.g., Google AdWords). Other Web 2.0 solutions rely on groups that do more than consume information, but contribute to the overall value of the network (e.g., “ebay” or “experts exchange”). An optimal infrastructure for asset management will offer a means of knowledge worker contribution in such a manner. This concept is built upon by the popular book The Wisdom of Crowds by James Surowiecki. Crowds can make very unwise decisions when each individual is attempting to conform to a perceived consensus; this is titled “Groupthink”xv . Mr. Surowiecki states that the key qualities of making crowds (any group of people acting collectively) smart are diverse, decentralized, and independent nodes contributing to a mechanism capable of summarizing the group’s opinions into one collective verdict.xvi An example of this is a betting pool for a horse race or sporting event. The network effect has been largely associated with social networks. The SOA seeks to lower the barriers between computing services to enable easier adoption into networks, leveraging the network affect. An example of the network effect where the nodes are computing agents, instead of humans, is found in agile systems. Agile Systems An agile system is defined as one that is able to rapidly adapt to changes in its environment. Such a system is composed of a large number of small, loosely coupled “agents” or software objects performing specific calculations on data streams and passing on computed results to accomplish an overall objective. Examples are found in military systems that guide a missile to a particular target and in financial systems turning profits from arbitrage trades between several stock markets.xvii The figure that follows illustrates a variation on agile systems that associates software agents to real-world items and dedicates agents to warfighters as well.
- 19. 17 Integrated Marine Multi-Agent C2 System (IMMACCS)xviii xix The IMMACCS assigns a software agent to a warfighter once that individual’s location is known (for example, when they power on their GPS-enabled palm pilot). That software agent is dedicated to the interests of that particular warfighter. It constantly looks for all available intelligence on known enemy locations within a certain perimeter (represented by the circle surrounding Alpha Company) and notifies the warfighter. In urban warfare environments intelligence is supplied, in part, by the network of warfighters inputting known enemy combatant locations in real time. Somewhat similar examples of these systems are found in computer games which leverage object-oriented computing to produce highly complex simulations of a “real- world” environment. The real-time, strategy-oriented computer game, “Age of Empires” produced by Ensemble Studios and published by Microsoft in 1997, depicts a life-like environment with populations of civilian and military characters that the gamer manages in order to build both an economy and a military component. Networked players can share the same landscape, or game board, while they manage their particular tribe’s economic and military growth in order to wage war to dominate a particular landscape. The Age of Empires (AoE) game is a great example of object-oriented (OO) programming. OO programming encapsulates data and methods into a single program, which may be “instantiated” (manifested, incarnated, turned into an actively running program) multiple times. An OO program is like a cookie cutter. Once it is defined it can stamp out multiple cookies (actively running programs) that are independent of one another (The cookie dough is memory with a dash of processor cycles). Once created, the cookies have no relationship to one another; they can be modified (decorated) but will retain the “inherited” shape given by the cookie cutter.
