Triển khai Modsecurity vào hệ thống NMS - Quan Minh Tâm
- 1. MODSECURITY ELK If we do not wish to fight we can prevent! {
- 2. ModSecurity Security Bootcamp 2014 2
- 3. *log Security Bootcamp 2014 3
- 4. ELK Security Bootcamp 2014 4
- 5. ModSecurity Ryan C. Barnett ModSecurity is an open source, cross-platform web application firewall (WAF) module. Known as the "Swiss Army Knife" of WAFs, it enables web application defenders to gain visibility into HTTP(S) traffic and provides a power rules language and API to implement advanced protections. Blackhat Arsenal 2014 Security Bootcamp 2014 5
- 6. Surviving D-Day Omaha Beach 1944 Security Bootcamp 2014 6
- 7. Surviving D-Day Omaha Beach 1944 Fake tank Fake aircraft Fake Napoli (Egypt) Fake …… Security Bootcamp 2014 7
- 8. HoneyTraps with ModSecurity http://map.honeycloud.net/ Security Bootcamp 2014 8
- 9. 1.Real-time Application Profiling Security Bootcamp 2014 9
- 10. Real-time Application Profiling Request method(s) Number of parameters (minimum/maximum range) Parameter names Parameter lengths (minimum/maximum range) Parameter types Flag (such as /path/to/foo.php?param) Digits (such as /path/to/foo.php?param=1234) Alpha (such as /path/to/foo.php?param=abcd) Alphanumeric (such as /path/to/foo.php?param=abcd1234) E-mail (such as /path/to/foo.php?param=foo@bar.com) Path (such as /path/to/foo.php?param=/dir/somefile.txt) URL (such as /path/to/foo.php?param=http://somehost/dir/file.txt) SafeText (such as /path/to/foo.php?param=some_data-12) Security Bootcamp 2014 10
- 11. Real-time Application Profiling Security Bootcamp 2014 11
- 12. Post-Process Profiling Security Bootcamp 2014 12
- 13. 4 scenarios If the HTTP response code is 404, the resource doesn’t exist. In this case, not only do we skip the profiling, but we also remove the resource key, so we delete the persistent storage. This is achieved by using the setvar:!resource.KEY action. If the HTTP response code is either level 4xx or level 5xx, the application says something is wrong with the transaction, so we won’t profile it in this case either. The OWASP ModSecurity Core Rule Set (CRS) can use anomaly scoring. We can check this transactional anomaly score. If it is anything other than 0, we should skip profiling. Finally, we have already seen enough traffic for our profiling model and are currently in enforcement mode, so we skip profiling. Security Bootcamp 2014 13
- 14. 2. Hacker Traps Security Bootcamp 2014 14
- 15. Hacker Traps Unused Web Ports Fake robots.txt Disallow Entries Fake HTML comments Fake hidden form fields Fake cookies Security Bootcamp 2014 15
- 16. Hacker Traps Unused Web Ports Security Bootcamp 2014 16
- 17. Hacker Traps Fake robots.txt Disallow Entries Security Bootcamp 2014 17
- 18. Hacker Traps Fake HTML comments Security Bootcamp 2014 18
- 19. Hacker Traps Fake HTML comments Security Bootcamp 2014 19
- 20. Hacker Traps Fake hidden form fields Security Bootcamp 2014 20
- 21. Hacker Traps Fake cookies Security Bootcamp 2014 21
- 22. Hacker Traps Fake cookies Security Bootcamp 2014 22
- 23. 3a. Self-Contained vs. Collaborative Detection Security Bootcamp 2014 23
- 24. Self-Contained vs. Collaborative Detection Self-Contained Collaborative Security Bootcamp 2014 24
- 25. Anomaly Scoring Threshold Levels Security Bootcamp 2014 25
- 26. 3b. Inbound/Outbound Correlation Security Bootcamp 2014 26
- 27. Correlation Did an inbound attack occur? Did an HTTP response status code error (4xx/5xx level) occur? Did an application information leakage event occur? Security Bootcamp 2014 27
- 28. Correlation If an inbound attack was detected, and either an outbound application status codeerror or information leakage event was detected, the overall event severity is raised to one of the following: • 0, EMERGENCY, is generated from correlation of anomaly scoring data where an inbound attack and an outbound leakage exist. • 1, ALERT, is generated from correlation where an inbound attack and an outbound application-level error exist. Security Bootcamp 2014 28
- 29. 4. Detecting Malicious Links Security Bootcamp 2014 29
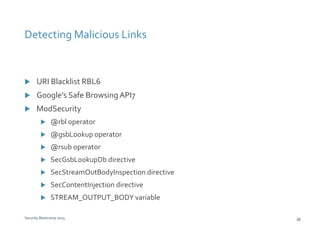
- 30. Detecting Malicious Links URI Blacklist RBL6 Google’s Safe Browsing API7 ModSecurity @rbl operator @gsbLookup operator @rsub operator SecGsbLookupDb directive SecStreamOutBodyInspection directive SecContentInjection directive STREAM_OUTPUT_BODY variable Security Bootcamp 2014 30
- 31. 5. Normalizing Unicode Security Bootcamp 2014 31
- 32. Normalizing Unicode Best-Fit Mapping Detecting Use of Full-/Half-Width Unicode Security Bootcamp 2014 32
- 33. Best-Fit Mapping %u3008scr%u0131pt%u3009%u212fval(%uFF07al%u212Frt(%22XSS%22)%u02C8)%u23 29/scr%u0131pt%u232A 〈(0x2329) ~= <(0x3c) 〈(0x3008) ~= <(0x3c) <(0xff1c) ~= <(0x3c) ʹ(0x2b9) ~= '(0x27) ʼ(0x2bc) ~= '(0x27) ˈ(0x2c8) ~= '(0x27) ′(0x2032) ~= '(0x27) '(0xff07) ~= '(0x27) Security Bootcamp 2014 33
- 34. Unicode Mapping Security Bootcamp 2014 34
- 35. Unicode Mapping Security Bootcamp 2014 35
- 36. Full-/Half-Width Unicode Security Bootcamp 2014 36
- 37. 6. Abnormal Header Ordering Security Bootcamp 2014 37
- 38. Passive OS fingerprinting Security Bootcamp 2014 38
- 39. 7. Detecting Page Title Changes Security Bootcamp 2014 39
- 40. Detecting Page Title Changes Security Bootcamp 2014 40
- 41. 8. Web Client Device Fingerprinting Security Bootcamp 2014 41
- 42. Web Client Device Fingerprinting Security Bootcamp 2014 42
- 43. 9. Slowing Down Automated Attack Tools Security Bootcamp 2014 43
- 44. Slowing Down Automated Attack Tools Security Bootcamp 2014 44
- 45. NSM Logstash Elasticsearch Kibana No code required Real-time analysis of streaming data Highly scalable Open source, community driven Security Bootcamp 2014 45
- 46. DEMO Security Bootcamp 2014 46
- 47. “ ” Thank you! Question, huh? FPT TELECOM Security Bootcamp 2014 47