- 20. 18 Battle Scene from the Age of Empiresxx Looking at the AoE game, each individual unit on the “game board” is an object. A character has set capabilities (e.g., can build buildings, fish, chop wood, move around, and has workflow rules it follows) and variables (e.g., health points, attack- and-defend variables, speed of movement, and inventory of collected raw materials). Dozens of characters of different types are guided by the gamer, each character an instantiated object representing an independent program. Changes to one character have no impact on other characters, yet all objects can interact with one another in an “arms-length” fashion. This general concept is in contrast to the ERP environment, where any change to a data structure or process has a broad impact. If a developer wanted to change a material master record in an ERP system so that just one record had a field that was longer, they could not do so without impacting all the records in that table. Likewise, if one wished to change a process, such as the sales order process, for just one sales order, this could not be done without impacting all sales orders flowing through that process. Asset-Oriented Computing The future of ERP is ESA, component services organized by BPM tools for diverse applications. The future of the Internet is Web 2.0, cheap and valuable information, personalized to user preferences, and even a mobile users’ location, provided on demand and programmatically consumable. The cost of customizing business processes drops and IT functionality and information available to workers increases, both from internal enterprise services and from external Internet- provided services. The network effect relies on nodes of self-interest providing value in a symbiotic fashion, best leveraged when individuals are empowered in their capabilities to
- 21. 19 develop solutions. How might the network effect be realized with a corporation’s physical assets? A concept for consideration is to associate one instantiated object with a single RFID tagged asset (product or non-product) or a logical asset collection (such as items on a pallet, a kit, or a lot). It is at this point that many of the concepts previously described come together to form a unique concept that this paper will refer to as “asset services.” This concept is highly academic in nature3 , but provides an end-point vision for asset management solutions. This concept departs substantially from conventional data- processing solutions and proposes a platform for enabling a “network effect” for asset management. The key to the network effect is the participation of the nodes on the network. The model seeks to provide knowledge workers with toolsets that enable the customization of asset “behavior,” thus exposing asset management to the network effect. Recapping several concepts: • RFID provides the fundamental capability to uniquely identify assets in a manner providing a great deal of data at a very low cost of data collection. • The network effect is seen in many Web 2.0 innovative services. The value of the network is in the size of the participating nodes, per Reed’s Law. • The network effect was exemplified in the Marine’s supply chain improvements, which enabled interested parties to view and affect the location of in-transit assets. • Both the Web 2.0 and ERP worlds are engaged in building reusable services with standardized interfaces. This lowers the barriers to entry for solution components to play a part in a larger network effect. • BPM tools are used to organize services into tailored applications and offer a means of programmatically defining business processes. • Object-oriented technology has specifically demonstrated capabilities relevant to the asset services model both in highly advanced applications (such as IMMACCS), as well as more commonplace applications such as the Age of Empires game. The object allows inheritance of standard behavior, but also allows customization per object with no negative impact on the overall system. These concepts can be formulated together into a strategic infrastructure for the management of assets in a setting where change is constant and the process authority is either localized or specialized. The IMMACCS dedicates a software agent to the warfighter which looks out for the warfighter’s interests; why not have a dedicated software agent for an asset that does the same? Revisiting the Marine’s Supply Chain As previously noted, the success of the Marine’s supply chain improvements stemmed from forward commanders being able to view real time, in-transit asset locations and act upon that information. The forward commander’s checks and phone calls for expedition could be replaced with dedicated agents, which the forward commanders manage. This would be conceptually similar (but much more robust) to an e-mail message that one would flag for a reminder (the e-mail message is singled out and customized to serve the readers’ agenda, likewise an 3 Note that the author has visited a startup company with several of the components in place for this computing model, so the model may become a strong commercial tool in years to come. Any implementation of this model would rely on several integrated (and standards- based) IT infrastructure- oriented products, not on one standalone product.
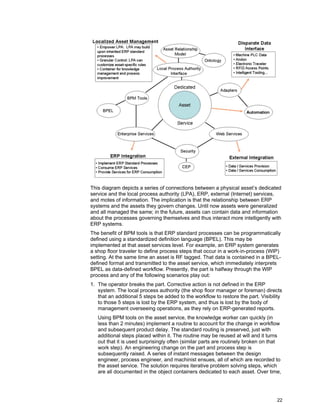
- 22. 20 asset service may be singled out and customized with a similar degree of ease). Such agents could do much more than monitor deliveries, as the next few examples demonstrate. The DoD is working to incorporate RFID with sensors in munitions in order to track life- cycle data on missiles. For example, a lot of 200 sparrow missiles procured in 1980 was broken into two groups; one group was stored on the USS Enterprise (posing a potential salination-based corrosion), the other in Saudi Arabia (posing a high temperature–based degradation). The two environments represent different forms of erosion on critical missile components. The use of RFID and integrated sensors allows for the complete life cycle environmental data to be used to assist in avoiding unnecessary demilitarization of such high-value items. This example does well to clear the Zrimsek Hurdle — it derives value in a new process through the use of RFID-collected data. Asset services agents could be dedicated to collecting and aggregating the environmental data for all 200 missiles. This would guide ordnance evaluators in determining the right statistical sample of missiles to test to determine the best demilitarization point. Suppose a shipment contains a chemical warfare antidote, which is sensitive to high temperatures impacting its shelf life. The pallet of antidote would have a dedicated service monitoring (among other things) its temperature sensor and able to notify local officers of a potential future spoilage issue. What if the temperature sensor on the pallet was nonexistent or broken? A dedicated agent could first look for agents of other pallets in close proximity to itself, obtain their temperature readings, and extrapolate the same data for itself. If no such data was available, it could search for an enterprise service that gives the internal temperature of the distribution center the asset is located in. If the “3G RFID w/SATCOM” tag is used, (which communicates directly to a satellite) the service could provide its GPS coordinates to a building locator Web service, which confirms that the tag is outdoors, then the object could check a Web service on weather.com to determine temperature conditions. It could go on to detect that tomorrow has unusually high temperatures predicted and send an alert with that information. This chain of behavior may seem difficult to develop, but it is exactly what BPM tools can provide with tools simple enough for a nonprogrammer to define in a quick manner. If these tools can be provided to knowledge workers in a manner that helps them do their jobs better, a network of asset management automation solutions will emerge. Such a network will become a repository for asset-centric knowledge. Industrial Applications of the Asset Services Model Consider a fan assembly for a jet engine, worth tens of thousands of dollars, at rest on a shop floor. Consider the depth and breadth of knowledge and expertise that contributes to the creation of that fan assembly, and how little of that knowledge is accessible. The concept of knowledge management is the gathering of information residing in people’s memory banks and storing that information in a manner that can be reused as necessary. The asset is a terrific container for knowledge about itself. Below is an abridged array of data and processes that surround the asset. Note that the asset is not directly connected to the data and processes.
- 23. 21 Aftermarket Data • Consumption/depreciation • Life-cycle data collection • Life-cycle services Aftermarket Process • Goods receipt/dispatch • Warehouse management • Repair history • Life-cycle management • Reduce fraud/theft/waste • Returns process • Supplier warranty tracking • Product and consumables reordering Warehouse/Distribution Processes • Replenishment • Right shipment to right customer • Process visibility • Tracking history • Reduction of out of stock Engineering Data • Engineering revision • Quality inspections • Certifications • Failure modes • Drawings Manufacturing Data • Machining statistical data • Image processing data • Tooling, lotting • Vendor/supplier • Raw materials • Instant messaging • Quality inspections • Bill of materials • Routing/traveler • Outsourced services • Personnel data • Project stock versus plant stock Manufacturing Processes • Electronic traveler • Tracking “as built” configuration • Automate line management • Inventory management • Configuration management • Condition monitoring • People and asset movement • Maintenance repair and overhaul • Mandate compliance • Accounting/costing Inbound Supplier Processes • Goods receipt/dispatch • Warehouse movement • Supply chain movement • Site security • Product track and trace • Inventory availability Asset ERP systems contain a great deal of standardized business process behavior that governs many of the processes and data collection models listed in the above figure. The asset, until now, has been only indirectly associated with data and processes relevant to it via ERP (which affords little process change capabilities) or shop floor systems (which are possibly more accommodating to process changes but exist in nonintegrated “motes” of information). The following figure depicts a means of connecting an asset to disparate data sources and enabling localized customization building upon ERP standards. Note that in this diagram, an asset is defined as a single asset, an asset class (such as a part class), or an asset collection (such as a pallet or collection of subassemblies). An asset can be any item, tangible (such as a machine) or virtual (such as a purchase order).
- 24. 22 This diagram depicts a series of connections between a physical asset’s dedicated service and the local process authority (LPA), ERP, external (Internet) services, and motes of information. The implication is that the relationship between ERP systems and the assets they govern changes. Until now assets were generalized and all managed the same; in the future, assets can contain data and information about the processes governing themselves and thus interact more intelligently with ERP systems. The benefit of BPM tools is that ERP standard processes can be programmatically defined using a standardized definition language (BPEL). This may be implemented at that asset services level. For example, an ERP system generates a shop floor traveler to define process steps that occur in a work-in-process (WIP) setting. At the same time an asset is RF tagged. That data is contained in a BPEL- defined format and transmitted to the asset service, which immediately interprets BPEL as data-defined workflow. Presently, the part is halfway through the WIP process and any of the following scenarios play out: 1. The operator breaks the part. Corrective action is not defined in the ERP system. The local process authority (the shop floor manager or foreman) directs that an additional 5 steps be added to the workflow to restore the part. Visibility to those 5 steps is lost by the ERP system, and thus is lost by the body of management overseeing operations, as they rely on ERP-generated reports. Using BPM tools on the asset service, the knowledge worker can quickly (in less than 2 minutes) implement a routine to account for the change in workflow and subsequent product delay. The standard routing is preserved, just with additional steps placed within it. The routine may be reused at will and it turns out that it is used surprisingly often (similar parts are routinely broken on that work step). An engineering change on the part and process step is subsequently raised. A series of instant messages between the design engineer, process engineer, and machinist ensues, all of which are recorded to the asset service. The solution requires iterative problem solving steps, which are all documented in the object containers dedicated to each asset. Over time,
- 25. 23 a library of custom process steps for such contingencies is implemented in that WIP area and available for other organization units to adopt. 2. The part is placed on a truck to be shipped to another company plant. The truck driver leaves for the weekend before making the delivery. The company has lost visibility into where the asset is. The plant manager creates his own workflow rule to notify the relevant parties when an asset is loaded on a truck in one location and does not show up at its intended location within a reasonable driving time. 3. The part is in one of four production lines which all end with the same finishing process. The end of all four lines is stacking up with inventory ready to move. Presently the finishing process is idle, as none of the WIP inventory has been moved yet. A bottleneck in operations is about to occur. The plant manager builds a rule to monitor WIP inventory levels in all pre- bottleneck locations. Notifications are sent to the line managers and manager of the finishing process. 4. An expensive tool used in forming the part breaks. The tool is placed in a scrap tooling bin. The asset service detects the tool’s location and reminds the relative worker that the tool is still under warranty, and offers a link to the warranty claim process. 5. A new tool, an automated torque wrench, is used in the WIP process. The new tool requires torque-related data. The asset service interfaces with the tool’s controller to provide torque specifications derived from either its BPEL-based shop floor traveler download, or the asset service calls an enterprise service which provides the data for that part type. The ability to override the torque settings is limited to shop process engineers. 6. The asset is finished and incorporated into an aircraft engine. Years later, the engine is overhauled and the asset is found to be severely damaged, requiring investigation. Some, but not all, similar assets have the same failure modes. The original asset services used when manufacturing the failed parts are restored from a persistent state. All of the data collected via the asset services is made available to forensic engineers. The root cause (e.g., an improperly calibrated tool or particular engineering revision level) is found and corrective action taken, including a recall of other specific parts that were impacted by the defined root cause. The manufacturer is able to limit the recall to the right parts. Data can become a form of intellectual property that provides competitive advantage. Further details are available in the “Aircraft Engine Aftermarket” appendix section. The network effect is at work. Over time, a series of routines become commonplace, some account for process steps that are ill-defined in the ERP system, some reflect specific workflow notification tasks which help management detect issues, some reflect rules such as invalid part combinations, etc. Beyond allowing adaptive process changes, this proposed model offers a platform for integrating disparate data sources that may or may not be relevant to ERP. Benefits of an Asset Services Infrastructure: • In-memory processing: continuous data streams may be monitored by an in- memory mechanism with a robust set of tools to aggregate data and/or apply
- 26. 24 business logic to data streams, triggering events such as ERP transactions or employee notifications. • Data and process change management: because the process is tied to an independent object, legacy processes may be allowed, enabling perfect flexibility in upgrading processes. New data sources may be tied to the asset. • The asset service allows robust asset management even when ERP systems are unavailable due to WAN outages or maintenance outages. • Inheritance of standard behavior: core ERP-driven standards are implemented; the local process authority cannot override core process requirements. • Scalable platform: the object may be extended to provide and consume an ever- increasing amount of enterprise and Web services. • Object interaction: As demonstrated in the Age of Empires, objects are able to execute arm’s-length transactions with one another. • Ability to rapidly prototype: new processes may be implemented and changed while in process one asset at a time. • Platform for “lean” management: the platform enables an event-driven environment, dovetailing with the single-piece flow concept. • Platform to enable computing “intelligence” in deriving inferences about real- world events: offers significant functionality for system security (see the CEP entry in the appendix for more details). Recommendations While the asset services model is not a mature product available commercially now, an IT decision maker can take steps toward enabling the network effect by looking for the following demonstrated principals in software purchase or development decisions: 1. To harness the network effect is to enable solution participants to add value. This is accomplished by providing simple, light development toolsets to knowledge workers. This requires defining the knowledge worker population and giving that group a voice in the software selection process. Note that process authority distribution will vary widely; for example, Wal-Mart has a centralized process authority (processes are not different for each store or distribution center), whereas GE has a very distributed process authority (with the strong emphasis on Six Sigma, which drives continuous improvement down to the front line managers). A Wal-Mart solution will likely be customized by a centralized competency center, which will derive and implement global best practices. The GE solution will likely be used by varied, distributed process owners, and the resulting applications will be unique to each division; however, the tools used to build each unique application will utilize a standardized toolset. The nature of the toolset will be determined by the technical expertise of the body of knowledge workers. Therefore, when comparing RFID candidate systems, look for the ease of solution customization in the hands of knowledge workers. 2. Scalability is a critical component to any RFID system. Solutions that utilize toolsets need to fit into a “hardening” path: a well-thought out plan for scaling the solution several orders of magnitude. This includes the hardware infrastructure as well as the capability of the solution to foster future growth, such as incorporating the ability to provide and consume Web and enterprise services. A key to enabling scalable future growth is the solution’s compliance with established computing standards such as Web and enterprise services,
- 27. 25 BPEL compliance, and EPC global standards. Multi-variable solutions will require new kinds of enabling technologies such as In-Memory databases.4, 5 3. Solutions should mirror reality as much as possible. An RFID solution ideally will offer a means of describing the relationships between real-world items. This will most likely leverage an ontology which will describe such relationships. RFID adoption should be included in strategic planning, as an overall direction towards an asset services model will not happen otherwise. RFID systems are known to accelerate the speed of business process change, prompting organizational changes. The procedures used to facilitate business process changes may need to be redefined. The organizational structure may need to be altered. A competency center may be needed to handle external infrastructure integration, toolset hardening paths, and support for the local process authority. Strategic planning needs to extend beyond supply chain solutions and consider the value of RFID in non-product assets or as a means of delivering value-adding services to the product offering. The Medtronic Corporation makes implantable healthcare devices such as pacemakers. In the 1990s, Medtronic built a strategic vision that planned a service offering by 2010, which would allow implanted devices to communicate vital statistics via RF signal to a patient’s home-based reader, which would transmit this data over the Internet to an online healthcare center. Here, RF technology is leveraged with the external infrastructure of the Internet to deliver a strong product differentiator. Medtronic can leverage the standards and network available over the Internet while preserving their value proposition with a proprietary protocol in the device-to-reader exchange. The “own versus influence” model offers some guidance when making strategic decisions surrounding the patching of emerging technologies. This model suggests that technologies with a potential for proprietary technical advantage be developed, procured, or acquired (see the appendix for the model diagram). RFID usage breaks into two categories. The first category is the use of cheap (costing pennies), disposable, passive RFID tags running serial process optimization in an open- loop environment. This category will be used to optimize existing business processes. It will utilize various external infrastructures such as the EPC global network and SCM hubs (such as SAP’s in-development SCM hubs, or vertical search engine communities). The second category will utilize more costly RFID tags, (ranging from basic active tags to the 3G RFID w/SATCOM tag, which is globally visible) and will utilize an ontology of defined relationships, leveraging the network effect and possibly implementing CEP for system security. In this category, RFID is used to visualize the status of multiple groups of assets. Integrating systems like IMMACCS with 3G RFID w/SATCOM in military applications is likely to be the first widely adopted implementation of this kind of RFID usage. As the market leader of ERP solutions, SAP is leading the way in building context- sensitive, industry-specific solutions built on reusable services. SAP is providing 4 Some instant messaging solutions offer the ability to directly view server memory over the network. This is a pull-based means of viewing data (and is heavy on network bandwidth); however, this offers a highly scalable means of dedicating any number of network servers to a single stream of data. 5 Multi-variable data sets offer more potential value as the permutations of variable data combinations offers exponentially greater data specificity about the real world. For example, a single data set tracks the location of WIP assets. Another data set tracks tooling locations. When combined, (making a multi-variable data set) the system can deduce which tools were used on which assets, offering functionality not available when the two data sets were separated.
- 28. 26 avenues for joint “co-innovation” amongst solution providers through a common business language. This business language connects disparate infrastructure products and software applications in its “partner ecosystem” space. According to SAP, the speed of innovation is increasing.xxi These developments intersect with the RFID data collection world to enable a fundamental change in the relationship between assets and IT systems. Assets will become contributing nodes in a network of solutions that offer new services to consumers and new efficiencies in asset management. As with the “horseless carriage,” RFID will grow out of the conception of “wireless bar coding” as it is adopted in business, military, and society.
- 29. 27 Appendix The Aircraft Engine Aftermarket Unique identification allows one to ask and answer valuable questions from a maintenance and repair operations perspective. For example, consider a jet engine hollow fan blade disassembled from an engine being overhauled. That blade has a unique identifier (called a UID, which is a two-dimensional bar code etching onto the part). Management can know the life-cycle history of that part, plus on-wing usage information for engine diagnostic systems. Inexpensive image collection and processing software can automate the identification of the “failure modes” exhibited by that blade (the failure modes being visible signs of wear and tear to the part). Here is an abridged list of available information regarding that particular blade: • Aircraft engine engineering build: an aircraft engine will have a specific engineering revision build, much like how an operating system or application has a service pack level. Differing levels will impact component wear or depreciation differently • Life-cycle data such as on-wing vibration, excess temperature, even plane operating locations (e.g., a plane in the Middle East will incur more sand- oriented damage) • Value chain data such as raw material supplier (even which hole in the ground the oar came from), engineering revision level, lot data, assemblers, machinists who built the part (and their relative certifications), tools used, calibration of the tools used, etc. • Other parts in the engine, with their relevant value chain and life-cycle data • Historical data on failure modes of all blades Here is a dramatic example of the vast amounts of data that could be integrated to better predict part depreciation, provide feedback to engineering on failure modes and what usage scenarios caused them, and better predict spare parts requirements, allowing for reductions in inventory. This demonstrates the concept of data as a competitive advantage. The manufacturing data generated by a company cannot be duplicated by competitors. Any value derived from that data may not be duplicated. This can make data a form of intellectual property. Pratt & Whitney announced in February 2006 that it would begin making parts for GE engines. A jet engine manufacturer sells its engines at cost, and makes several times that amount in the aftermarket which spans from 20 to 30 years following the sale. This move by Pratt & Whitney substantially impacts GE’s financial models, and could have a ripple effect across the aerospace industry. This demonstrates the potential business impact of aftermarket ownership, as well as the concept that your manufacturing data could constitute a competitive advantage. Data can become a form of intellectual property; no other company can duplicate it.
- 30. 28 Details on SAP’s “Auto ID Infrastructure” (Aii) Product The Aii module is designed for the first scenario shown above (as indicated by the “1” and the green connecting lines). The Aii module reads device controller- provided data serially (one record at a time) and applies rules, or filters, to the data to determine what activities or function modules are executed. This is ideal for all gate-based activities. The Aii module interfaces via XI (SAP’s EAI toolset) to R/3 and other SAP components. Aii also has its own Business Warehouse stack. Aii can trigger automated transactions in R/3, such as a goods receipt or shipping transactions. If customized, other transactions may be automated, such as a goods movement in inventory. Aii has a mobile device component, so SAP- delivered mobile applications will enjoy more rich functionality as the Aii product is continually invested in by SAP. Aii can also send data to the Event Manager, which is an SAP component that provides process track and trace functionality. A multivariable processing solution (e.g., an in-memory database) may be placed in front of Aii (see the “Localized Solution” box above). Such a solution could glean events from RFID multivariable data streams and pass that to Aii for processing (marked as “2”). If the Aii module does not need to be used, the solution could connect to the XI (EAI hub – marked as “3”) data processing hub, which will route messages asynchronously to targets, such as the event manager. Lastly, if a highly customized R/3 application requires synchronous communication with the RFID device controller layer, the line marked as “4” may be drawn by implementing a SAP JCO solution which utilizes a direct “RFC” connection. Another option (not displayed as it is currently not validated by SAP) is to connect RFID asset location information directly to the cache on a custom table located on an R/3 application server. This would be used when frequent random R/3 calls are issued looking for specific asset location data. The “Heavy Solution”, (see diagram below) displays the cost of implementing Aii for a heavily customized R/3 application. In this case the Aii software is purchased; however, the standard Aii functionality does not fit with the existing custom packing solution. The result is that Aii is used as an EPC generator and device interface. The solution is heavy in system resource consumption, infrastructure component requirements, and ongoing maintenance. If a data structure is changed in R/3, the
- 31. 29 change could require up to 6 downstream data structure modifications (steps 1, 5, 7, 11, 15, 18). The “Light Solution” is an alternative that involves fewer moving parts, faster execution time, less infrastructure resource consumption, and more code reusability. The connection between steps 3 and 4 of the light solution is a point to point connection that is authenticated once then kept open as long as both components are live. While XI offers the ability to add future subscribers to the data flowing through it, it also validates each message’s header login data. In the case above, it is very hard to imagine a situation where another network entity would reasonably wish to receive the data being transmitted to the device controller. A benefit of RFC-based communication with SAP is that a session is established and persists beyond each message. The Exchange Infrastructure product requires that each message packet be authenticated, adding data, overhead, and functionality not needed in this example to the data transfer process. This leads to the following rule of thumb: Where very high volume data transfers occur on an ad hoc basis between a trusted on-network source and R/3, and where such data being transferred is highly unlikely to be of use to any other potential applications, such a connection may utilize the RFC protocol, bypassing XI. There are more variables to take into consideration when choosing the best solution (consult your local CSC technical representative). The value of Aii is primarily in its extension of SAP business processes and the development platform it offers. For this reason, it appears that the best implementation of Aii is as a single, integrated solution co-located with its target R/3 server. The architecture can scale by adding device controllers (with expandable data filtering functionality) placed in various shop floor locations, matched by Aii server resource additions which allow increased work processes and communication channels. Complex Event Processing (CEP) CEP is a means of building causality models which can interpret multiple sources of data to gather inferences about real world events. CEP does this by defining event causality within a system. For example, a tagged asset is moved from a WIP location to a finished goods inventory location. The RFID access points transmit the data to a location appliance, which is interrogated by an in-memory database. That database applies established business rules to detect the WIP completion event and triggers an event by sending a message to a SAP Aii module. The SAP Aii module receives a single data packet, applies a rule, which triggers an activity and processes the event by sending a message to SAP R/3, which performs a few validation checks and then writes to the database. This is graphically depicted (partially) in the below figure.
- 32. 30 This figure represents streams of data from RFID access points being filtered for events, which cascade down to a layer of activity (or persistence). The small green square at the persistence layer represents the WIP to Finished Goods Inventory event. That event (referred to as the “causal event”) triggers an ERP application server function to perform 3 sub-functions, the last of which writes data to the database server. The hierarchy of activities caused by the one causal event is denoted on the right hand side of the figure. Note that systems work processes and network transmissions are included in the hierarchy. Among other things, the CEP model creates a system monitoring mechanism that anticipates what the system load should be, given the inventory of current causal events. It can then check what the system load actually is. A discrepancy between what should be and what system load actually is may indicate a security breach. For example, an unexplained spike in network activity may indicate a denial of service attack. An unexplained set of server work processes may indicate the presence of a software virus. The basic tools that CEP uses involve the tracking of causality and timing of events in a system landscape. A major concern about RFID is security.6 A CEP model may be applied to help secure a system from unauthorized access, and may be used to compile more variables about real world events to gauge suspicious behavior. 6 Though security is out of scope of the grant work, (it is addressed in a 2005 LEF Grant) the recommendation by the grantee is to avoid storing sensitive data on an RF tag, instead, store that data on a network and use the tag serial number as a data access mechanism. If the secure data is required in areas without network connectivity, consider a UID label (which would require a direct physical read by the user and a camera-based reader). Other options involve using more advanced RF tags, for example if concerned about unauthorized RF reads of items in transit on a truck, the RF tags can be designed to transmit when not in motion, or only when not in motion for a certain amount of time. Lastly, the EPC Generation 2 standard allows for tag readers to supply encrypted passwords which active tags validate before responding.
- 33. 31 CEP defines the Event Processing Language (EPL) which can be used to answer in-memory database questions (such as “tell me when these two events happen within 30 seconds”) as well as interpret data streams to infer real world events (e.g. the asset is on the lathe, the lathe is on, the worker is in front of the lathe, therefore the person is working on the asset). The Own Versus Influence Model i Stakutis, Chris, Webster, John. “Inescapable Data: Harnessing the Power of Convergence.” IBM Press, 2006, page 1, Chapter 8. ii Stakutis, Chris, Webster, John. “Inescapable Data: Harnessing the Power of Convergence.” IBM Press, 2006, page 2, Chapter 8. iii Collins, Jonathan. “RFID’s Impact at Wal-Mart Greater Than Expected.” http://www.rifdjournal.com/article/articlepring/2314/-1/1 read 5/5/2006. iv Collins, Jonathan. “RFID’s Impact at Wal-Mart Greater Than Expected.” http://www.rifdjournal.com/article/articlepring/2314/-1/1 read 5/5/2006. v ComputerWeekly.com, “RFID Revolution Years Away, says Gartner,” July 29, 2005. http://www.computerweekly.com/articles/article.asp?liArticleID=135349&liFlavourID=1&sp=1 # vi Collins, Jonathan. “DoD Quantifies Payback from RFID.” http://www.rfidjournal.com/article/articlepring/2323/-1/1/ read 5/5/2006 vii Collins, Jonathan. “DoD Quantifies Payback from RFID.” http://www.rfidjournal.com/article/articlepring/2323/-1/1/ read 5/5/2006. viii “New Portable Deployment Kit uses Iridium Satellite Links to Track Military Supplies in Area of Operations,” Iridium Press. http://www.iridium.com/corp/iri_corp- news.asp?newsid=163 read 12/5/2005. ix Collins, Jonathan. “DoD Tries Tags That Phone Home.” http://www.rfidjournal.com/article/articleview/1458/1/65/ read 12/5/2005. x Fee, Jeffrey D. and Schmack, Alan. “Improving RFID Technology.” http://www.globalsecurity.org/military/library/report/2005/050200-rfid.htm read 12/5/2005. xi “Architecting the Internet of Things,” http://autoid.mit.edu/cs/video.aspx xii http://www.scripting.com/disruption/mail.html
- 34. 32 xiii http://www.internetnews.com/ent-news/article.php/3562881 xiv Greene, Jay. “Microsoft’s Strange Spending Splurge.” http://webdesign.ittoolbox.com/news/display.asp?i=142080&t=7 read 4/28/2006 xv http://en.wikipedia.org/wiki/Groupthink xvi “Q&A with James Surowiecki,” Random House. http://www.randomhouse.com/features/wisdomofcrowds/Q&A.html xvii Luckham, David. “The Power Of Events,” Pearson Education, Inc. 2002, page 21. xviii Pohl, Jens; Wood, Anthony A. (Col. USMC, Ret.); and Pohl, Kym Jason. “IMMACCS: An Experimental Multi-Agent C2 System.” http://www.cadrc.calpoly.edu/pdf/immaccs_multi.pdf xix Pohl, Jens. “Intelligent Software Systems: Do We Need Them?” http://lef.csc.com/technologyprograms/ xx http://en.wikipedia.org/wiki/Age_of_empires xxi Agassi, Shai, SAP Executive Board Member. “Leading the Web Services Wave.” (Blog Site) http://www.sap.com/community/int/blog/ShowBlog.epx?PostID=353432 read 5/22/2006.